 The red variant of Cerber ransomware keeps being the persistent and savage beast in the malware world. The virus does not have much improvements since the red version came out, but only few modifications in it’s code. These at first hand incremental changes in the virus were actually focused on interacting with database processes and shutting them down in order to uninterruptedly encrypt databases.
The red variant of Cerber ransomware keeps being the persistent and savage beast in the malware world. The virus does not have much improvements since the red version came out, but only few modifications in it’s code. These at first hand incremental changes in the virus were actually focused on interacting with database processes and shutting them down in order to uninterruptedly encrypt databases.
Why So Many Versions?
Since malware authors often come up with different improvements and in the old habit of renaming a version to be a newer one after the improvements, there have so far been many Cerber iterations. However, the changes were not massive, for example some partial changes in the code of the virus or changes in the ransom note or adding an audio message. Since they were so much, the authors of Cerber ransomware may have stopped adding version numbers, like the previously detected 4.1.1, 4.1.2, etc. iterations exactly for that reason.
What is New In HELP_HELP_HELP Cerber?
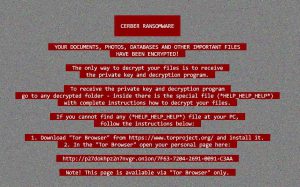
Being as it is, this version almost does not have anything different than the previous Red Cerber variants, primarily because the virus simply works and since the 1st version which is now decryptable, no other version of this virus is able to be decrypted.
The differences however are in how the virus actually infects. While Cerber has preserved the good old e-mail spamming methods, the virus uses many different exploit kits and distribution malware types, like Trojans, malicious scripts and even worm-like malware to maximize the infection rate.
Cerber still uses the same PseudoDarkLeech RIG-V exploit kit and what is interesting about it is that via UDP, similar traffic is noticed with another ransomware virus, which many refer to as Sage Ransomware.
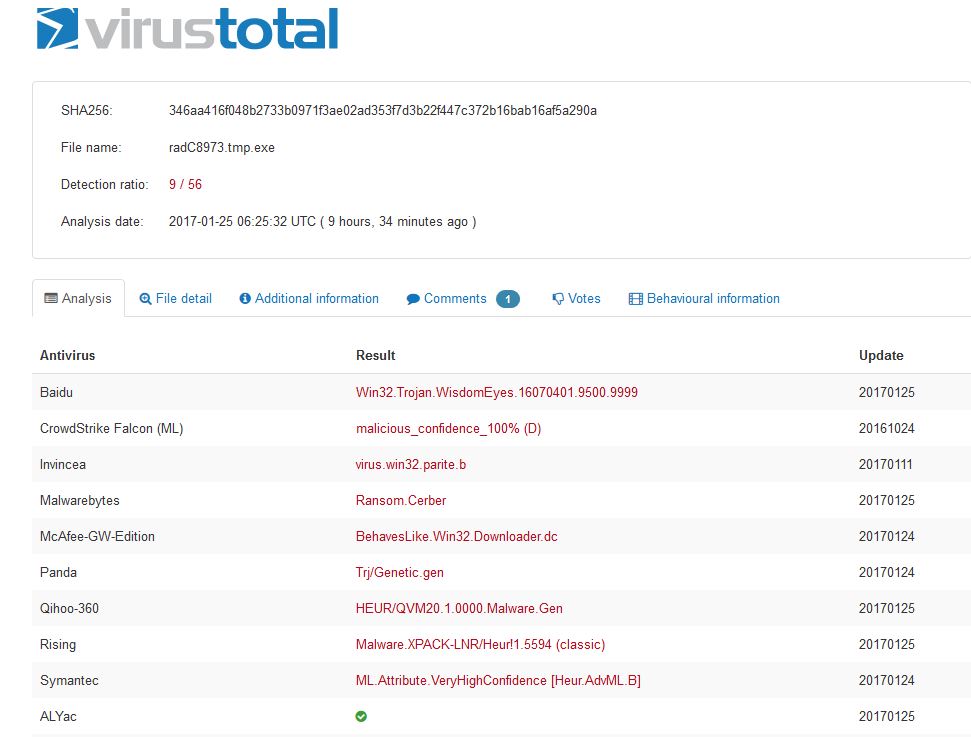
What is more, zerophagemalware reports that Cerber still has a low detection rate dropping a randomly named .exe payload:

Conclusion
As a bottom line, Cerber ransomware may seem different, but every new version has either some small improvement in it or changes in how the virus infects. This latest version has many changes when it comes to database encryption and shutting down processes of Windows that may interfere with the encryption process. Whatever the case may be, most Cerber infections are spread via e-mail, so our advice to users is to read our related article below and learn how to protect yourself from such e-mails: