Error: Ox800VDS is a recent example of a tricky tech-support scam. If you see such a pop-up, proceed with caution, as scammers will be trying to persuade you that your computer is infected. This guide will help you deal with the scam and its consequences.
What Is Error: Ox800VDS?
The “Error: Ox800VDS” scam imitates Windows OS graphics and color palette to deceive users. When a visitor lands on the website, they are bombarded with multiple pop-ups, including one that mimics the Microsoft Defender Antivirus interface, supposedly running a system scan.
Overlaid on this is another pop-up alerting the user of an error labeled “Ox800VDS,” claiming that the scan failed and several infected files were detected but not removed. This pop-up urges the user to perform a manual scan and call a fake “Windows Support” helpline. The scam page continuously pressures the user to make this call. In addition, a prominent pop-up claims that the operating system has been locked due to unusual activity, urging the user to sign in with their Microsoft ID and password and contact “Microsoft Support.”
This phishing attempt aims to steal login credentials and other sensitive information. Despite its convincing appearance, all claims made by this scam are false, and it is not associated with Microsoft products or services. The primary goal of the “Error: Ox800VDS” scam is to trick users into calling the bogus support line, where the scam can progress in various harmful ways, posing significant threats to the user’s security.
Threat Summary
| Name | Error: Ox800VDS |
| Type | Tech Support Scam |
| Removal Time | Approximately 15 minutes to scan the whole system and remove any discovered threats |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
Error: Ox800VDS Scam: What You Need to Know
Tech support scams such as Error: Ox800VDS have become a prevalent threat, exploiting the reliance of individuals and businesses on technology. These scams often involve fraudsters impersonating tech support representatives to deceive victims into paying for nonexistent services or surrendering sensitive information. Understanding the mechanisms behind these scams is vital for protection against them.
In the case of the Error: Ox800VDS scam, the fraudsters are attempting to deceive individuals by convincing them to grant remote access to their computers through the use of a legitimate software called Remote Utilities. They have manipulated the interface of this software to make it look like it is developed by Microsoft, thereby enhancing their credibility. It is crucial to avoid trusting such scam webpages, downloading any software from them, or contacting the scammers through the provided phone number.
How Does the “Error: Ox800VDS” Scam Scam Operate?
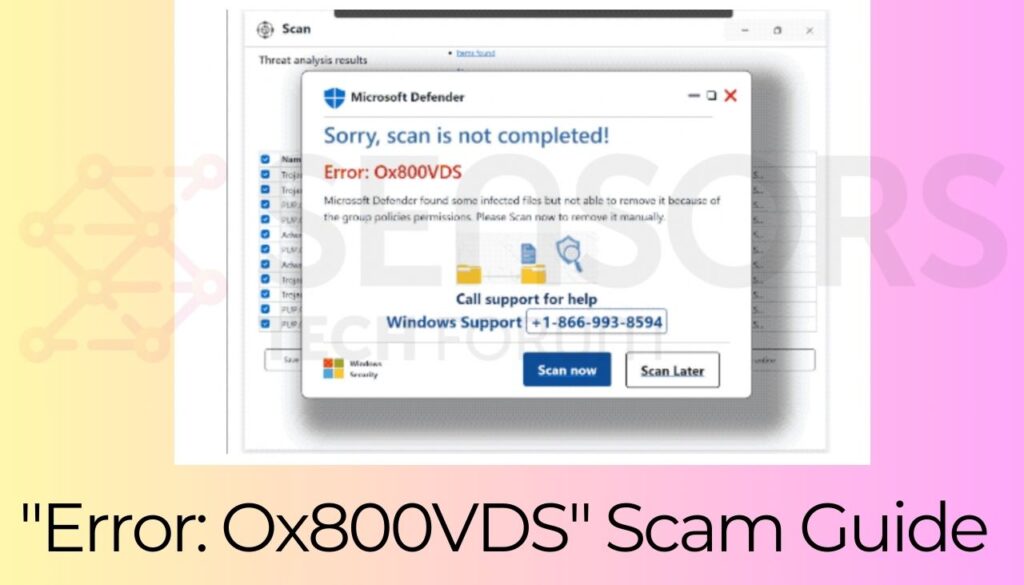
This scam involves displaying fake Microsoft Defender notifications that claim malicious software has been detected on a visitor’s computer, along with the “Error: Ox800VDS” error code. To resolve the issue, the scam instructs visitors to call the number “+1-866-993-8594” and follow the provided instructions. Here’s the text of the scam:
Microsoft Defender
Sorry, scan is not completed!
Error: Ox800VDS
Microsoft Defender found some infected files but not able to remove it because of the group policies permissions. Please Scan now to remove it manually.
Call support for help
Windows Support +1-866-993-8594
How to Recognize the Red Flags of Tech Support Frauds
Identifying the warning signs of tech support scams such as Error: Ox800VDS can significantly reduce the risk of falling victim to them. Here are some prominent red flags to be aware of:
- Unsolicited Contact: Legitimate companies, including Microsoft, do not make unsolicited calls or send unsolicited emails to offer technical support. Be skeptical of any unexpected communication claiming to be tech support.
- Pressure Tactics: Scammers often create a sense of urgency, claiming your computer is at risk to pressure you into immediate action. Authentic tech support will not pressure you into making fast decisions.
- Requests for Payment in Untraceable Methods: Be wary if you’re asked to pay for services with cryptocurrencies or gift cards. Legitimate companies will provide standard, secure payment methods.
- Claims of Malware or Virus Detection: Scammers may claim they’ve detected malware or viruses on your computer to scare you. Understand that legitimate alerts from your computer will never ask you to call a phone number.
- Request for Remote Access: Providing remote access to your computer can put personal and financial information at risk. Be cautious about allowing remote access unless you initiated the contact with a trusted company.
- Fake Error Messages: Tech support scammers frequently use pop-up messages or full-screen alerts claiming to be from reputable companies. Remember, genuine error messages will not include phone numbers or prompt you to make a call.
To safeguard against tech support frauds, adopt a proactive stance by utilizing reputable security software. For enhanced protection, SpyHunter offers robust features designed to detect and remove malware and other threats, effectively blocking scam attempts. By recognizing these red flags and taking preventive measures, you can significantly reduce the risk of becoming a tech support scam victim.
Staying informed about the latest scam tactics and maintaining a critical approach to unsolicited communication are key steps in protecting your digital security. When in doubt, contact tech support services directly through official channels to verify the authenticity of any claims or requests.
Why Popup Ads are More Dangerous than You Think
Fake pop-ups such as the ones generated by Error: Ox800VDS are often seen as minor annoyances that are a standard part of internet browsing. However, their potential for harm goes beyond simple inconvenience. These ads can serve as vehicles for cybercriminals to disseminate malware, extract sensitive personal data, or deceive users into parting with their money through scams.
Unlike traditional ads that are easily dismissed or avoided, harmful popups use deceptive tactics to lure users into interacting with them. This can include fake virus alerts, promises of won prizes, or urgent messages that mimic the appearances of legitimate sites. The danger lies not only in the potential financial loss or identity theft but also in the fact that such interactions can compromise your device’s security.
Deciphering Harmful Pop-ups from Harmless Ones
Identifying the difference between harmful popup ads such as Error: Ox800VDS and those that are benign can be challenging. However, there are several red flags to watch for. Scam popups often contain spelling mistakes and display non-professional images, which could be your first clue. They may create a sense of urgency, pressuring you to act quickly by providing personal information or subscribing to services. Legitimate companies do not operate by instilling panic or offering exclusive financial gain opportunities with vague details.
- Engineering Urgency: Be wary of timers or alerts claiming immediate action is needed, as legitimate entities understand the importance of informed decision-making.
- False Promises: If you encounter a popup claiming you’ve won a prize without participation, it’s likely a scam. Authentic competitions or giveaways do not operate in secrecy or without directly engaging participants.
- Device Scans: Popups that simulate device scans and claim virus detection are unequivocally deceptive. Real scans require software installed on the device and can’t be performed through a browser popup.
- Exclusivity Clauses: Offers claiming you’re the ‘only one selected’ for a secretive and lucrative deal are almost always scams designed to entice quick decisions without proper scrutiny.
When faced with a popup, regardless of how urgent or tempting it appears, the safest approach is to close it without interaction. On devices like iPhones, iPads, or Macs, employ built-in features and settings to block unwanted popups. In addition, utilizing security software such as SpyHunter can offer an added layer of protection by detecting and blocking malicious sites and popups. This approach helps ensure your online browsing is not only safer but also more enjoyable, free from unnecessary interruptions and potential threats.
Top Techniques Scammers Use to Lure Victims
Understanding how scammers operate is the first step in protecting yourself from tech support scams. By recognizing the methods used to trick individuals into believing their technology is at risk, you can more effectively guard against these fraudulent activities. Scammers are becoming increasingly sophisticated, but their tactics often follow similar patterns designed to exploit fear, trust, and urgency.
The Art of Imitation: How Scams Mimic Legitimate Tech Support
One of the primary strategies employed by online scammers is the art of imitation. By pretending to be representatives from well-known tech companies, in this case Microsoft, they exploit the trust that people have in these brands. Here’s how they do it:
- Caller ID Spoofing: Scammers can manipulate caller ID systems to display a legitimate company’s phone number, making it appear as if the call is coming from a trusted source.
- Fake Error Messages: Upon visiting compromised websites or even through advertisements, users might encounter alarming error messages prompting them to contact a tech support hotline. It’s important to remember that real error messages from your operating system or software will never provide a phone number for tech support.
- Imitation Websites: Scammers often create websites that mimic the look and feel of official tech support resources. These sites may offer downloads of “helpful” software that is actually malware intended to compromise your device.
- Fear Tactics: By displaying urgent pop-up messages or creating fake system warnings, scammers play on fear to convince you there’s an immediate problem with your computer that requires their intervention.
- Remote Access Requests: Once in contact, scammers will frequently request remote access to your device to “solve” the issue. Granting this access can lead to data theft, installation of malicious software, or other privacy invasions.
It’s crucial to approach unsolicited tech support calls or messages with skepticism. Legitimate companies like Microsoft will never contact you in this way for technical support issues. If you encounter a situation where you’re unsure about the legitimacy of a tech support claim, it’s safer to independently contact the company through official channels.
