What Can Hackers Do If You Have an Insecure Connection?
The fear of hackers exists because that is a legitimate threat. There are different hackers out there, but your biggest concern should be black-hat hackers. Black hats break into networks with a malicious intent, and more specifically, to destroy, modify, or steal data, or to make the networks unusable. Thus, you would not want to send any kind of information or credentials over an unsecure network.
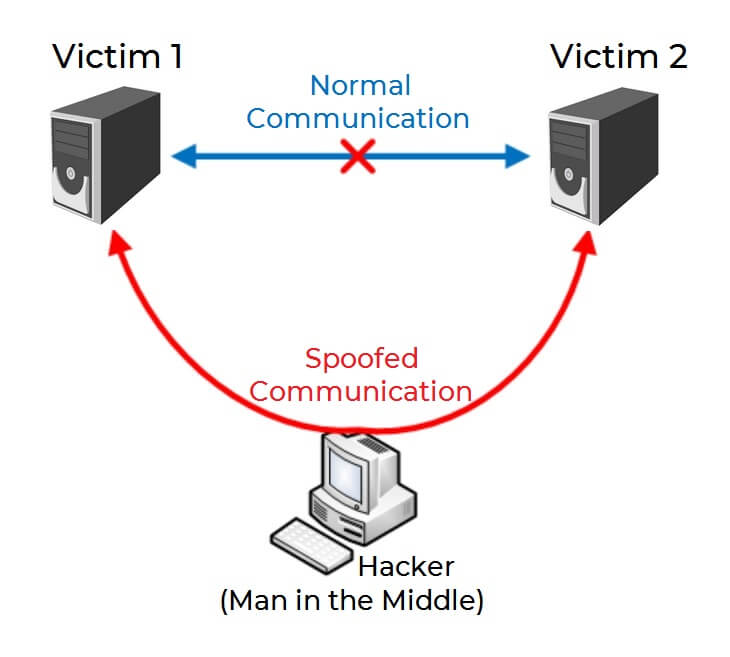
The term “black hat” can also be applied loosely to a person tampering with communications between people for malicious reasons. Performing such an attack is known as a man-in-the-middle attack (MITM), which is sometimes referenced as fire brigade attack, eavesdropping attack, or connection hijacking attack. There are tools that can sniff data over a network if they are previously set up for that cause. The result is that the communication between two or more Internet users becomes spoofed.
Technically speaking, exploiting inherent vulnerabilities of the TCP/IP protocol at different layers can make a MITM attack possible. A more professional man-in-the-middle attack would involve the interception of traffic, breaking the authentication chain, and impersonating the hacked endpoints seamlessly. The main goal is to steal the session, and thus the information being transmitted over the wire.
The TCP/IP protocol works on a three way handshake (SYN, SYN-ACK, ACK). The handshake establishes a connection between two different network interface cards, which use a packet sequence and data acknowledgement to both receive and send data. The information flows from the physical layer to the application layer (the application layer being mostly the web browser). At layer 2 and layer 3 of the OSI model, an Ethernet and IP packet datagram are formed, whereas at the presentation layer, the cryptographic SSL session is established assuming. Any of these layers can potentially be involved in a MITM attack.
To be put simply, the whole concept of a man-in-the-middle attack is when a communication between two computer systems is intercepted by a third party entity. That third party, or the man in the middle, receives the message intended for the second person in the conversation then the hacker manipulates it, so a modified message is received instead. It is made in such a way that the two parties in the conversation do not know about the spoofed communication and they end up sharing valuable information along the way. You can see a visual example on the sketch showcased above.
To perform a man-in-the-middle (MITM) attack, a hacker does not need to do much. Multiple hacking tools are available online for a cheap price. There are multiple types of man-in-the-middle attacks as listed below:
- IP spoofing
- DNS spoofing
- HTTPS spoofing
- SSL hijacking
- Email hijacking
- Wi-Fi eavesdropping
- Stealing browser cookies
The methodology of spoofing a communication does not differ much, but the entry point is what distinguishes these sub-types of MITM attacks. Later in the article, we will provide you with a few simple steps to follow in order to prevent most of these attacks.
How Can You Prevent Hacker Attacks With a VPN?
