
How to Remove Trojan from Mac
What are Mac Trojans? How to remove a Trojan from Mac? How to stop Mac Trojans in the future? Trojans are the types of threats on Mac, whose main purpose is to obtain data from it and perform a range…

What are Mac Trojans? How to remove a Trojan from Mac? How to stop Mac Trojans in the future? Trojans are the types of threats on Mac, whose main purpose is to obtain data from it and perform a range…

What is .lanset ransomware also known as .lanset file virus? What to do if your files were encrypted by .lanset ransomware? If your files are encrypted and the .lanset extension is appended to them, then you are dealing with a…

The .luboversova148 ransomware is a new Globe Imposter version. It is being distributed using the familiar tactics associated with other similar threats. As the .luboversova148 ransomware is based on the main Globe Imposter code we anticipate that the hackers has…
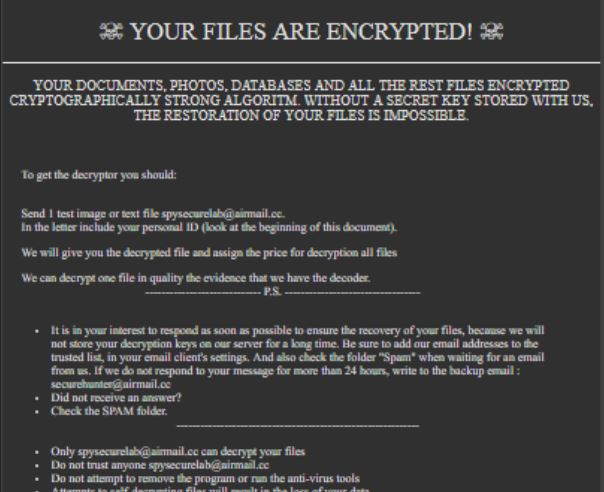
