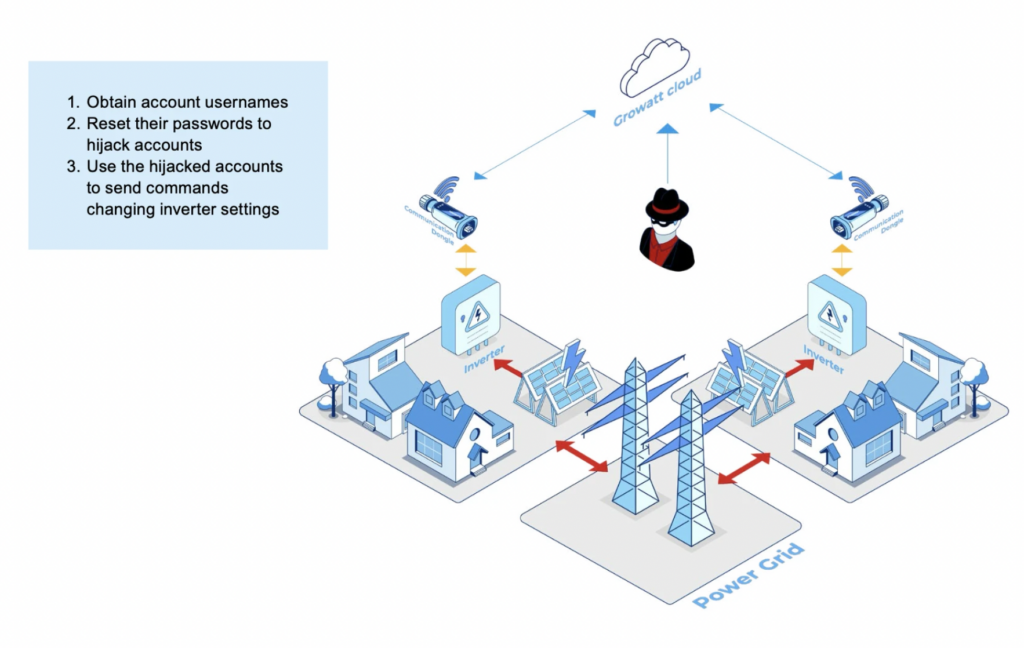
A new report from Forescout’s Vedere Labs reveals alarming cybersecurity vulnerabilities in solar power systems produced by some of the industry’s biggest names – Sungrow, Growatt, and SMA. These flaws, collectively named SUN:DOWN, could potentially open the door for cyberattacks targeting energy production, grid stability, and consumer data.
SUN:DOWN Vulnerabilities: Weak Links in Solar Infrastructure
Forescout’s research identified 46 distinct vulnerabilities across various components in solar energy ecosystems, including:
- Solar Monitors (38%)
- Cloud Management Platforms (25%)
- Photovoltaic (PV) Inverters (15%)
These flaws were found in both hardware and software interfaces that connect to public networks, making them especially susceptible to remote exploitation. Some could allow attackers to gain full control over solar inverters or impersonate cloud services used for updates and monitoring.
According to the researchers, the “findings show an insecure ecosystem — with dangerous energy and national security implications.”
While each residential solar system produces limited power, their combined output reaches dozens of gigawatts — making their collective impact on cybersecurity and grid reliability too significant to ignore.
Solar Inverters: The Silent Target
PV inverters (or photovoltaic inverters), responsible for converting solar-generated DC power into AC for the grid, are a growing target for cybercriminals. Attackers exploiting these systems could:
- Modify power output to destabilize the grid
- Shut down solar systems remotely
- Inject false data into monitoring platforms
- Form large-scale botnets for distributed attacks
Real-World Implications for Grid Stability
These vulnerabilities aren’t hypothetical. If an attacker gains control of even just 2% of the solar inverters in a given region, it could destabilize the power grid enough to trigger emergency systems or, in severe cases, cause large-scale blackouts due to the grid’s sensitivity to sudden disturbances. Due to the rise of distributed solar energy in both residential and industrial settings, the risks are only increasing.
Security Gaps in the Solar Supply Chain
Another concern is the absence of consistent security practices across manufacturers and integrators. Many devices still use outdated firmware, weak authentication, or open ports. Cloud platforms, too, were found to lack proper validation, exposing them to spoofing and impersonation attacks.
In addition, because third-party installers often configure these systems, maintaining strong cybersecurity standards across the entire ecosystem becomes even more complicated.
Recommendations to Strengthen Solar Cybersecurity against SUN:DOWN
For Manufacturers
- Implement secure-by-design principles
- Offer regular firmware updates and security patches
- Use encryption and strong authentication for all connections
For Commercial and Industrial Operators
- Include cybersecurity terms in procurement contracts
- Perform system-wide risk assessments and pentests
- Segment networks and ensure visibility into solar devices
- Monitor for anomalies and unusual traffic patterns
For Policymakers and Regulators
- Classify solar components as critical infrastructure
- Enforce NIST and DOE cybersecurity compliance
- Support public-private collaboration on threat intelligence
Conclusion: How to Secure the Future of Renewable Energy
What this research ultimately reveals is a tension between innovation and security. A tension that, if left unaddressed, could undermine the very progress we’re making toward a more sustainable future.
The SUN:DOWN vulnerabilities are not just technical oversights, as they reflect a systemic underestimation of how cybersecurity risks scale in tandem with physical infrastructure. Solar inverters, once seen as simple hardware, have evolved into intelligent, networked devices embedded deep within our energy systems. But with that intelligence comes exposure, and with exposure, vulnerability.
What we need is a shift in mindset. Energy producers and technology manufacturers can no longer afford to treat cybersecurity as a secondary concern or a feature to be patched in later. Security must be designed into the architecture of every connected energy device from the start.
Moreover, there’s an ethical dimension to these issues. Energy systems don’t just power cities, as they introduce the ideology of a more sustainable future. When the tools of renewable energy are left unsecured, we risk not only grid instability but public trust in the technologies that are meant to lead us into a cleaner, more equitable world.
The conversation around renewable energy must now evolve to include cybersecurity as a backbone of resilience. Only by integrating security with sustainability can we build an energy future that’s not just green, but also safe, stable, and enduring.
Explore the full technical breakdown and detailed vulnerabilities in Forescout’s official report.


