Have you ever encountered an email that made your heart skip a beat with its claims of spyware and leaked personal data? The Pegasus Email Scam also known as “Have you heard of Pegasus?” email scam preys on such fears, fabricating stories of compromised devices to extort victims. Its strategy: to bluff recipients into believing that their most private moments are under threat by the notorious Pegasus spyware.
This article dives deep into the anatomy of the Pegasus Email Scam, revealing the tactics employed by cybercriminals and offering practical steps to identify, repel, and recover from these deceitful attempts. Read on to arm yourself with knowledge and tools that safeguard your digital safety against this modern-day extortion.
Threat Summary
| Name | Pegasus Email Scam also known as “Have you heard of Pegasus?” email scam |
| Type | Tech Support Scam |
| Short Description | An extortion scam claiming that the victim is infected with the infamous Pegasus spyware. |
| Removal Time | Approximately 15 minutes to scan the whole system and remove any discovered threats |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
What Exactly Is the Pegasus Email Scam?
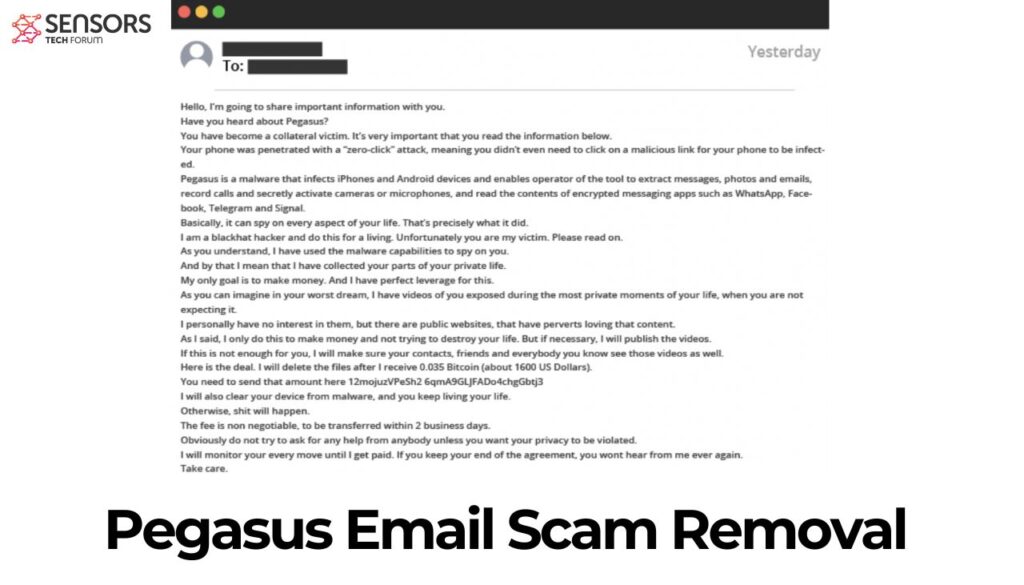
The Pegasus Email Scam is a sophisticated attempt, a social engineering trick, to exploit human emotions through fear and extortion. Individuals receive an email falsely claiming that a hacker has compromised their devices with Pegasus spyware. Here’s an example of such an email message:
Hello, I’m going to share important information with you.
Have you heard about Pegasus?
You have become a collateral victim. It’s very important that you read the information below.Your phone was penetrated with a “zero-click” attack, meaning you didn’t even need to click on a malicious link for your phone to be infected.
Pegasus is a malware that infects iPhones and Android devices and enables operator of the tool to extract messages, photos and emails,
record calls and secretly activate cameras or microphones, and read the contents of encrypted messaging apps such as WhatsApp, Facebook, Telegram and Signal.Basically, it can spy on every aspect of your life. That’s precisely what it did.
I am a blackhat hacker and do this for a living. Unfortunately you are my victim. Please read on.As you understand, I have used the malware capabilities to spy on you.
And by that I mean that I have collected your parts of your private life.My only goal is to make money. And I have perfect leverage for this.
As you can imagine in your worst dream, I have videos of you exposed during the most private moments of your life, when you are not expecting it.I personally have no interest in them, but there are public websites, that have perverts loving that content.
As I said, I only do this to make money and not trying to destroy your life. But if necessary, I will publish the videos.
If this is not enough for you, I will make sure your contacts, friends and everybody you know see those videos as well.Here is the deal. I will delete the files after I receive 0.035 Bitcoin (about 1600 US Dollars).
You need to send that amount here 1AXNYLDEG5YEzc2eyUh7SUYYKeRUaRwseuI will also clear your device from malware, and you keep living your life.
Otherwise, shit will happen.The fee is non negotiable, to be transferred within 2 business days.
Obviously do not try to ask for any help from anybody unless you want your privacy to be violated.
I will monitor your every move until I get paid. If you keep your end of the agreement, you wont hear from me ever again.
Take care.
This spyware, known for its surveillance capabilities, allegedly captures compromising information or activities. The scammer then demands a ransom, typically in Bitcoin, threatening to release the gathered content to the recipient’s contacts if not paid. However, the truth behind these emails is far less alarming, as they are baseless, relying solely on deception and the recipient’s lack of knowledge about cyber threats.
Grasping the Pegasus Email Scam Mechanism
The mechanism behind this scam is rather straightforward yet effective due to its exploitation of leaked data and human psychology. Scammers first acquire potential victims’ contact information and passwords from previous data breaches. They then send out mass emails, incorporating these personal details to add credibility to their claims. These messages assert that through Pegasus spyware, the scammer has obtained explicit videos or incriminating footage of the recipients. The final stroke of their deceit involves demanding ransom in cryptocurrency, exploiting the anonymous nature of such transactions to avoid tracing.
- Acquisition of leaked user data from past breaches.
- Dispatch of tailored scam emails featuring obtained personal information.
- False claims of spyware infiltration and data theft.
- Ransom demand with threats of public disclosure.
This scare tactic preys on the fear of social embarrassment and the potential fallout from such exposures. Yet, with no actual spyware or stolen data, the scam relies solely on the victim’s reaction and compliance.
Origins of the Pegasus Email Scam: A Brief Overview
The origins of the Pegasus Email Scam trace back to a growing awareness and fear of digital surveillance tools among the general public. Pegasus, a real spyware developed for governmental surveillance, became publicly known for its robust capabilities of accessing smartphones and other devices in depth. Capitalizing on the widespread coverage and concern surrounding such spyware, scammers saw an opportunity. By merely mentioning Pegasus, they lend a veneer of credibility and imminent threat to their schemes.
This scareware tactic has evolved from various forms of online extortion, adapting to incorporate current events or public fears into its narrative. As digital literacy varies among email users, the believability of these scams also fluctuates. However, a common thread in their success is the exploitation of human psychology specifically, the fear of embarrassment and the desire to quickly resolve potential threats to one’s privacy.
In summary, the Pegasus Email Scam represents a blend of opportunistic cybercriminal activity and social engineering, exploiting known fears for financial gain. While it is named after real spyware, the connection ends there; no actual spying occurs. Awareness and education on such scams can significantly diminish their impact and prevent potential financial and emotional distress among targets.
How Can You Identify a Pegasus Email Scam?
Email scams have become sophisticated over the years, attempting to trick individuals into believing their security has been compromised. The “Have you heard of Pegasus?” email scam is particularly notorious for instilling fear by pretending to exploit the victim’s privacy. Recognizing the signs of this scam can protect your digital wellbeing. Here’s how to identify such deceitful attempts:
Key Characteristics of Pegasus Scam Emails
The first step in safeguarding yourself from the Pegasus email scam is to understand its characteristics. These emails typically:
- Claim to have installed Pegasus spyware on your device without your consent.
- Allege to have gathered compromising information or videos of you.
- Demand payment, often in Bitcoin, to prevent the alleged information from being leaked.
- Include urgent and threatening language to create panic and prompt immediate action.
- May mention a password you have previously used, obtained from data breaches, to appear legitimate.
Spotting these hallmarks can be the first line of defense against being scammed.
Comparing Pegasus Emails with Legitimate Notifications
Distinguishing between scam and legitimate notification emails is crucial for online safety. Legitimate emails from service providers or security companies:
- Lack urgent and threatening tones often found in scam communications.
- Do not demand payments in crypto-currency for issue resolution.
- Include verified contact information allowing recipients to confirm the message’s authenticity directly.
- Feature company logos and branding, though this alone isn’t a reliability indicator due to potential spoofing.
- Provide detailed information on how to independently verify and address the issue mentioned.