The .SECURE ransomware is a new derivative of the Globe Imposter malware family. It is being distributed in a similar way to previous versions of the malware family. As the malware builds on an earlier version we anticipate that the…
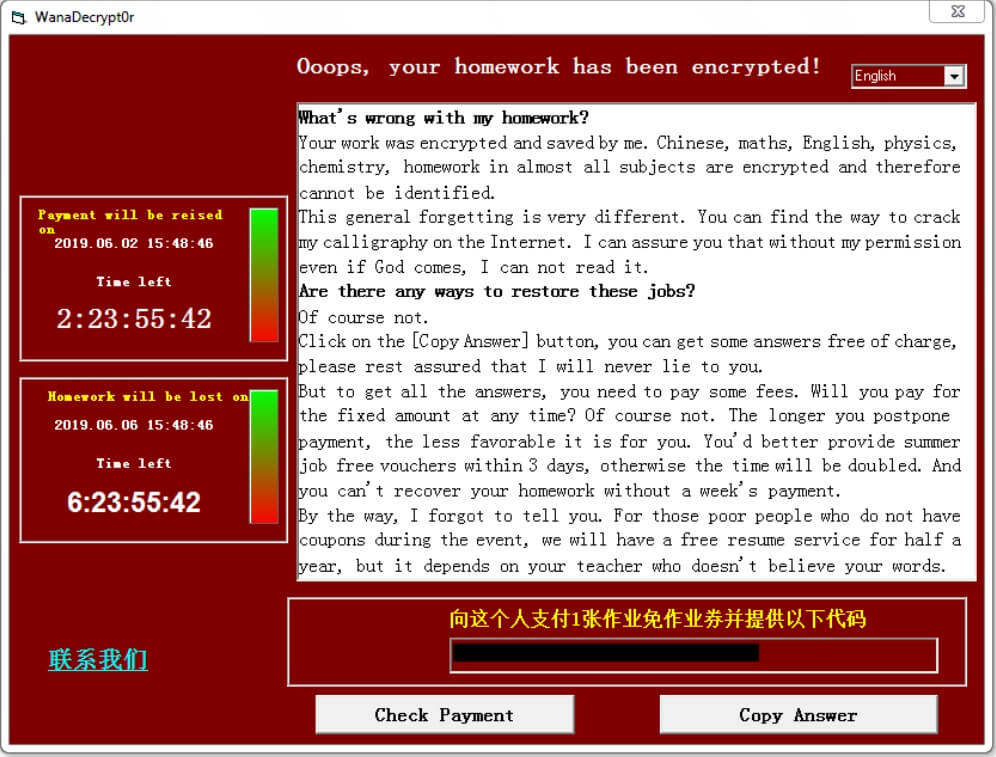
What is .PLEASE_CONTACT_1398456099@qq_com files virus? What is Ooops, your homework has been encrypted! ransomware? Can files encrypted by the .PLEASE_CONTACT_1398456099@qq_com files virus be recovered? Ooops, your homework has been encrypted! or otherwise known as .PLEASE_CONTACT_1398456099@qq_com files virus is ransomware. It…

This article will help you remove .bak files virus totally. Follow the ransomware removal instructions provided at the end of the article. Rotorcrypt is the name of a virus that encrypts your files, also known as .bak files virus. Files…