In the event that you suspect a tech support scam or your device is compromised, employing a robust cybersecurity tool like SpyHunter can help safeguard your information and rectify any security issues caused by malicious software. SpyHunter is designed to detect and remove malware, offering peace of mind when navigating the complexities of online security threats.
Adjusting Browser Settings to Protect Against Error: Ox800VDS
To provide an additional safeguard against scams and malicious websites, adjusting your browser settings is a key step. Every major browser has settings designed to protect users, and knowing how to configure them can enhance your browsing safety. Here are some general tips:
- Block Pop-ups: Ensure that the pop-up blocker feature is enabled in your browser’s settings. This prevents unwanted ads and potential scam pop-ups from appearing.
- Fraudulent Website Warning: Activate the feature that warns you about suspicious or fraudulent websites. This can alert you before you enter a potentially harmful site.
- Download Protection: Enable settings that scan downloads for threats before saving them to your computer. Many modern browsers have integrated security features that offer this level of protection.
- Privacy Settings: Review and adjust your browser’s privacy settings to minimize data sharing. Limiting cookies and site data can reduce tracking and the risk of data theft.
It’s also advisable to use advanced security tools and software to enhance your protection against browsing-related threats. For example, deploying security solutions like SpyHunter can provide extensive protection against malware, ransomware, and other cyber threats. Security tools that offer real-time protection and frequent updates can be invaluable assets in defending against the constantly evolving tactics used by cybercriminals.
Why SpyHunter Is Your Go-To Solution for Avoiding Scams
Given the rise of scams such as the Error: Ox800VDS scam, which cunningly tricks users into granting remote access to their computers, the importance of robust security software cannot be overstated. SpyHunter is engineered to detect and remove malware infections, thwarting attempts by scammers to compromise your system’s integrity and your personal data’s confidentiality.
SpyHunter offers a comprehensive shield against a variety of threats including malware, ransomware, Trojans, and keylogers that form the backbone of many online scams. Its advanced scanning technology not only identifies existing threats but also provides real-time protection to prevent future infections. Here’s how SpyHunter can safeguard your digital life:
- Up-to-date Malware Database: SpyHunter’s continuously updated database ensures protection against the latest malware strains, including those used in tech support scams and other phishing attempts.
- User-friendly Interface: Designed with simplicity in mind, SpyHunter provides an intuitive interface that allows users to easily manage their security settings and scan their systems for threats, making cyber security accessible to everyone regardless of tech expertise.
- Customized Remediation: Unlike one-size-fits-all solutions, SpyHunter offers customized remediation strategies tailored to the specific needs of your system, ensuring that detected threats are dealt with effectively.
- Customer Support: In addition to its autonomous protective features, SpyHunter also provides access to a dedicated support team. This ensures that users have expert assistance available should they encounter complex issues or threats.
- Privacy Protection: By securing your system against unauthorized access and malware, SpyHunter also plays a crucial role in protecting your sensitive information from being compromised, reducing the risk of identity theft and fraud.
Immediate Actions After Encountering a Tech Support Scam
When you realize you might have engaged with a tech support scammer, it’s important to act swiftly to secure your digital life. Here are the steps you should take without delay:
- Uninstall Suspicious Applications: If the scammer instructed you to download any software, remove it immediately from your device. For Windows users, you can uninstall programs through the Control Panel or Settings app. For macOS, drag the application from the Applications folder to the Trash.
- Reset Your Device: If scammers had remote access to your device, performing a factory reset may be necessary to remove any hidden malware. While resetting your device can be time-consuming, it’s a critical step in ensuring your device is clean.