By comparing these characteristics, you can more easily spot scam emails pretending to wield the Pegasus spyware threat. It’s important to always be informed and understand that legitimate entities will not engage in intimidation tactics or demand cryptocurrencies for problem-solving. If ever in doubt, directly contact the mentioned organization using official contact details found on their website.
In any circumstance where you’re unsure about the authenticity of an alarming email or if you fear your device’s security might be at risk, it’s wise to use trusted security software. SpyHunter is highly recommended for scanning and protecting your devices against malware threats and ensuring your digital environment remains secure.
Immediate Steps to Take if You’ve Received a Pegasus Scam Email
Discovering a scam email in your inbox can be a troubling experience, especially when it comes with threats regarding your privacy. The “Have you heard of Pegasus?” scam email uses fear to manipulate its recipients, but knowing the immediate steps to take can help you navigate this situation with confidence. Here’s what you should do…
Do Not Respond: The First Rule of Dealing with Scam Emails
Engaging with scam emails only brings you closer to potential dangers. Regardless of how urgent or threatening the message seems, your best course of action is to avoid replying. Responding to these emails can signal to the scammers that your email is active, possibly leading to more phishing attempts or targeted scams. Moreover, never open any attachments or click on links within such emails, as they could harbor malware designed to infect your device or steal personal information.
Reporting the Scam: Where and How to Report Pegasus Emails
If you’ve become the target of a “Have you heard of Pegasus?” scam email, reporting it is a crucial step. By alerting the authorities, you not only protect yourself but also help prevent the spread of these fraudulent activities. The Internet Crime Complaint Center and the Federal Trade Commission are two main platforms where scams like these can be reported. When you report the scam, try to provide as much information as possible, including the email address of the sender, the date you received the message, and any other relevant details.
Remember, scammers prey on fear and uncertainty. By taking these immediate steps, you arm yourself with knowledge and support from authorities, greatly reducing the potential impact of the scam. Stay informed, and you’ll find yourself much safer in the digital environment.
For individuals concerned about potential malware or spyware on their devices, security software like SpyHunter can offer peace of mind. SpyHunter is engineered to detect and remove malware, providing real-time defense against a variety of threats. Its user-friendly interface makes safeguarding your digital privacy straightforward and effective, ensuring your device remains protected against the latest malware threats.
The Role of SpyHunter in Protecting Against Email Scams
Email scams have become a sophisticated threat, preying on both individuals and businesses with deceptive messages that can lead to identity theft, financial loss, and malware infections. Amidst this landscape, SpyHunter emerges as a pivotal defense mechanism, offering both detection and removal capabilities that are critical in safeguarding users’ digital environments. By focusing on the latest malware threats, including those propagated through email scams, SpyHunter ensures that users have an advanced layer of protection that adapts to the dynamic nature of cyber threats.
How SpyHunter Can Aid in Detecting and Removing Threats Related to Email Scams
SpyHunter is designed with the end-user in mind, featuring a user-friendly interface that simplifies the process of detecting and eliminating malware. Here’s how SpyHunter excels in dealing with email scam threats:
- Advanced Malware Detection: Utilizing a robust scanning engine, SpyHunter can identify malware signatures and anomalies associated with email scams, including phishing attempts and malicious attachments.
- Regular Updates: To combat the constantly evolving nature of malware, SpyHunter’s malware definition database is regularly updated. This ensures the software can recognize and mitigate even the newest threats.
- Custom Malware Fixes: In cases where SpyHunter encounters unknown or stubborn malware, it offers a custom fix solution. Users can submit a support ticket, and SpyHunter’s technicians will provide a personalized remedy tailored to their specific situation.
- User-Friendly Removal: Once threats are identified, SpyHunter facilitates their easy removal. This is particularly important for users who may not have extensive technical knowledge but need effective solutions against sophisticated email scams.
By melding these features, SpyHunter acts as a formidable barrier between email scam threats and the user’s digital life, offering peace of mind in the ever-risky online world.
Setting Up SpyHunter: A Step-by-Step Guide to Enhance Your Email Security
Securing your digital communications from email scams is straightforward with SpyHunter. Here’s a simple guide to enhancing your email security:
- Download and Install SpyHunter: Visit the official SpyHunter website and download the software. Follow the installation instructions to set it up on your system.
- Run a System Scan: Open SpyHunter and initiate a full system scan. This will allow the software to search your computer for any existing threats, including those related to email scams.
- Review Scan Results: Once the scan is complete, review the findings. SpyHunter will list identified threats and provide an option to remove them from your computer.
- Activate Real-time Protection: Enable SpyHunter’s real-time protection feature. This will guard your system against threats as they appear, preventing email scams from taking root in your system.
- Set Regular Scan Schedules: Schedule regular scans with SpyHunter to ensure continuous protection. Regular scans help catch and mitigate threats that may slip through the cracks.
By following these steps, you can bolster your defense against the threat of email scams and maintain a secure and healthy digital environment. Remember, staying proactive about your cybersecurity measures is key to preventing the potentially devastating impacts of email scams.
Recovering From the Pegasus Email Scam: Essential Steps
Falling victim to a scam can feel both frightening and overwhelming. However, recovering from the “Have You Heard of Pegasus?” email scam involves clear, decisive actions to safeguard your digital life. Taking these steps not only helps in mitigating potential damage but also empowers you to regain control over your online presence.
Securing Your Accounts After a Scam: Changing Passwords and More
In the wake of experiencing a scam, your immediate focus should be on securing your online accounts. Here’s how:
- Change Your Passwords: Start with your most sensitive accounts, such as your email, banking, and social media accounts. Select strong, unique passwords for each to thwart unauthorized access. Avoid common words or sequences that can be easily guessed.
- Enable Two-Factor Authentication (2FA): Adding an extra layer of security, 2FA requires a second form of verification besides your password, like a code sent to your phone. This significantly reduces the chances of unauthorized access.
- Review Account Activities: Check for any unauthorized transactions or changes. If you notice anything suspicious, report it immediately to the service provider.
- Security Questions: Update your security questions and answers. Choose questions and answers that are not easily guessable by someone who might know you or could find information about you online.
Implementing these steps helps shield your accounts from further risk and is crucial for your online security.
Monitoring for Identity Theft and Financial Fraud Post-Scam
After being targeted by a scam, it’s vital to stay vigilant against identity theft and financial fraud:
- Monitor Your Financial Statements: Keep a close eye on your bank statements, credit card statements, and any other financial accounts for unauthorized transactions. Early detection can prevent significant financial loss.
- Check Your Credit Report: Regularly reviewing your credit report can help you spot signs of identity theft early. Look for inquiries or accounts you didn’t initiate.
- Set Up Alerts: Many financial institutions offer free monitoring services that alert you to any unusual activity within your accounts. These alerts can be a first line of defense against fraud.
- Contact Authorities: If you suspect that your information has been misused, report it to your local law enforcement and consider filing a report with relevant financial protection agencies.
Staying proactive with these monitoring efforts can make a big difference in protecting yourself from the long-term effects of identity theft and financial fraud. In the unfortunate event of malware suspicion or the need to enhance your digital security, SpyHunter’s malware remediation utility can serve as a robust solution, offering comprehensive scanning and protection tools designed to identify and remove threats, ensuring your digital environment remains secure.
Remember, the key to overcoming the effects of a scam lies in immediate action and the continuous maintenance of your digital hygiene. By following these simple steps, you can significantly reduce the risk of further damage and secure your online presence against future threats.
Preventing Future Scams: Tips and Best Practices
In today’s dynamic digital era, protecting oneself from scams demands both proactive measures and an informed mindset. By understanding the various tactics scammers employ and how to effectively counter them, individuals can significantly enhance their online security and resilience against fraudulent activities. The essence of scam prevention lies in adopting a comprehensive approach that combines safeguarding personal information with continuously educating oneself about the evolving nature of threats. Below are actionable tips and best practices formulated to fortify your defenses against potential scams.
Enhancing Your Email Security: Practical Tips
Email has become an essential communication tool, but it’s also a common vector for scams and phishing attempts. To safeguard your inbox from malicious activities, start with simple yet effective steps that bolster your email security. Creating unique, complex passwords for each of your accounts dramatically reduces the risk of unauthorized access. Utilize password managers to generate and store passwords, ensuring they are not easily decipherable. Enable two-factor authentication (2FA) wherever possible, adding an additional layer of security beyond just the password. This step significantly hampers a hacker’s ability to gain access to your account, even if they manage to decipher your password.
It’s crucial to exercise caution with every link and attachment received via email, even from known contacts. Cybercriminals often disguise themselves as trustworthy sources. Verify the sender’s credibility by double-checking their email address against known addresses; a slight modification in the address is a common tactic used by scammers. Never click on any links or download attachments from suspicious or unexpected emails. When in doubt, directly contact the sender through another communication method to confirm the authenticity of their message.