What is adware? How to remove adware and unwanted programs from your Mac? How to stop ads and pop-ups from Macs? Adware programs are those pesky applications on Mac that tend to harass users with a lot of different pop-ups,…

The macOS operating system has been found to possess a critical security flaw, the malware technique is known as “synthetic clicks”. In essence this allows for various apps and scripts to bypass the security prompts and access sensitive data. Synthetic…

What is .redmat ransomware a.k.a. .redmat files virus? What to do if your files were encrypted by .redmat ransomware? If your files are encrypted with the .redmat extension appended to them, then you are dealing with a serious ransomware infection.…

What is a ransomware infection? How to remove a ransomware virus from Mac? Can ransomware infect a Mac? How to stop ransomware on Mac? A ransomware virus is the type of virus that encrypts your files or denies access to…
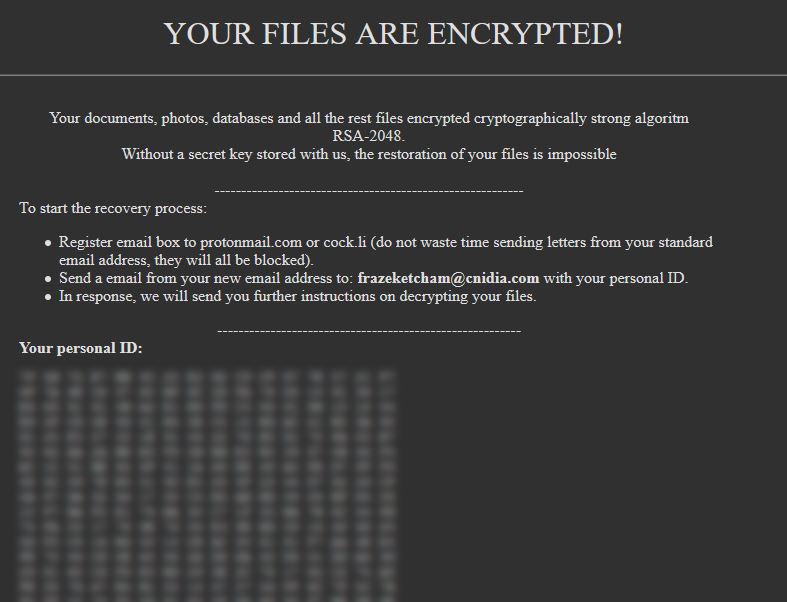