- Run a Full Malware Scan: Use your antivirus software to run a comprehensive scan of your device to find and remove any malware. For users without security software, Windows Security provides a built-in scanning option.
- Update Your Software: Ensure all your software, especially your operating system and antivirus program, are up to date with the latest security patches. Scammers often exploit known vulnerabilities that updates can fix.
- Change Your Passwords: Update passwords for all critical accounts, including your computer, financial institutions, and any other sites where you have an account. This prevents scammers from gaining further access.
- Contact Your Financial Institutions: If you’ve disclosed any financial information or made payments to the scammers, contact your bank or credit card provider immediately to report the fraud and protect your accounts.
In addition to these steps, it’s wise to consider using specialized security software for an extra layer of protection. SpyHunter is a robust option designed to detect and remove malware and other threats that conventional antivirus programs might miss. It provides comprehensive protection against a wide range of malware infections, including those that tech support scammers might install on your computer.
Where and How to Report Scammers
Reporting tech support scams is a critical step in the fight against cybercriminals. Whether these scammers claim to be from a reputable company like Microsoft or not, your prompt action can help mitigate the impact of these fraudulent activities. Here’s how and where you can report these scams effectively:
- Microsoft’s Report a Scam Page: Microsoft encourages users to report tech support scams directly through their dedicated portal at www.microsoft.com/reportascam. This platform is designed for reporting scams regardless of whether they pretend to be associated with Microsoft.
- Report Unsafe Sites in Microsoft Edge: If you encounter suspicious websites while using Microsoft Edge, you can report them directly by selecting Settings and More > Help and Feedback > Report unsafe site. This simple step helps in marking dangerous sites and contributes to a safer browsing environment for everyone.
- Contact Microsoft Support Global Customer Service: For urgent situations where immediate assistance is needed, reaching out to Microsoft’s Global Customer Service can provide you with the necessary support and guidance on the steps to take next.
- Notify Your Local Law Enforcement: In addition to reporting the scam to Microsoft, consider notifying your local law enforcement agency. This can help in taking legal action against the scammers and protect others in your community from similar frauds.
- Windows
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
- Internet Explorer
- Stop Push Pop-ups
How to Remove Error: Ox800VDS from Windows.
Step 1: Scan for Error: Ox800VDS with SpyHunter Anti-Malware Tool



Step 2: Boot Your PC In Safe Mode





Step 3: Uninstall Error: Ox800VDS and related software from Windows
Uninstall Steps for Windows 11
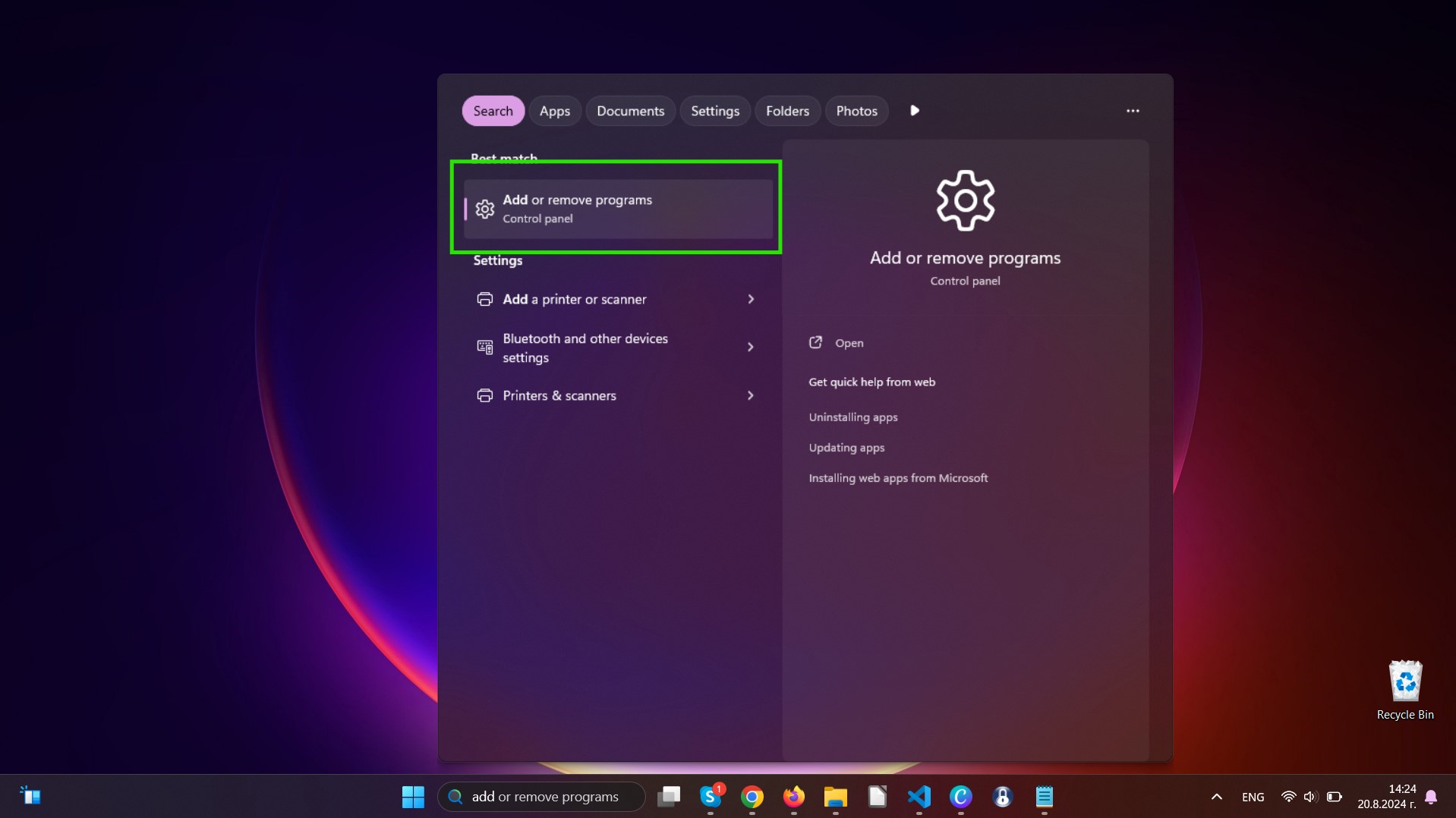
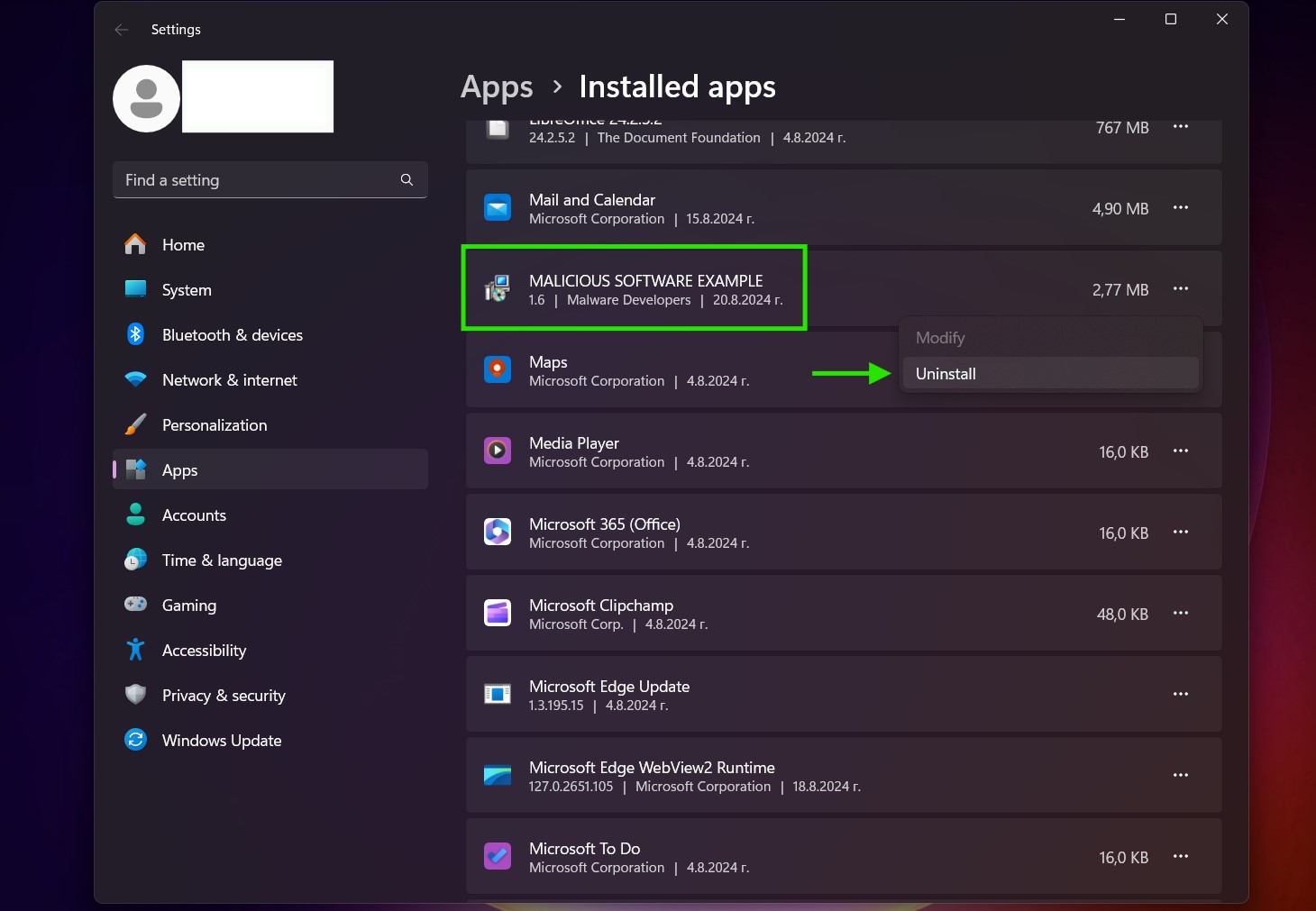
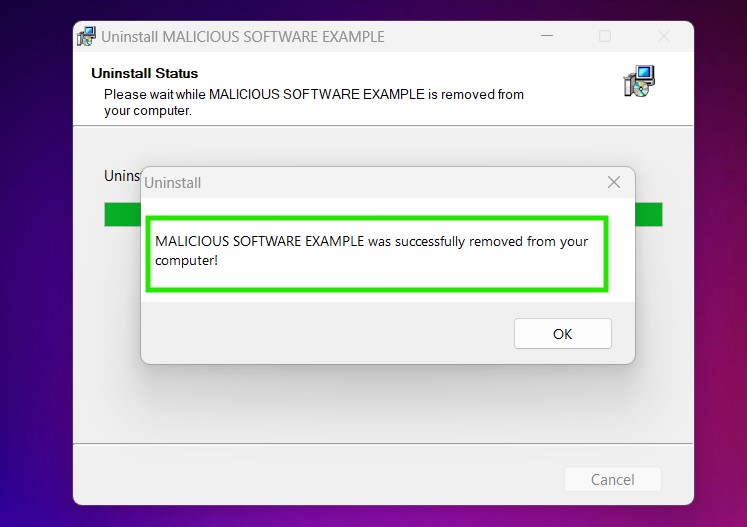
Uninstall Steps for Windows 10 and Older Versions
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully uninstall most programs.
Follow the instructions above and you will successfully uninstall most programs.
Step 4: Clean Any registries, Created by Error: Ox800VDS on Your PC.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Error: Ox800VDS there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Video Removal Guide for Error: Ox800VDS (Windows).
Get rid of Error: Ox800VDS from Mac OS X.
Step 1: Uninstall Error: Ox800VDS and remove related files and objects
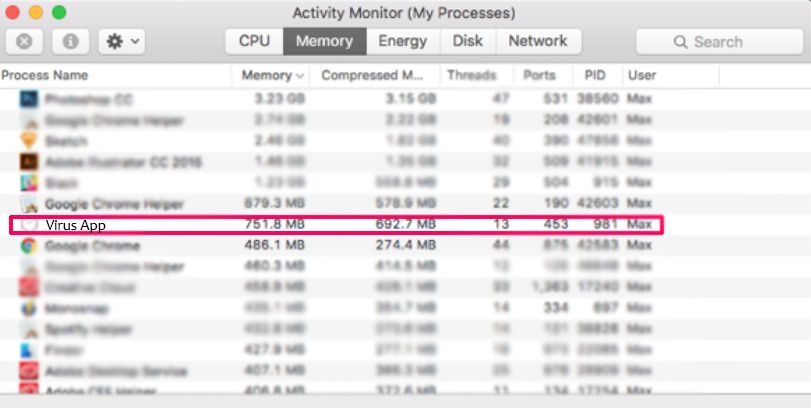
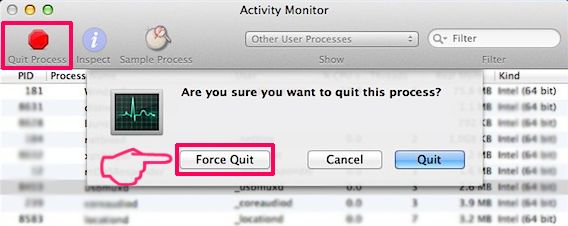
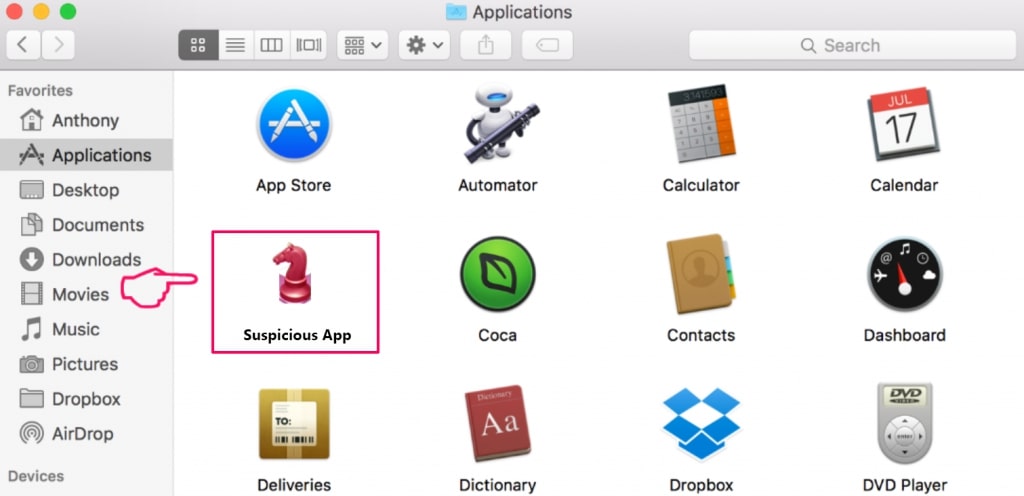
Your Mac will then show you a list of items that start automatically when you log in. Look for any suspicious apps identical or similar to Error: Ox800VDS. Check the app you want to stop from running automatically and then select on the Minus (“-“) icon to hide it.
- Go to Finder.
- In the search bar type the name of the app that you want to remove.
- Above the search bar change the two drop down menus to “System Files” and “Are Included” so that you can see all of the files associated with the application you want to remove. Bear in mind that some of the files may not be related to the app so be very careful which files you delete.
- If all of the files are related, hold the ⌘+A buttons to select them and then drive them to “Trash”.
