Mobile privacy is an area that every user should be paying attention to. In other words, users should be very concerned with the privacy of their smartphones and the personal information shared with app developers. And there are is plenty of reasons for that.
New statistics reveal that the average smartphone user has between 60 and 90 apps installed on their devices. Most of these apps request some sort of information about you and the device you are using. Requested personal information may include name, email address, or even physical address.
But because smartphones are so powerful, they can also get quite a bit more than that, such as your exact location, Symantec researchers pointed out. Other apps can be even more invasive requesting access to the device’s camera or microphone. While user request is demanded prior to the information collection, the level of access some access have to our personal data is still startling.
Did you know that 45 percent of the most popular Android apps and 25 percent of the most popular iOS apps request location tracking, for example? Or that 46 percent of popular Android apps and 25 percent of popular iOS apps request permission to access your device’s camera? Some Android apps even ask you to give them access to your SMS messages and phone call logs.
Researchers decided to dig deeper and to find out exactly what type of data installed apps are looking to collect. To do this estimation, the expert team downloaded and analyzed the top 100 free apps on Google Play store and Apple App Store. For each app, the researchers tried to uncover two things mainly – the volume of personal information shared with the particular app and smartphone features access by the app.
This is the moment to point out that most apps require device permissions and user consent, and in most cases there is reason behind these requests. For example, a taxi app will need to be able to access a user’s location in order to tell the driver where to go, the researchers pointed out. That is why the researchers’ curiosity lies elsewhere – in answering the question whether app developers were doing everything in their power to protect the privacy of their users.
PII Requested by the Top 100 Free Android/ iOS Apps
What type of personally identifiable information is requested by these Android apps? It turns out that the most common piece of PII which is shared with apps is email addresses. 48 percent of the iOS apps and 44 percent of the Android apps of the analyzed apps request email addresses, the research found.
The next most common piece of PII was the username (which is usually someone’s full name as they’ve entered it on social networking sites or on the app), which was shared with 33 percent of iOS apps and 30 percent of Android apps. Phone numbers, meanwhile, were shared with 12 percent of iOS apps and 9 percent of Android apps. Finally, the user’s address was shared with 4 percent of iOS apps and 5 percent of Android apps.
It should be pointed out that these statistics don’t fully account for the full amount of personally identifiable information users share with their apps.
Some of the apps integrate with social media to enable the user to log into the app using their social media account, thus allowing the app to post directly to the social networking site. Even though this may seem helpful to the user, this “symbiotic relationship” also allows the app to collect user data from the social media account, while also allowing the social media service to collect data from the app.
The researchers were able to uncover the type of PII gathered by iOS apps using social media integration but they were unable to do the same for Android. The reason is that the apps in question all employed Facebook’s widely used Graph application programming interface (API) and the Android version of Graph uses certificate pinning, which prevented the team from seeing what PII was being shared.
More about the Facebook Graph
Facebook Graph was used by Cambridge Analytica to compile personal information relating to 87 million Facebook users. As you know, this information was later used in targeted campaigns on social media during the 2016 U.S. presidential election campaign.
In July, Facebook announced several Facebook API changes some of which concern developers as several APIs were deprecated, such as the Graph API Explorer App, Profile Expression Kit, Trending API, the Signal tool, Trending Topics, Hashtag Voting, Topic Search, Topic Insights, Topic Feed, and Public Figure.
In addition, Facebook Graph is one of the most popular integration services, but it isn’t the most widely used. The researchers’ analysis shows that 47 percent of Android apps and 29 percent of iOS apps offered the Google integration service, while 41 percent of Android apps and 26 percent of iOS apps offered the Facebook Graph API service.
Smartphone Features Also Accessed
PII aside, there are apps that need permission to access specific features on the device such as the camera in the case of Instagram. Some of those permissions are considered more risky than others. Indeed, these are permissions that allow access to data or resources that involve the user’s private information or could potentially affect the user’s stored data or the operation of other apps. Such risky permissions are the access to the user’s location, contacts, SMS messages, phone logs, camera, or calendar.
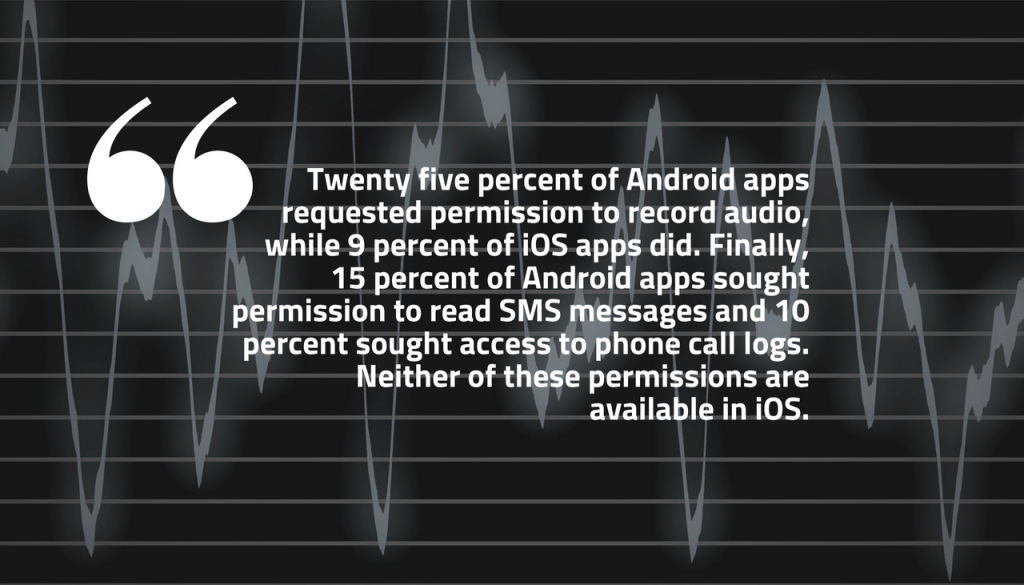
Among these risky permissions, camera access was the most requested one – 46 percent of Android apps and 25 percent of iOS apps require this access. Camera access is followed by location tracking (needed by 45 percent of Android apps and 25 percent of iOS apps). Further down the list is the permission to record audio, followed by permission to read SMS messages and access to phone call logs:
Twenty five percent of Android apps requested permission to record audio, while 9 percent of iOS apps did. Finally, 15 percent of Android apps sought permission to read SMS messages and 10 percent sought access to phone call logs. Neither of these permissions are available in iOS.
Even though the researchers named those permissions risky, they still underline the fact that there is usually a good reason for the developers to request them. That is why these permissions “should be seen as permissions the user should exercise more caution about granting, asking themselves if the app really does need this permission and if they’re comfortable granting it to this particular app”.
The Security of the Analyzed Apps
Unfortunately, some of the apps that were analyzed had very poor security and privacy implemented. More specifically, four percent of the Android apps and 3 percent of the iOS apps that were requesting risky permissions didn’t have any privacy policy. It is crucial for ay app to provide a privacy policy which clearly reveals the type of data being collected, where it is stored, who else has access to it, etc.
As for the so-called certificate pinning, it turns out that only a handful of apps implement certificate pinning at login: 8 percent of Android apps and 11 percent of iOS apps.
Certificate pinning is a security precaution that helps prevent attackers intercepting supposedly secure communications. This is done by ensuring the app only communicates with a server using the correct security certificate, the researchers explained.