Finally, leverage technology to your advantage by using reputable email filtering and anti-malware tools. These solutions can significantly reduce the number of phishing emails that reach your inbox and provide an added security layer by scanning for known threats. SpyHunter’s email scanning feature, for instance, offers robust protection against malware and phishing attempts, ensuring your digital safety.
Educational Resources on Email Scams
Staying informed about the latest email scam techniques and trends is pivotal in maintaining a secure online presence. A wealth of resources is available, designed to enhance your understanding and help you stay one step ahead of cybercriminals. Official government websites, cybersecurity news portals, and consumer protection organizations frequently update their content with valuable information on recognizing and avoiding new scams.
Engaging with online forums and cybersecurity communities can also provide insights into recent scam operations and prevention strategies. These platforms allow individuals to share experiences and advice, fostering a collective defense against online threats.
Moreover, consider subscribing to newsletters from trusted cybersecurity experts and organizations. These subscriptions can serve as a continuous source of up-to-date information, directly delivered to your inbox. By dedicating a few minutes each week to reading these updates, you can significantly enhance your ability to spot and avoid email scams.
Educational workshops and webinars are another excellent way to deepen your knowledge on cybersecurity. Many organizations offer free sessions that cover various topics, from email and internet security to advanced protective measures for your digital life. Participation in these educational avenues equips you with the knowledge to better protect your personal information and devices from emerging cyber threats.
In summary, preventing email scams and enhancing your online security require a blend of technological tools, such as SpyHunter, and an ongoing commitment to education and vigilance. By staying informed and adopting robust security practices, you can significantly reduce your risk of falling victim to email scams and other digital threats.
What Should You Know About Email Scams?
Email scams are a common threat in the online world, employing various tactics to deceive individuals and exploit their information for malicious purposes. Understanding these scams is your first line of defense against becoming a victim. Below are some of the most frequently asked questions related to email scams, with clear and straightforward answers for easy comprehension.
What Makes the Pegasus Email Scam Different from Others?
The Pegasus email scam distinguishes itself through its use of intimidation, leveraging the notoriety of the actual Pegasus spyware’s highly sophisticated software known for its capabilities to infiltrate mobile devices without user interaction. Scammers deploy fear tactics, falsely claiming they’ve installed Pegasus on the recipient’s device to spy on them or harvest sensitive information. Unlike traditional scams that might ask for personal details directly, this strategy involves coercing victims into paying a ransom to “remove” the threat. It’s crucial to remember that these claims are entirely unfounded, and acknowledging the deceit can prevent potential financial loss.
Can Email Scams Lead to Malware Infections?
Yes, email scams can indeed lead to malware infections. Cybercriminals frequently embed malicious links or attachments in their messages, which, when clicked or opened, can install malware on your device. This malware can range from ransomware, which locks you out of your data until a ransom is paid, to spyware, designed to stealthily monitor and report back your activities. Preventative measures include avoiding suspicious emails, especially those that you weren’t expecting, and not interacting with their contents (links or attachments). Additionally, maintaining updated security software on your device offers another layer of protection against such threats.
Why is it Important to Use Security Software like SpyHunter?
Using reliable security software, like SpyHunter, plays a pivotal role in defending against the pervasive threat of email scams and the potential malware they may carry. SpyHunter is engineered to detect and remove a vast array of malware, from the deeply hidden to the more commonly encountered varieties. Its importance cannot be overstated for several reasons:
- Real-time Protection: It offers continuous monitoring and protection against new and emerging threats, acting as a vigilant guard for your digital safety.
- Comprehensive Removal: Unlike some basic defenses, SpyHunter can root out complex malware strains that burrow deep into your system, ensuring a thorough cleanse.
- User-friendly: Designed with simplicity in mind, it’s accessible to users of all technical levels, making strong cybersecurity attainable for everybody.
- Regular Updates: To counter the constantly evolving landscape of cyber threats, Spy Pluto is regularly updated, ensuring its defense mechanisms are up to the task.
In the context of email scams, having SpyHunter at your disposal ensures that even if you accidentally engage with a malicious email, the threat can be swiftly identified and dealt with before causing significant harm to your system or privacy.
Key Takeaways on Staying Safe from the Pegasus Email Scam
The “Have you heard of Pegasus?” email scam represents a modern twist on cyber extortion, leveraging the fear of privacy invasion to manipulate its victims. Understanding the scam’s nature and how to protect yourself is crucial. Here’s what you need to keep in mind:
- Recognize the Scam: First and foremost, know that these emails play on the fear of having your most private moments exposed. Remember, the threats are scare tactics with no truth behind them. The detailed claims about accessing your device using Pegasus malware are entirely fabricated.
- Do Not Engage: If you receive such an email, do not respond, open any attachments, or pay the ransom. Responding only signals to the scammer that you’re receptive, which could lead to more targeted threats.
- Report Immediately: Help prevent the spread of this malicious activity by reporting it. Alert authorities through platforms like ic3.gov and reportfraud.ftc.gov. Reporting can assist in tracking down the perpetrators and preventing future scams.
- Strengthen Your Defenses: Change your online account passwords immediately after detecting a scam attempt. Opt for complex, unique passwords for each account and enable two-factor authentication (2FA) where available.
- Stay Calm and Informed: It’s essential to remain calm and rational. Understand that millions are targeted by scam emails daily, and you’re not alone. Most importantly, no compromising videos or data have been acquired by the scammers.
- Maintain Vigilance: Always exercise caution when handling emails, especially those from unknown sources. Avoid opening suspicious emails or clicking on any links and attachments they contain.
- Deploy Anti-Malware Protection: Ensure your devices are protected with reliable security software to detect and remove potential threats. Regular system scans are vital for maintaining cybersecurity. For those seeking a robust solution, SpyHunter is a dependable option for removing malware and enhancing your device’s security.
By following these straightforward yet effective steps, you can safeguard your digital life against the “Have you heard of Pegasus?” email scam and similar cyber threats. Knowledge is power – equip yourself with it and reduce your vulnerability to online scams. Remember, the goal of these scammers is to exploit fear and uncertainty; standing informed and cautious dismantles their strategy, keeping you and your private data safe.
- Windows
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
- Internet Explorer
- Stop Push Pop-ups
How to Remove Pegasus Email Scam from Windows.
Step 1: Scan for Pegasus Email Scam with SpyHunter Anti-Malware Tool



Step 2: Boot Your PC In Safe Mode





Step 3: Uninstall Pegasus Email Scam and related software from Windows
Uninstall Steps for Windows 11
Uninstall Steps for Windows 10 and Older Versions
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully uninstall most programs.
Follow the instructions above and you will successfully uninstall most programs.
Step 4: Clean Any registries, Created by Pegasus Email Scam on Your PC.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Pegasus Email Scam there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Video Removal Guide for Pegasus Email Scam (Windows).
Get rid of Pegasus Email Scam from Mac OS X.