In case you cannot remove Error: Ox800VDS via Step 1 above:
In case you cannot find the virus files and objects in your Applications or other places we have shown above, you can manually look for them in the Libraries of your Mac. But before doing this, please read the disclaimer below:
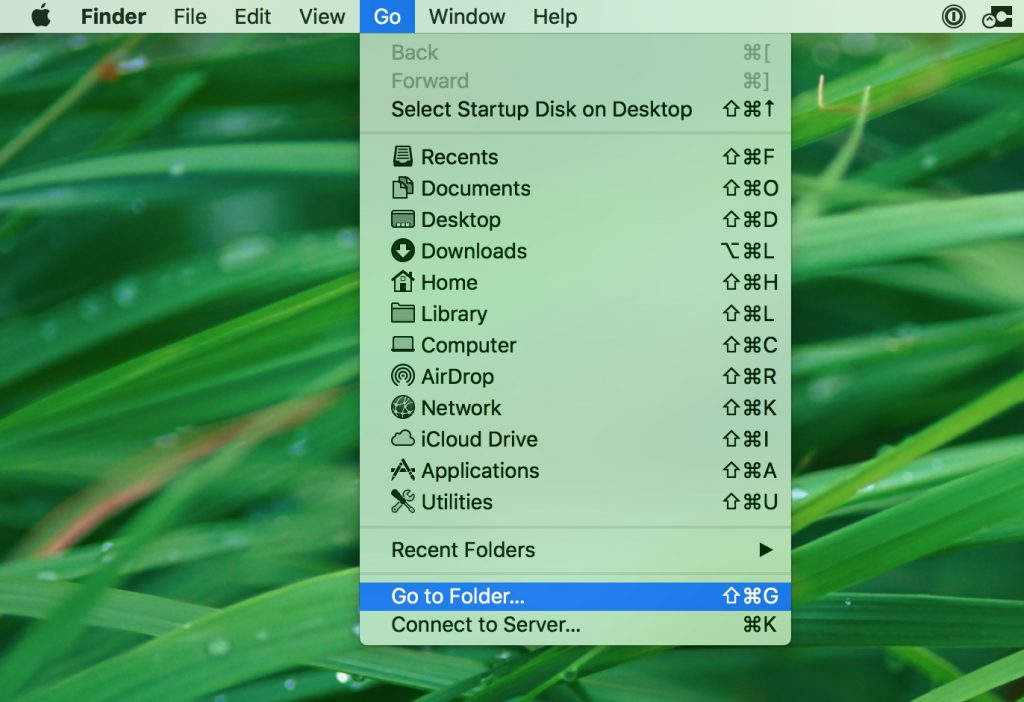
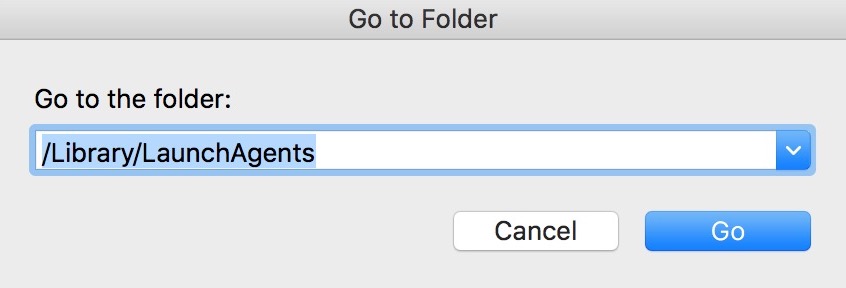
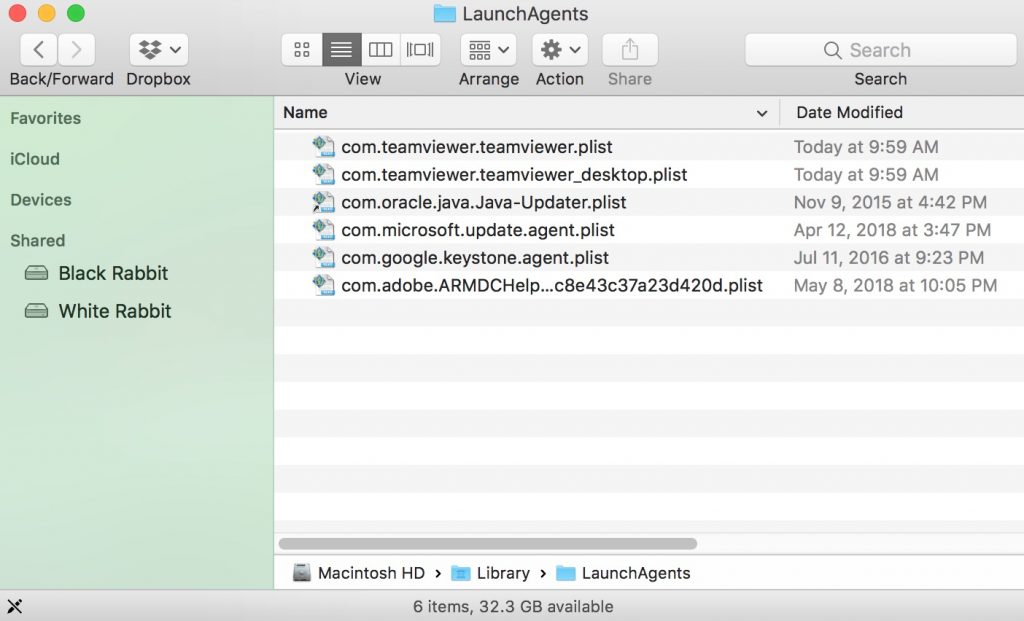
You can repeat the same procedure with the following other Library directories:
→ ~/Library/LaunchAgents
/Library/LaunchDaemons
Tip: ~ is there on purpose, because it leads to more LaunchAgents.
Step 2: Scan for and remove Error: Ox800VDS files from your Mac
When you are facing problems on your Mac as a result of unwanted scripts and programs such as Error: Ox800VDS, the recommended way of eliminating the threat is by using an anti-malware program. SpyHunter for Mac offers advanced security features along with other modules that will improve your Mac’s security and protect it in the future.
Video Removal Guide for Error: Ox800VDS (Mac)
Remove Error: Ox800VDS from Google Chrome.
Step 1: Start Google Chrome and open the drop menu
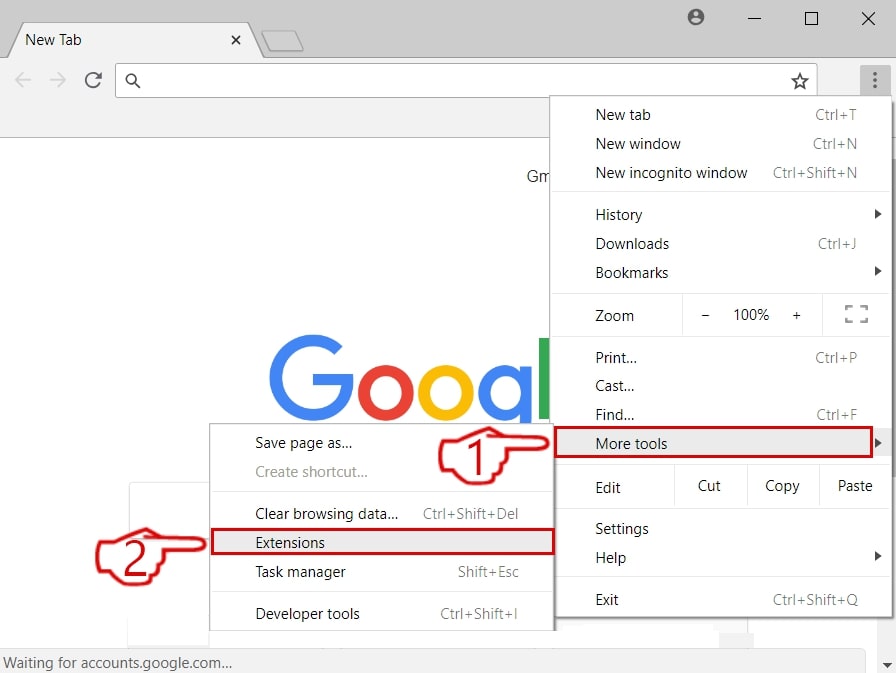
Step 2: Move the cursor over "Tools" and then from the extended menu choose "Extensions"
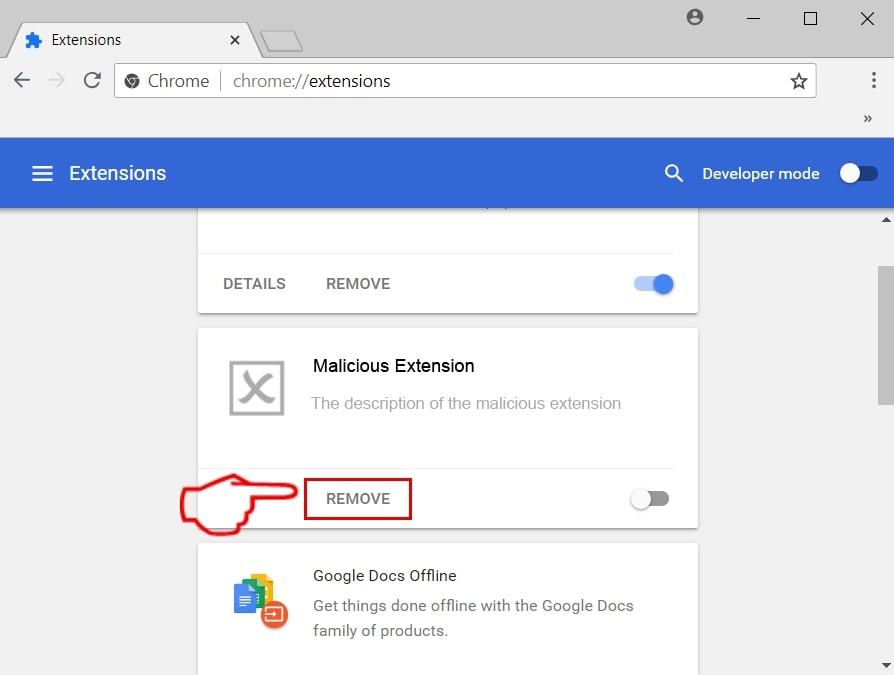
Step 3: From the opened "Extensions" menu locate the unwanted extension and click on its "Remove" button.
Step 4: After the extension is removed, restart Google Chrome by closing it from the red "X" button at the top right corner and start it again.
Erase Error: Ox800VDS from Mozilla Firefox.
