 The latest trend in the 21st century – IoT, common systems of devices organized to revolutionize our daily lives are becoming a playground for hackers. This becomes particularly interesting primarily for IT security professionals who are always looking forward to improving security by discovering how such hacks work. It has become a game of cat and mouse between reverse engineers and hackers who not only just hack those devices but use that access to hack other devices that are interconnected to them one way or another.
The latest trend in the 21st century – IoT, common systems of devices organized to revolutionize our daily lives are becoming a playground for hackers. This becomes particularly interesting primarily for IT security professionals who are always looking forward to improving security by discovering how such hacks work. It has become a game of cat and mouse between reverse engineers and hackers who not only just hack those devices but use that access to hack other devices that are interconnected to them one way or another.
Researcher Johannes Ullrich at InfoSec Handlers Diary Blog explains how DVR’s can be taken over and used as a cyber-weapon to gain access to other devices:
“Over two years ago, we reported about how exploited DVRs are used to attack other devices across the internet. Back then, like today, the vulnerability was an open telnet server with a trivial default password……
You can no longer turn it on via the web-based interface, but only by using the “physical” interface displayed to the user connected to the DVR via an attached monitor.”
The malware researcher also states a report on DDoS attacks performed by botnets all over the world primarily via DVR devices. In fact, there have been detected over 100 thousand devices which combined in botnets can cause a massive DDoS attack of over 1TBps (1 000 000MBps). Such attacks are possible via those IoT devices because they act as an opportunity for the hackers. Since such devices are passive and their security is often not monitored properly by organizations, they are a lucrative target.
Ullrich also displays a graph of what appears to be his research showing a massive increase in infections since the start of October:
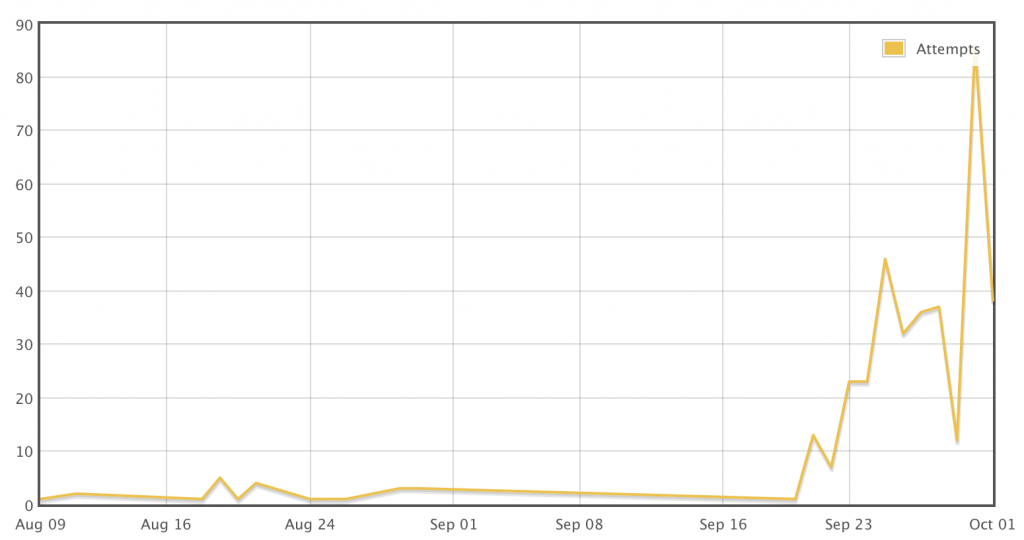 Source: Johannes Ullrich’s InfoSec Report
Source: Johannes Ullrich’s InfoSec Report
The researcher still feels convinced that many of the IoT devices nowadays are not updated properly and do not contain passwords that are strong enough. Yes, the password itself may be very complicated, but some DVR devices may contain weaker encryption allowing hackers to penetrate it with time.
Johannes also conducted an experiment. He set up an old DVR device after which he ran a network sniffer on it to follow the packets and monitor what happens with the network connection of the device.
The results were surprising – very soon after Ullrich has set up the IoT device and has connected it, connection attempts have begun to show up. The primary method of connecting to the DVR was via Telnet. The researcher also reports that there were so many attacks that the telnet server of the DVR device becomes unresponsive at times.
The researcher also reports several different attacks that were successful in getting the right password, unlike most of them.
The modern infection method according to Johannes unlike the previous exploit kits that download malware by exploiting scripts on bash or python languages the modern attacks were very small regarding lines of code and bytes.
These small binaries were reportedly acting as “recons” since they are believed to begin scanning for interconnected hosts that were vulnerable to infections and send reports to remote servers via unsecured ports. The malware researcher has concluded that he received several hacking attempts that resulted in success per one hour.

The Bottom Line for IoT Hacking
In case you have a network of smart IoT devices, whether they are DVR or anything else, you should analyze what passwords you have used on them and what is their encryption and strength according to Ullrich’s recommendations. And it is very much advisable to raise awareness of the danger these types of threats represent to anyone who is using IoT, especially the home or office network.


