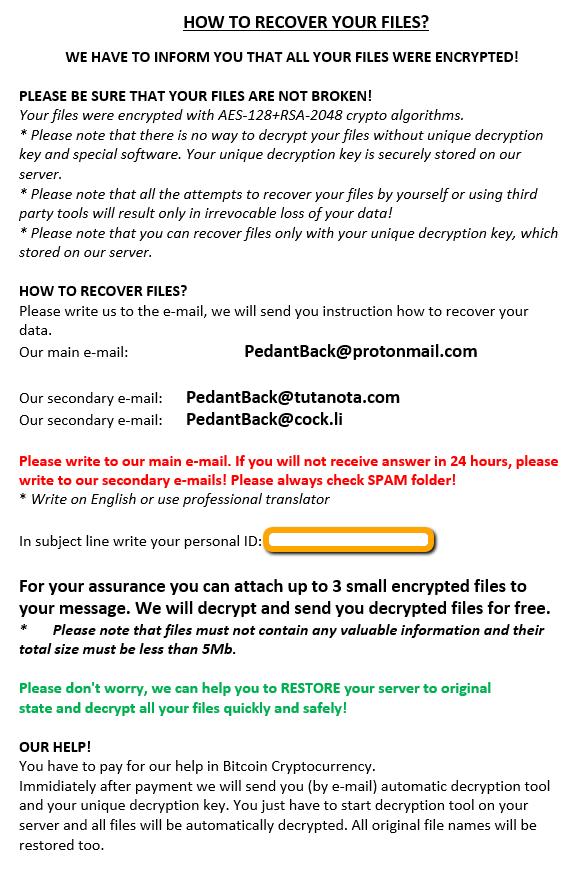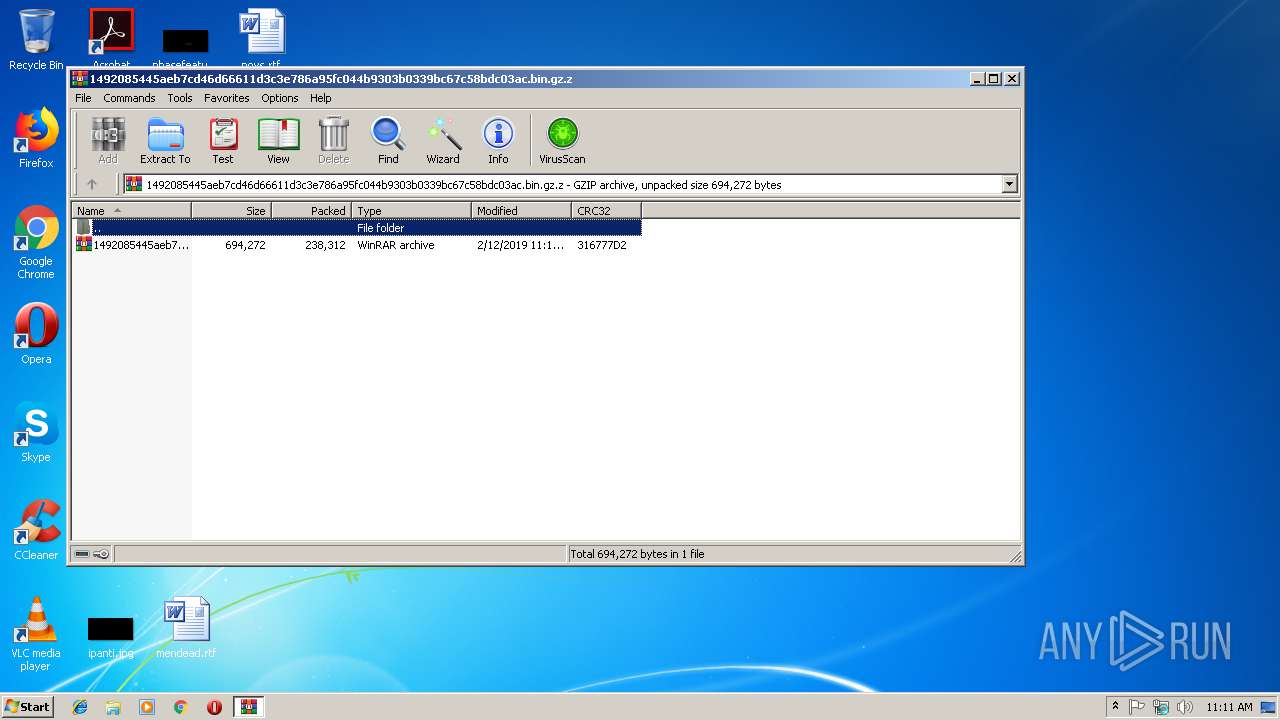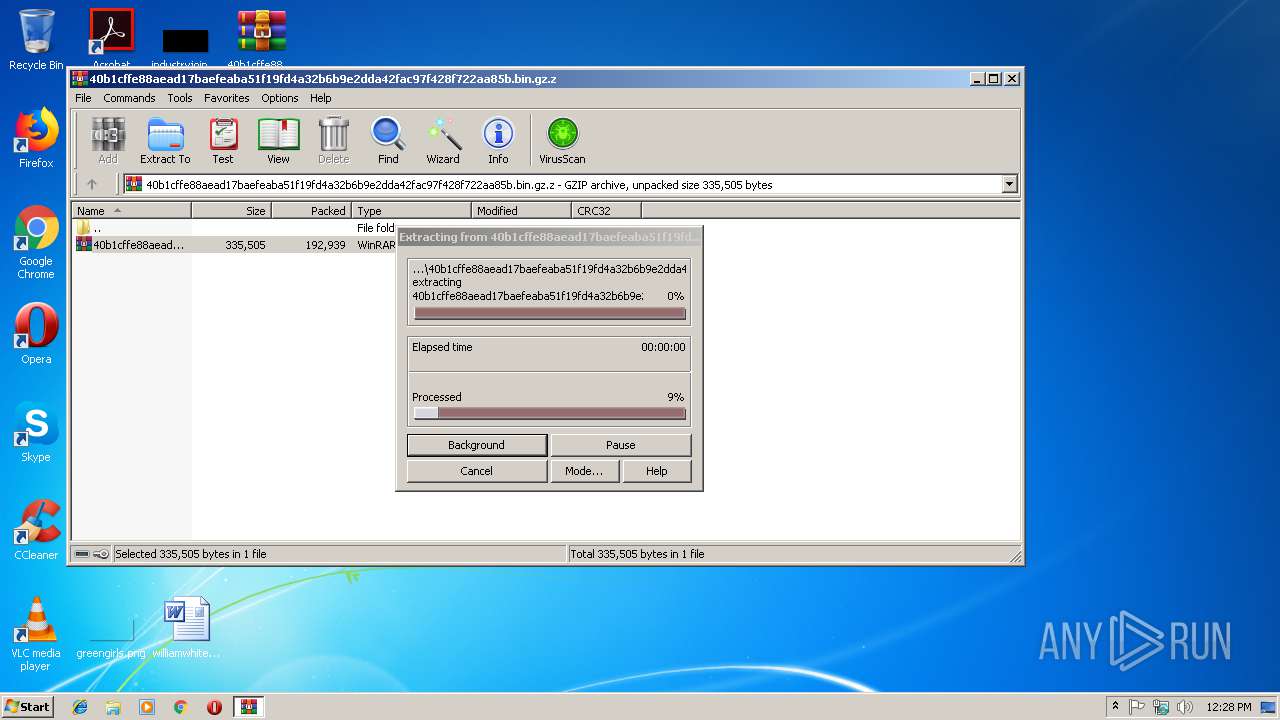