Step 1: Start Mozilla Firefox. Open the menu window:
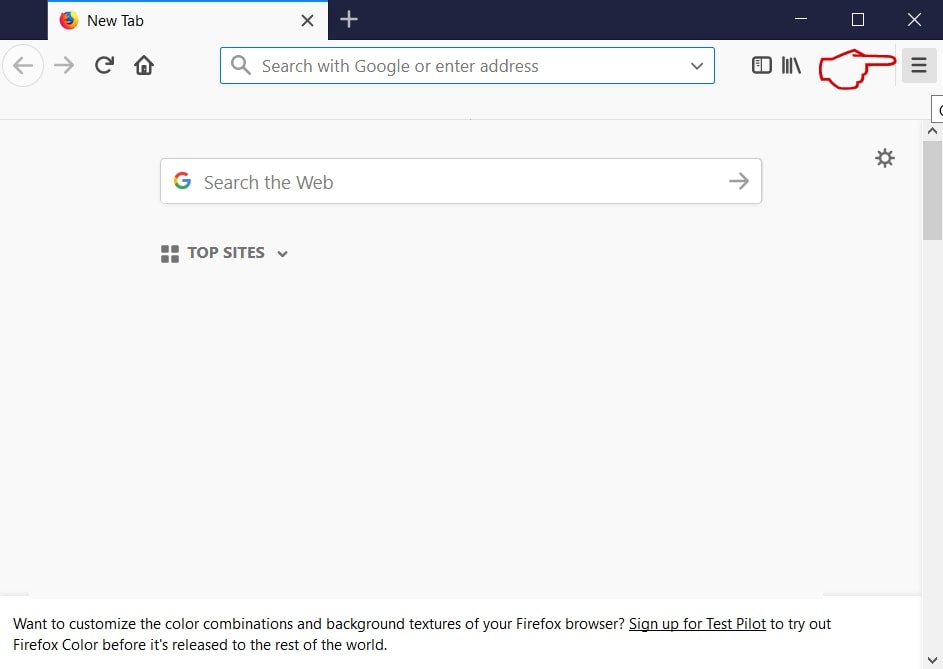
Step 2: Select the "Add-ons" icon from the menu.
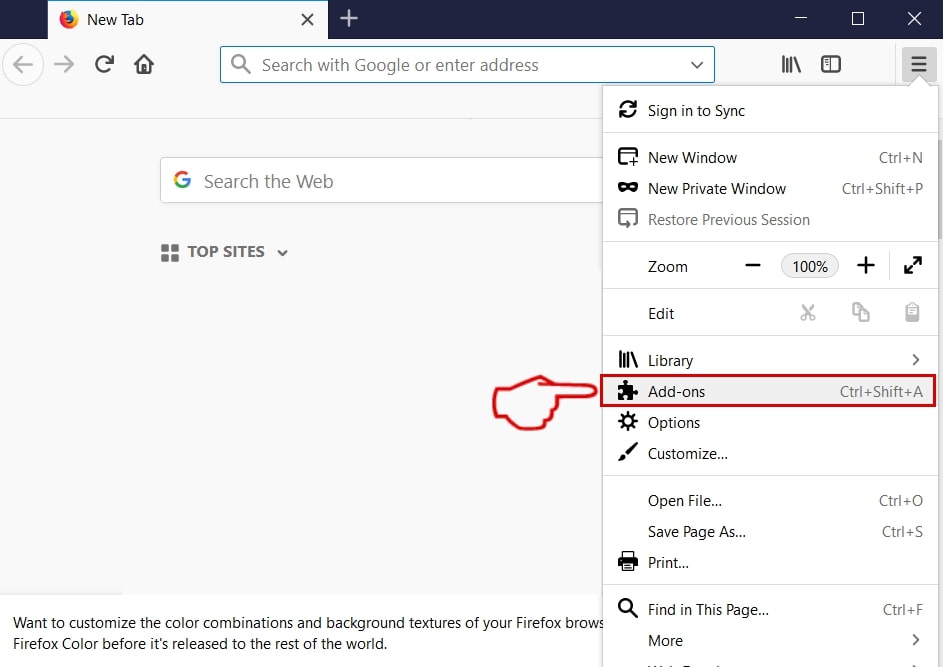
Step 3: Select the unwanted extension and click "Remove"

Step 4: After the extension is removed, restart Mozilla Firefox by closing it from the red "X" button at the top right corner and start it again.
Uninstall Error: Ox800VDS from Microsoft Edge.
Step 1: Start Edge browser.
Step 2: Open the drop menu by clicking on the icon at the top right corner.
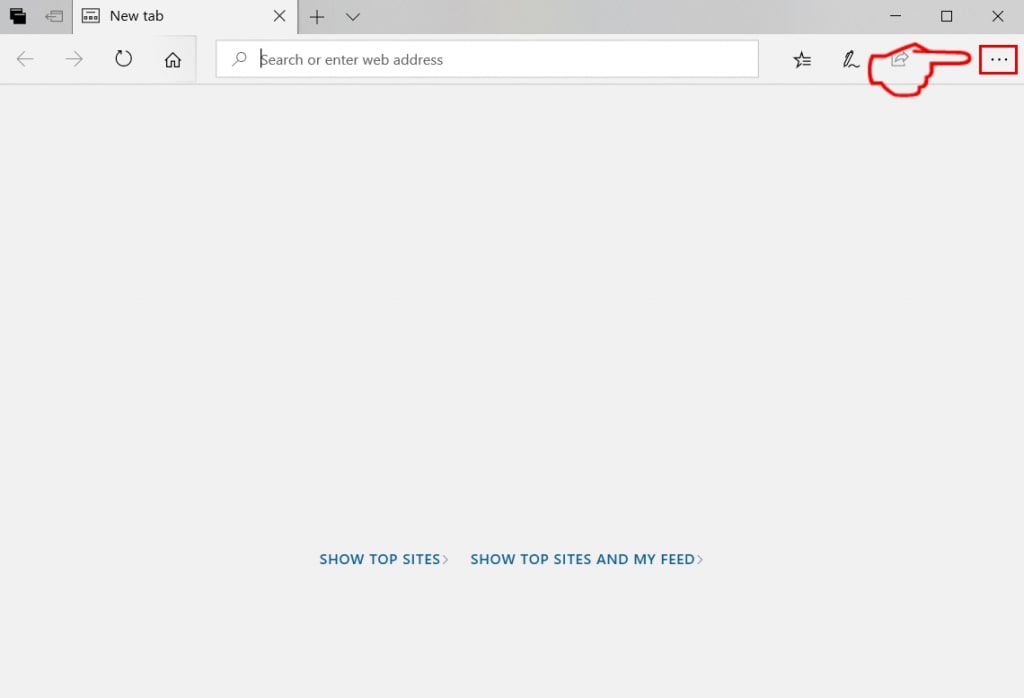
Step 3: From the drop menu select "Extensions".
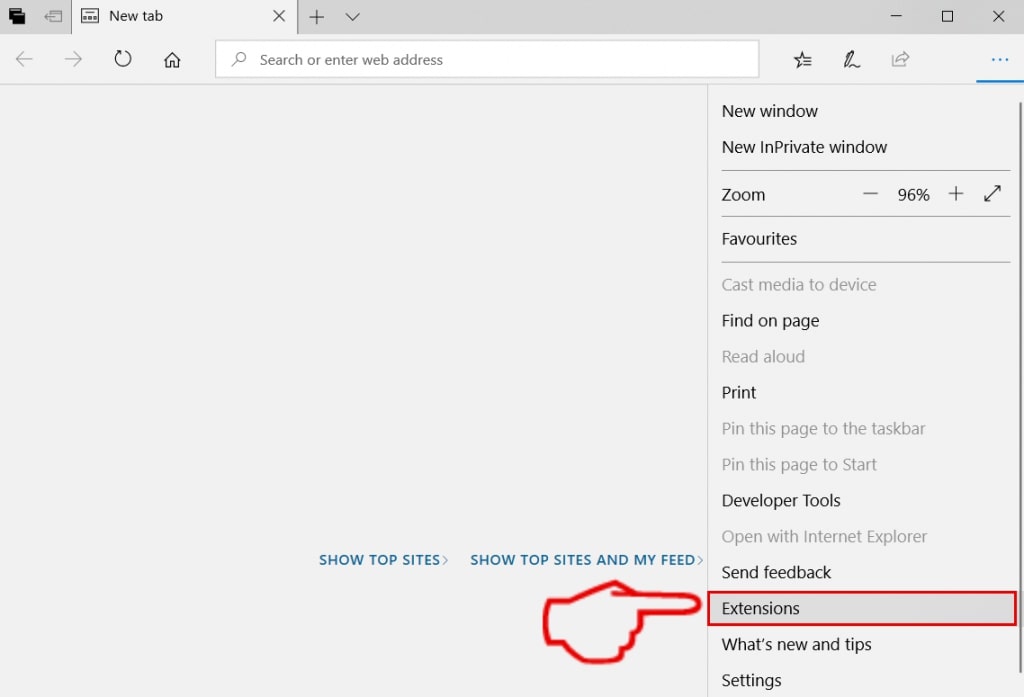
Step 4: Choose the suspected malicious extension you want to remove and then click on the gear icon.
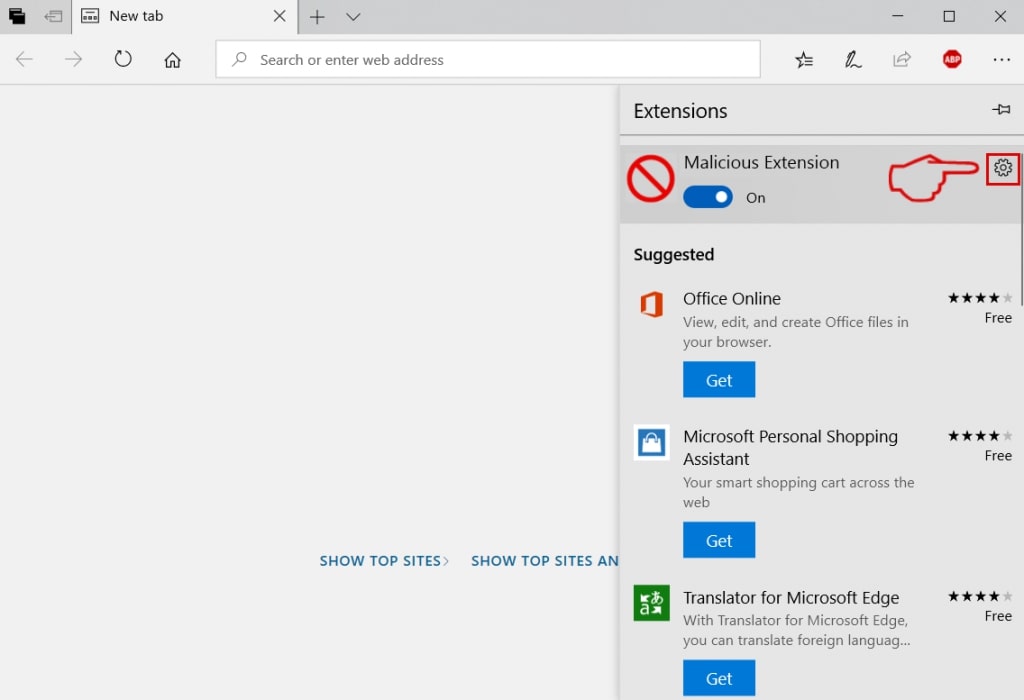
Step 5: Remove the malicious extension by scrolling down and then clicking on Uninstall.