The .hv88g2 ransomware is a new virus iteration of the Globe Imposter family. Ransomware samples of this particular type have been detected in an ongoing attack campaign. As the malware builds on an earlier version we anticipate that the hackers…
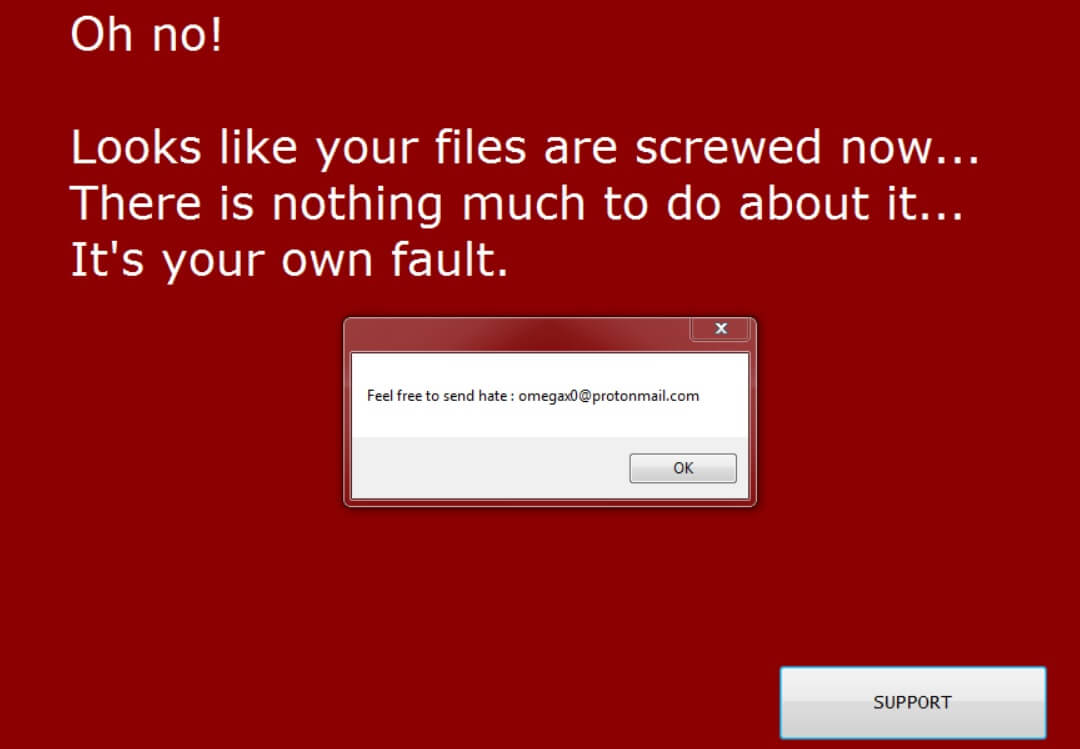
What is .dodger files virus? What is Dodger ransomware? Can files encrypted by the .dodger files virus be recovered? Dodger or otherwise known as .dodger files virus is ransomware. It encrypts files by appending the .dodger extension to them, making…

Security researcher Dhiraj Mishra just discovered a security vulnerability, CVE-2019-12477, in the SUPRA smart TV brand. Apparently, Supra Smart Cloud TV allows remote file inclusion in the openLiveURL function, which could enable a local attacker to broadcast fake video without…
What is Searchinggood.com page? Which program causes Searchinggood.com redirects? How to remove the unwanted program, causing Searchinggood.com redirects from your computer? The Searchinggood.com redirect is a malware browser hijacker and page combination which aims to infect as many victims worldwide.…