Step 1: Uninstall Pegasus Email Scam and remove related files and objects
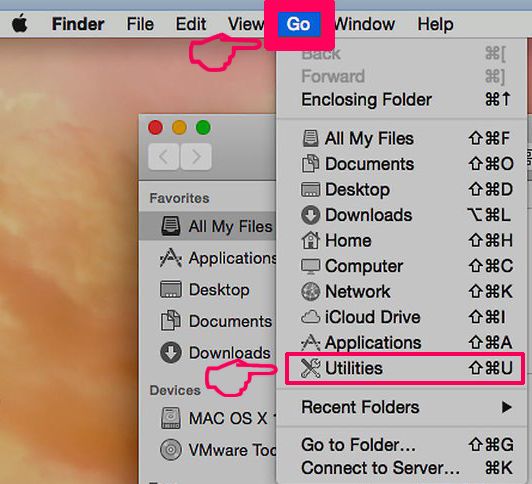
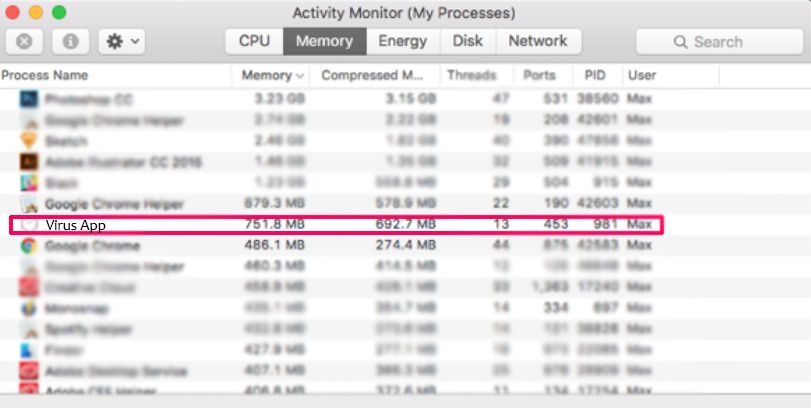
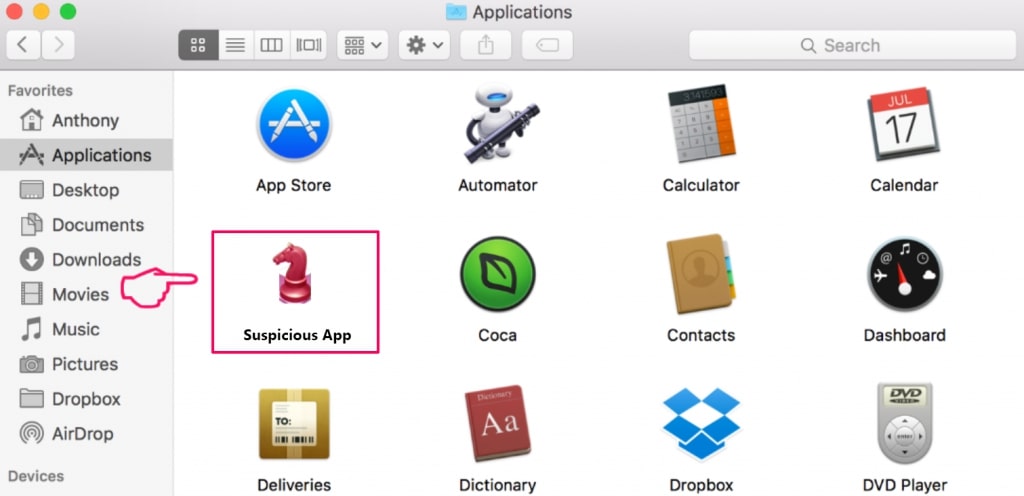
Your Mac will then show you a list of items that start automatically when you log in. Look for any suspicious apps identical or similar to Pegasus Email Scam. Check the app you want to stop from running automatically and then select on the Minus (“-“) icon to hide it.
- Go to Finder.
- In the search bar type the name of the app that you want to remove.
- Above the search bar change the two drop down menus to “System Files” and “Are Included” so that you can see all of the files associated with the application you want to remove. Bear in mind that some of the files may not be related to the app so be very careful which files you delete.
- If all of the files are related, hold the ⌘+A buttons to select them and then drive them to “Trash”.
In case you cannot remove Pegasus Email Scam via Step 1 above:
In case you cannot find the virus files and objects in your Applications or other places we have shown above, you can manually look for them in the Libraries of your Mac. But before doing this, please read the disclaimer below:
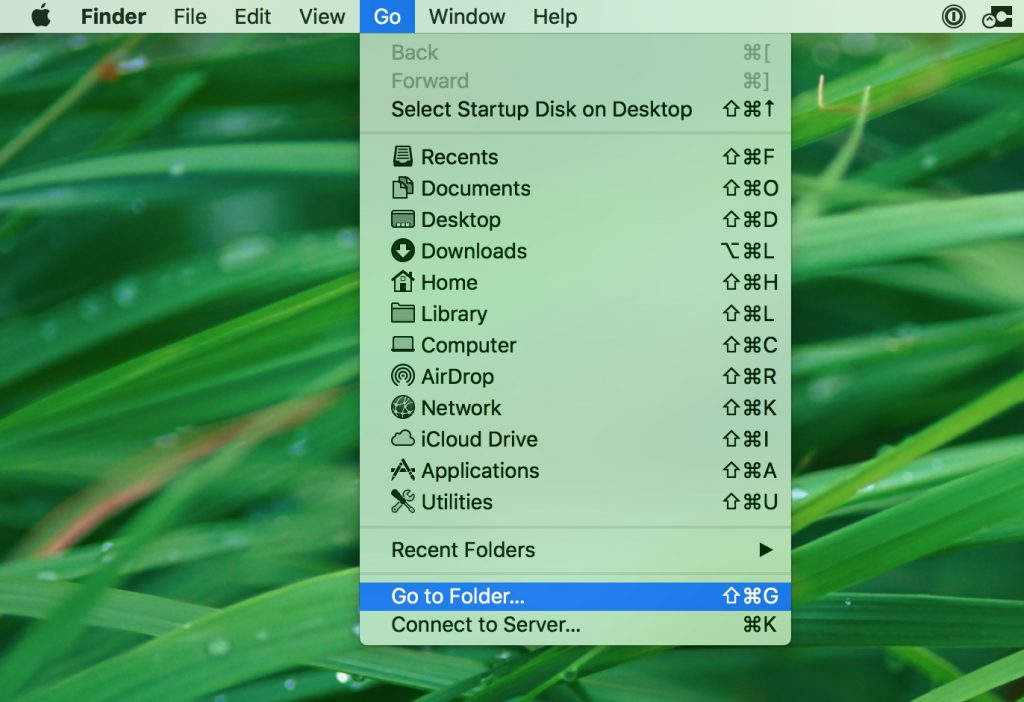
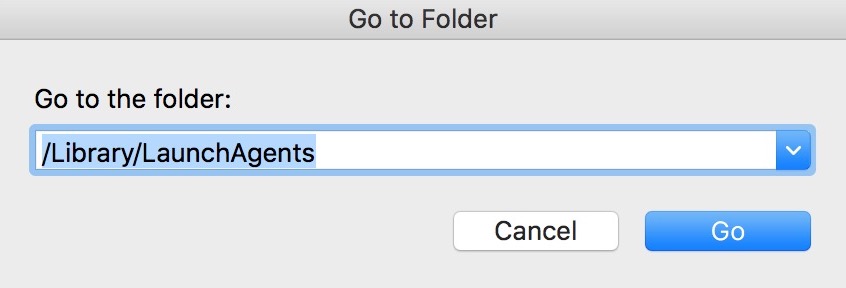
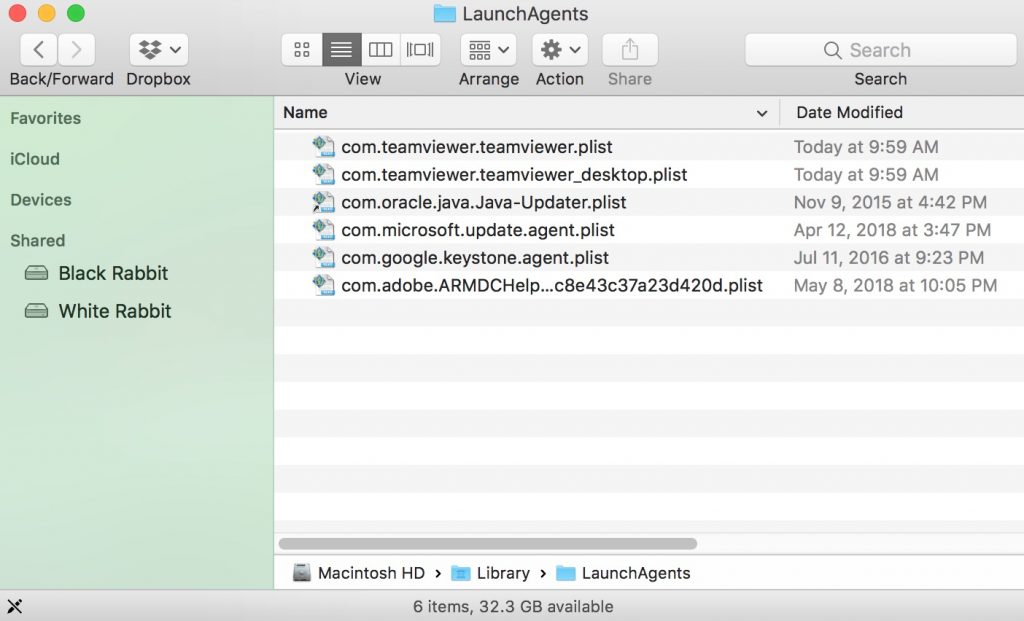
You can repeat the same procedure with the following other Library directories:
→ ~/Library/LaunchAgents
/Library/LaunchDaemons
Tip: ~ is there on purpose, because it leads to more LaunchAgents.