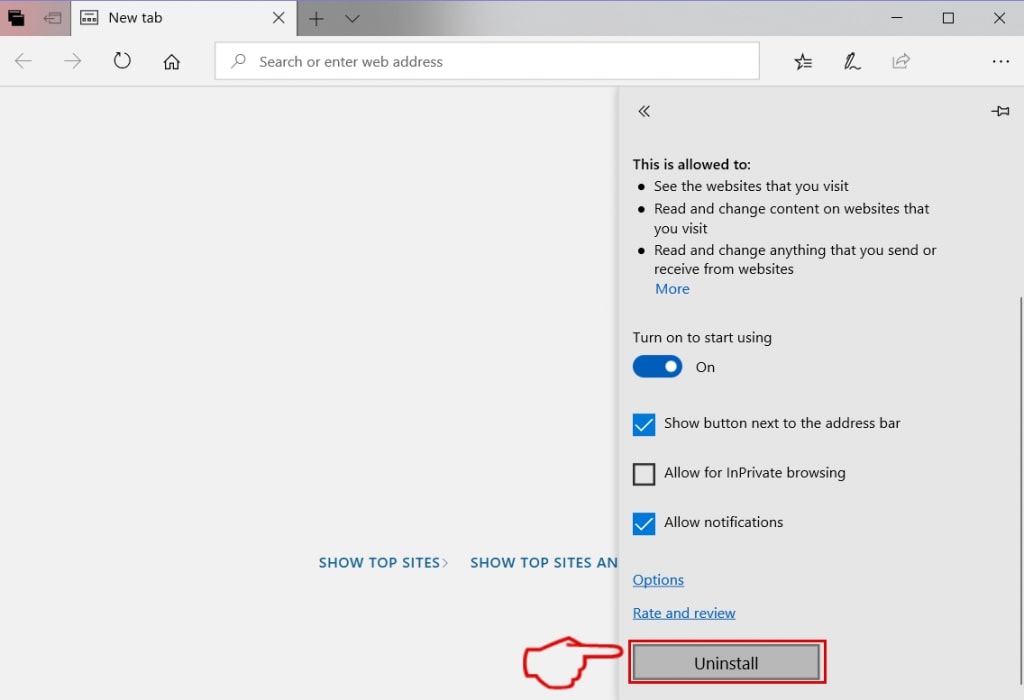
Remove Error: Ox800VDS from Safari
Step 1: Start the Safari app.
Step 2: After hovering your mouse cursor to the top of the screen, click on the Safari text to open its drop down menu.
Step 3: From the menu, click on "Preferences".
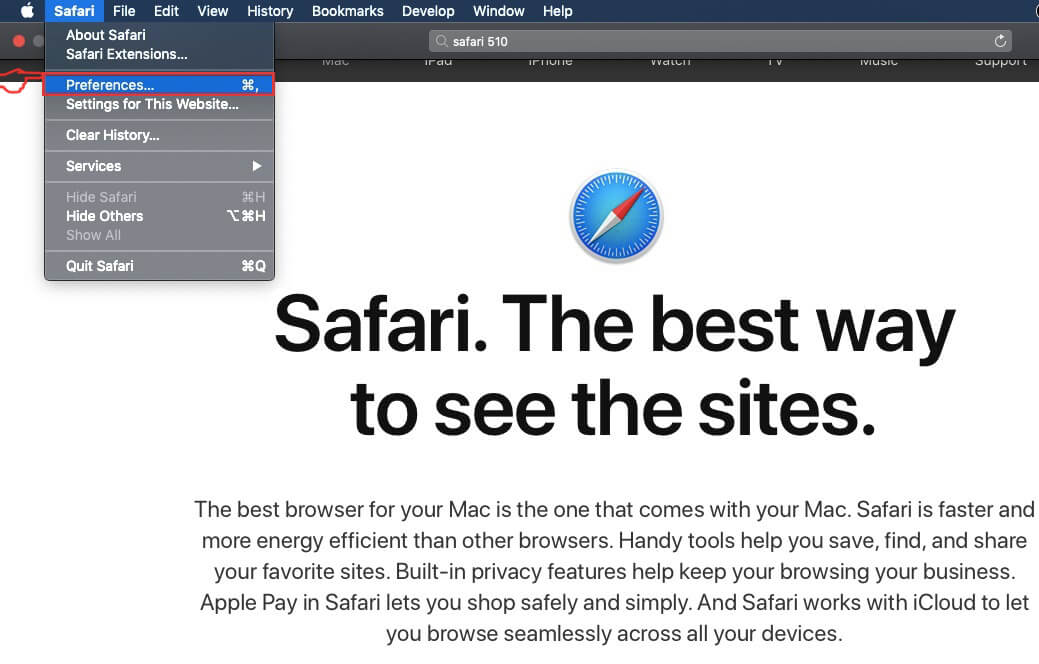
Step 4: After that, select the 'Extensions' Tab.
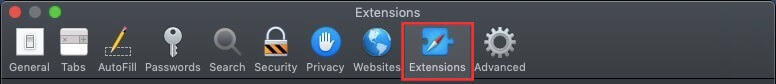
Step 5: Click once on the extension you want to remove.
Step 6: Click 'Uninstall'.
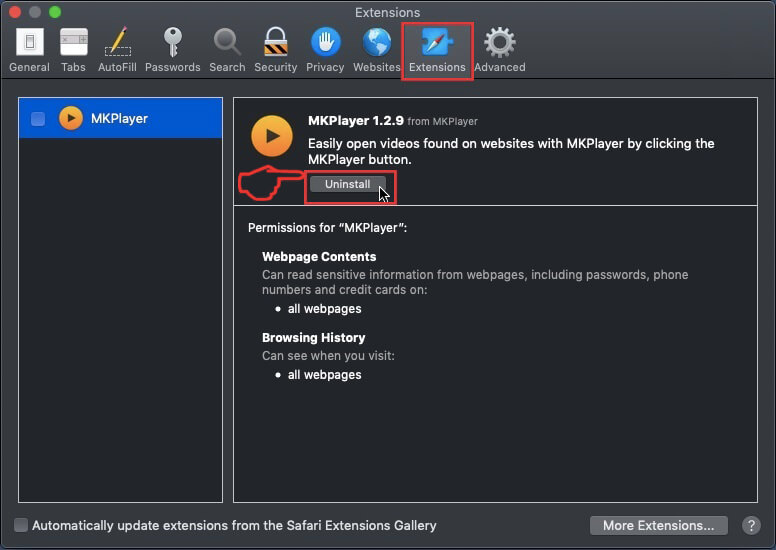
A pop-up window will appear asking for confirmation to uninstall the extension. Select 'Uninstall' again, and the Error: Ox800VDS will be removed.
Eliminate Error: Ox800VDS from Internet Explorer.
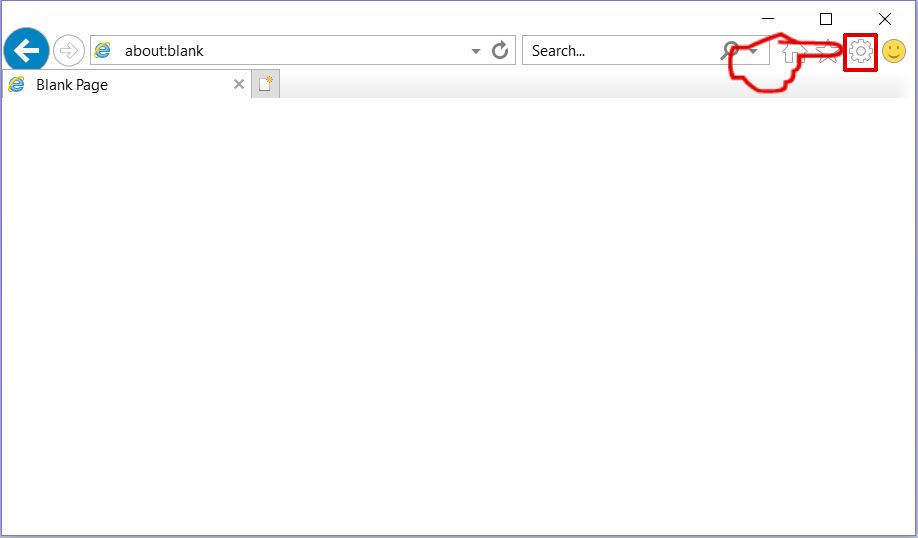
Step 1: Start Internet Explorer.
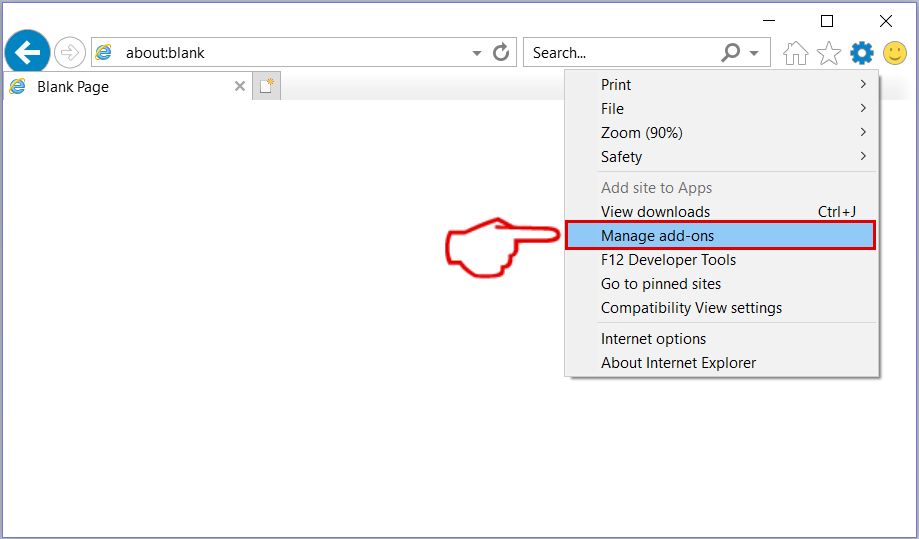
Step 2: Click on the gear icon labeled 'Tools' to open the drop menu and select 'Manage Add-ons'
Step 3: In the 'Manage Add-ons' window.
