Security researchers at Proofpoint recently published “Analysis of a Cybercrime Infrastructure,” where they revealed the Qbot botnet has infected 500,000 systems and sniffed 800,000 banking transactions. 59% of these transactions are from accounts from five of the largest banks in the United States.
The experts have a reason to believe that the cybercrime group is Russian-speaking and apparently targeting mainly US-based banking accounts.
How Qbot botnet works
Proofpoint experts have managed to gain access to the hackers’ network and here’s what they’ve found:
In order to masquerade its presence, Qbot botnet infects the system first and then inserts a load of malware in it. This way, taking control over the infected computer or protecting it becomes nearly impossible.
→Proofpoint has seen that these systems are not only effective, but flexible: because of the use of an emplaced “dropper” rather than a single piece of malware, the compromised computer can be stocked with multiple elements of malware, assisting the malware in avoiding signature detection (if one element is detected, others may not be) as well as in ensuring the compromised system can be used in multiple ways,” the analysis says.
According to the report, the cyber criminals compromised WordPress websites, uploaded malware in them, and when clients visited those websites, they got infected too. Newsletters with infected content distributed by these WordPress websites were also used to spread malware. Thankfully, the report contains instructions for the WordPress users on how to detect infections and protect their websites.
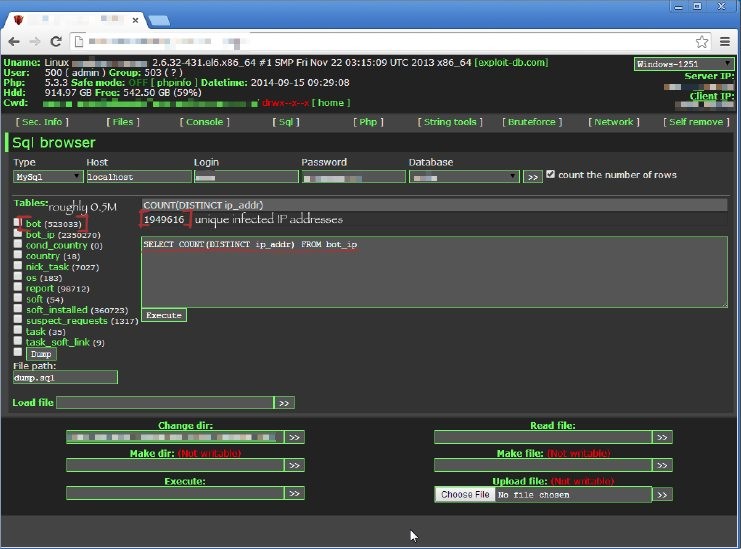
Researchers discovered that at least 520,000 computers were enslaved as the malware used by the hackers generates unique IDs for each infected system. Thus, it is safe to say that gaining control over such an amount of machines via compromised WordPress websites is an elaboration of a huge gang of attackers.
Another intriguing fact about the Qbot botnet is that 52% of the infected systems belong to Windows XP users, and 39% – to Windows 7 users. Apparently, Microsoft has still plenty to work on its security.
The experts were able to determine that the attackers are Russians targeting mainly US banking transactions. The Russians, however, cooperated with other countries like Great Britain, Canada and Italy. The security company is certain that the primary motive of the cyber criminals is purely financial –targeting financial accounts and having a wide range of options to monetize the infected computers.