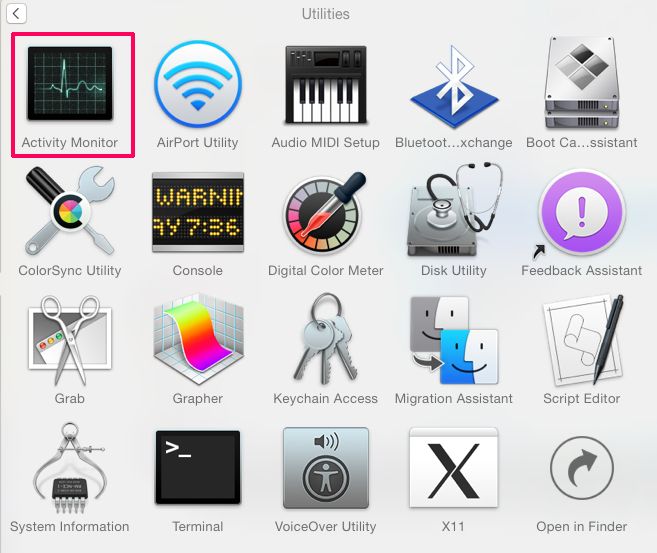
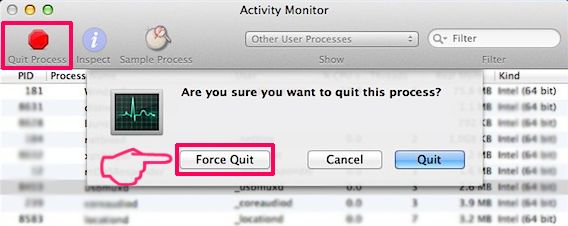
Step 2: Scan for and remove Pegasus Email Scam files from your Mac
When you are facing problems on your Mac as a result of unwanted scripts and programs such as Pegasus Email Scam, the recommended way of eliminating the threat is by using an anti-malware program. SpyHunter for Mac offers advanced security features along with other modules that will improve your Mac’s security and protect it in the future.
Video Removal Guide for Pegasus Email Scam (Mac)
Remove Pegasus Email Scam from Google Chrome.
Step 1: Start Google Chrome and open the drop menu
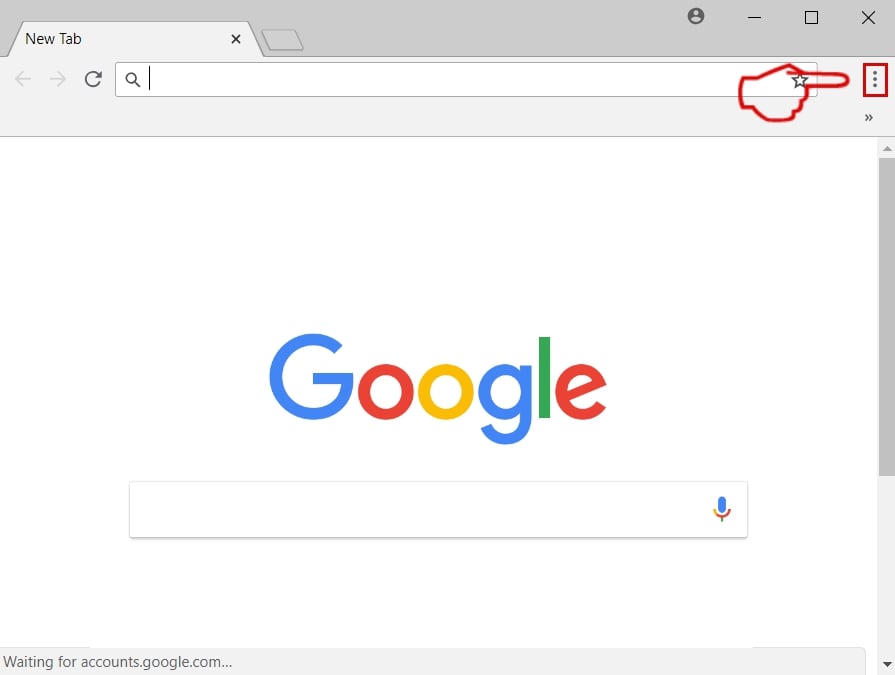
Step 2: Move the cursor over "Tools" and then from the extended menu choose "Extensions"
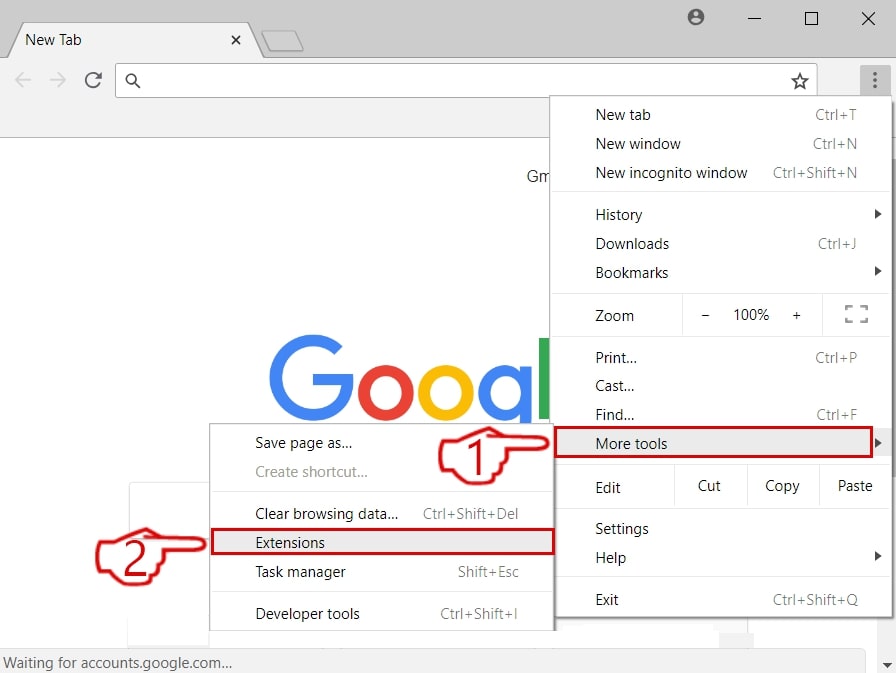
Step 3: From the opened "Extensions" menu locate the unwanted extension and click on its "Remove" button.
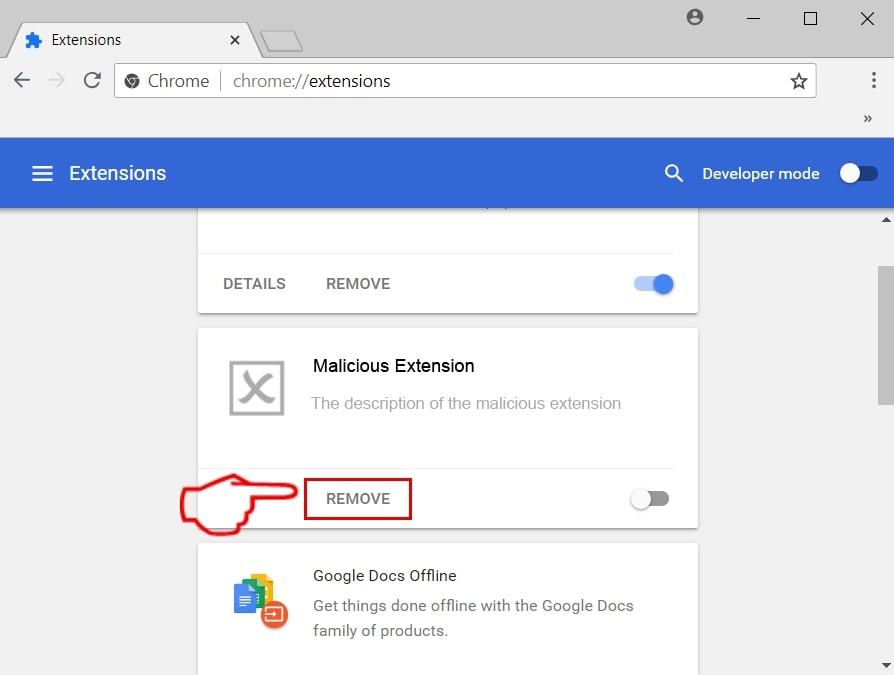
Step 4: After the extension is removed, restart Google Chrome by closing it from the red "X" button at the top right corner and start it again.
Erase Pegasus Email Scam from Mozilla Firefox.