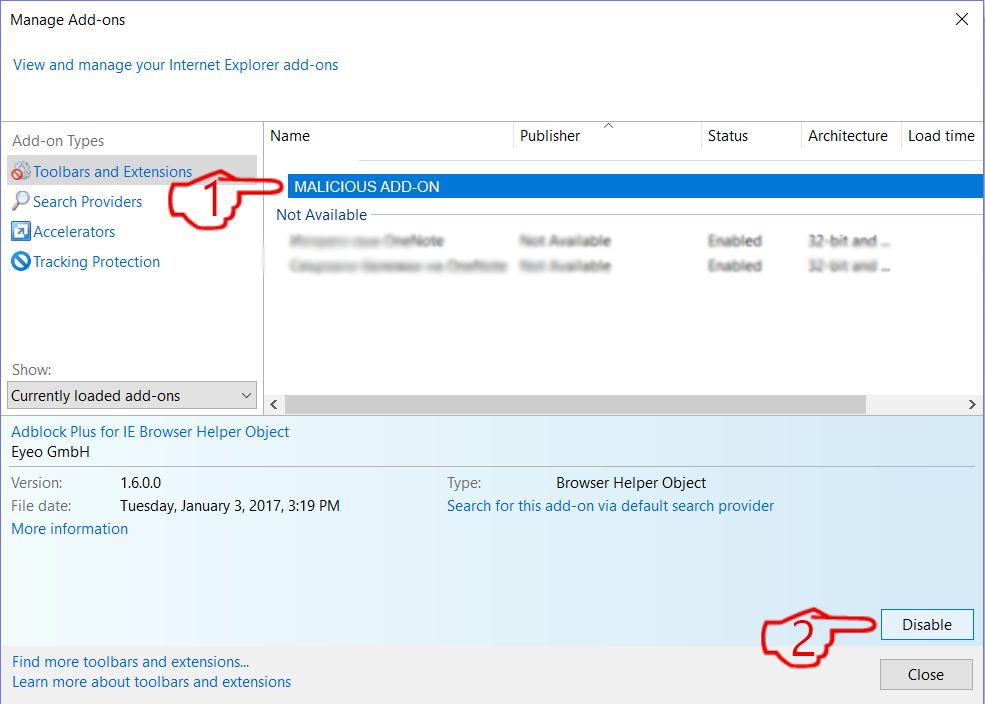
Step 4: Select the extension you want to remove and then click 'Disable'. A pop-up window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be disabled as well. Leave all the boxes checked, and click 'Disable'.
Step 5: After the unwanted extension has been removed, restart Internet Explorer by closing it from the red 'X' button located at the top right corner and start it again.
Remove Push Notifications from Your Browsers
Turn Off Push Notifications from Google Chrome
To disable any Push Notices from Google Chrome browser, please follow the steps below:
Step 1: Go to Settings in Chrome.
Step 2: In Settings, select “Advanced Settings”:
Step 3: Click “Content Settings”:
Step 4: Open “Notifications”:
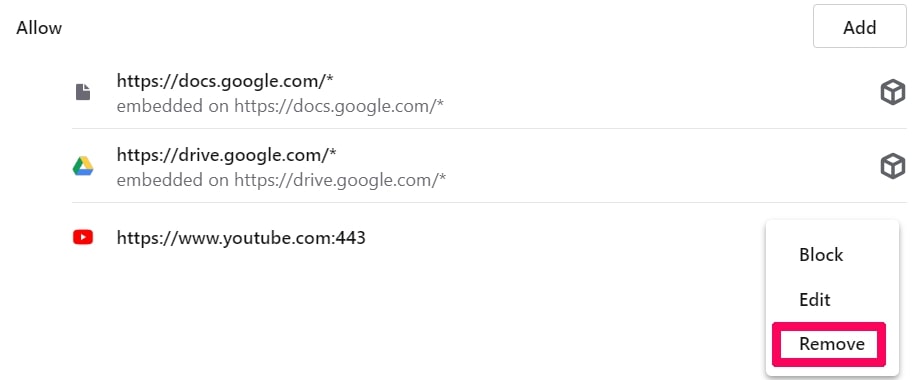
Step 5: Click the three dots and choose Block, Edit or Remove options:

Remove Push Notifications on Firefox
Step 1: Go to Firefox Options.
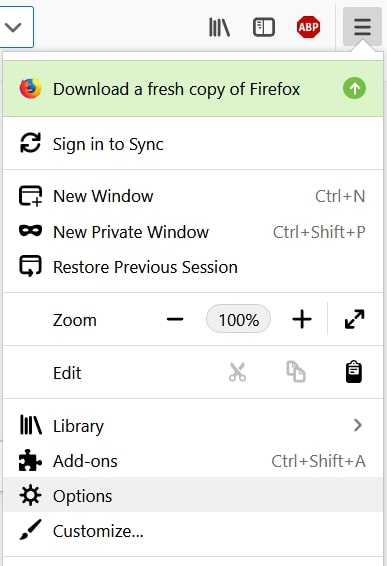
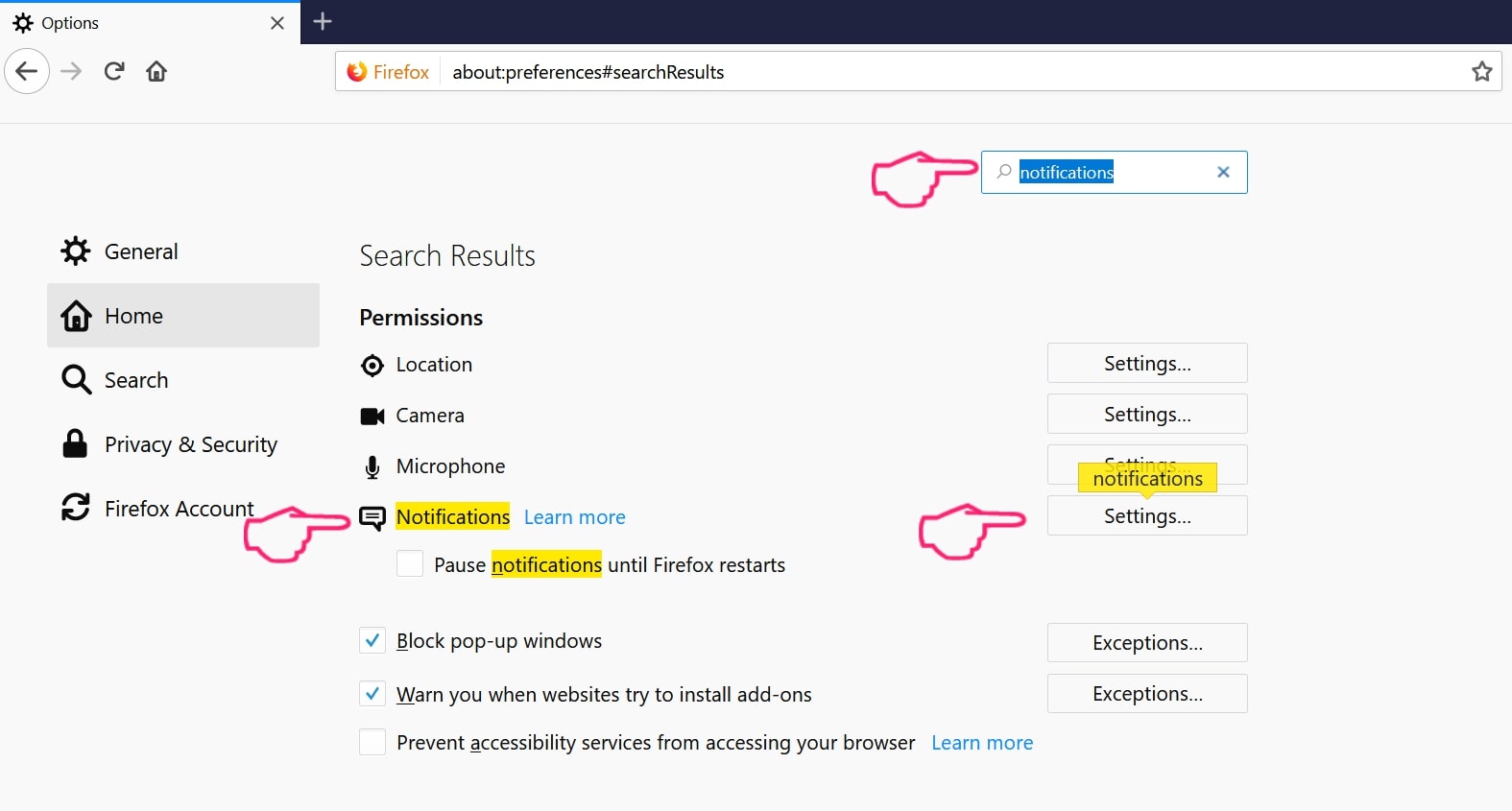
Step 2: Go to “Settings”, type “notifications” in the search bar and click "Settings":
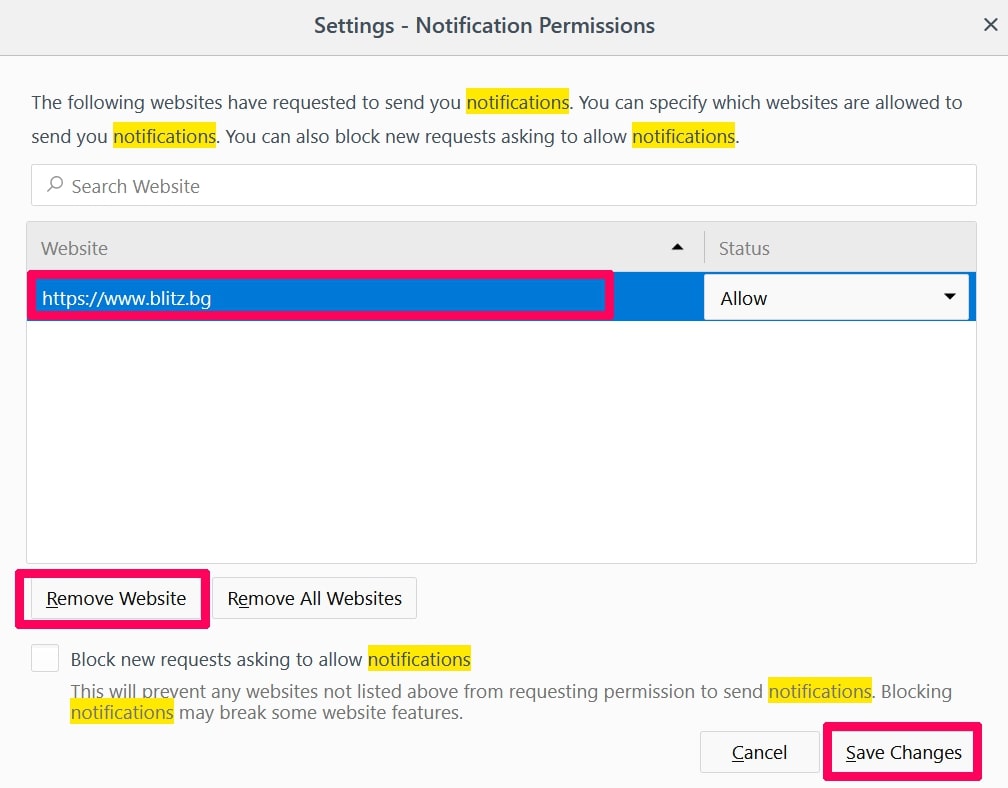
Step 3: Click “Remove” on any site you wish notifications gone and click “Save Changes”
Stop Push Notifications on Opera
Step 1: In Opera, press ALT+P to go to Settings.