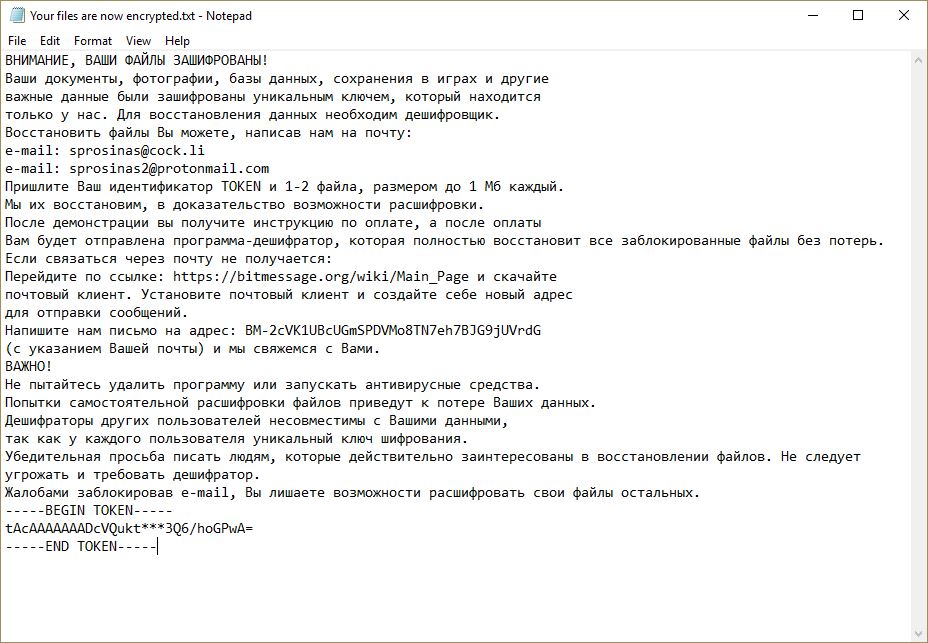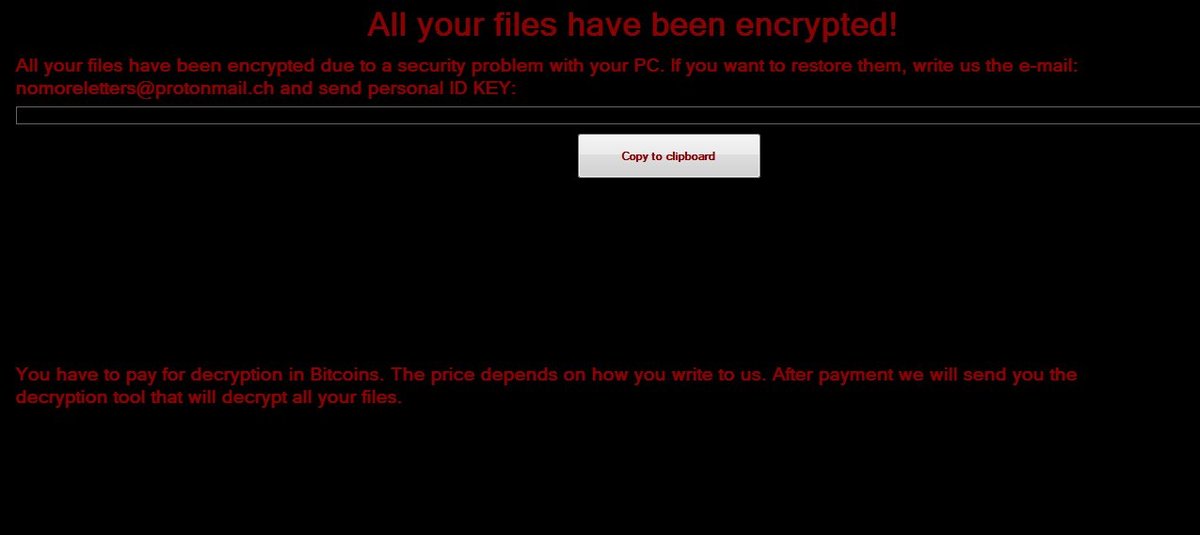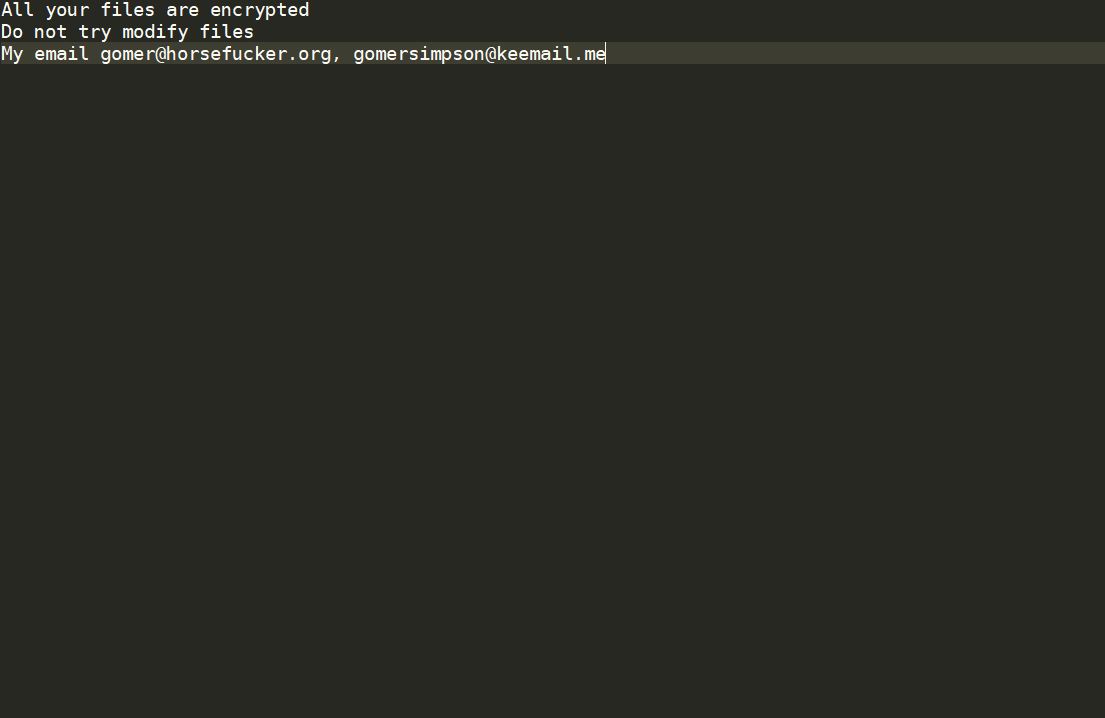