This article has been created in order to give you insight on how to quickly remove the SearchAwesome Mac Adware from your Mac effectively.
The SearchAwesome Mac Adware is a very dangerous threat to all Mac computers as it can install itself silently and lead to data theft. Active infections can be made without any apparent symptoms and depending on the specific hacker instructions different actions can take place. This is the reason why affected users should remove it immediately.

Threat Summary
| Name | SearchAwesome Mac Adware |
| Type | Mac OS Adware |
| Short Description | The SearchAwesome Mac Adware installs various malware on the target computers. |
| Symptoms | The victims may not experience any apparent signs of infection. |
| Distribution Method | Emails, infected software installers and other methods. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss SearchAwesome Mac Adware. |
SearchAwesome Mac Adware — How Did I Get It
The SearchAwesome Mac Adware is a popular malicious threat which is known to be spread using several different methods. The available research shows that the malicious actors behind it attempt to coerce the targets into installing a setup file that looks like a legitimate app installer.
One of the most common ways to do this is to coordinate email SPAM messages that are sent in bulk to the target recipients. They are usually designed to appear as legitimate notifications or offers sent by well-known companies or services. These setup files may be directly attached or linked in the body contents.
These setup files can also be spread using various malicious payloads, two of the common types are the following:
- Malicious Documents — The operators can use macro-infected documents of all popular types to spread the infections. A virus-infected file can be a rich text document, presentation, database or spreadsheet. When the relevant file is opened a notification prompt will be spawned which will request the user to enable the built-in scripts. If this is done then the virus infection will automatically begin.
- Bundle Installers — The malicious code can be bundled with the installers of popular end-user software: system utilities, creativity suites and productivity applications. Whenever they are installed the virus instance will also be installed.
To further increase the chances of acquiring the infection the criminal operators can construct malicious sites. They can be made to look like an official vendor product image and download portals. The SearchAwesome Mac Adware samples can also be found on file sharing networks. A very popular option is BitTorrent where both legitimate and pirate content can be found.
In advanced cases the hacker operators can also make use of browser hijackers which are often used to spread all kinds of malware. They represent malicious web browser plugins which are uploaded to the official repositories. They are advertised as useful additions and performance optimizations. They are uploaded using fake/stolen user reviews and developer credentials. When the installation is complete the built-in pattern of code will be started.
When the infections are done using the startup file carrying the infection an authorization prompt will be shown. There are two authentication boxes which require the users to enter in their account credentials — Certificate Trust Settings and Network Configuration Modification. This will lead to the second-stage payload delivery script.
SearchAwesome Mac Adware — Full Description
Following the initial deployment the SearchAwesome Mac Adware will install an application and several launch agents. The distinct feature is that during this phase an additional step is made — the installation of a certificate allowing man-in-the-middle attacks. This process allows the malicious operators to spy even on encrypted traffic. A side effect is ability to intercept all kinds of private data: usernames, passwords and etc.
The application that is installed is the open-source software called mitmproxy. This is an utility that is used to intercept, inspect, modify and replay web traffic. When this is combined with the certificate this also allows the manipulation of encrypted traffic.
Another side effect of the SearchAwesome Mac Adware is the injection of JavaScript code into all loaded pages. This can result in the ability to load various malware. A sample list includes the following:
- Intrusive Ads — The SearchAwesome Mac Adware in most cases is used to load intrusive ads in the form of pop-ups, banners and redirects. They display sponsored content, every click made by the user leads to profit generation for the malicious operators.
- Cryptocurrency Miners — The JavaScript code is used to load a miner instance which will take advantage of the available system resources to execute complex tasks. When they are complete this will be reported to a specialist hacker-controlled server which will award the malware operators with digital currency.
- Hijackers — In some cases the infections can be used to install malicious web browser plugins. They are usually accompanied by a description promising greater functionality or optimization. Once installed they can lead to many modifications of the browser settings and the deployment of other threats.
- Trojan Instances — Another dangerous possibility is to load Trojan viruses which are primarily used to spy on the victim users. They set up a secure connection to a hacker-controlled server. This allows the hackers to remote control the victim systems, hijack user data and spy on the users activities at any given time.
- Ransomware — Active infections can be used to deliver ransomware viruses. They are used to encrypt target user files according to a built-in list of file type extensions.
The security reports indicate that it is very possible that the JavaScript code can be changed to include a keylogger component. It is used to monitor the keystrokes and mouse movement thereby revealing even entry to online banking accounts. This is possible due to the fact that most of them use virtual on-screen keyboards.
Steps to Prepare Before Removal:
Before starting to follow the steps below, be advised that you should first do the following preparations:
- Backup your files in case the worst happens.
- Make sure to have a device with these instructions on standy.
