Several sources, among which the websites BoingBoing and PCworld, have recently published articles about librarians from Massachusetts installing the software Tor on all public PCs they have in order to allow their patrons use the web anonymously. The librarians are going through all these troubles as a stand against the passive government surveillance and against the companies that track users online aiming to build dossiers of the users which they can later use in highly-targeted advertising campaigns.
The experts say that this is a very interesting project and a bold statement for the privacy of the user. Those people who want to serve the World Wide Web anonymously can do so not only in that library, but also at home. Connection to the Tor network is possible from the users’ own PCs, it is easy and quick and is done through the Tor Browser.
The Nature of TOR
Tor is a computer network which is run by volunteers located around the world. The volunteers’ job is to run a relay, which is a computer that runs specific software that allows users to connect to the internet via the Tor network. The Tor Browser, before joining the Internet, connects to several different relays and wipes its tracks. In this way the Tor Browser is making it difficult for another person to figure out who and where the user is.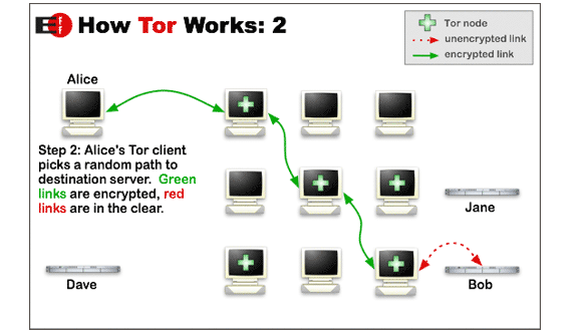
Experts say that Tor is very popular as a tool for certain illicit goods to be purchased online, however the Tor software has plenty of numerous legitimate uses including, for example, journalists who are in communication with anonymous sources and activists from different oppressive regimes.
Average Internet users, however, are also interested in the Tor tool, as they appreciate the fact that the software will keep their private browsing free from advertisements and data collection.
How to download TOR
The easiest way in which people can use Tor is to download the Tor Browser. The Tor Browser is a modified version of Firefox, equipped with other software used to connect the user to the Tor network. When the installer is downloaded, they can check the installation file’s GPG signature and make sure they have downloaded the proper version of the browser and then to install the Tor software.
The GPG signature checking is easy to be done and it requires additional software to be downloaded.
How to install TOR
The process of Tor Browser installing follows the checked of the GPG signature. In Windows, the Tor Browser is an EXE file and it is simple to install just like the rest of the programs. The difference here is that the Tor browser is not with the same default location as the other programs. The Tor Browser usually offers the user’s desktop to be marked as the ‘location’. It can do that as Tor Browser is portable software and it does not need to integrate in the Windows system in the typical way.
The Tor Browser can be run from anywhere – the Documents’ folder, the Desktop, the USB drive. How is this done? The user goes to ‘Choose install location’ window, clocks on ‘Browse’ and chooses where the browser should be to installed. When the location is selected, the user has to press the ‘Install’ button and the Tor Browser will do all that has to be done.
How to use the Tor Browser
When the Tor Browser is installed, the user gets a plain folder called Tor Browser. Inside is located the exe file called ‘Start Tor Browser’. When the user clicks on that file, a new window opens asking the user whether the user would like to configure proxy settings first or to connect directly to the Tor network. As a rule, the average Internet users prefer the direct option and they should press ‘Connect’. Just a few seconds after that, they see a version of Firefox that is launching on their computers and thus they are connected to the Tor network. There, the users are welcome to browse and stay anonymous.
How to make sure that you are using Tor Browser
The users who want to make sure that they are connected to the Tor Browser should visit the website whatusmyip.com and it will detect their location based on the Internet Protocol address. In case the browser shows a location that is not that of the user, then he is using Tor Broswer. The user should make sure that all the anonymous browsing is done from the Tor Browser itself as the other programs are in fact not connected to Tor.
The anonymous browsing on Tor is not that simple as there are rules which the user has to observe. This includes connection to the SSL/TSL encryption (HTTPS) of the visited websites. If the user does not do that, anything that one does online can be seen by the person running the exit node.
The Tor Browser further has HTTPS Everywhere Electronic Frontier Foundation add-on which is installed by default, and which covers the users’ SSL/TSL needs at that time. The users should also be aware that the anonymous browsing does not immune them from malware. Tor Browser has not the capacity to protect the users from malicious software; it can only protect the users from revealing their location and help them stay private.

