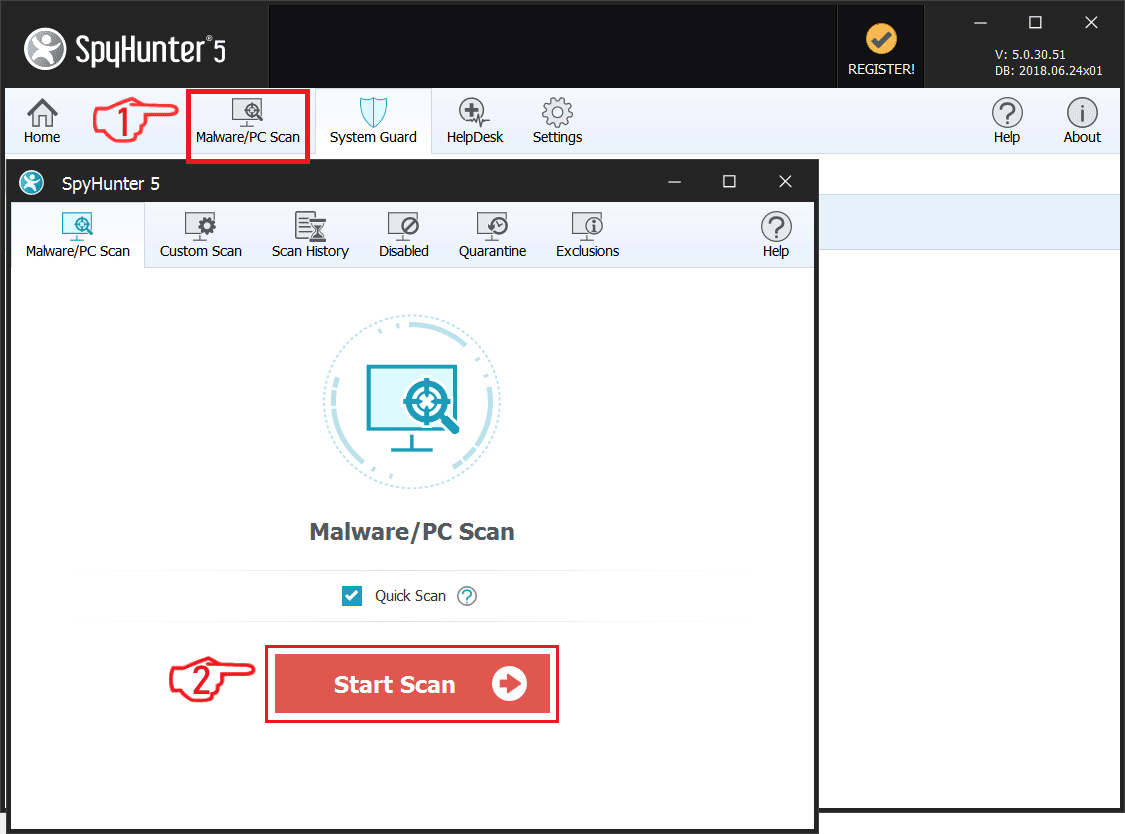
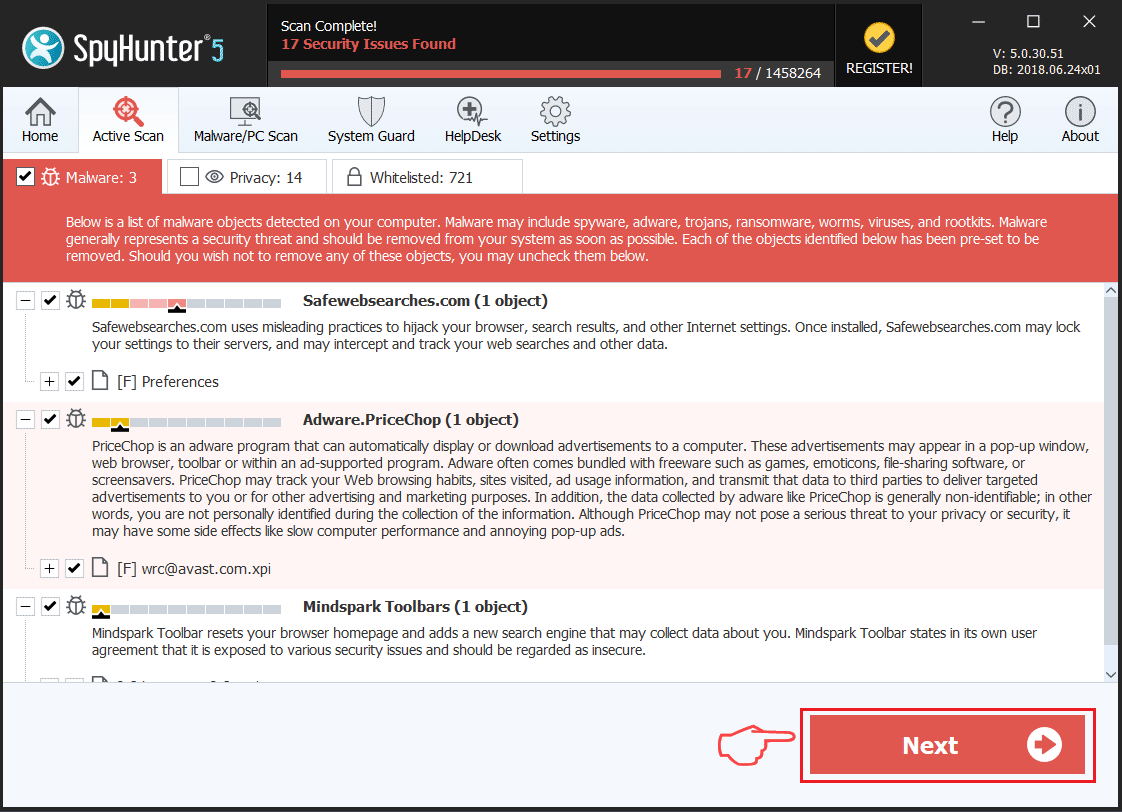
The Teamfostealer Trojan is a dangerous weapon used against computer users worldwide. It infects mainly via infected software installers. Our article gives an overview of its behavior according to the collected samples and available reports, also it may be helpful in attempting to remove the virus.