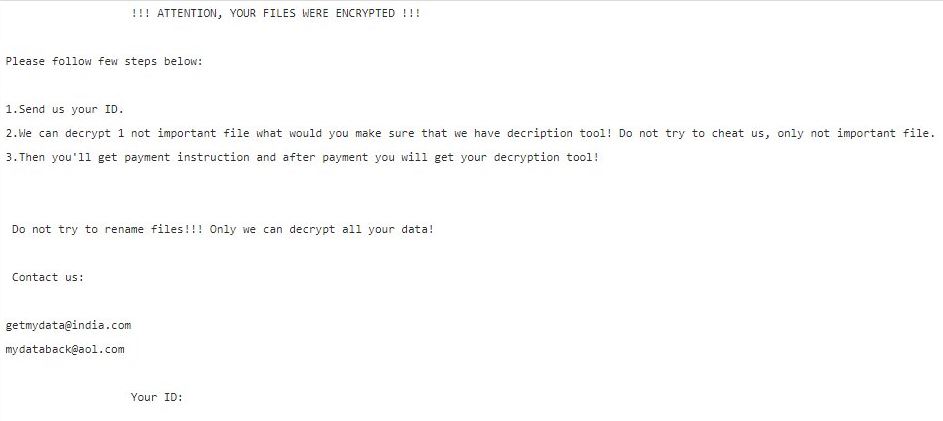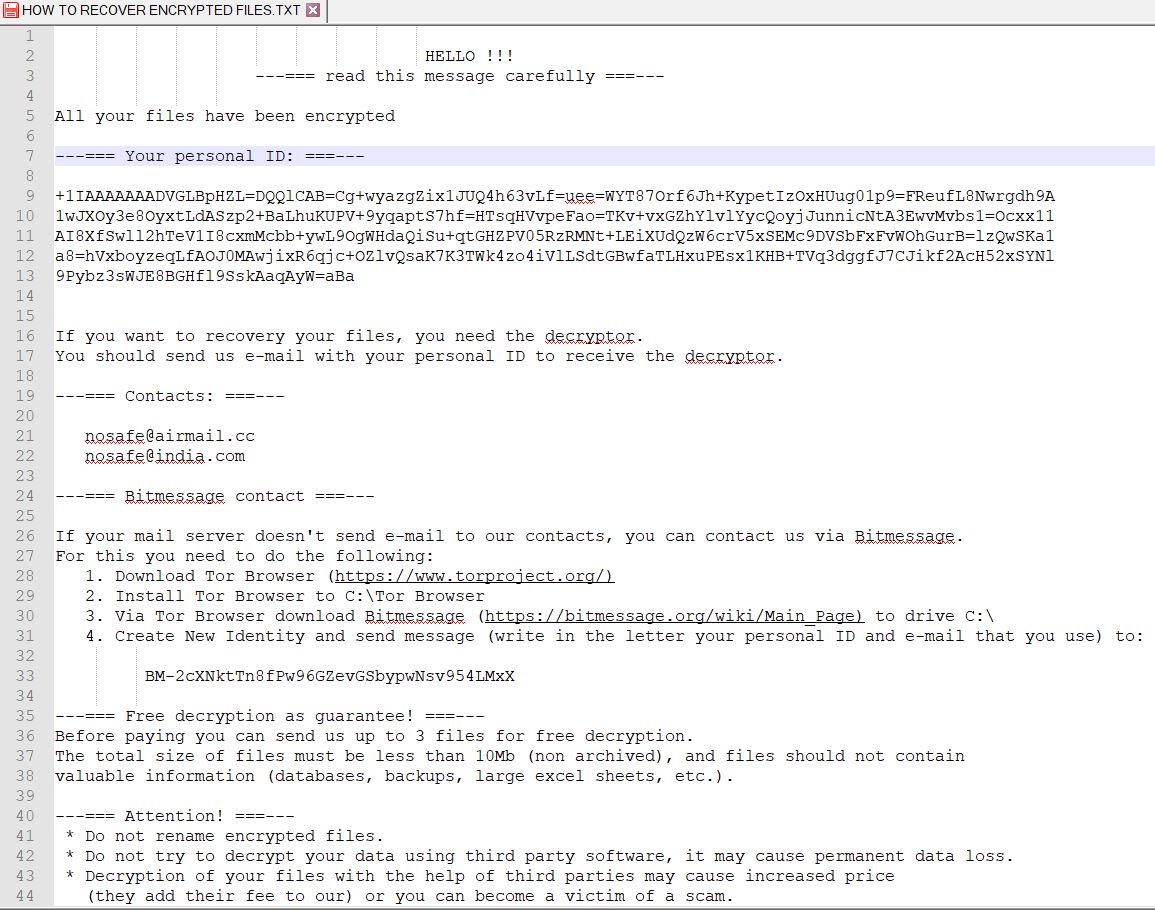