Step 1: Start Mozilla Firefox. Open the menu window:
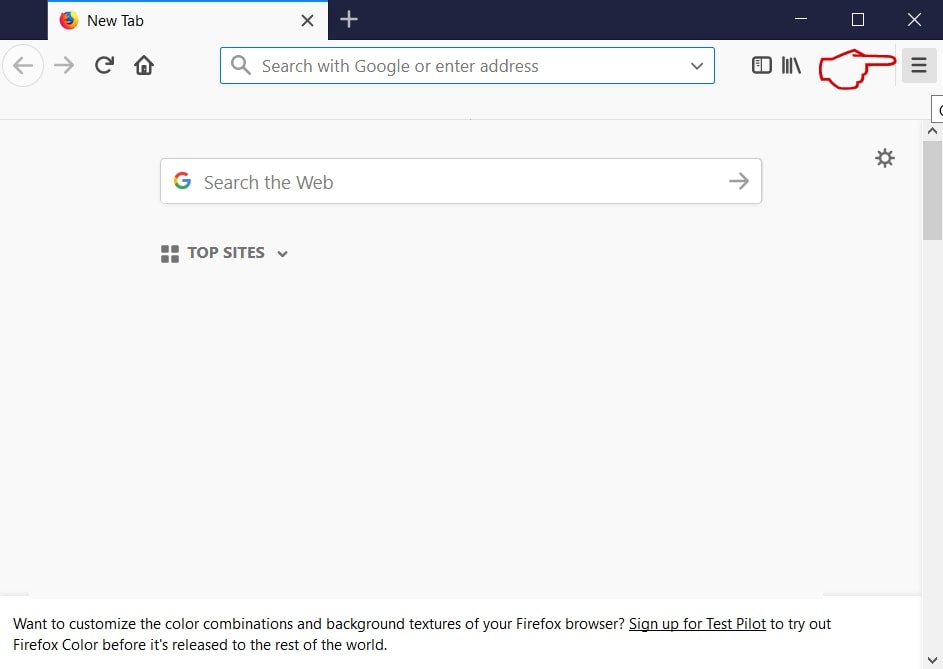
Step 2: Select the "Add-ons" icon from the menu.
Step 3: Select the unwanted extension and click "Remove"

Step 4: After the extension is removed, restart Mozilla Firefox by closing it from the red "X" button at the top right corner and start it again.
Uninstall Pegasus Email Scam from Microsoft Edge.
Step 1: Start Edge browser.
Step 2: Open the drop menu by clicking on the icon at the top right corner.
Step 3: From the drop menu select "Extensions".
Step 4: Choose the suspected malicious extension you want to remove and then click on the gear icon.
Step 5: Remove the malicious extension by scrolling down and then clicking on Uninstall.
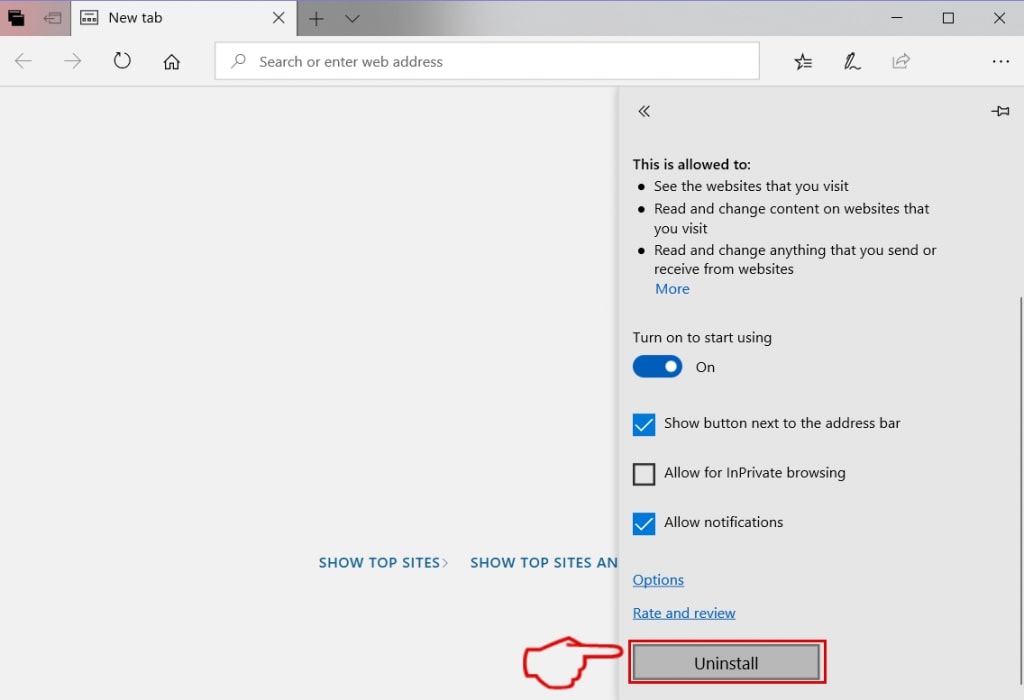
Remove Pegasus Email Scam from Safari
Step 1: Start the Safari app.
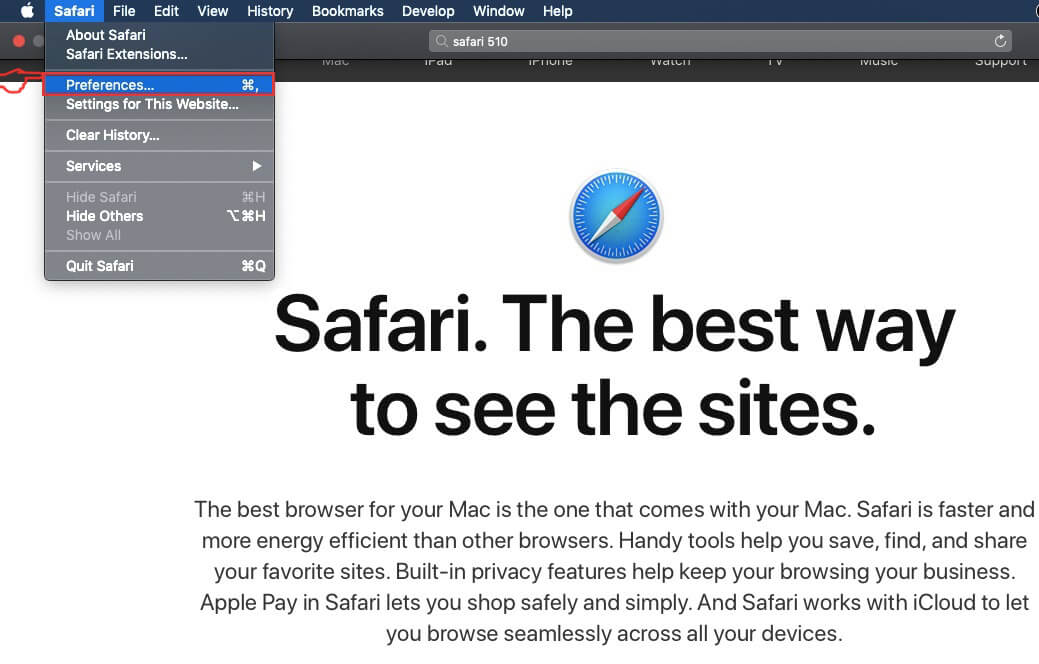
Step 2: After hovering your mouse cursor to the top of the screen, click on the Safari text to open its drop down menu.
Step 3: From the menu, click on "Preferences".
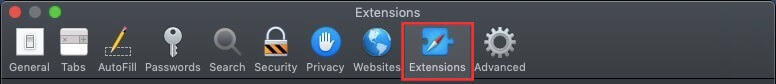
Step 4: After that, select the 'Extensions' Tab.
Step 5: Click once on the extension you want to remove.
Step 6: Click 'Uninstall'.
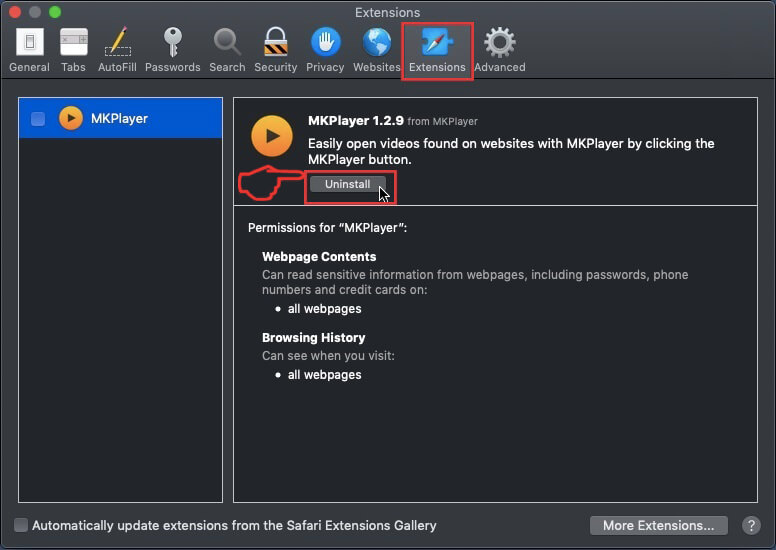
A pop-up window will appear asking for confirmation to uninstall the extension. Select 'Uninstall' again, and the Pegasus Email Scam will be removed.