Threat Summary
| Name | Teamfostealer Trojan |
| Type | Trojan |
| Short Description | The Teamfostealer Trojan is a computer virus that is designed to silently infiltrate computer systems. |
| Symptoms | The victims may not experience any apparent symptoms of infection. |
| Distribution Method | Software Vulnerabilities, Freeware Installations, Bundled Packages, Scripts and others. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
| User Experience | Join Our Forum to Discuss Teamfostealer Trojan. |

Teamfostealer Trojan – Distribution Methods
The Teamfostealer Trojan is a very dangerous malware which was recently captured in an active campaign. The method of distribution is seen as very effective — the criminal collective behind the Teamfostealer Trojan is currently embedding the Trojan installation code in application installers of one of the most popular system utilities — Team Viewer. This is one of the most widely used solutions for remote logins.
This mechanism is primarily done by taking the real installers and modifying them to include the virus code. The hacking collective will download the legitimate setup file and modify it accordingly. The files are then delivered to the targets using a series of tactics — concentrating on a given approach or using several ones at once in order to maximize the number of possible infected computers.
At the moment the captured samples have been found posted on hacker-controlled sites. This means that some ind of a redirect scheme is being employed in order to lure them into downloading and running the malicious files. There are several popular approaches that can be undertaken:
- Email-based Phishing Campaigns — The hackers can plan an email-based phishing campaign which sends out messages that pose as legitimate notifications by welll-known companies or services. The criminals will spoof the original body design and text layout of the companies which can make it almost impossible to distinguish them from the real ones. The malicious Team Viewer files that contain the Teamfostealer Trojan installation code can be linked in the body contents or directly attached to the emails.
- Malicious Sites — A similar mechanism is the creation and maintenance Internet pages that look like the real landing pages of well-known search engines, download portals, company profiles pages and etc. They are hosted on similar sounding domain names that are very difficult to differentiate from the legitimate ones. Additionally they can include security certificates that can build the feeling that the accessed pages are safe.
- Bundle Downloads — The Teamfostealer Trojan can be embedded in application installers across the Internet. They are very similar to the infected application installers in a sense that they are made by modifying legitimate files with virus code.
- File-sharing networks — BitTorrent and other P2P platforms are very popular at sending both legitimate and pirate content. As such they are among the most dangerous conduits of malware files.
- Browser Hijackers — The infections can also be be caused through the use of dangerous plugins made for the most popular web browsers, alternatively known as hijackers. They are widely available from their associated repositories or download sites and promoted through elaborate descriptions and fake user reviews. When installed they will change the default settings in order to redirect the victims to a hacker-controlled web page. At the same time the virus infection will also be triggered.
Various other methods can be used in future campaigns. Take note that the delivered malicious Team Viewer packages are self-extracting archives (SFX/SEA) which is not the way the vendor has intended it to be. This is yet another warning sign that the package may be malicious in nature.