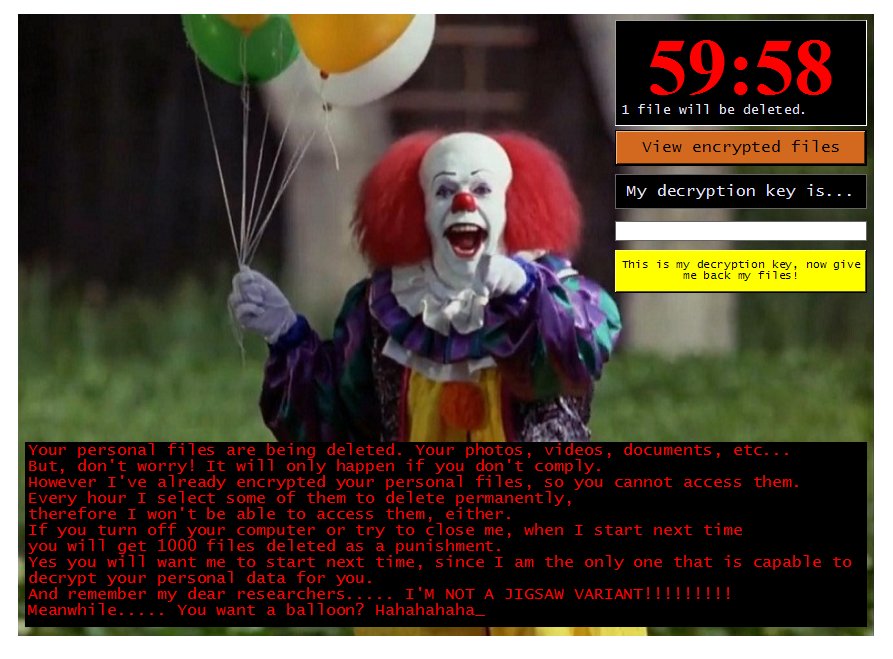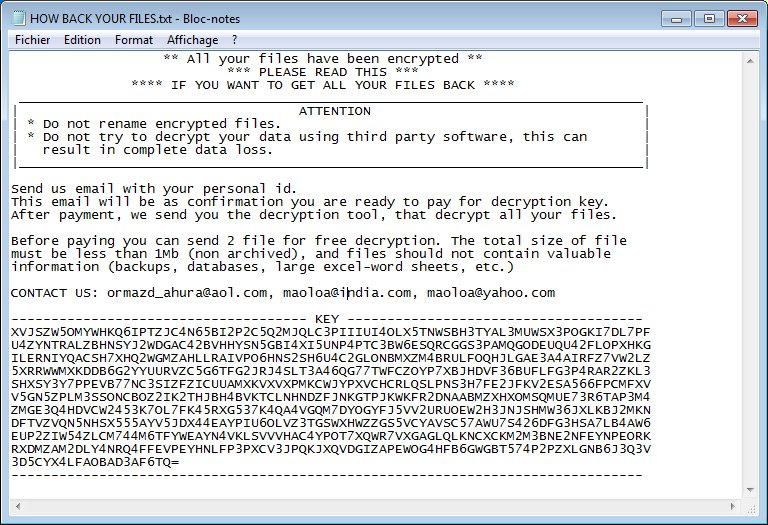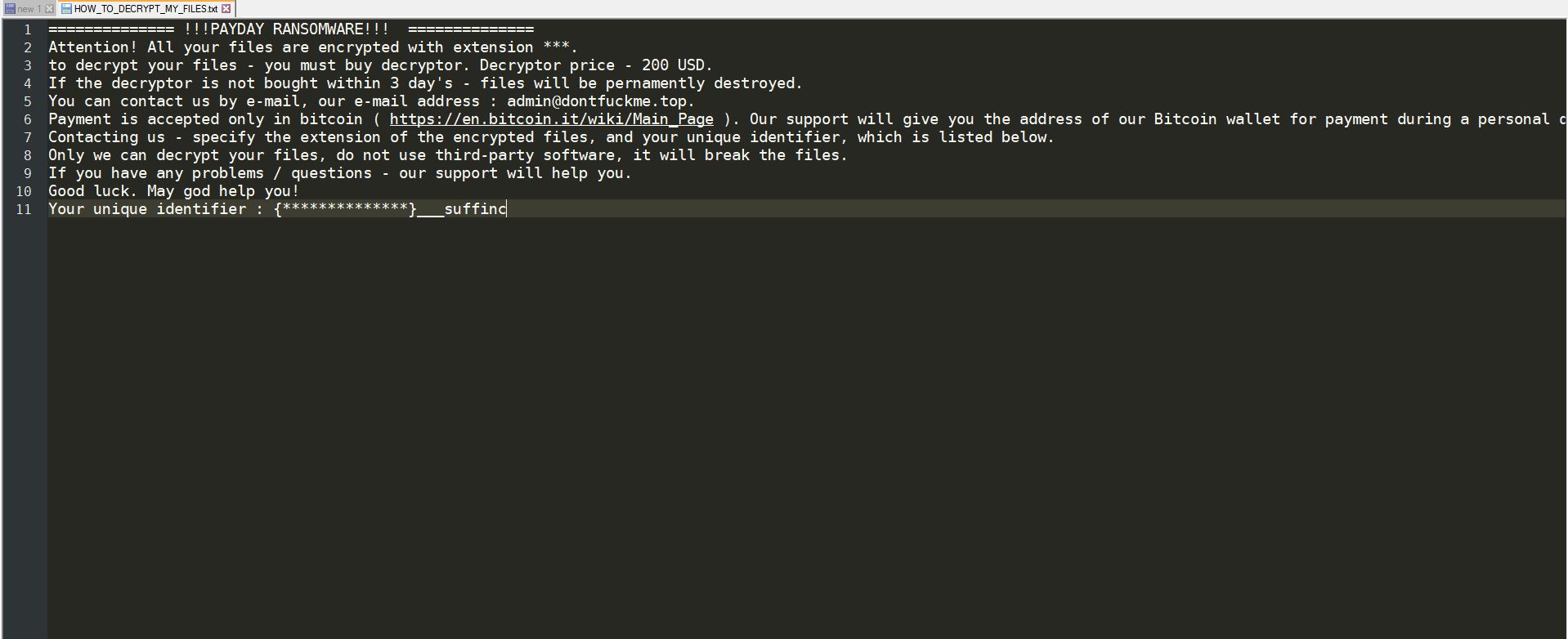