- Arm yourself with patience.
- 1. Scan for Mac Malware
- 2. Uninstall Risky Apps
- 3. Clean Your Browsers
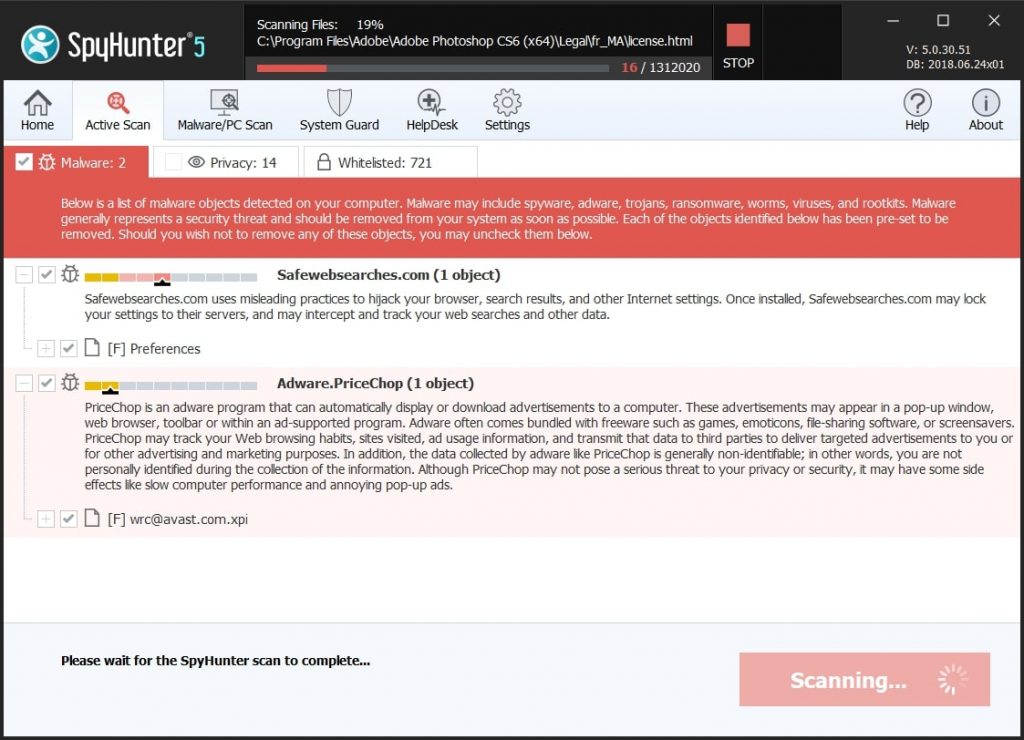
Step 1: Scan for and remove SearchAwesome Mac Adware files from your Mac
When you are facing problems on your Mac as a result of unwanted scripts and programs such as SearchAwesome Mac Adware, the recommended way of eliminating the threat is by using an anti-malware program. SpyHunter for Mac offers advanced security features along with other modules that will improve your Mac’s security and protect it in the future.
Quick and Easy Mac Malware Video Removal Guide
Bonus Step: How to Make Your Mac Run Faster?
Mac machines maintain probably the fastest operating system out there. Still, Macs do become slow and sluggish sometimes. The video guide below examines all of the possible problems that may lead to your Mac being slower than usual as well as all of the steps that can help you to speed up your Mac.