Teamfostealer Trojan – Detailed Description
The Teamfostealer Trojan will run the typical behavior patterns as observed by many other similar threats. Instead of the legitimate Team Viewer application the dangerous Trojan will be deployed to the systems. The first commands that are to be run will be to drop spyware data inside the User’s temporary folder as files that have typical Windows-related data which doesn’t raise any alarms of suspicion.
The malicious TeamViewer.exe will then load these files and launch a data collection module which will acquire the information and send it to the hacker operators via a network connection. The following information is confirmed to be extracted:
- Operating System
- OS Architecture
- Computer Name
- User Name
- RAM size
- Presence of AV Products
- Administrator Privilege
So far the Trojan has been found to focus mainly on data retrieval, possibly extending this feature to personal information as well. If this is done the engine will be programmed tool acquire strings that can directly expose the identity of the victim users. Such include their names, address, phone number, interests and any stored account credentials. If the Trojan interacts with the Windows Volume Manager it will be able to access removable storage devices and network shares as well. Successful exploitation of this behavior can help facilitate crimes such as identity theft and financial abuse.
Other malicious behavior that can be exhibited includes the execution of other modules in future versions. A common component is the persistent installation — it will set up the infection in such a way that the malicious code will be started every time the computer is powered on. This means that most of the manual user recovery instructions will not work as the virus will disable the access to the recovery menus and boot options.
An associated practice is the launch of a security bypass which will scan the infected machine for the presence of any anti-virus products and actively disable them. This is an effective solution against all services that can block the Trojan’s operations: firewalls, anti-virus products, virtual machine hosts and etc.
One of the most dangerous consequences of having such infections active on a host computer is when additional payloads are delivered. This is a very dangerous scenario as it has already disabled the security on the target computers and all dropped malware will have the ability to unfold all of their capabilities. The forthcoming campaign might contain a radically changed engine that will follow another set of behavior patterns.

Remove Teamfostealer Trojan Trojan
If your computer system got infected with the Teamfostealer Trojan Trojan, you should have a bit of experience in removing malware. You should get rid of this Trojan as quickly as possible before it can have the chance to spread further and infect other computers. You should remove the Trojan and follow the step-by-step instructions guide provided below.
Note! Your computer system may be affected by Teamfostealer Trojan and other threats.
Scan Your PC with SpyHunter
SpyHunter is a powerful malware removal tool designed to help users with in-depth system security analysis, detection and removal of Teamfostealer Trojan.
Keep in mind, that SpyHunter’s scanner is only for malware detection. If SpyHunter detects malware on your PC, you will need to purchase SpyHunter’s malware removal tool to remove the malware threats. Read our SpyHunter 5 review. Click on the corresponding links to check SpyHunter’s EULA, Privacy Policy and Threat Assessment Criteria.
To remove Teamfostealer Trojan follow these steps:
Use SpyHunter to scan for malware and unwanted programs
Preparation before removing Teamfostealer Trojan.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Make sure you have these instructions always open and in front of your eyes.
- Do a backup of all of your files, even if they could be damaged. You should back up your data with a cloud backup solution and insure your files against any type of loss, even from the most severe threats.
- Be patient as this could take a while.
- Scan for Malware
- Fix Registries
- Remove Virus Files
Step 1: Scan for Teamfostealer Trojan with SpyHunter Anti-Malware Tool



