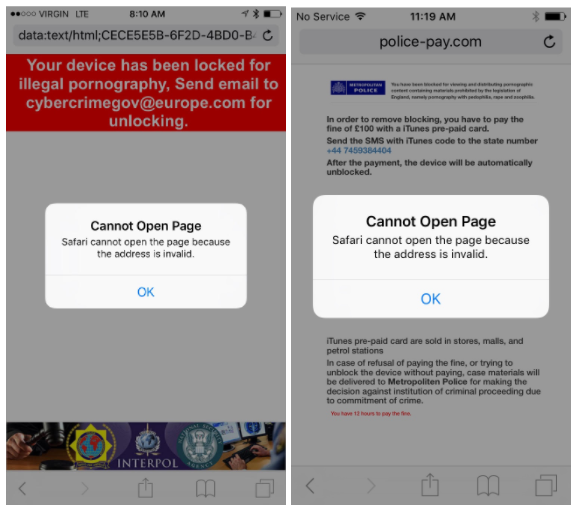
Ransomware scareware attempts based on users viewing adult content is not something new but they often turn out to be successful. A brand new such campaign was recently detected by Lookout researchers on iOS Mobile Safari browser, extorting money from users who viewed obscene content on their devices. Fortunately, the vulnerability that led to the attacks was patched in Monday’s iOS patch.
How was the campaign carried out?
The ransomware / scareware campaign was built on a vulnerability which involved the way Safari displayed JavaScript pop-ups. The attackers exploited the handling of these pop-up dialogs in Mobile Safari resulting in preventing the user from using the browser. During that time, a threatening (hence the scareware name of this tactic) message would be displayed to force the victim into paying. The victim would be blocked until the ransom was paid in the form of an iTunes Gift Card.
Related: How to Bypass Apple’s iOS Activation Lock on iPhone and iPad
However, as explained by Lookout:
A knowledgeable user could restore functionality of Mobile Safari by clearing the browser’s cache via the the iOS Settings — the attack doesn’t actually encrypt any data and hold it ransom. Its purpose is to scare the victim into paying to unlock the browser before he realizes he doesn’t have to pay the ransom to recover data or access the browser.
Luckily, the attack surface was utterly eradicated with the iOS 10.3 patch. The patch changed the way Mobile Safari handles website pop-up dialogs, “making them per-tab rather than taking over the entire app”.
The attack was originally reported to Lookout’s Support desk by one of the company’s users running iOS 10.2. The user said he had lost control over his browser after he visited a website. Researchers say that attacks based on this code appear to have been developed for older versions of iOS, like iOS 8. However, the exploit of pop-up dialogs was still possible up to iOS 10.3.
In addition, it’s very likely that the scammers behind this scareware campaign purchased a large amount of domains in an attempt to catch potential victims searching for explicit content.