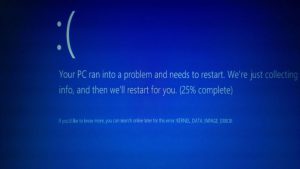
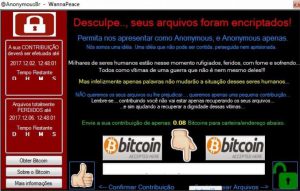
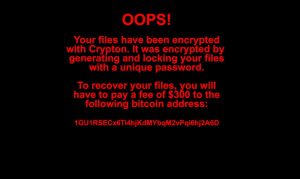
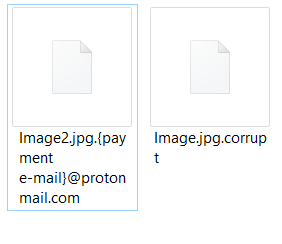
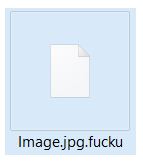
30Tab.com Redirect Search “Virus” – How to Remove It
This article has been created in order to show you how to remove the 30tab.com “virus” from your browsers and computer completely. A new unwanted program has been reported by malware researchers to display various different advertisements on the computers…