The Slackor RAT is a tool developed primarily for security researchers allowing for malicious actors to use Slack as a server backend. In real-world scenarios it can also be utilized by hackers in large-scale attacks. This can be extremely dangerous as Slack allows the hackers to set up custom channels that lead to a very capable infrastructure.
Slackor RAT Developed as a Security Tool, Can Be Utilized By Hackers
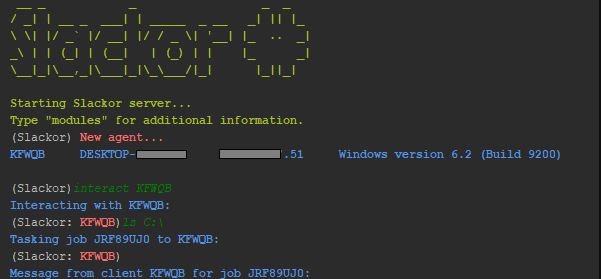
The Slackor RAT is being developed by a security researcher in order to penetration testers during their analysis of client’s network security. The tool is available as an open-source download which is written in the Golang language. The main advantage of Slackor is that it uses a widely-known application as server infrastructure which actively bypasses the firewall rules. This allows the connections to be made without any issues and the malicious commands will make use of the security that is implemented in the program — the TLS protocol which guarantees the data protection. The reason why Slack is being used is the fact that it is used as a collaboration platform by many enterprise clients which automatically makes it a white-listed application throughout the security defenses of the company networks.
Another advantage of using Slack is that it comes with a well-documented API which is easy to be implemented in various scripts and programs. Network resolutions and connections made to servers will only show the main domain. By itself Slackor is developed on top of the idea carried used by previous tools that used Slack as a backend. There have been several known instances to this date that have taken advantage of Slack as infrastructure.
Slackor and Slack In Real-World Scenarios
As Slackor code can be easily embedded in a wide range of scripts and programs it can be placed across all kinds of payload carriers — this can include documents of all popular formats (spreadsheets, presentations, databases and text files) and application installers. These files can be spread using a multitude of methods:
- File-Sharing Networks — They can be used to spread both pirate and legitimate files.
- Phishing Campaigns — The criminals can send out email messages that pose as legitimate and well-known companies or services. In their contents and links the recipients will be led to the dangerous files.
- Malicious Sites — Another popular approach is the creation of pages and sites that appear as safe and useful portals. They will contain links, scripts or other resources that can lead to the installation of the Slackor RAT.
- Direct Attacks — Existing infections and direct penetration testing attacks can lead to the delivery and installation of the Slackor RAT.
And even though the Slackor RAT code will function as intended according to the commands of the operators it still contains limitations. The applications is designed with a specific rate limiting which means that messages and request responses may be delayed. This can bring forth problems when the Slackor RAT is used en-mase against many users at once. The other problem is that there is an imposed limit on the number of characters that can be sent This reduces the possibility of harvesting large numbers of sensitive information and transmitting it in a single message. Certain directory listings can exceed this limit. Slack can also be used to transfer data, the full list of the capabilities of the Slackor RAT include the following:
- Delivery and execution of other threats.
- Uploading and downloading of Files
- Commands Execution
- Keylogging of User Input
- Information Harvesting
As an open-source tool the Slackor RAT can be modified and modeled according to the exact instructions governed by the criminals. As of the date of writing this article there have been no reported infections however we assume that it can be employed in future campaigns.