Step 2: Uninstall SearchAwesome Mac Adware and remove related files and objects
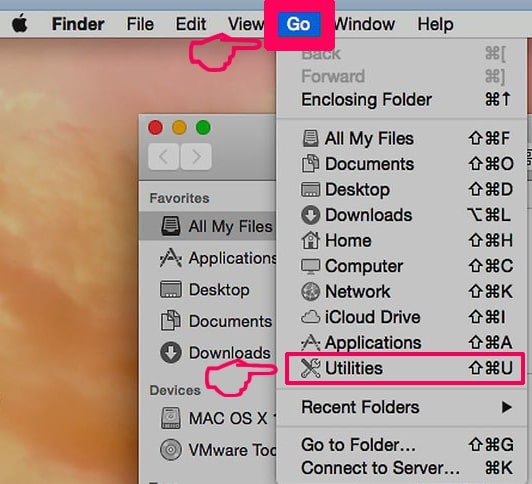
1. Hit the ⇧+⌘+U keys to open Utilities. Another way is to click on “Go” and then click “Utilities”, like the image below shows:
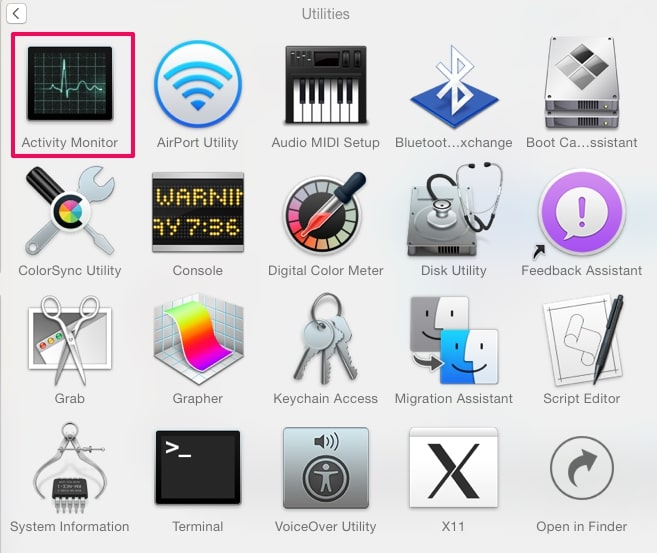
2. Find Activity Monitor and double-click it:
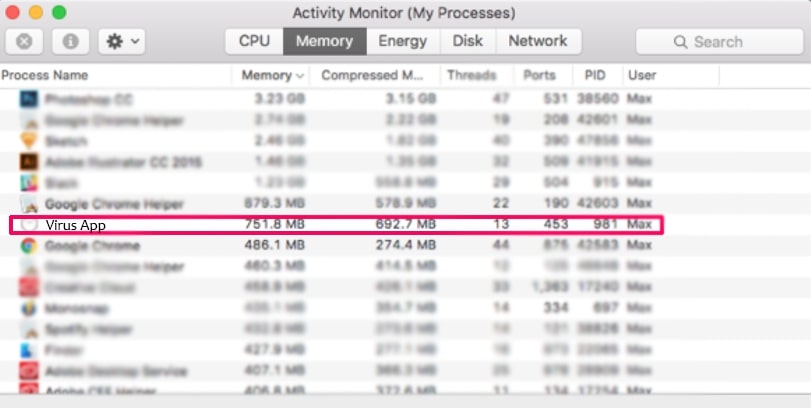
3. In the Activity Monitor look for any suspicious processes, belonging or related to SearchAwesome Mac Adware:
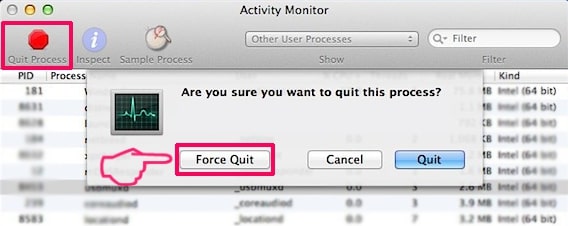
4. Click on the "Go" button again, but this time select Applications. Another way is with the ⇧+⌘+A buttons.
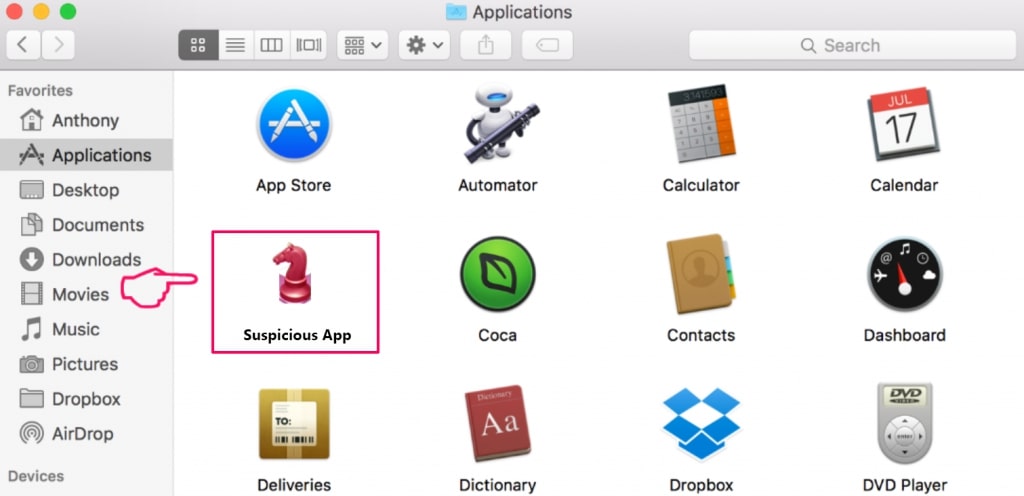
5. In the Applications menu, look for any suspicious app or an app with a name, similar or identical to SearchAwesome Mac Adware. If you find it, right-click on the app and select “Move to Trash”.
