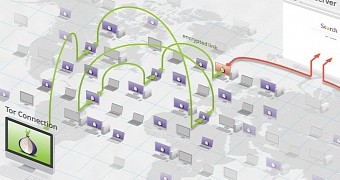
Josh Pitts with Leviathan Security discovered an ”exit node” for the TOR network that is currently located in Russia and has been used to distribute a modified version of the legitimate code that the user has requested.
In order to turn anonymous, TOR connections go through numerous servers that relay the message in an encrypted form until they reach an exit node that communicates with the destination directly.
That type of server was used to distribute patched binaries that were used for malicious activities. As the user issues the download request, he would be provided with a tampered executable, in case the connection was established through the Russian Tor exit node in question.
Bypassing Varification
Pitts explains that a large number of binaries are hosted without profiting from TLS encryption. A great part of them are not signed, so they would not get modified in transit. In such cases, the hackers could use the man-in-the-middle approach to intercept the user’s request and return a different file than the one expected by the user, and do this without raising suspicion.
It took the researcher about an hour to find a harmful exit node, once he resorted to TOR. The specialists have analyzed more than 1,110 exit servers, and the one Pitts has discovered seems to be patching almost all binaries he attempted to download. Reportedly, the note patches uncompressed PE files only.
Pitts thinks that the original binary is wrapped with a second one and that the hackers found a way to preserve the file icon. This way the cyber crooks can bypass the self-checking mechanisms in the case of NSIS.
→What the Nullsoft Scriptable Install System does is create installers for the Windows platform.
TOR Security Issues
To limit the risks, developers are advised to deliver their binaries through an encrypted connection. Users should make sure that the hash of the file they have downloaded is the same as the original one. This must be done before they execute the program.
The TOR Project is alerted about the issue, and the relay server is red-flagged, warning users not to connect through it.