Cerberus virus for Android is a banking trojan that has the immense capability of bypassing 2 factor authentication and unlocking your phone or tablet automatically. Read this article to learn how to remove it.
Cerberus Virus Android
Ceberus is the type of virus, whose main goal is to enter your Android device and act as a RAT (Remote Access Trojan). Repots indicate that it can bypass Google Authenticator and uses advanced mechanisms to enter your device. Once it enters your phone, it can steal all sorts of information from it, but the main goal of Cerberus Virus is to make sure that it steals banking information and payment information plus passwords of your Android device. What is new with this Cerberus RAT is that whoever infects you can also manage the apps on your infected Android device. Not only this, but also you can have the Cerberus virus to lock your Android device, and also remotely unlock it. Furthermore, the crooks are so creative that they can also tap into cameras, microphones, track what you do for months and you may not even notice them.

Threat Summary
| Name | Cerberus virus |
| Type | Android banking malware. |
| Short Description | Very dangerous banking Trojan that can remote control your Android device completely. |
| Symptoms | The Trojan has the capability to lock your phone, switch it off, cut away your internet connection and display fake login screens to make you giveaway your passwords. |
| Distribution Method | Via virus URLs or malicious fake apps. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss Cerberus virus. |
Cerberus Virus Android Description
An Android monetary malware called Cerberus Virus has in fact been located to acquire all types of monetary qualifications along with take login details and root gadgets. The designers of this malware have really developed it to function mainly as banking malware offering great deals of profitable possibilities for the cyber-criminals that are mosting likely to be using it. Clients are extremely suggested to read this post and additionally discover just how to safeguard themselves from this Android OS financial malware.
The criminals that rearrange this trojan have extremely skillfully though out the process of recreating this malware infection. Among the techniques the crooks utilize is to download and install a primary application, such as Pokemon Go, Vkontakte or Telegram as well as strip it’s code down to include a damaging manuscript in it. After that, they re-upload the transformed malicious application along with upload it on dishonest third-party sites.
Given that such web websites do not have their approach of self-replicating, the lawbreakers might additionally connect these sites along with advertise the harmful links that may produce the download of such applications. This can happen in several methods, among which is Facebook spam that promotes the application, much like My Secret Video Facebook malware does.
After the applications are mounted on the device, the malware after that may connect to numerous third-party internet links and download the complete haul of the Cerberus virus trojan.
The malware is specifically fantastic in it’s tasks. One activity it performs is that it collaborates with the counterfeit application which works as a downloader. After the application downloads the devastating documents, which are protected for obfuscation, it decrypts them on the device as well as also implements them.
Hereafter has really been done, the malicious application might additionally download as well as mount updates to the application including new functions to it’s currently existing ones. And also the presently existing functions are numerous that they offer the ones that have in fact infected you a push-button control like authorizations:
- Complete SMS control.
- Complete control of the phone calls.
- Data checks of the phone.
- Obtaining the phone’s calls.
- Stealing information and sending it to crooks’ server.
- Making checklists that gather password and username data.
- Taking screenshots.
- Stealing financial information.
- Stealing audio data.
- Making a lock screen on the phone as well as disclosing a web page.
- Switching on and likewise shutting off your phone.
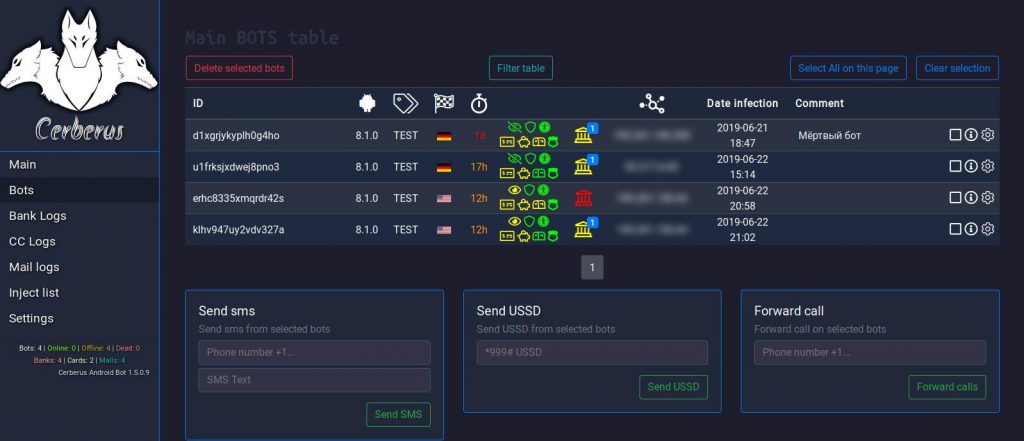
The main panel that the criminals use from which they control your Android device has been reported by malware analysts at Cert.pl to appear like the following:
Besides those various functions, this malware also has the capability of rooting the phone, indicating that the cyber-criminals might have access to even more characteristics also, equally as an origin client. This, besides offering complete control to the phone’s applications, software, along with devices, it also allows them to swipe all the details they wish to and additionally input it in their promptly created login databases.