6. Select Accounts, after which click on the Login Items preference. Your Mac will then show you a list of items that start automatically when you log in. Look for any suspicious apps identical or similar to SearchAwesome Mac Adware. Check the app you want to stop from running automatically and then select on the Minus (“-“) icon to hide it.
7. Remove any leftover files that might be related to this threat manually by following the sub-steps below:
- Go to Finder.
- In the search bar type the name of the app that you want to remove.
- Above the search bar change the two drop down menus to “System Files” and “Are Included” so that you can see all of the files associated with the application you want to remove. Bear in mind that some of the files may not be related to the app so be very careful which files you delete.
- If all of the files are related, hold the ⌘+A buttons to select them and then drive them to “Trash”.
In case you cannot remove SearchAwesome Mac Adware via Step 1 above:
In case you cannot find the virus files and objects in your Applications or other places we have shown above, you can manually look for them in the Libraries of your Mac. But before doing this, please read the disclaimer below:
1. Click on "Go" and Then "Go to Folder" as shown underneath:
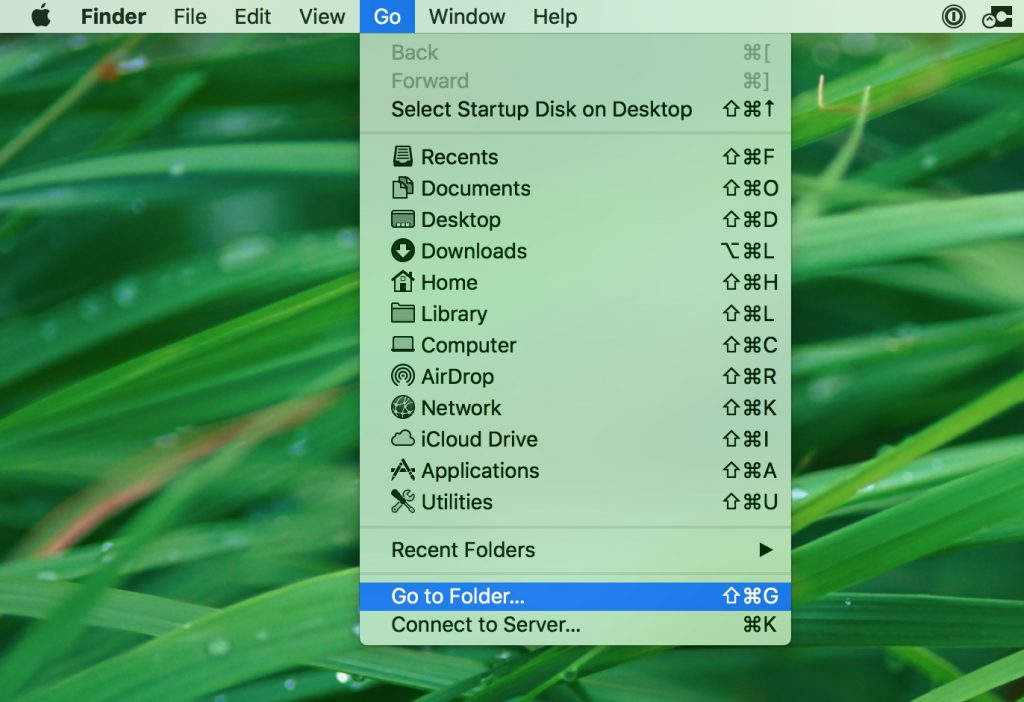
2. Type in "/Library/LauchAgents/" and click Ok:
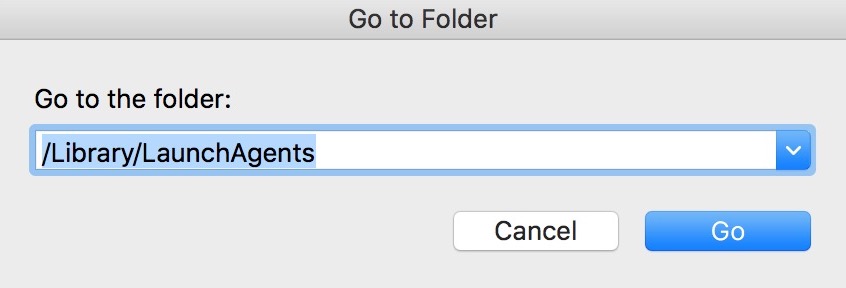
3. Delete all of the virus files that have similar or the same name as SearchAwesome Mac Adware. If you believe there is no such file, do not delete anything.