Virtual Private Networks (VPNs) are an effective measure to prevent most hacker attacks, especially all types of man-in-the-middle attacks. VPNs are also used to prevent corporate espionage, as well as achieving communication between employees without fear of hackers. Be aware that free VPN services lack features and have leaks which could lead to all kinds of hacker attacks. Always choose a paid VPN that guarantees to have a DNS leak protection, along with IP protocol leak defense. Also note that, some free VPNs even sell users’ data to third parties, while guaranteeing otherwise.
Preventing middle-man access and sending data via a secure tunnel are fully possible, but a few requirements are necessary to accomplish that. These requirements include a DNS Leak Protection (over IPv4, IPv6 and WebRTC), HTTPS being enforced, encryption on the traffic that goes in and out of the tunnel, and no logging. Big businesses take it a step further and even implement policies preventing employees from having access to master keys used for the decryption process of the channeled data in real time. There are free online tools that can check your VPN service of choice for any leaks of the DNS, IPv4 protocol, IPv6 protocol and WebRTC.
To browse without fear of hackers you have to not only use a paid VPN with all those features and functions available, but set everything up in the correct way and order. You have to first clear all cookies, then install the VPN and set it up so every protection is turned on, and then test for leaks before transferring data or having a conversation with anyone. For more details on how to set up a VPN service and what other steps to make to truly lift your fear of hackers, continue to read below.
How To Set Up a VPN Properly?
In this section of the article, we have prepared a few simple steps, via which you can properly set up any VPN service you want, in order to browse without fear of hackers:
Step 1: Register for a VPN service of your choice, that suits your personal or business needs. A paid VPN service is best, as free VPNs can leak your information to hackers as mentioned earlier.
Step 2: Clear all cookies in your web browsers and disk drives. Delete any browser extensions you consider suspicious. For maximum effectiveness, we recommend that you simply Clear All Browsing Data such as history, cookies, passwords, autofill forms, cache and everything else that accompanies it, from the settings menu.
Step 3: Check the VPN’s settings such as DNS Leak Protection and IPv6 Leak Protection are enabled. Also, check which encryption method you want to use and which security protocol.
Step 4: Launch the VPN server and connect to a location of your choice that is outside your country you reside in currently. Then just wait for the server to connect. You will be notified when the service has assigned your new location and IP address, after you have connected.
What Else To Do for Browsing Without Fear of Hackers?
VPN services are not the sole layer of protection that you need for making your browsing safe from hackers, but it is the most crucial one. Below we have laid several tips and we suggest you to combine all of them to maximize your online security.
Tip 1: Make sure to always use an anti-virus or anti-malware tool that is updated on a regular basis. If the Databases of your preferred security software is updated daily and has an active protection, then that is the best you can have in terms of such a computer program.
Tip 2: Be aware of what type of websites you visit while browsing online. If the website has only HTTP and not HTTPS enabled, then you should know that the site is not encrypted. That way, hackers could access the information you input via the website and track your movements, if they have exploited the HTTP protocol’s vulnerabilities.
Tip 3: Do not type in any personal information on websites that you visit and do not fully trust. Always check a website’s URL to make certain that is the authentic one and not a spoofed copy. There are many phishing pages on the Internet that attempt to steal credentials and other data. Some of them are targeting potential victims by sending fake e-mails or messages over social media.
Tip 4: Always link your cellphone to your sensitive accounts in order to enable another layer of protection. You should always enable two-factor authentication whenever it is made available to you, as that will further boost the level of security of your accounts. Even if your cellphone is out of the equation, there are other methods to set up two-factor authentication – email is one of them.
Tip 5: Enable alerts via phone or email. Receiving notifications whenever your account is accessed by an unknown device or when someone else is logging in to your accounts. This will allow you to react immediately, especially if the notifications are sent to your mobile phone via SMS messaging. Take note, that when you are using a VPN, you might receive such messages constantly, because you are changing your IP address that way. In that case you can enable only the email notifications for certain websites and services.
Disclaimer! Keep in mind, that no VPN service provides complete security and privacy, but just adds one layer of protection in that direction. In addition, a VPN is held by a company. The company may change its policies or provide data to governments if National Security might be at stake. Using a VPN does not deem you free of any rules and regulations – you have to abide by the laws of the country you reside in, the country hosting the VPN service and probably some others. You may not be completely anonymous by simply setting and using a VPN.