What is .stone Files Virus? How to remove it from infected PC? Can .stone files be recovered? The so-called .stone files virus is a nasty ransomware infection that corrupts computer systems with the goal to encode personal files and demand…
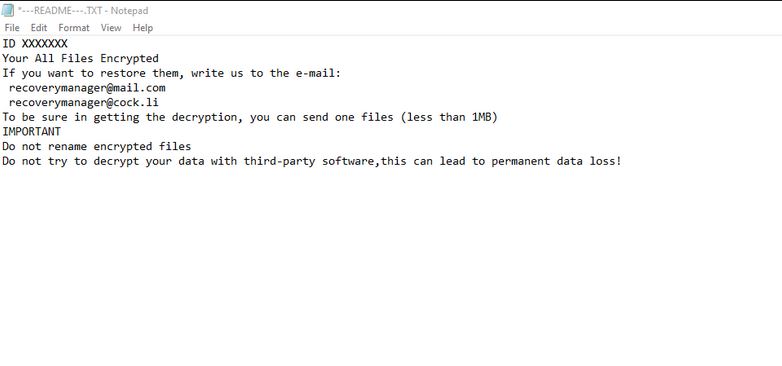
Update September 2019. The .SONIC ransomware is a dangerous new iteration of the Jamper malware family which is being distributed using the most popular tactics. It is not known whether or not the original collective behind Jamper is responsible for…
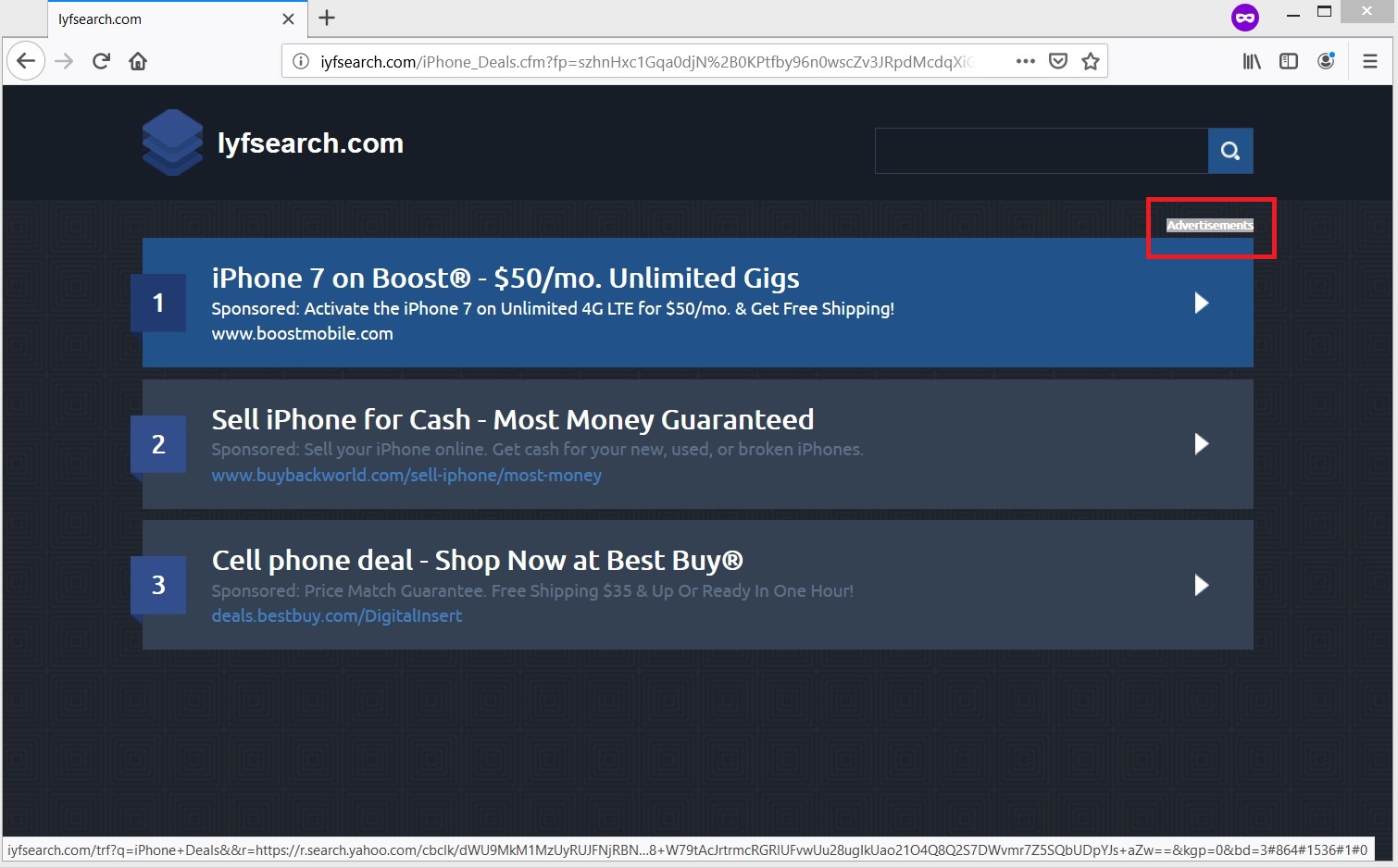
This article presents information about the annoying iyfsearch.com browser redirect and provides help for its complete removal from the affected system. The website iyfsearch.com is as presented an online platform that presents software and product promotions. It is categorized as…
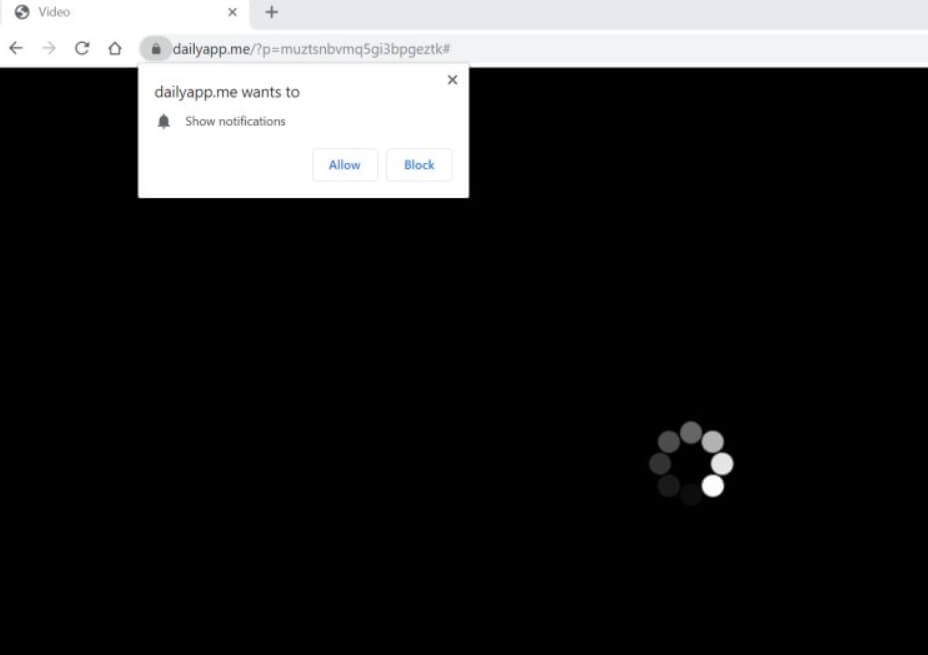