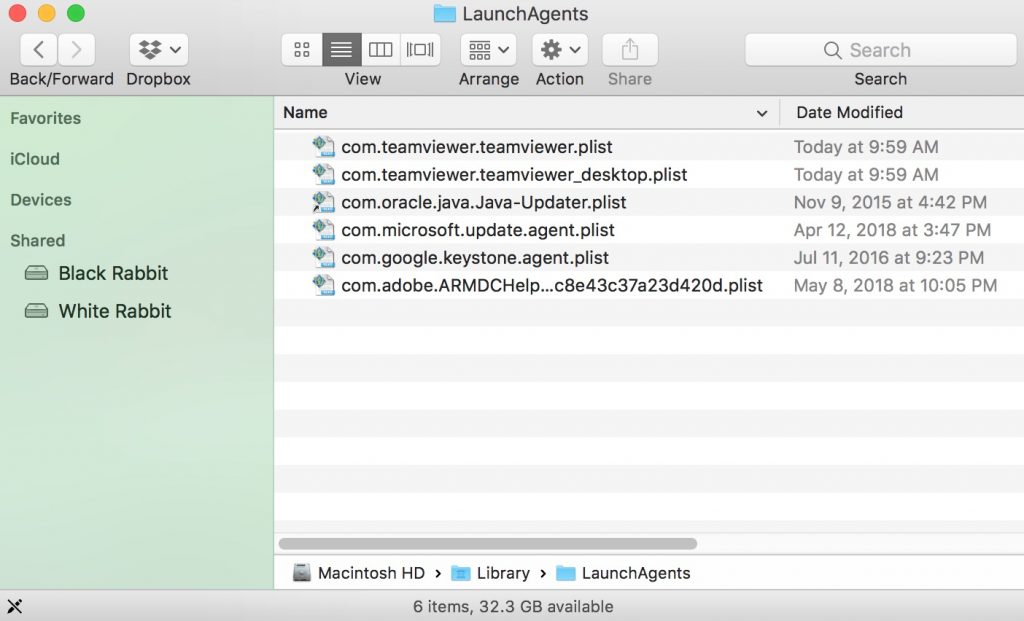
You can repeat the same procedure with the following other Library directories:
→ ~/Library/LaunchAgents
/Library/LaunchDaemons
Tip: ~ is there on purpose, because it leads to more LaunchAgents.
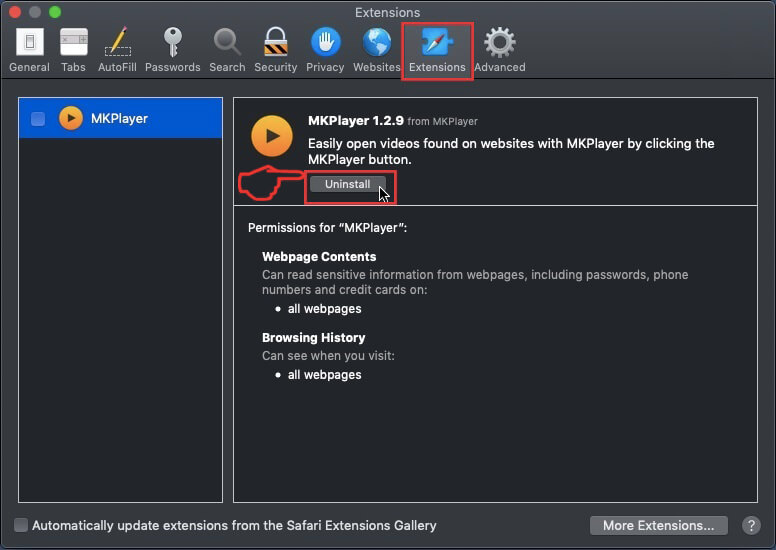
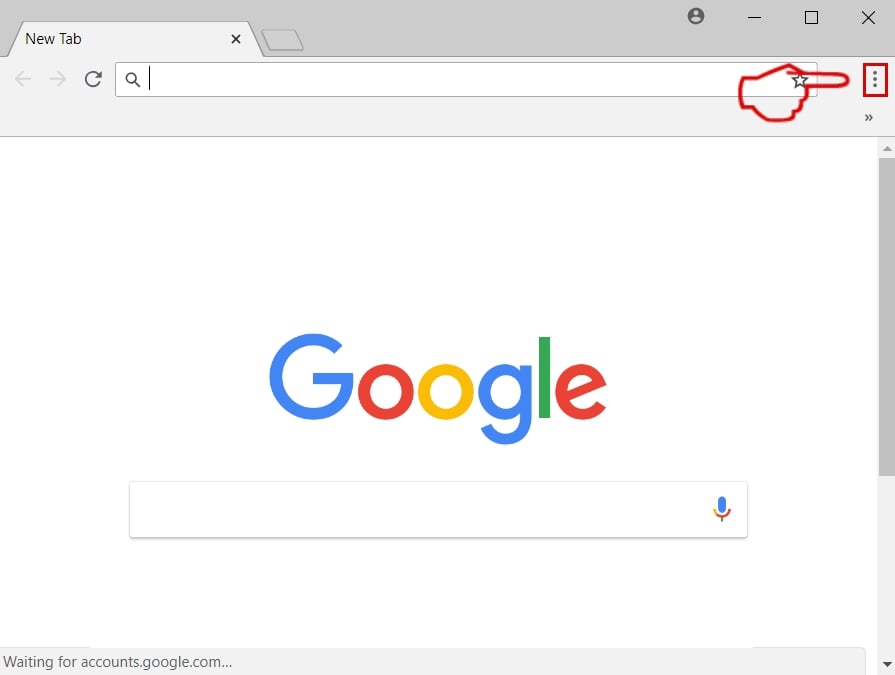
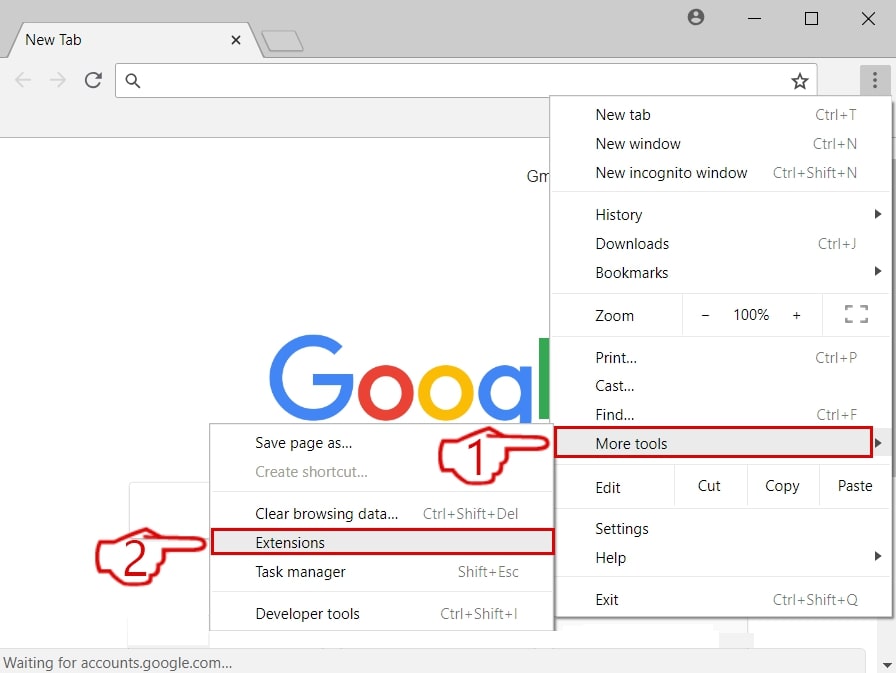
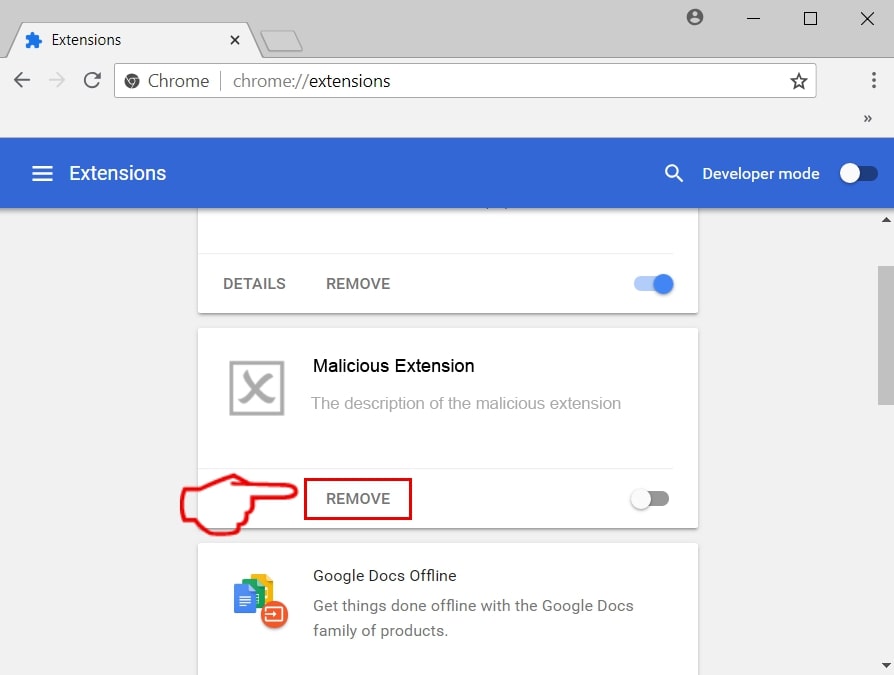
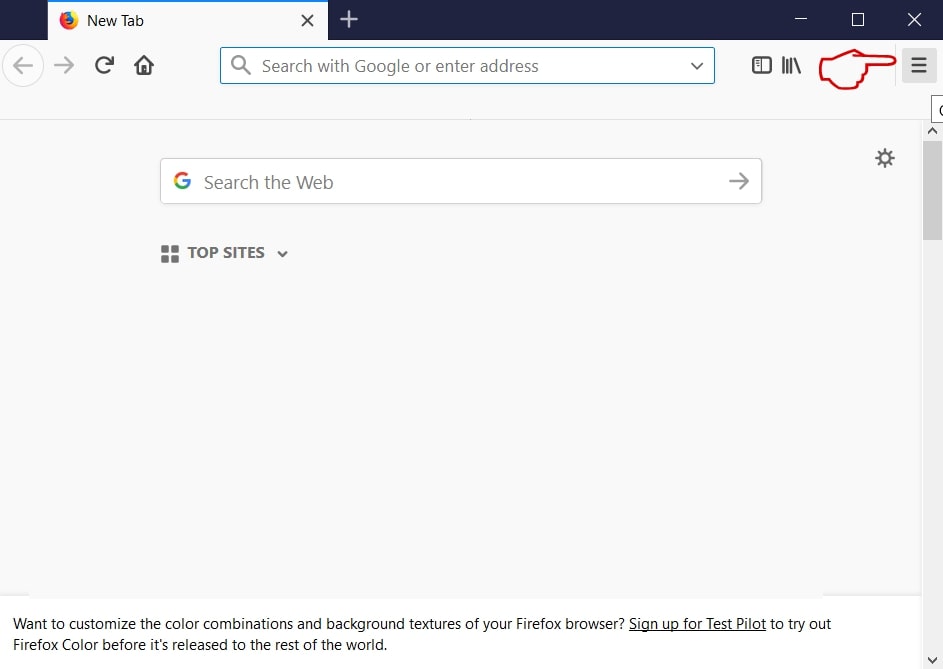
Step 3: Remove SearchAwesome Mac Adware – related extensions from Safari / Chrome / Firefox
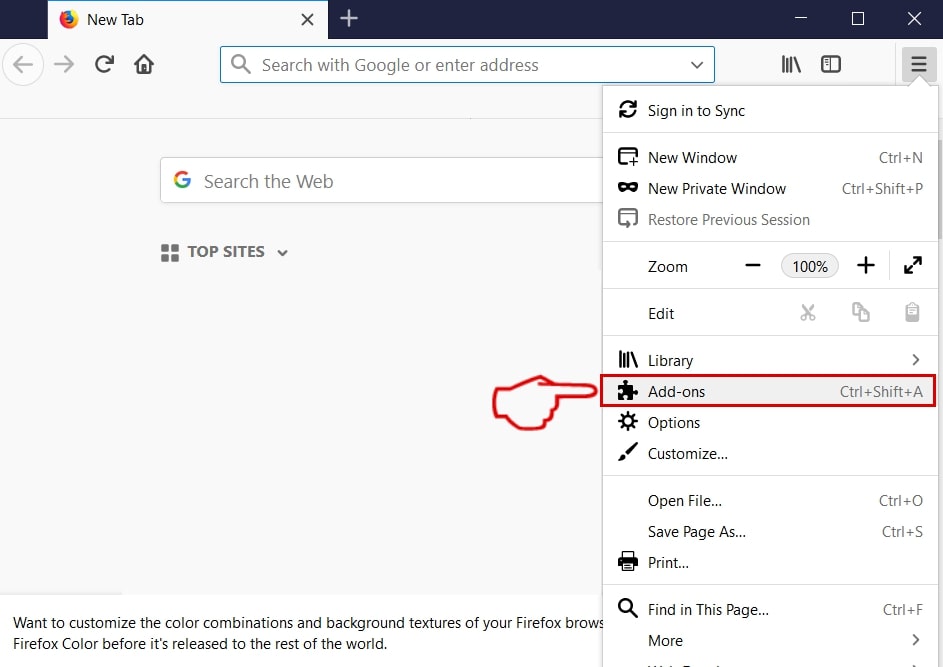
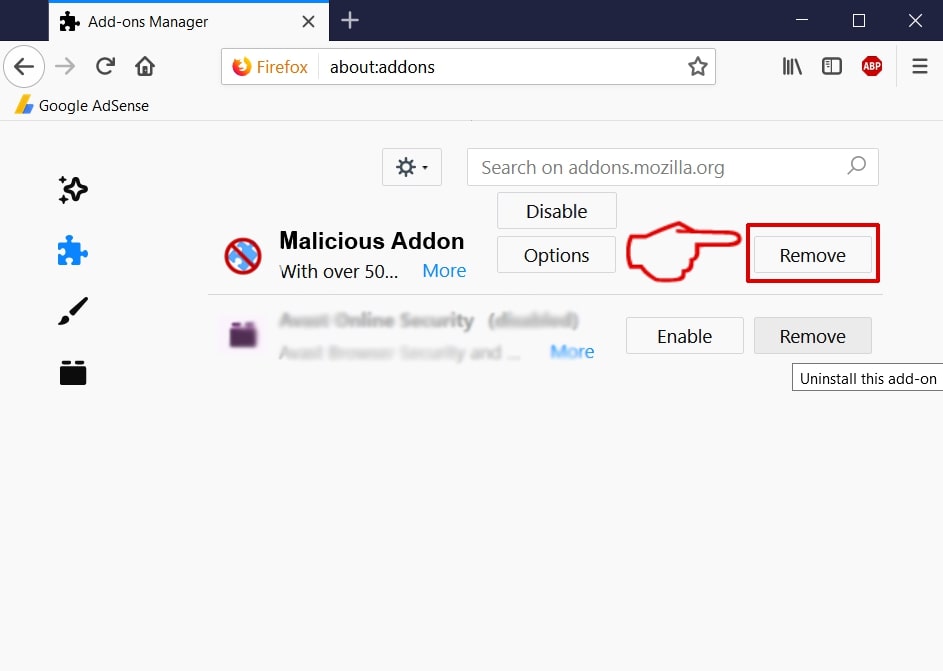
SearchAwesome Mac Adware-FAQ
What is SearchAwesome Mac Adware on your Mac?
The SearchAwesome Mac Adware threat is probably a potentially unwanted app. There is also a chance it could be related to Mac malware. If so, such apps tend to slow your Mac down significantly and display advertisements. They could also use cookies and other trackers to obtain browsing information from the installed web browsers on your Mac.
Can Macs Get Viruses?