How to Remove Cerberus Virus from Android
The Cerberus virus financial trojan is an exceptionally dangerous threat, as well as the criminals who established it are especially creative. One factor is that they have really taken care of to successfully focus on Android devices given that mobile repayment use is winding up being a lot more constant than ever. All customers that use mobile settlement strategies and also have actually established applications from questionable areas should certainly safeguard their phone by difficult resetting it, which can be rapidly done if you comply with the guidelines hereafter message.
Preparation before removal of malware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Turn off your phone until you know how bad is the virus infection.
- Open these steps on another, safe device.
- Make sure to take out your SIM card, as the virus could corrupt it in some rare cases.
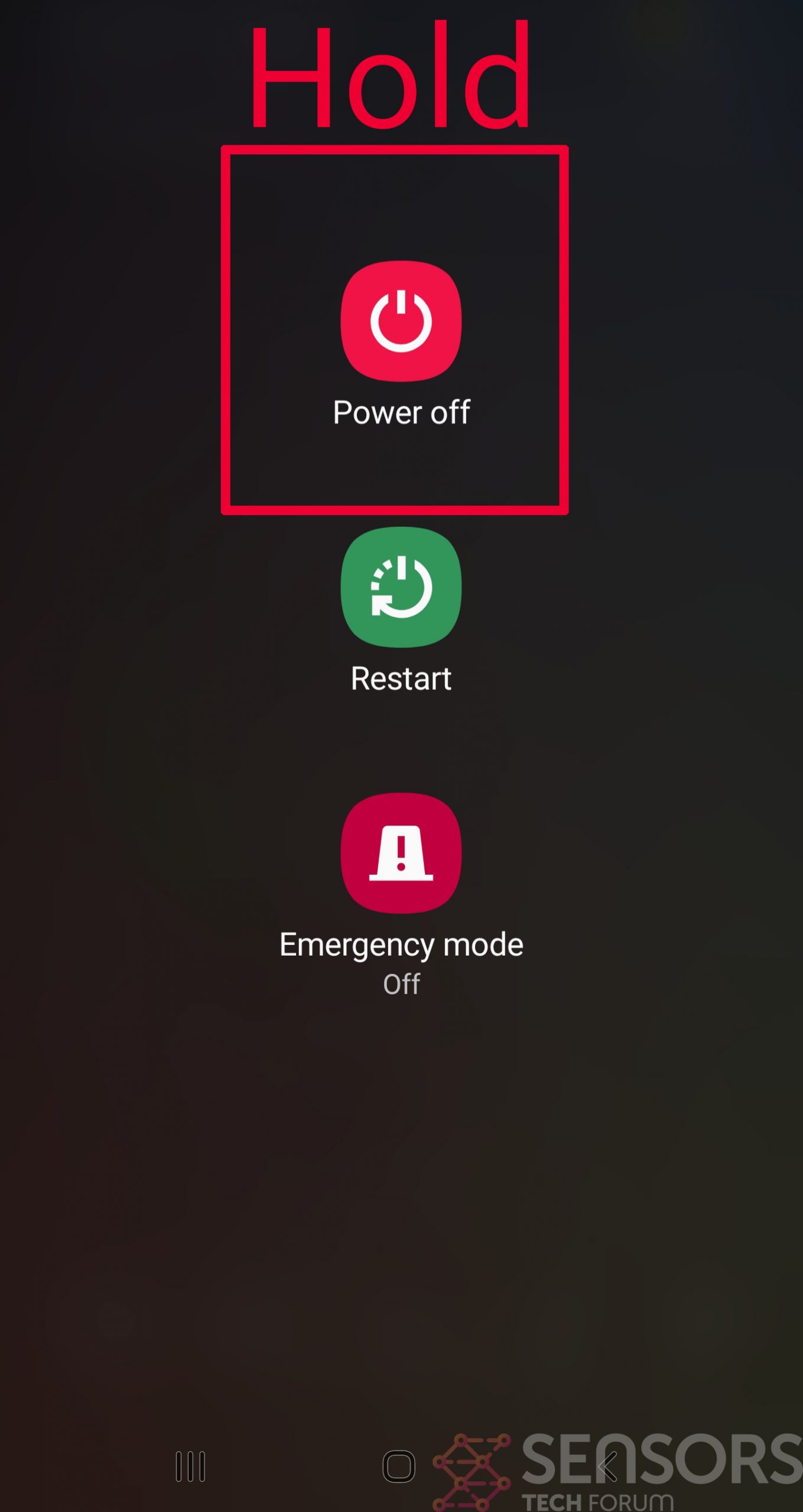
Step 1: Shut Down your phone to win some time
Shutting down your phone can be done by pressing and holding its power button and choosing shut down.
In case the virus does not let you do this, you can also try to remove the battery.
In case your battery is non-removable, you can try to drain it as fast as possible if you still have control over it.