Can Dailyapp.me pop-ups affect your browser? Is Dailyapp.me a redirect? Does Dailyapp.me spam you with pop-up ads? How to remove Dailyapp.me redirect? Dailyapp.me is a malicious URL address used for the purposes of redirecting users to sites containing spam, advertisements…
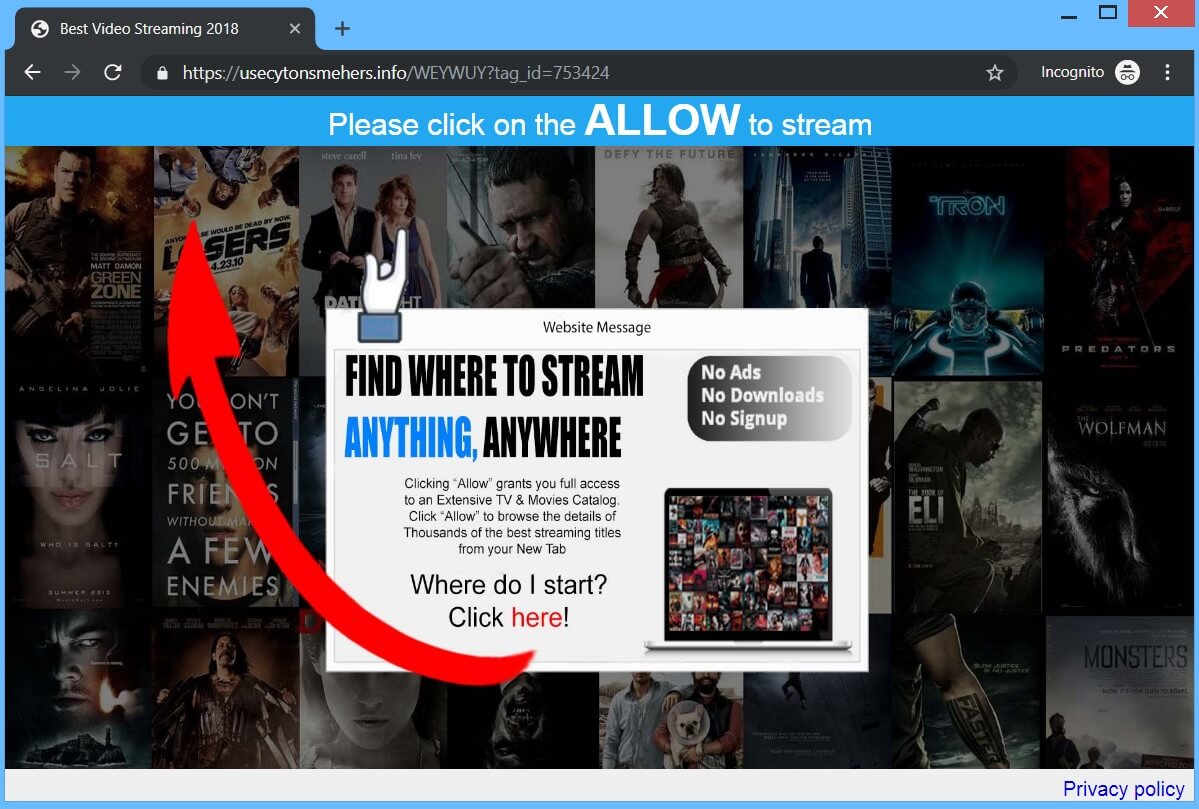
Can Usecytonsmehers.info pop-ups affect your browser? Is Usecytonsmehers.info a redirect? Does Usecytonsmehers.info spam you with pop-up ads? How to remove Usecytonsmehers.info redirect? Usecytonsmehers.info is a malicious URL address used for the purposes of redirecting users to sites containing spam, advertisements…
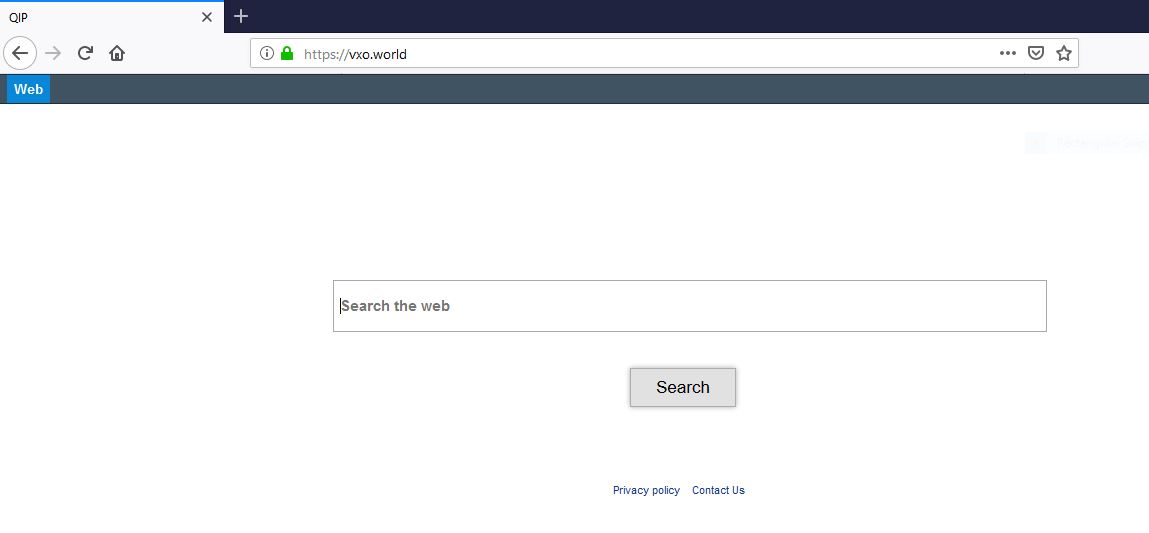
What is Vxo.world page? Which program causes Vxo.world redirects? How to remove the unwanted program, causing Vxo.world redirects from your computer? The Vxo.world redirect is a new browser hijacker and malware page combination which is set against victims worldwide. At…