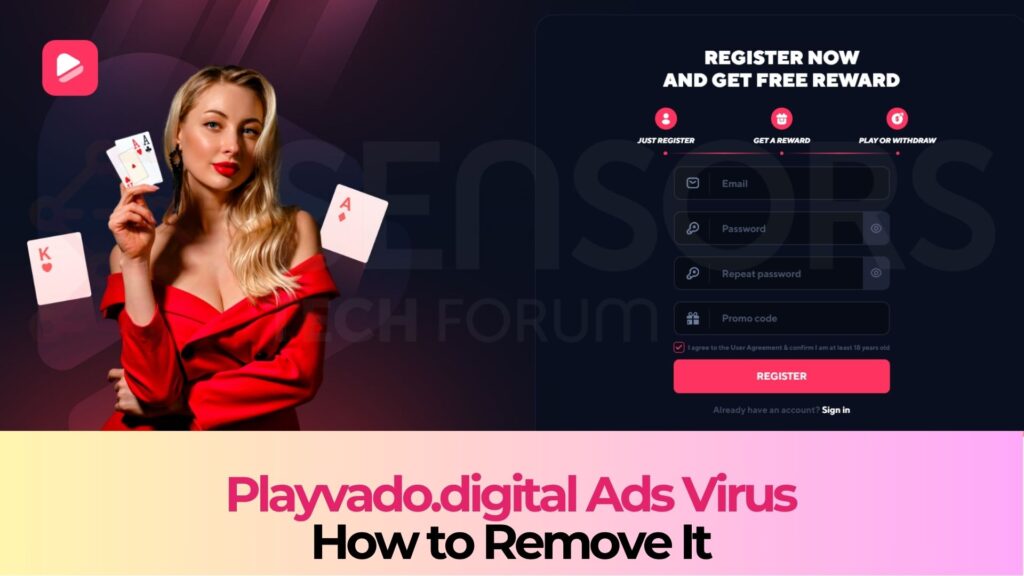
Playvado.digital Redirects Virus – Removal Guide
Problems with Playvado.digital hijacking your browser? Read this article as we will explain here how to get rid of it and prevent similar issues in the future. What Is Playvado.digital? If Playvado.digital suddenly shows up in your browser, that often…



![Adventurer Virus [.adventurer Files] – Removal & Recovery Adventurer Virus [.adventurer Files] - Removal & Recovery](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/adventurer-virus-ransomware-files-removal-and-decryption-1024x576.jpg)
![BQTLOCK Virus [.BQTLOCK Files] Removal + Restore Guide BQTLOCK Virus [.BQTLOCK Files] Removal + Restore Guide](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/BQTLOCK-virus-ransomware-removal-1024x576.jpg)


![Jumobet.com Pop-ups Virus – How to Remove It [Fix] Jumobet.com](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Jumobet.com-ads-virus-removal-1024x576.jpg)
![Rimobet.com – Is It Safe? [Scam Check] Rimobet.com - Is It Safe? [Scam Check]](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Rimobet.com-is-it-safe-1024x576.jpg)
![Dalubform.com Virus Pop-ups – Removal Guide [Fix]
Dalubform.com ads virus fix](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Dalubform-com-ads-virus-removal-1024x576.jpg)
![Trixroll.com – Is It Safe? [Scam + Virus Check] Trixroll.com - Is It Safe?](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Trixroll.com-virus-ads-is-it-safe-scam-1024x576.jpg)
![DesignHub Ads Virus – Removal Guide [Solved] DesignHub ads](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/DesignHub-virus-site-removal-guide-ads-1024x576.jpg)
![Asw-confm.co.in Pop-ups Malware – Removal Steps [Fix] Asw-confm.co.in](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Asw-confm.co_.in-ads-website-remvoal-guide-1024x576.jpg)
![Sinobi Virus Ransomware [.Sinobi Files] Removal & Fix sinobi-virus-ransomware-removal-guide](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Sinobi-virus-removal-guide-1-1024x576.jpg)
![Sync.contextualadv.com Ads Virus – Removal Guide [Fix] Sync.contextualadv.com adware removal guide](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Sync.contextualadv.com-virus-ads-removal-guide-1024x576.jpg)