Notes: This gives you time to see how bad the situation is and to be able to take out your SIM card safely, without the numbers in it to be erased. If the virus is on your computer, it is espeically dangerous to keep the sim card there.
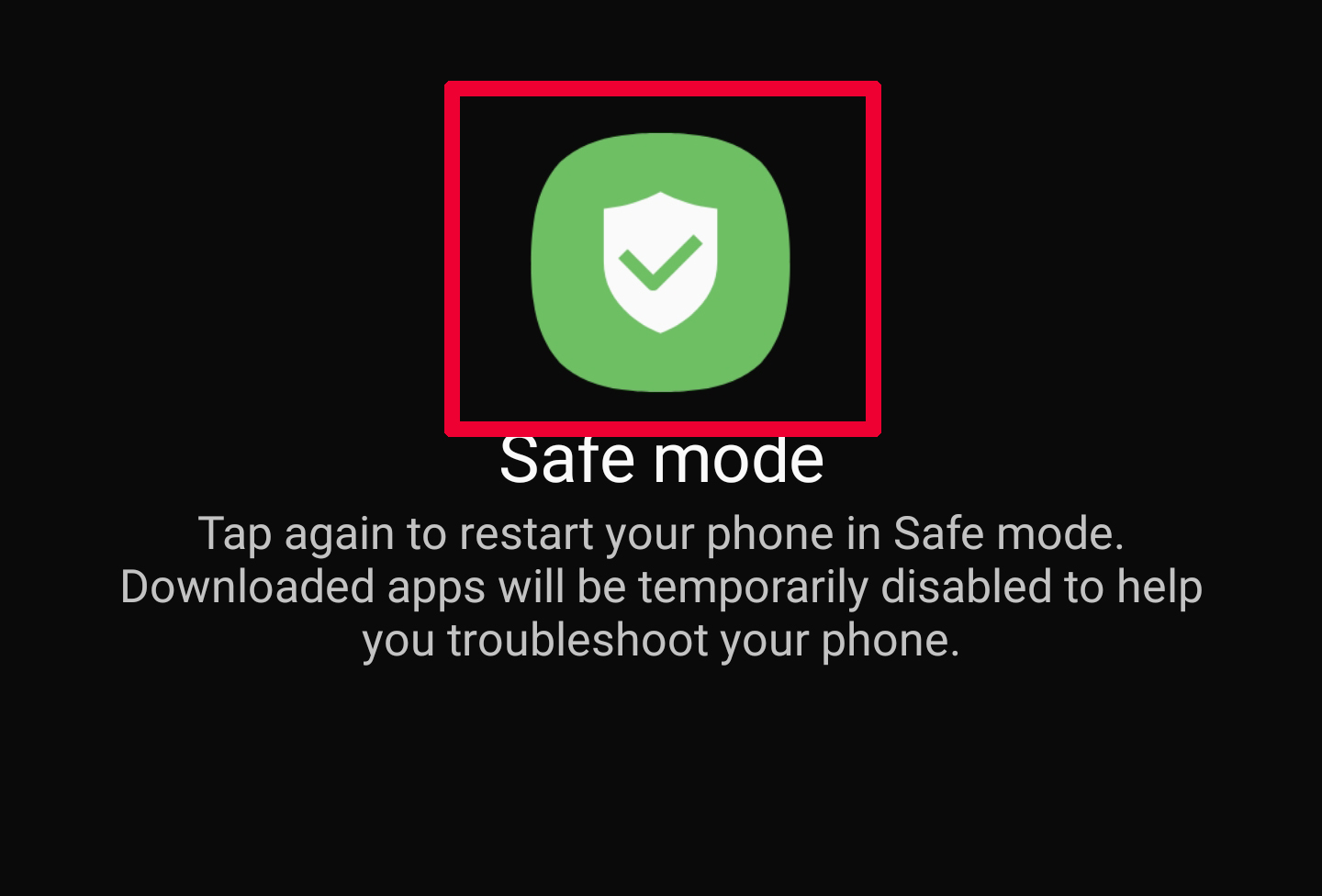
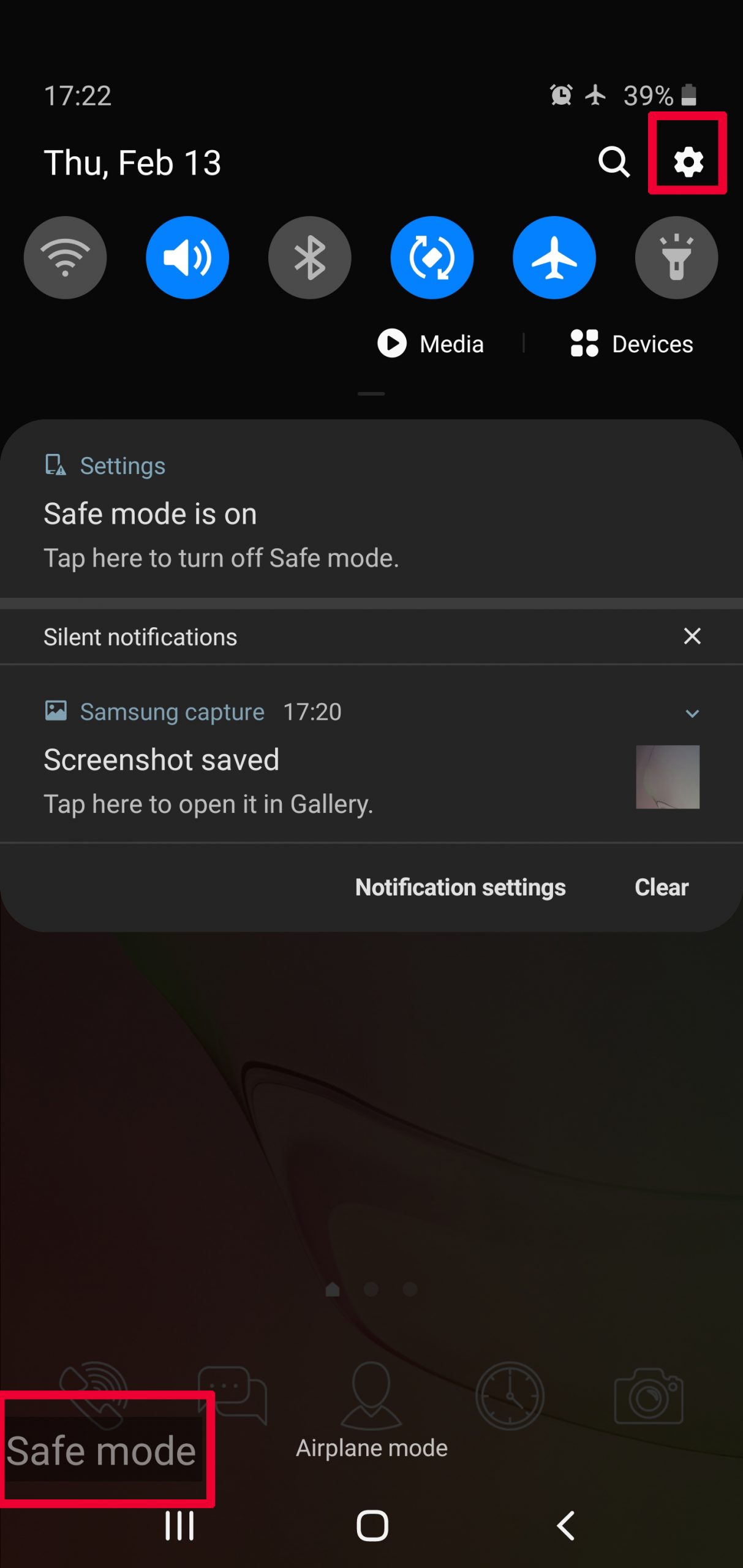
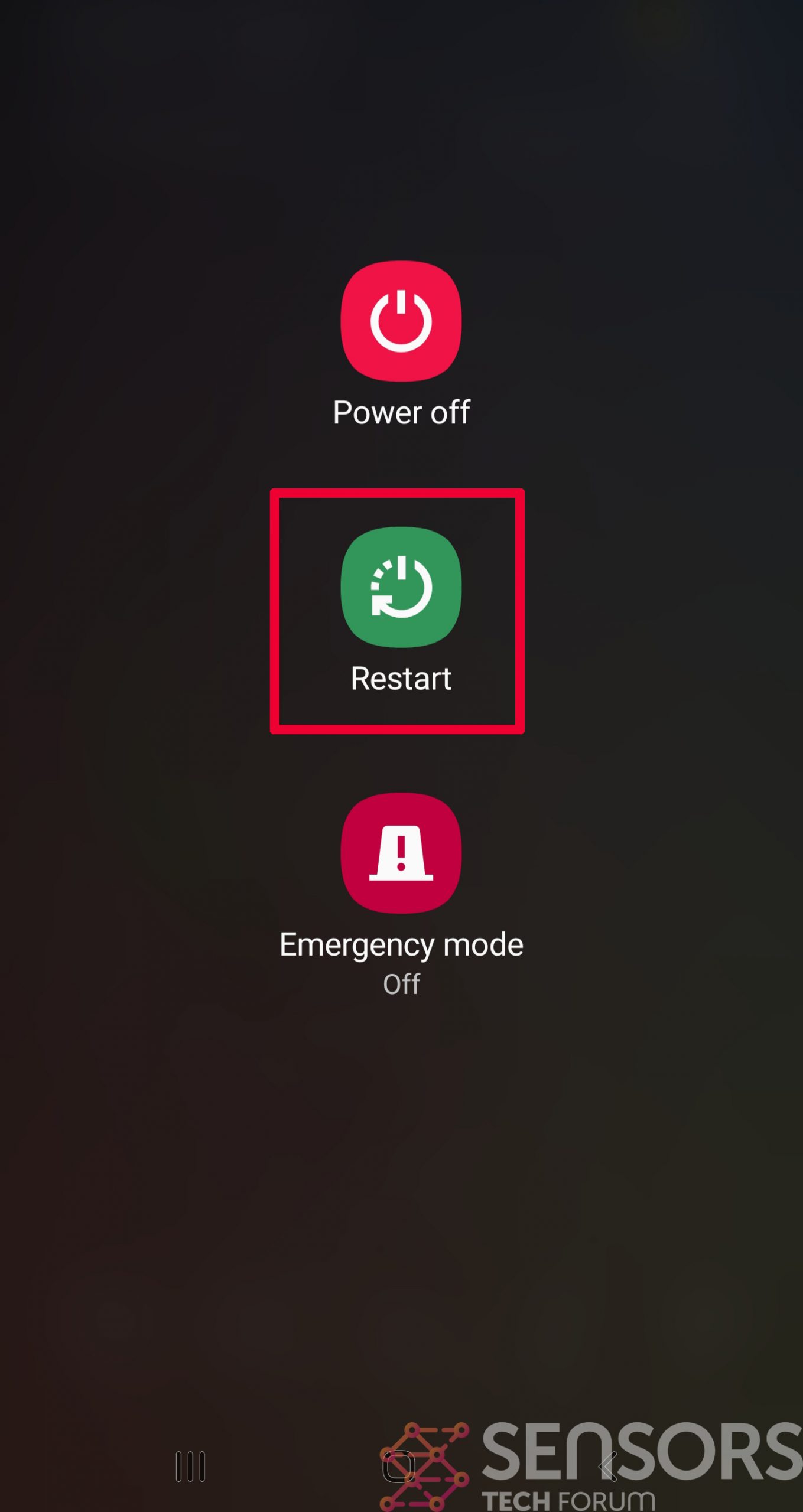
Step 2: Turn on Safe Mode of your Android device.