Eliminate Pegasus Email Scam from Internet Explorer.
Step 1: Start Internet Explorer.
Step 2: Click on the gear icon labeled 'Tools' to open the drop menu and select 'Manage Add-ons'
Step 3: In the 'Manage Add-ons' window.
Step 4: Select the extension you want to remove and then click 'Disable'. A pop-up window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be disabled as well. Leave all the boxes checked, and click 'Disable'.
Step 5: After the unwanted extension has been removed, restart Internet Explorer by closing it from the red 'X' button located at the top right corner and start it again.
Remove Push Notifications from Your Browsers
Turn Off Push Notifications from Google Chrome
To disable any Push Notices from Google Chrome browser, please follow the steps below:
Step 1: Go to Settings in Chrome.
Step 2: In Settings, select “Advanced Settings”:
Step 3: Click “Content Settings”:
Step 4: Open “Notifications”:
Step 5: Click the three dots and choose Block, Edit or Remove options:

Remove Push Notifications on Firefox
Step 1: Go to Firefox Options.
Step 2: Go to “Settings”, type “notifications” in the search bar and click "Settings":
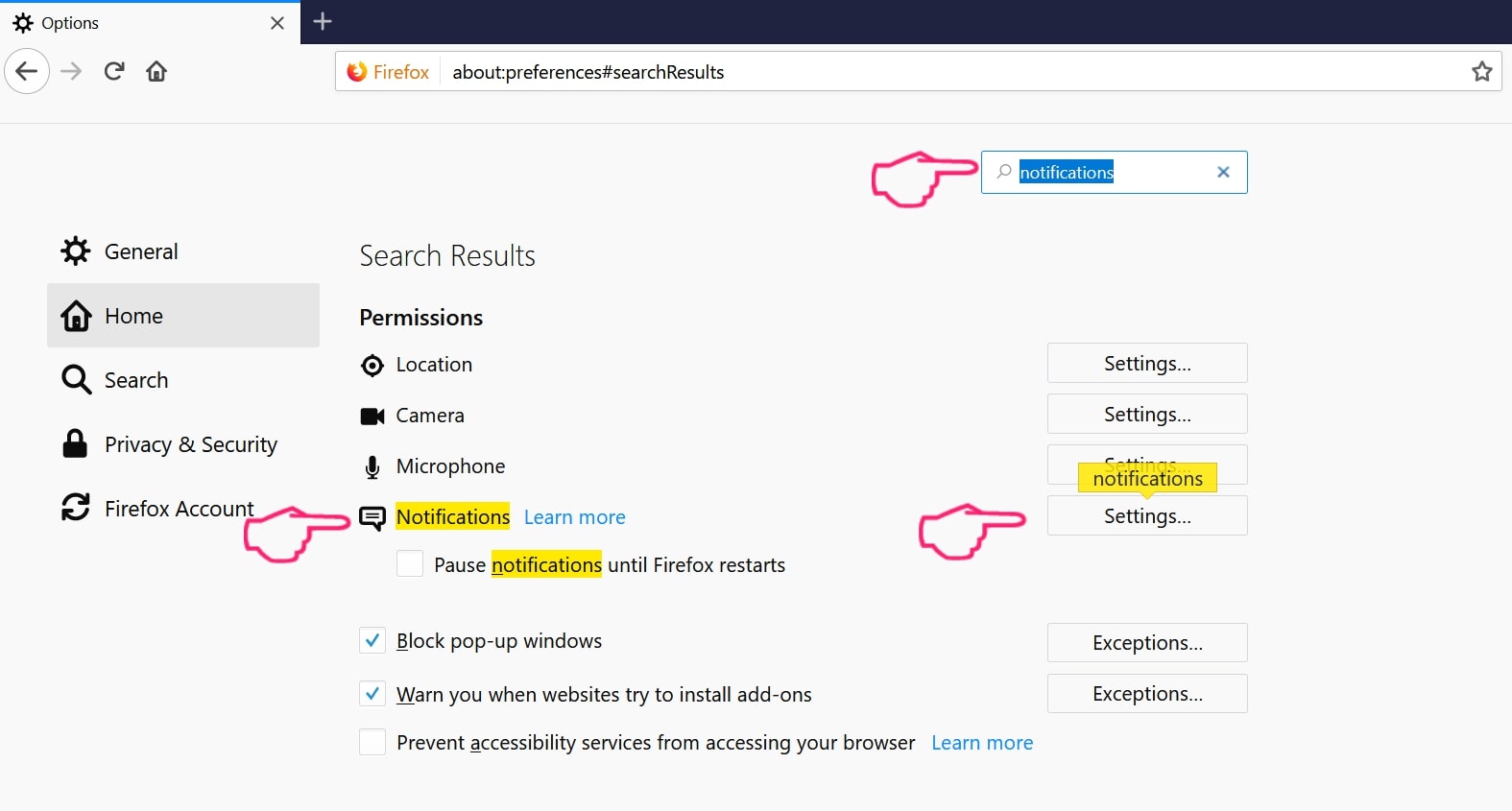
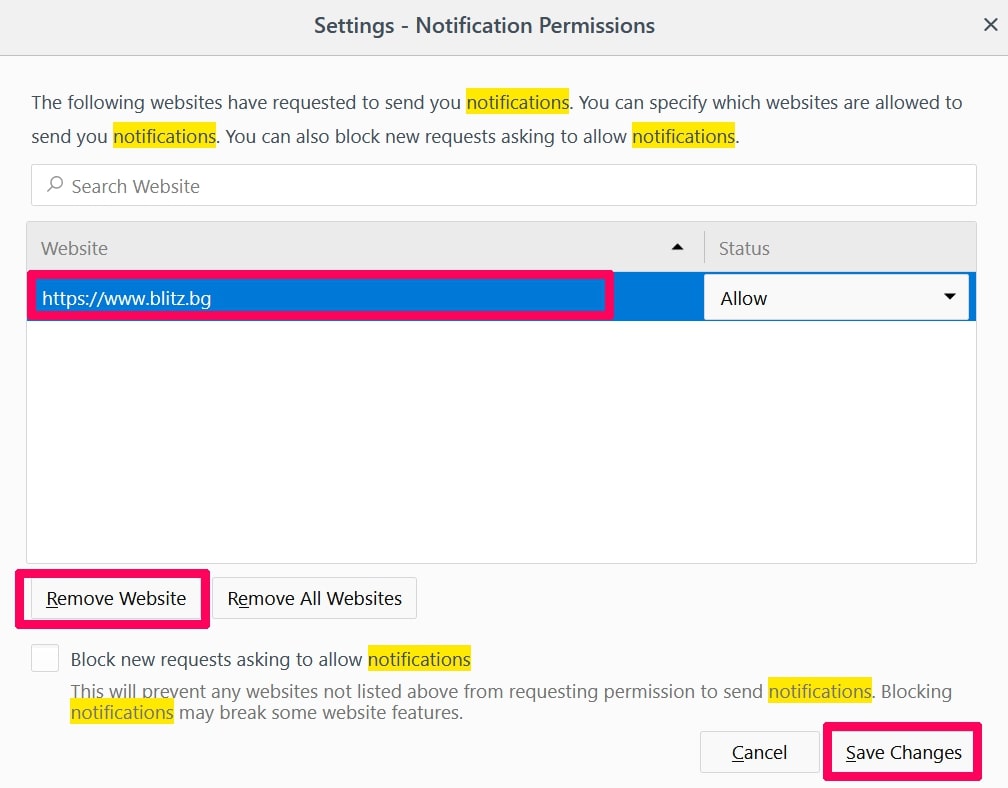
Step 3: Click “Remove” on any site you wish notifications gone and click “Save Changes”
Stop Push Notifications on Opera
Step 1: In Opera, press ALT+P to go to Settings.
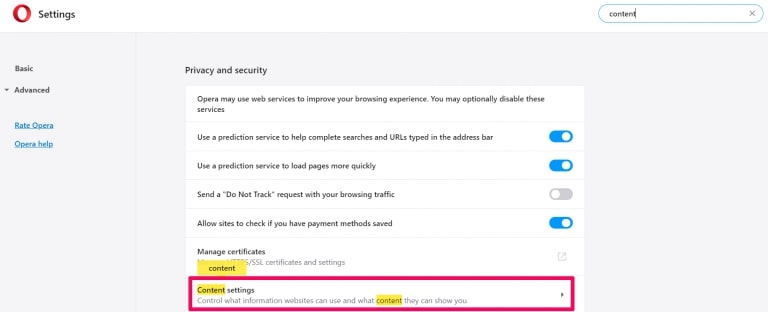
Step 2: In Setting search, type “Content” to go to Content Settings.