Step 2: In Setting search, type “Content” to go to Content Settings.
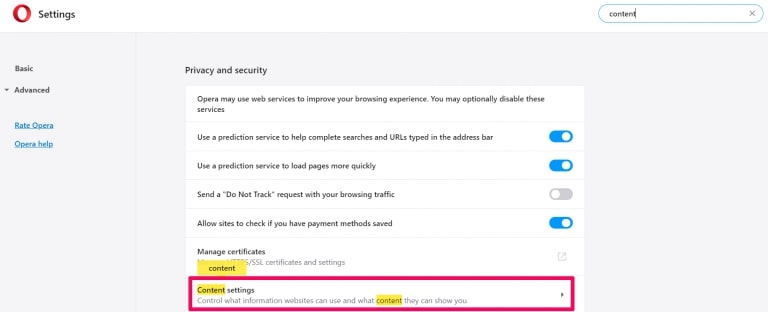
Step 3: Open Notifications:
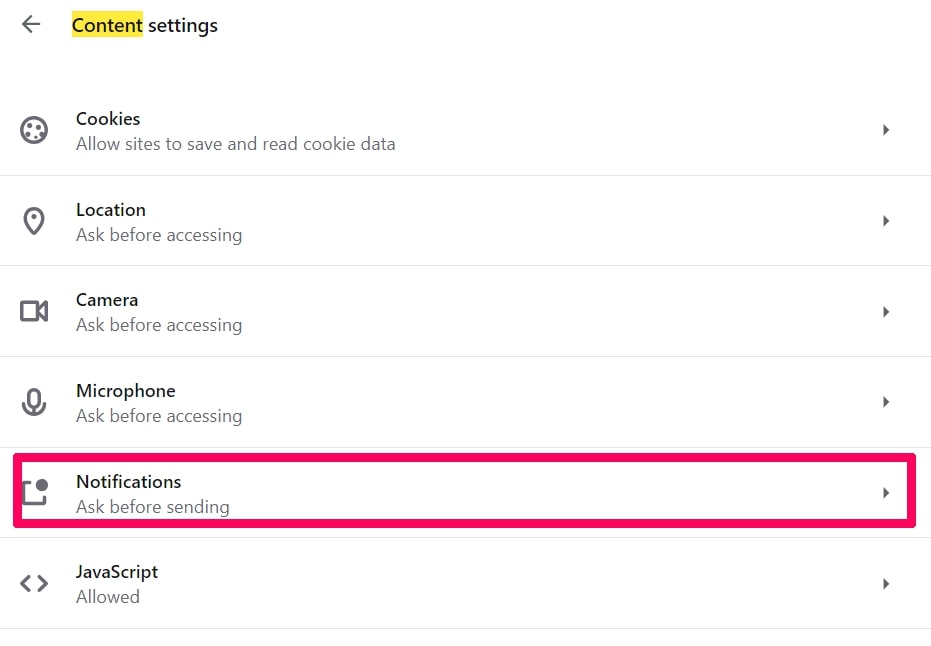
Step 4: Do the same as you did with Google Chrome (explained below):
Eliminate Push Notifications on Safari
Step 1: Open Safari Preferences.
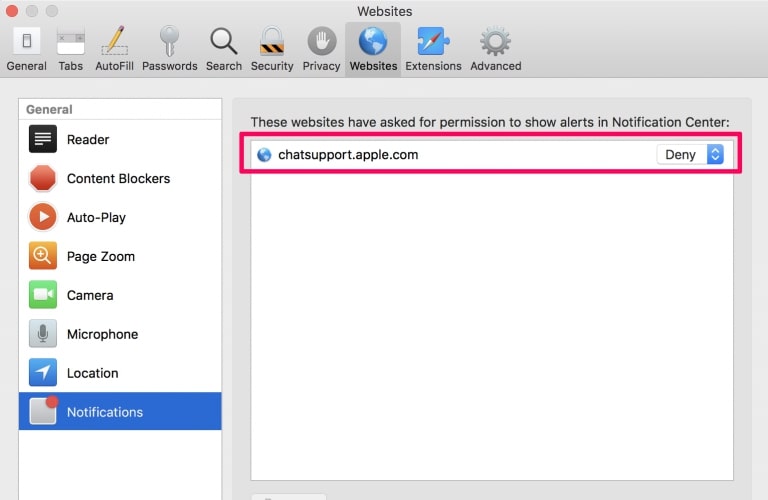
Step 2: Choose the domain from where you like push pop-ups gone and change to "Deny" from "Allow".
Error: Ox800VDS-FAQ
What Is Error: Ox800VDS?
The Error: Ox800VDS threat is adware or browser redirect virus.
It may slow your computer down significantly and display advertisements. The main idea is for your information to likely get stolen or more ads to appear on your device.
The creators of such unwanted apps work with pay-per-click schemes to get your computer to visit risky or different types of websites that may generate them funds. This is why they do not even care what types of websites show up on the ads. This makes their unwanted software indirectly risky for your OS.
What Are the Symptoms of Error: Ox800VDS?
There are several symptoms to look for when this particular threat and also unwanted apps in general are active:
Symptom #1: Your computer may become slow and have poor performance in general.
Symptom #2: You have toolbars, add-ons or extensions on your web browsers that you don't remember adding.
Symptom #3: You see all types of ads, like ad-supported search results, pop-ups and redirects to randomly appear.
Symptom #4: You see installed apps on your Mac running automatically and you do not remember installing them.
Symptom #5: You see suspicious processes running in your Task Manager.
If you see one or more of those symptoms, then security experts recommend that you check your computer for viruses.
What Types of Unwanted Programs Are There?
According to most malware researchers and cyber-security experts, the threats that can currently affect your device can be rogue antivirus software, adware, browser hijackers, clickers, fake optimizers and any forms of PUPs.
What to Do If I Have a "virus" like Error: Ox800VDS?
With few simple actions. First and foremost, it is imperative that you follow these steps:
Step 1: Find a safe computer and connect it to another network, not the one that your Mac was infected in.
Step 2: Change all of your passwords, starting from your email passwords.
Step 3: Enable two-factor authentication for protection of your important accounts.
Step 4: Call your bank to change your credit card details (secret code, etc.) if you have saved your credit card for online shopping or have done online activities with your card.
Step 5: Make sure to call your ISP (Internet provider or carrier) and ask them to change your IP address.
Step 6: Change your Wi-Fi password.
Step 7: (Optional): Make sure to scan all of the devices connected to your network for viruses and repeat these steps for them if they are affected.
Step 8: Install anti-malware software with real-time protection on every device you have.
Step 9: Try not to download software from sites you know nothing about and stay away from low-reputation websites in general.
If you follow these recommendations, your network and all devices will become significantly more secure against any threats or information invasive software and be virus free and protected in the future too.
How Does Error: Ox800VDS Work?
Once installed, Error: Ox800VDS can collect data using trackers. This data is about your web browsing habits, such as the websites you visit and the search terms you use. It is then used to target you with ads or to sell your information to third parties.
Error: Ox800VDS can also download other malicious software onto your computer, such as viruses and spyware, which can be used to steal your personal information and show risky ads, that may redirect to virus sites or scams.
Is Error: Ox800VDS Malware?
The truth is that PUPs (adware, browser hijackers) are not viruses, but may be just as dangerous since they may show you and redirect you to malware websites and scam pages.
Many security experts classify potentially unwanted programs as malware. This is because of the unwanted effects that PUPs can cause, such as displaying intrusive ads and collecting user data without the user’s knowledge or consent.
About the Error: Ox800VDS Research
The content we publish on SensorsTechForum.com, this Error: Ox800VDS how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific, adware-related problem, and restore your browser and computer system.
How did we conduct the research on Error: Ox800VDS?
Please note that our research is based on independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware, adware, and browser hijacker definitions.
Furthermore, the research behind the Error: Ox800VDS threat is backed with VirusTotal.
To better understand this online threat, please refer to the following articles which provide knowledgeable details.