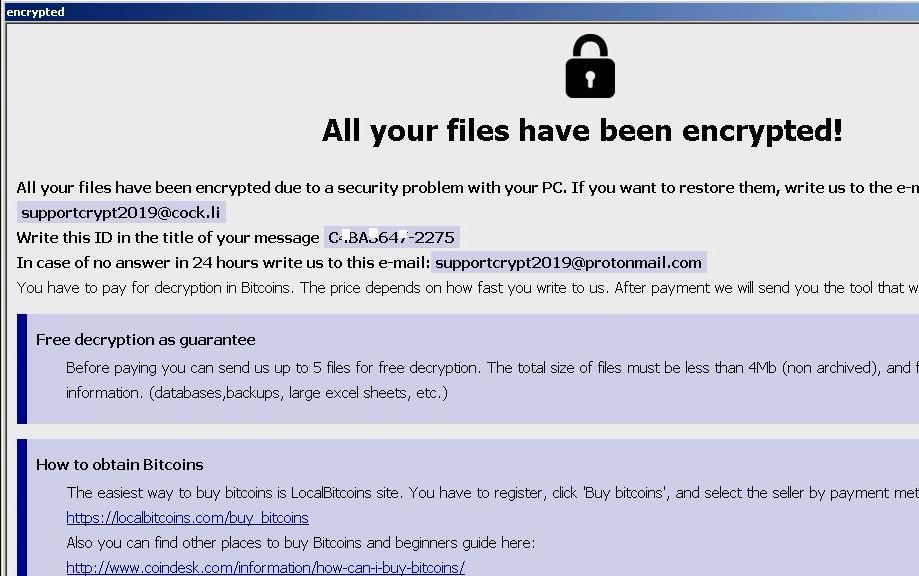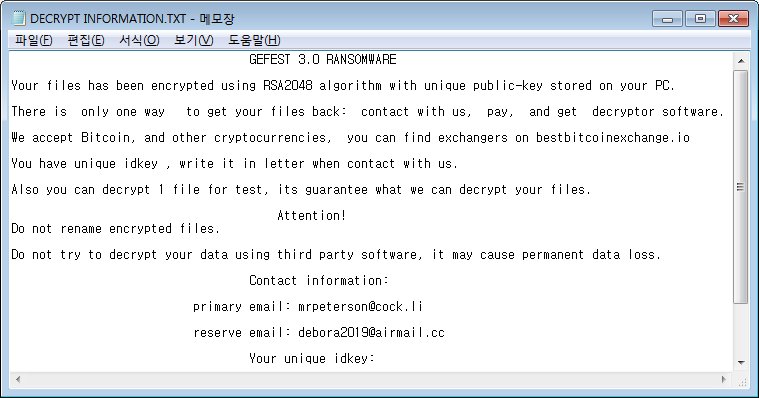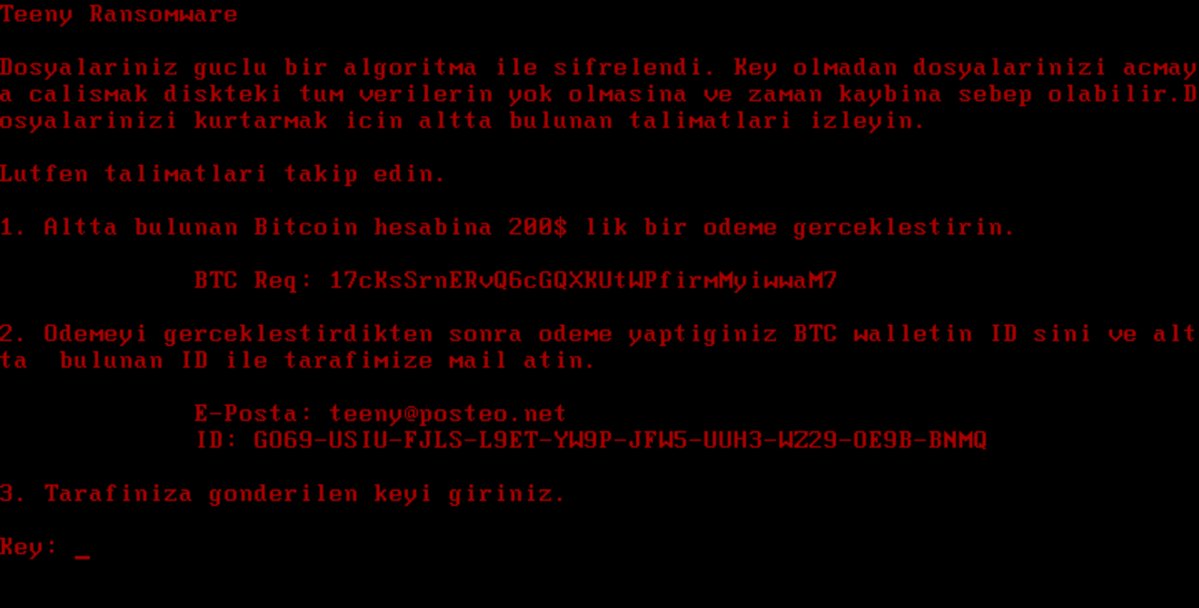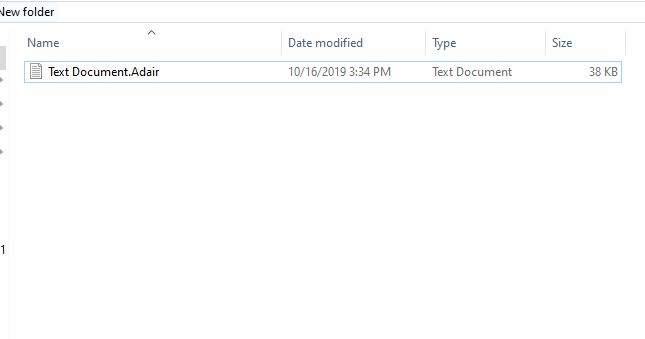
Dever Virus (.Dever Files) — How to Remove This Phobos Ransomware
The .Dever is a Phobos ransomware that is currently set against target end users on a global scale. There is no information available about the hacking group behind it. It is believed to be a new iteration of the famous…