Intele.exe Miner Virus – How to Detect and Remove It
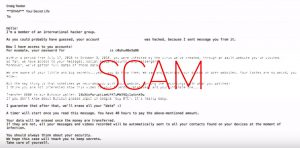
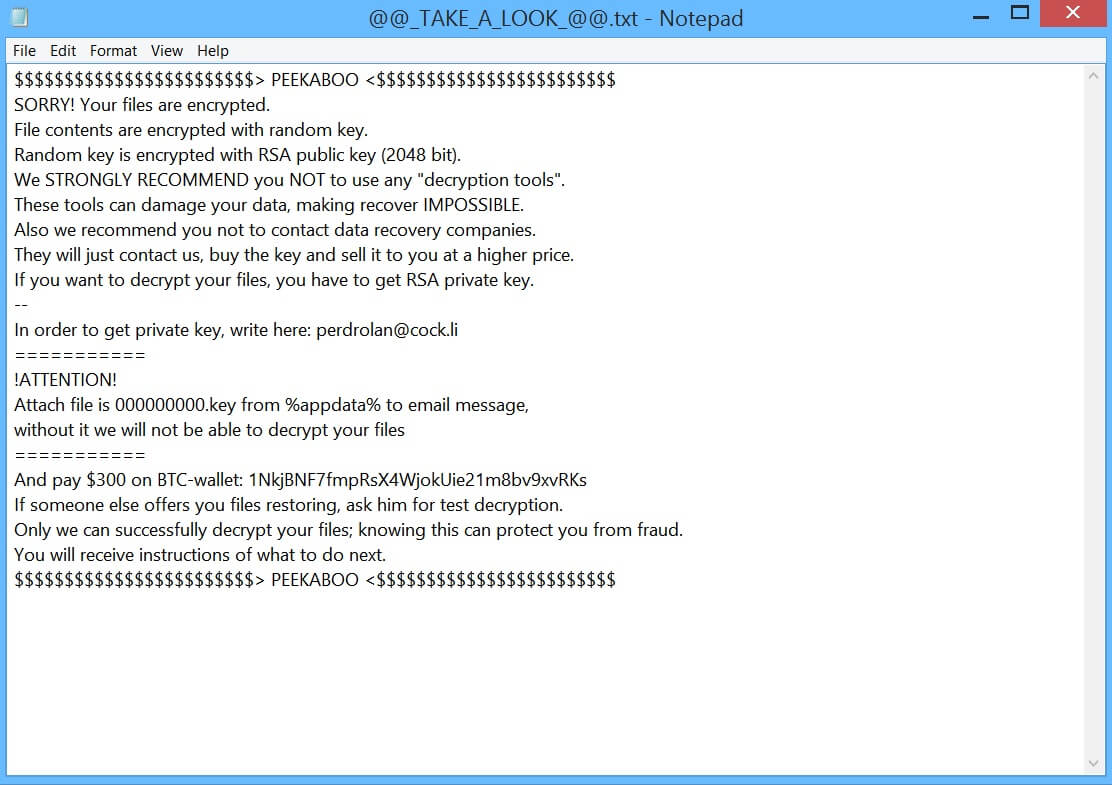
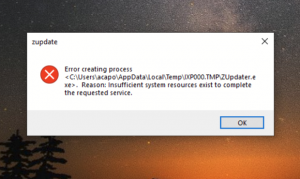
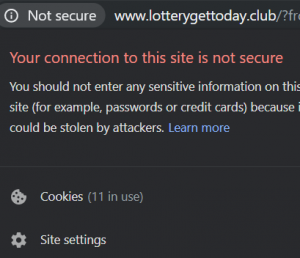
Is Intele.exe a miner? Does Intele.exe harm your computer? Can Intele.exe a cryptocurrency miner? The Intele.exe is a dangerous miner and potentially a Trojan sample which is believed to be spread by an experienced criminal group. It can be acquired…