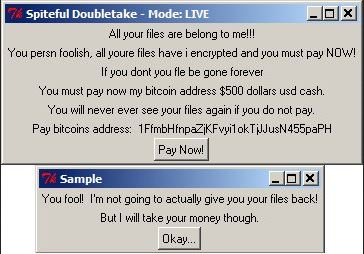
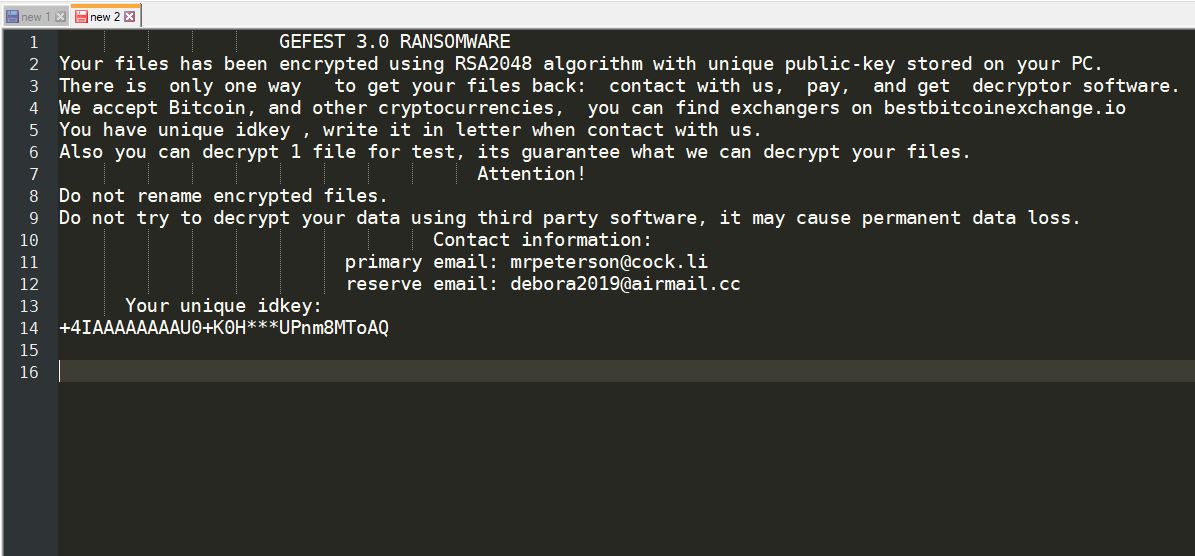
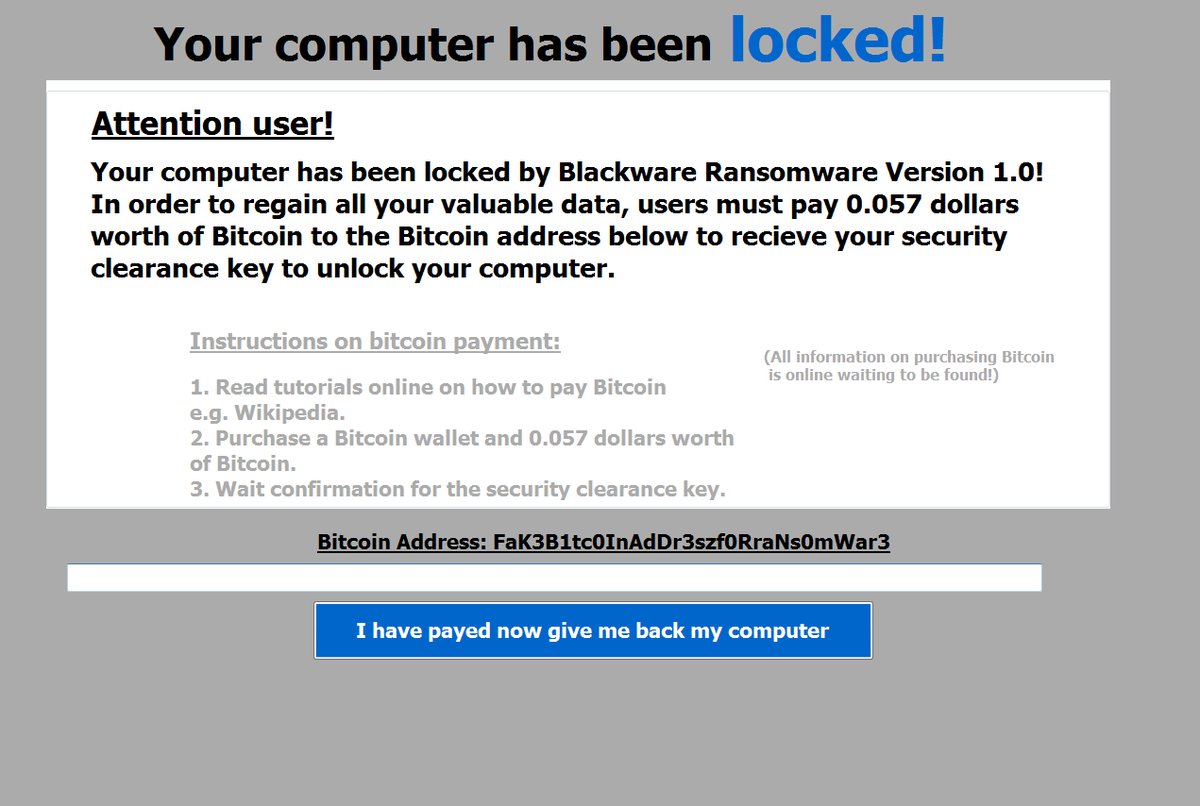
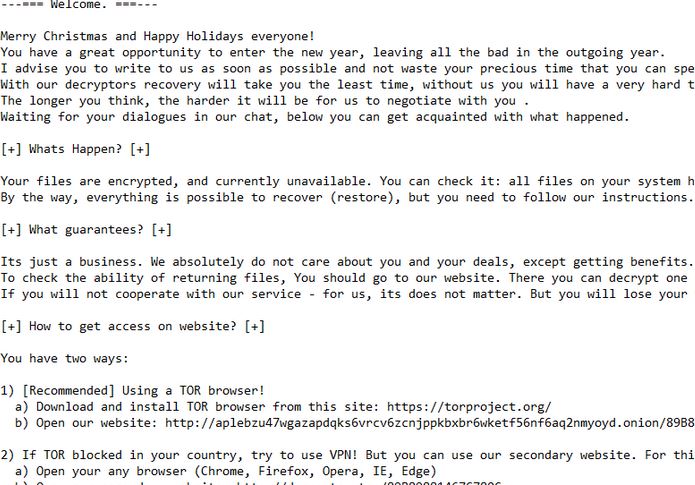
