After a research about a Tor exit node, modifying uncompressed Windows executable files downloaded through it was recently published, experts have discovered that the issue leads back to the Russian APT family MiniDuke, which is famous for being used in malicious campaigns targeting NATO and European government agencies. However, the malware exploited in this case belongs to a separate malware family, which was dubbed OnionDuke.
What Is OnionDuke and How Does It Work?
As the victim downloads an executable through the malevolent Tor exit node, he gets an executable “wrapper” containing the original and a malicious executable. The separate wrapper help avoiding any kind of integrity checks that the original binary may contain. As the wrapper is being executed, it keeps writing the disk and executing the original .EXE. This way the victim is led to believe that the process was completed normally. But the wrapper would also launch the second executable, which is detected as Trojan-Dropper:Win32/OnionDuke.A. It contains a PE resource disguised as an image file, which is, in fact, an encrypted DLL file.
Upon execution, the DDL file decrypts an embedded configuration and tries to connect to URLs from the Command and Control servers. The C&Cs may send instructions to the malware to download and execute more harmful components. Experts believe that the malicious domains are regular websites, hacked by the cyber crooks.
Components of the OnionDuke Malware Family
The research team that’s been analyzing the OnionDuke malware family detected components designed to steal login credentials from the compromised computers, as well as elements that were created to collect other data on the affected machine. For example is a firewall, or an antivirus product is active on the computer. A part of the observed components are downloaded and executed by the backdoor process. The infection vector of others is yet to be determined.
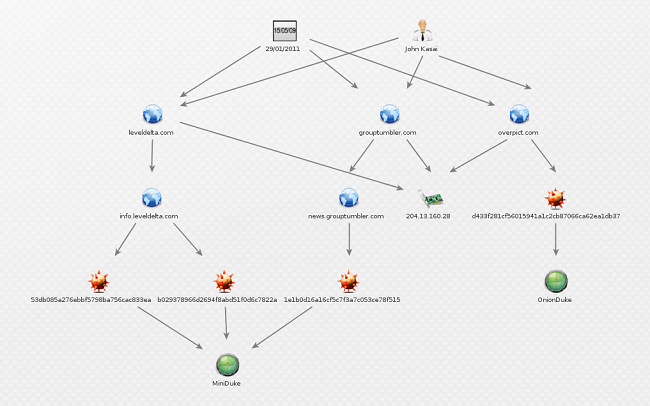
One of the components has been considered an exception by the researchers. This particular DLL file has a different C&C domain in its configuration data – overpict.com. The experts are almost certain that this component is capable of abusing Twitter as a C&C channel. This domain has been registered by John Kasai along with a large number of other domains. Here’s the list:
- beijingnewsblog.net
- leveldelta.com
- natureinhome.com
- nostressjob.com
- oilnewsblog.com
- ustradecomp.com
- sixsquare.net
- airtravelabroad.com
- grouptumbler.com
- nasdaqblog.ne
- nestedmail.com
- nytunion.com
Тwo of these domains – grouptumbler.com and leveldelta.com – were used in previous MiniDuke campaigns. This is a clear sign that despite the fact that both MiniDuke and OnionDuke belong to different malware families, they share an infrastructure.
Experts believe that the OnionDuke has been active since October 2013. Evidence suggests that the malware has been infecting executables in . torrent files that contained pirated software since February 2014. The compilation timestamps analyzed by the team suggest that the OnionDuke malware family is much older.
The OnionDuke was most probably used in attacks against government agencies in Europe, using two different strategies:
- Mass-infection through altered binaries.
- Surgical targeting, often associated with APT operations.
There are still too many blanks at the moment, but one is clear – using the Tor network is a plus when you want to stay anonymous, but it makes you an easy target for cyber-attacks. Avoid downloading binaries through Tor without encryption, because you never know who maintains the exit node you use.