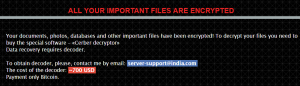
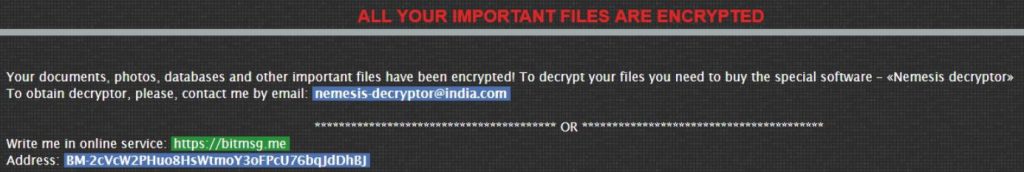
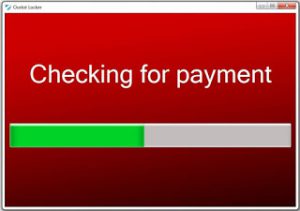
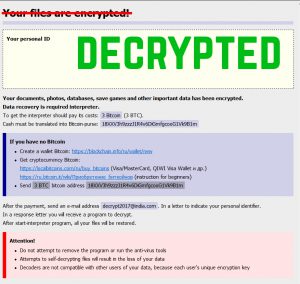
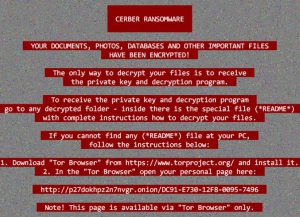
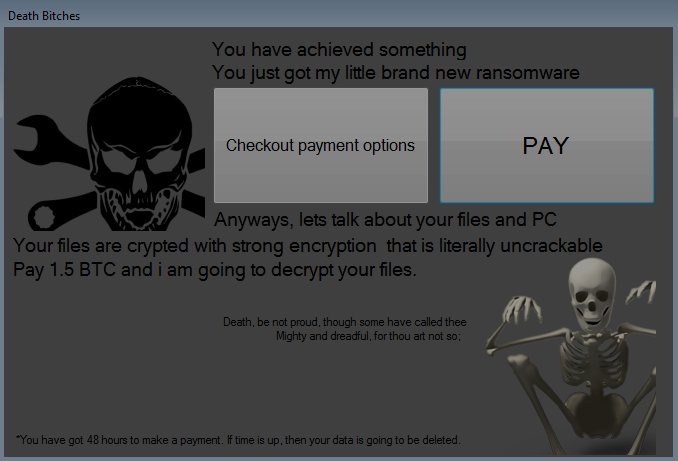
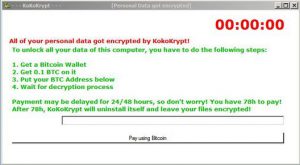
Decrypt .Oops Files Encrypted by Marlboro Ransomware
This article aims to display how to remove Marlboro ransomware and decrypt .oops files encrypted by it. Ever since the .oops virus, dubbed Marlboro came out, it has been causing nothing but trouble. This ransomware type of malware aims to…