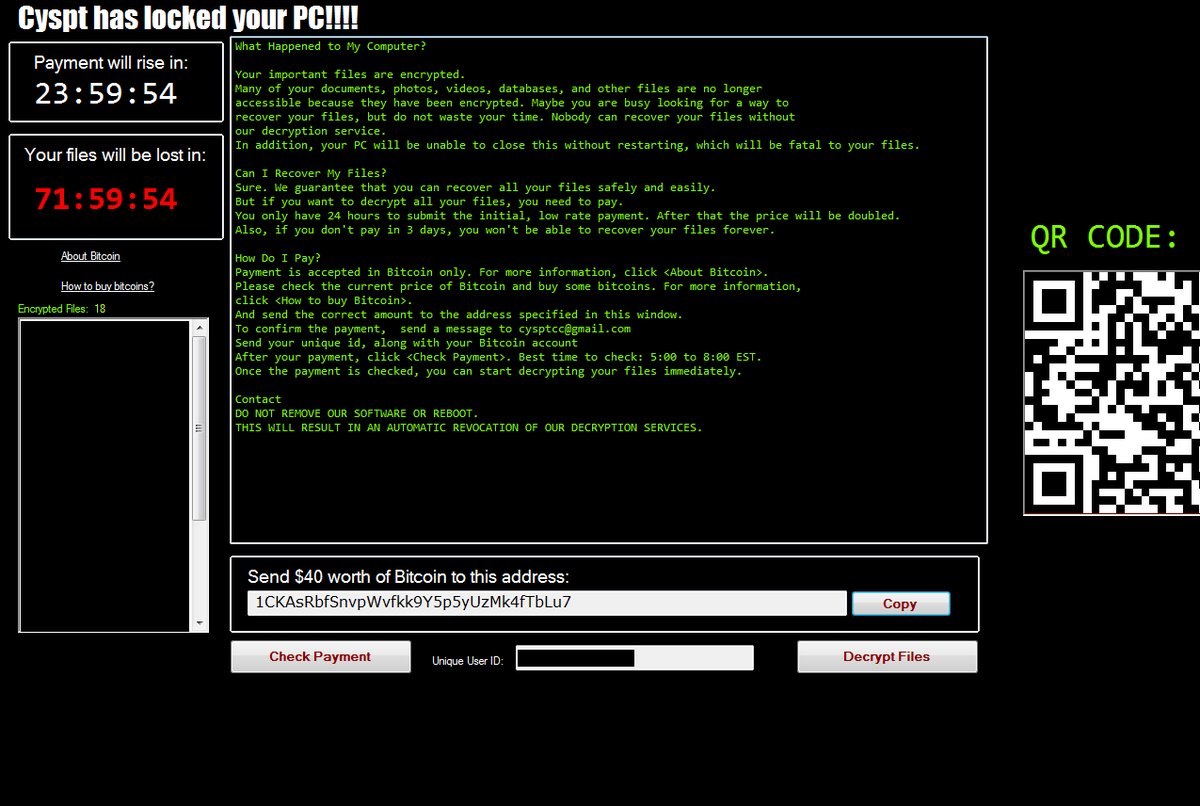
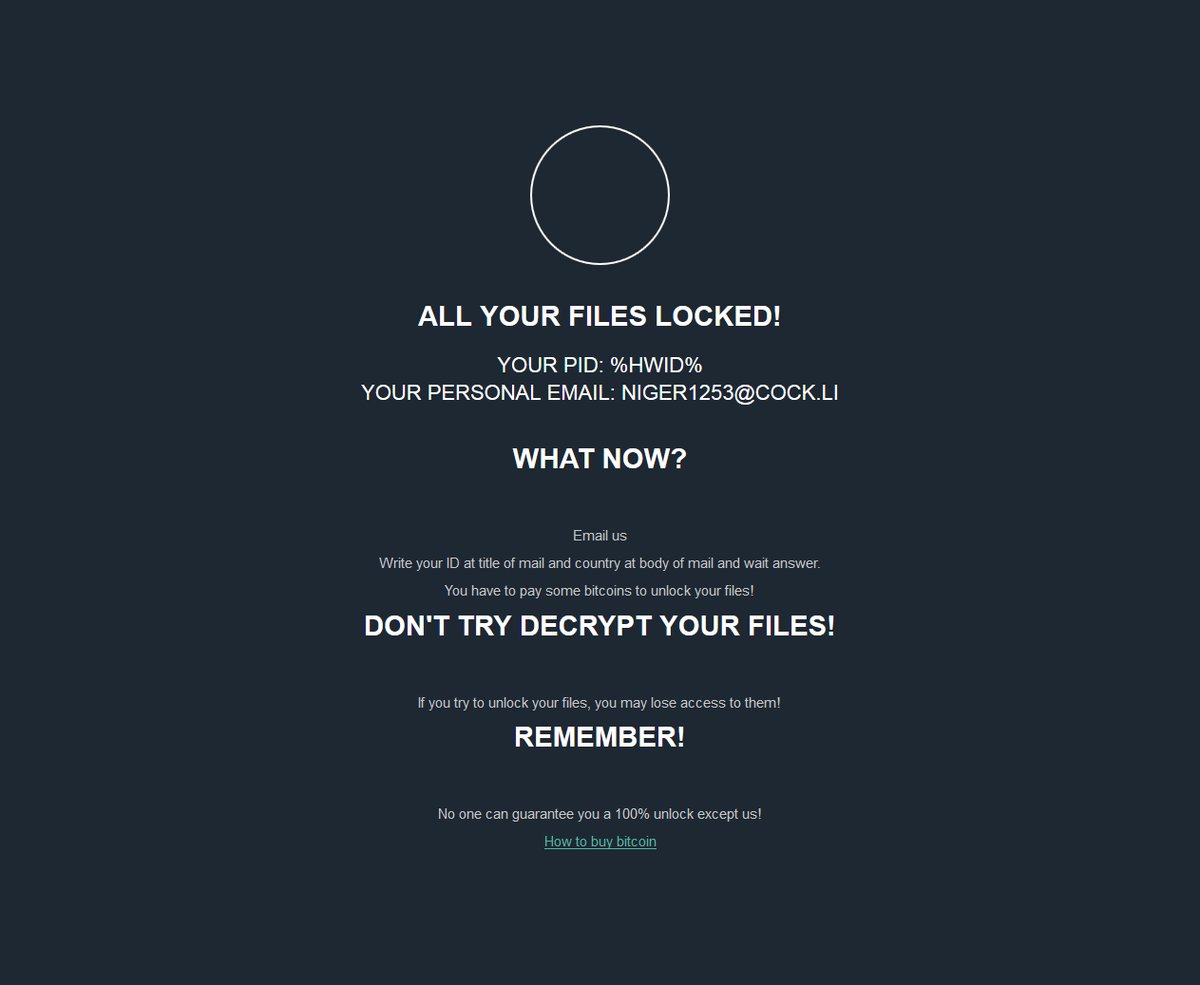
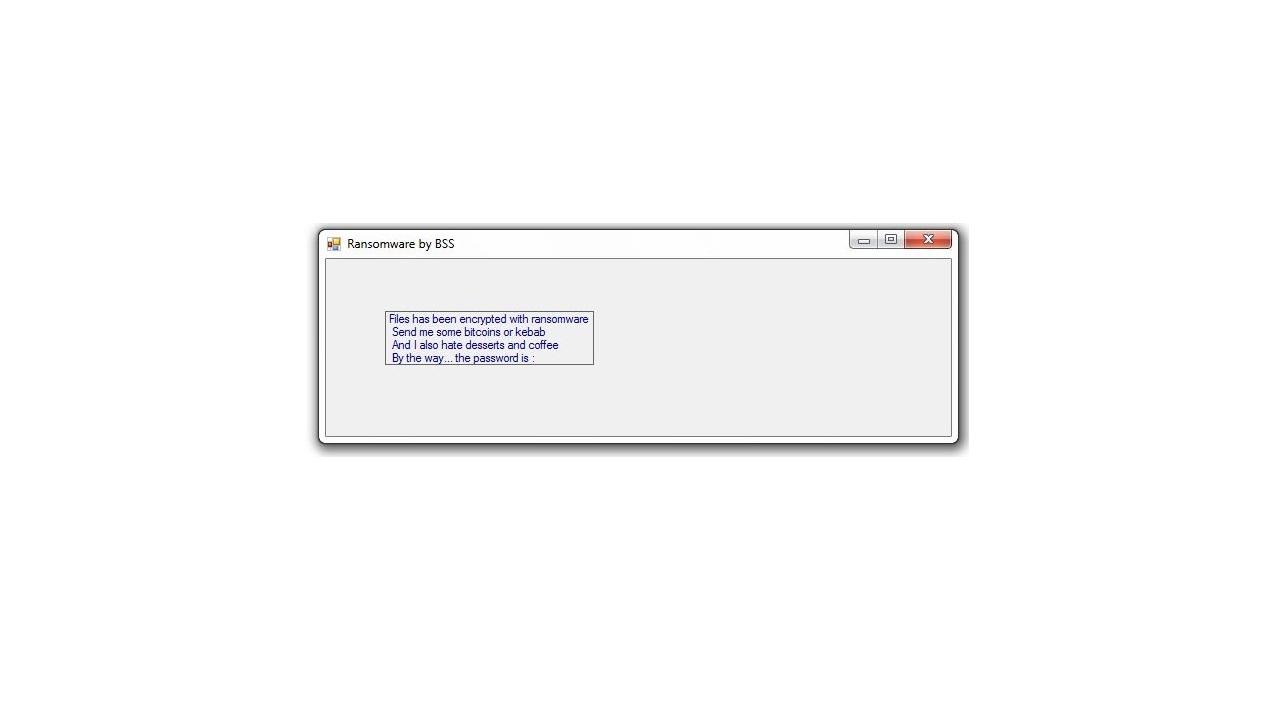
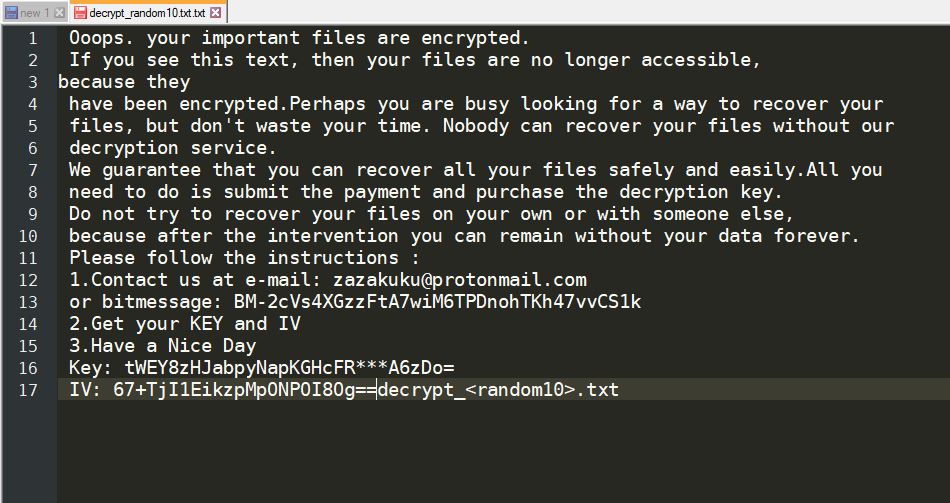
Hackers Can Exploit Systemd-Journald Via CVE-2018-18865, CVE-2018-16866
The systemd-journald service has been found to be affected by two dangerous vulnerabilities that are tracked in the CVE-2018-16865 and CVE-2018-16866 advisories. By exploiting them, computer criminals can manipulate the memory and take over control of the machines. Nowadays sytemd-journald…