Step 3: Open Notifications:
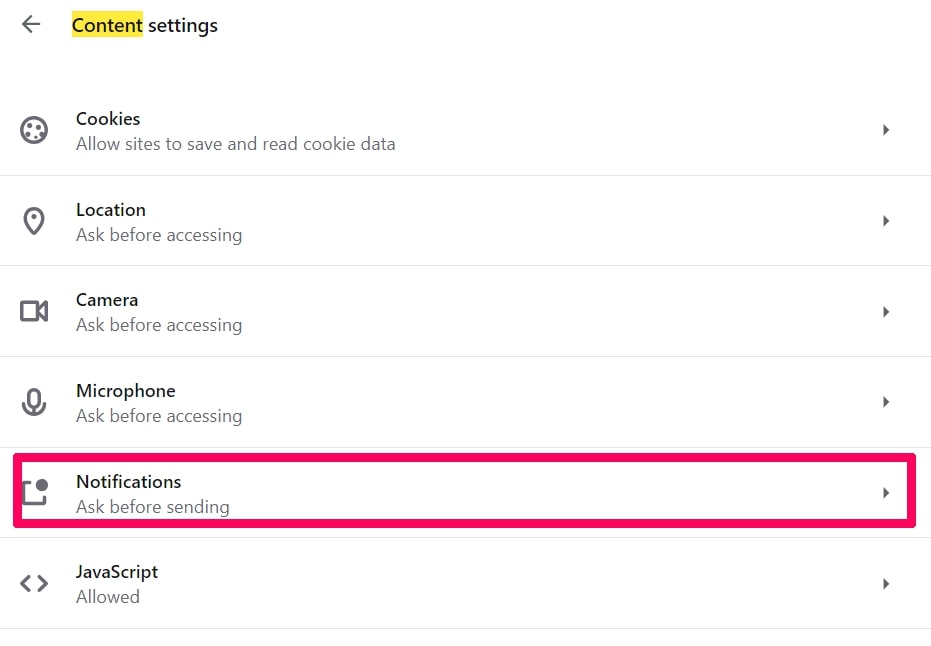
Step 4: Do the same as you did with Google Chrome (explained below):
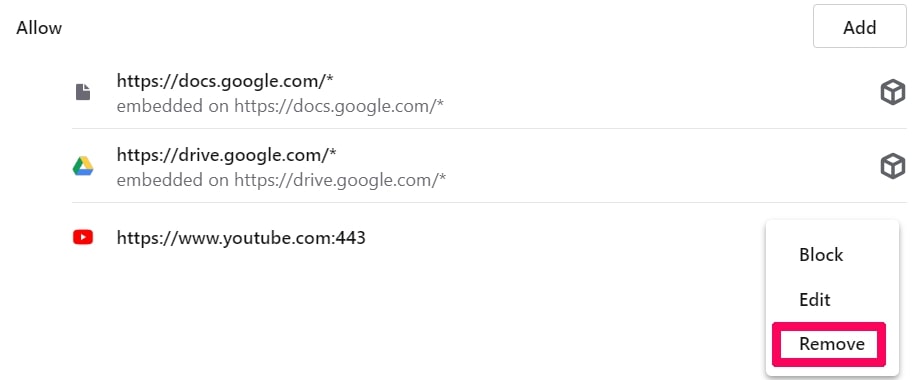
Eliminate Push Notifications on Safari
Step 1: Open Safari Preferences.
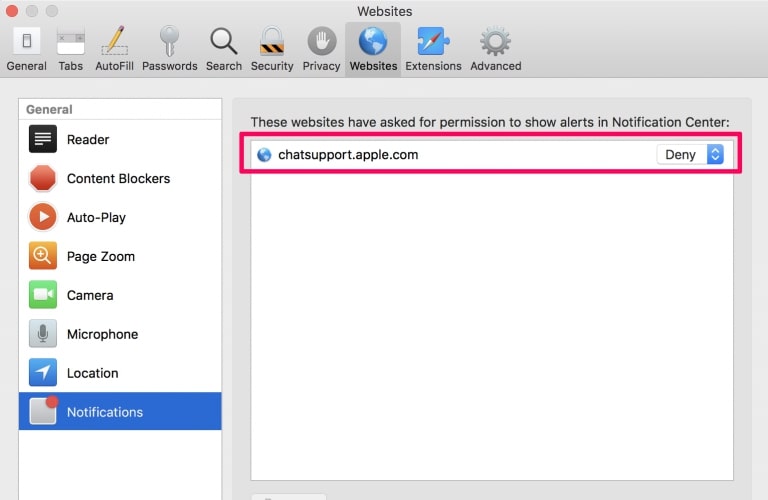
Step 2: Choose the domain from where you like push pop-ups gone and change to "Deny" from "Allow".
Pegasus Email Scam-FAQ
What Is Pegasus Email Scam?
The Pegasus Email Scam threat is adware or browser redirect virus.
It may slow your computer down significantly and display advertisements. The main idea is for your information to likely get stolen or more ads to appear on your device.
The creators of such unwanted apps work with pay-per-click schemes to get your computer to visit risky or different types of websites that may generate them funds. This is why they do not even care what types of websites show up on the ads. This makes their unwanted software indirectly risky for your OS.
What Are the Symptoms of Pegasus Email Scam?
There are several symptoms to look for when this particular threat and also unwanted apps in general are active:
Symptom #1: Your computer may become slow and have poor performance in general.
Symptom #2: You have toolbars, add-ons or extensions on your web browsers that you don't remember adding.
Symptom #3: You see all types of ads, like ad-supported search results, pop-ups and redirects to randomly appear.
Symptom #4: You see installed apps on your Mac running automatically and you do not remember installing them.
Symptom #5: You see suspicious processes running in your Task Manager.
If you see one or more of those symptoms, then security experts recommend that you check your computer for viruses.
What Types of Unwanted Programs Are There?
According to most malware researchers and cyber-security experts, the threats that can currently affect your device can be rogue antivirus software, adware, browser hijackers, clickers, fake optimizers and any forms of PUPs.
What to Do If I Have a "virus" like Pegasus Email Scam?
With few simple actions. First and foremost, it is imperative that you follow these steps:
Step 1: Find a safe computer and connect it to another network, not the one that your Mac was infected in.
Step 2: Change all of your passwords, starting from your email passwords.
Step 3: Enable two-factor authentication for protection of your important accounts.
Step 4: Call your bank to change your credit card details (secret code, etc.) if you have saved your credit card for online shopping or have done online activities with your card.
Step 5: Make sure to call your ISP (Internet provider or carrier) and ask them to change your IP address.
Step 6: Change your Wi-Fi password.
Step 7: (Optional): Make sure to scan all of the devices connected to your network for viruses and repeat these steps for them if they are affected.
Step 8: Install anti-malware software with real-time protection on every device you have.
Step 9: Try not to download software from sites you know nothing about and stay away from low-reputation websites in general.
If you follow these recommendations, your network and all devices will become significantly more secure against any threats or information invasive software and be virus free and protected in the future too.
How Does Pegasus Email Scam Work?
Once installed, Pegasus Email Scam can collect data using trackers. This data is about your web browsing habits, such as the websites you visit and the search terms you use. It is then used to target you with ads or to sell your information to third parties.
Pegasus Email Scam can also download other malicious software onto your computer, such as viruses and spyware, which can be used to steal your personal information and show risky ads, that may redirect to virus sites or scams.
Is Pegasus Email Scam Malware?
The truth is that PUPs (adware, browser hijackers) are not viruses, but may be just as dangerous since they may show you and redirect you to malware websites and scam pages.
Many security experts classify potentially unwanted programs as malware. This is because of the unwanted effects that PUPs can cause, such as displaying intrusive ads and collecting user data without the user’s knowledge or consent.
About the Pegasus Email Scam Research
The content we publish on SensorsTechForum.com, this Pegasus Email Scam how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific, adware-related problem, and restore your browser and computer system.
How did we conduct the research on Pegasus Email Scam?
Please note that our research is based on independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware, adware, and browser hijacker definitions.
Furthermore, the research behind the Pegasus Email Scam threat is backed with VirusTotal.
To better understand this online threat, please refer to the following articles which provide knowledgeable details.