Step 2: Clean any registries, created by Teamfostealer Trojan on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Teamfostealer Trojan there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.Step 3: Find virus files created by Teamfostealer Trojan on your PC.
1.For Windows 8, 8.1 and 10.
For Newer Windows Operating Systems
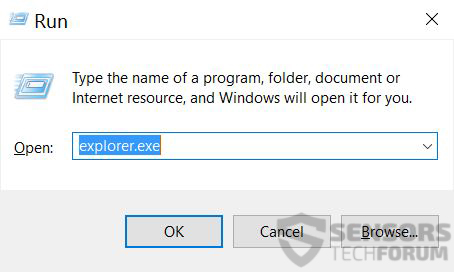
1: On your keyboard press + R and write explorer.exe in the Run text box and then click on the Ok button.

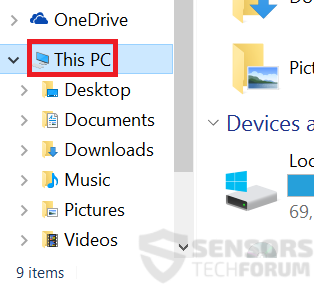
2: Click on your PC from the quick access bar. This is usually an icon with a monitor and its name is either “My Computer”, “My PC” or “This PC” or whatever you have named it.

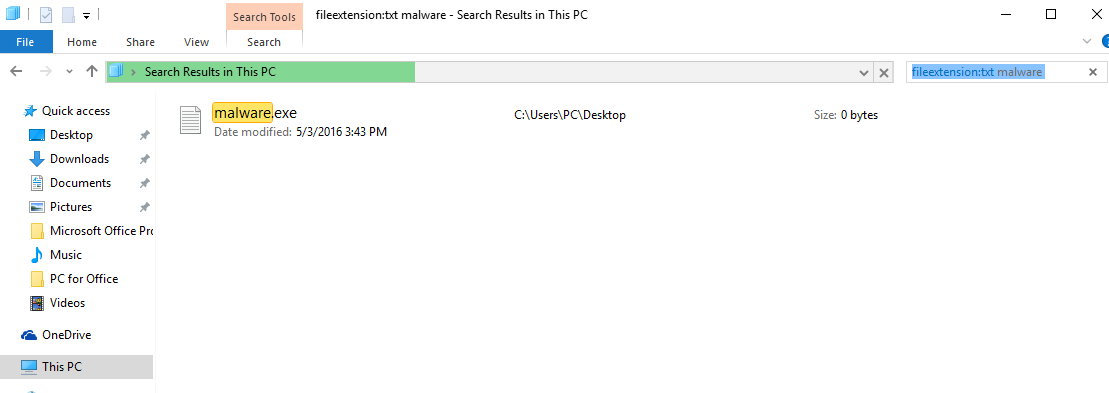
3: Navigate to the search box in the top-right of your PC's screen and type “fileextension:” and after which type the file extension. If you are looking for malicious executables, an example may be "fileextension:exe". After doing that, leave a space and type the file name you believe the malware has created. Here is how it may appear if your file has been found:

N.B. We recommend to wait for the green loading bar in the navigation box to fill up in case the PC is looking for the file and hasn't found it yet.
2.For Windows XP, Vista, and 7.
For Older Windows Operating Systems
In older Windows OS's the conventional approach should be the effective one:
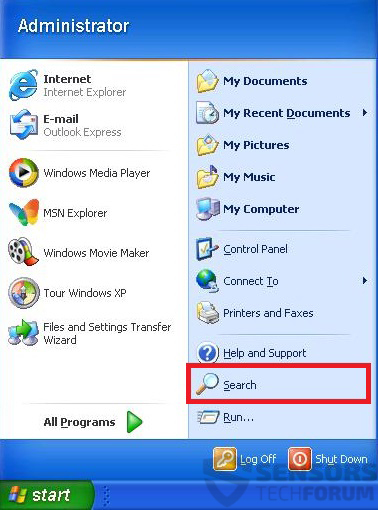
1: Click on the Start Menu icon (usually on your bottom-left) and then choose the Search preference.

2: After the search window appears, choose More Advanced Options from the search assistant box. Another way is by clicking on All Files and Folders.