Yes. As much as any other device, Apple computers do get malware. Apple devices may not be a frequent target by malware authors, but rest assured that almost all of the Apple devices can become infected with a threat.
What Types of Mac Threats Are There?
According to most malware researchers and cyber-security experts, the types of threats that can currently infect your Mac can be rogue antivirus programs, adware or hijackers (PUPs), Trojan horses, ransomware and crypto-miner malware.
What To Do If I Have a Mac Virus, Like SearchAwesome Mac Adware?
Do not panic! You can easily get rid of most Mac threats by firstly isolating them and then removing them. One recommended way to do that is by using a reputable malware removal software that can take care of the removal automatically for you.
There are many Mac anti-malware apps out there that you can choose from. SpyHunter for Mac is one of the reccomended Mac anti-malware apps, that can scan for free and detect any viruses. This saves time for manual removal that you would otherwise have to do.
How to Secure My Data from SearchAwesome Mac Adware?
With few simple actions. First and foremost, it is imperative that you follow these steps:
Step 1: Find a safe computer and connect it to another network, not the one that your Mac was infected in.
Step 2: Change all of your passwords, starting from your e-mail passwords.
Step 3: Enable two-factor authentication for protection of your important accounts.
Step 4: Call your bank to change your credit card details (secret code, etc.) if you have saved your credit card for online shopping or have done online activiites with your card.
Step 5: Make sure to call your ISP (Internet provider or carrier) and ask them to change your IP address.
Step 6: Change your Wi-Fi password.
Step 7: (Optional): Make sure to scan all of the devices connected to your network for viruses and repeat these steps for them if they are affected.
Step 8: Install anti-malware software with real-time protection on every device you have.
Step 9: Try not to download software from sites you know nothing about and stay away from low-reputation websites in general.
If you follow these reccomendations, your network and Apple devices will become significantly more safe against any threats or information invasive software and be virus free and protected in the future too.
More tips you can find on our MacOS Virus section, where you can also ask any questions and comment about your Mac problems.
About the SearchAwesome Mac Adware Research
The content we publish on SensorsTechForum.com, this SearchAwesome Mac Adware how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific macOS issue.
How did we conduct the research on SearchAwesome Mac Adware?
Please note that our research is based on an independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware definitions, including the various types of Mac threats, especially adware and potentially unwanted apps (PUAs).
Furthermore, the research behind the SearchAwesome Mac Adware threat is backed with VirusTotal.
To better understand the threat posed by Mac malware, please refer to the following articles which provide knowledgeable details.