3: After that type the name of the file you are looking for and click on the Search button. This might take some time after which results will appear. If you have found the malicious file, you may copy or open its location by right-clicking on it.
Now you should be able to discover any file on Windows as long as it is on your hard drive and is not concealed via special software.
Teamfostealer Trojan FAQ
What Does Teamfostealer Trojan Trojan Do?
The Teamfostealer Trojan Trojan is a malicious computer program designed to disrupt, damage, or gain unauthorized access to a computer system. It can be used to steal sensitive data, gain control over a system, or launch other malicious activities.
Can Trojans Steal Passwords?
Yes, Trojans, like Teamfostealer Trojan, can steal passwords. These malicious programs are designed to gain access to a user's computer, spy on victims and steal sensitive information such as banking details and passwords.
Can Teamfostealer Trojan Trojan Hide Itself?
Yes, it can. A Trojan can use various techniques to mask itself, including rootkits, encryption, and obfuscation, to hide from security scanners and evade detection.
Can a Trojan be Removed by Factory Reset?
Yes, a Trojan can be removed by factory resetting your device. This is because it will restore the device to its original state, eliminating any malicious software that may have been installed. Bear in mind that there are more sophisticated Trojans that leave backdoors and reinfect even after a factory reset.
Can Teamfostealer Trojan Trojan Infect WiFi?
Yes, it is possible for a Trojan to infect WiFi networks. When a user connects to the infected network, the Trojan can spread to other connected devices and can access sensitive information on the network.
Can Trojans Be Deleted?
Yes, Trojans can be deleted. This is typically done by running a powerful anti-virus or anti-malware program that is designed to detect and remove malicious files. In some cases, manual deletion of the Trojan may also be necessary.
Can Trojans Steal Files?
Yes, Trojans can steal files if they are installed on a computer. This is done by allowing the malware author or user to gain access to the computer and then steal the files stored on it.
Which Anti-Malware Can Remove Trojans?
Anti-malware programs such as SpyHunter are capable of scanning for and removing Trojans from your computer. It is important to keep your anti-malware up to date and regularly scan your system for any malicious software.
Can Trojans Infect USB?
Yes, Trojans can infect USB devices. USB Trojans typically spread through malicious files downloaded from the internet or shared via email, allowing the hacker to gain access to a user's confidential data.
About the Teamfostealer Trojan Research
The content we publish on SensorsTechForum.com, this Teamfostealer Trojan how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific trojan problem.
How did we conduct the research on Teamfostealer Trojan?
Please note that our research is based on an independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware definitions, including the various types of trojans (backdoor, downloader, infostealer, ransom, etc.)
Furthermore, the research behind the Teamfostealer Trojan threat is backed with VirusTotal.
To better understand the threat posed by trojans, please refer to the following articles which provide knowledgeable details.


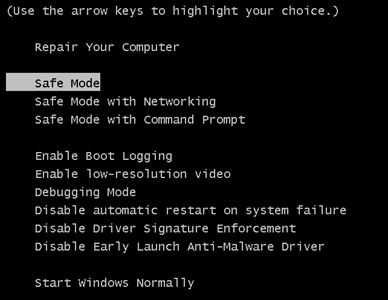
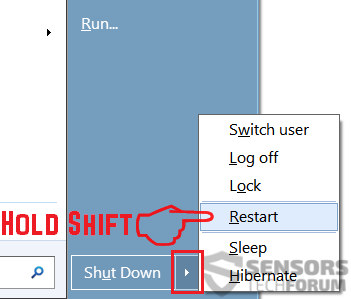
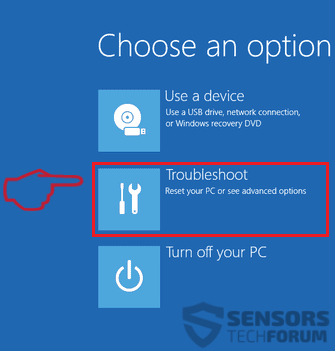
 1. For Windows XP, Vista and 7.
1. For Windows XP, Vista and 7. 2. For Windows 8, 8.1 and 10.
2. For Windows 8, 8.1 and 10. Fix registry entries created by malware and PUPs on your PC.
Fix registry entries created by malware and PUPs on your PC.
 1. Install SpyHunter to scan for Teamfostealer Trojan and remove them.
1. Install SpyHunter to scan for Teamfostealer Trojan and remove them.