For most Android devices, switching to Safe Mode is the same. Its done by following these mini-steps:

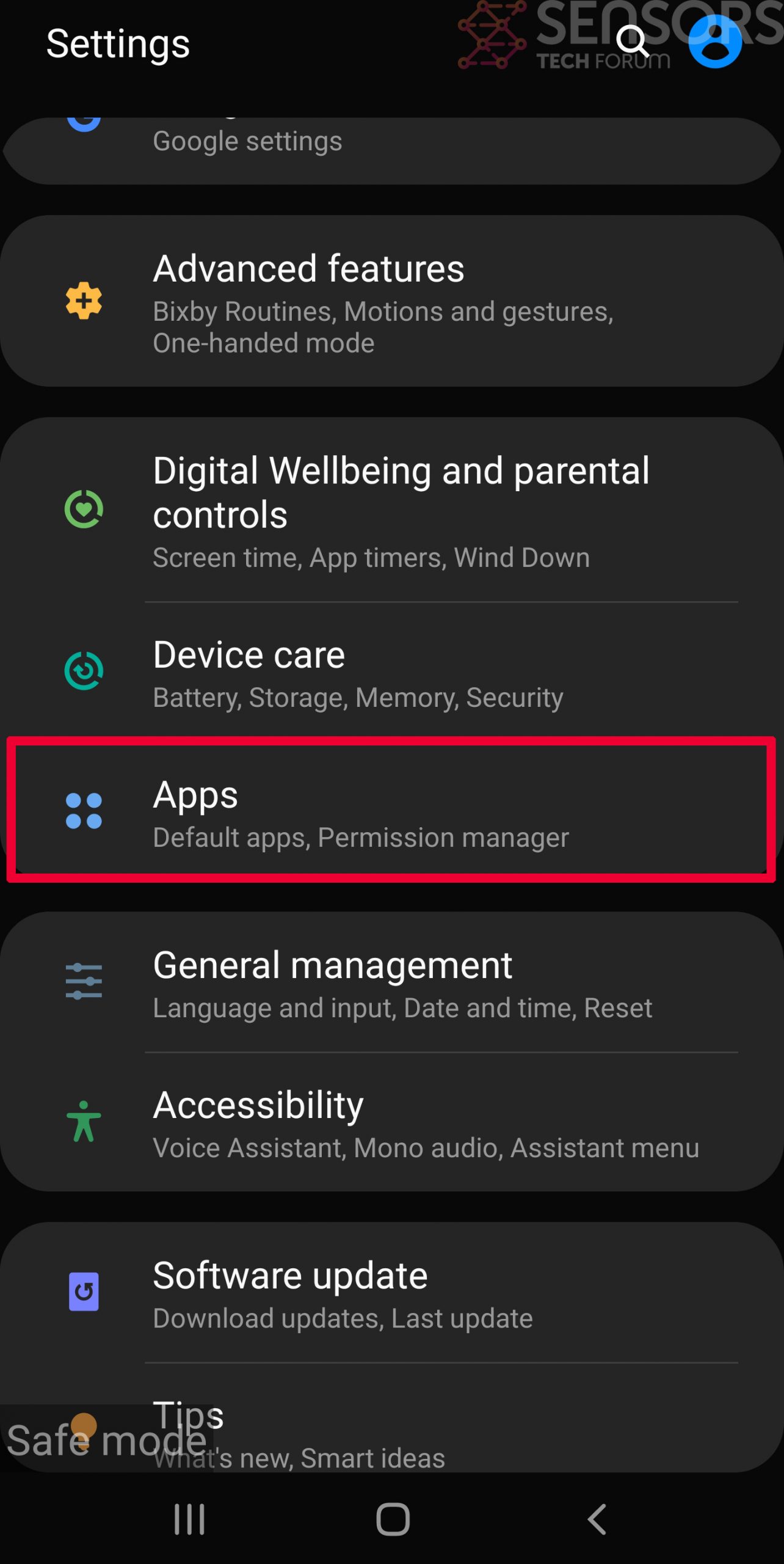
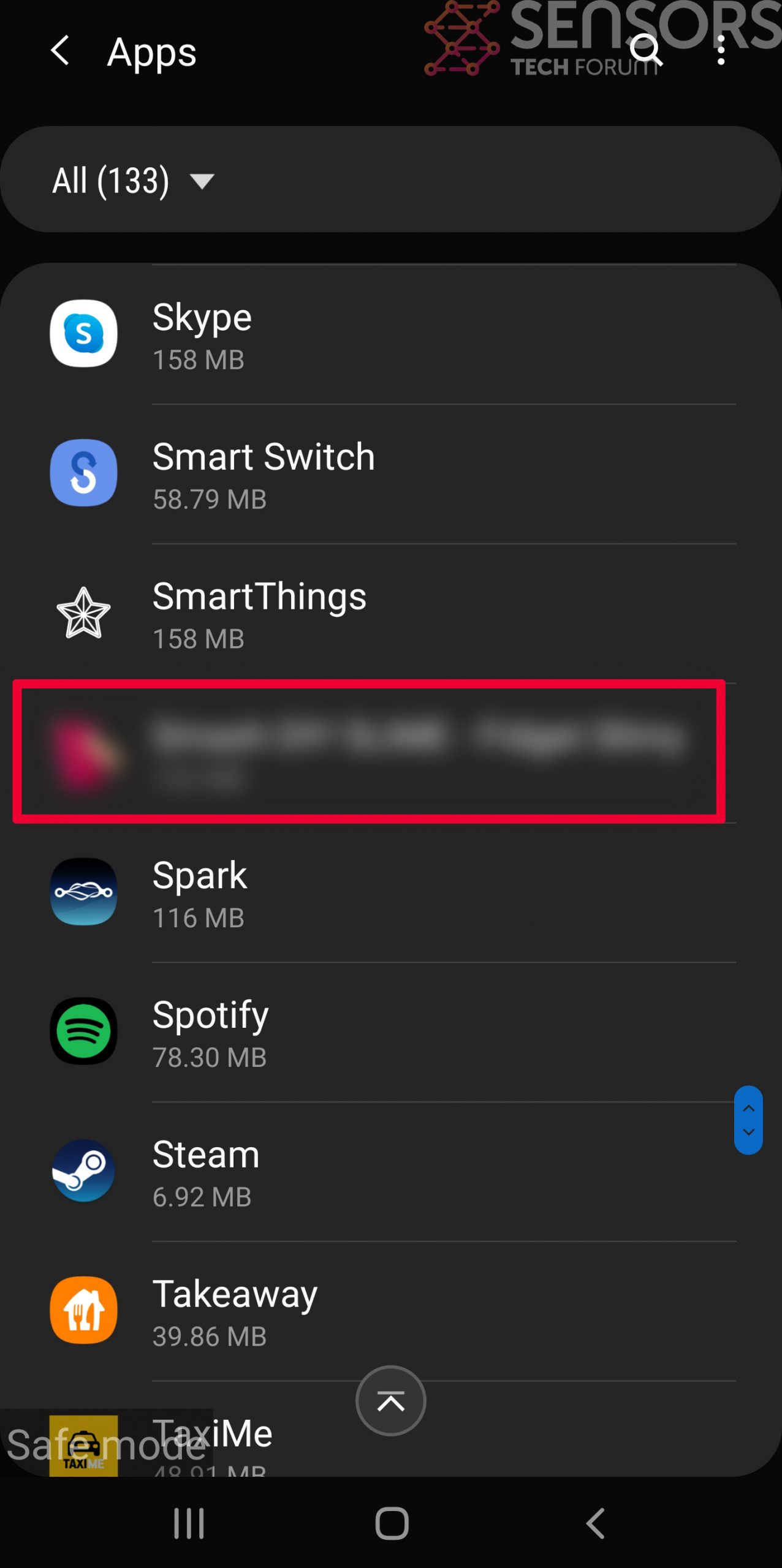
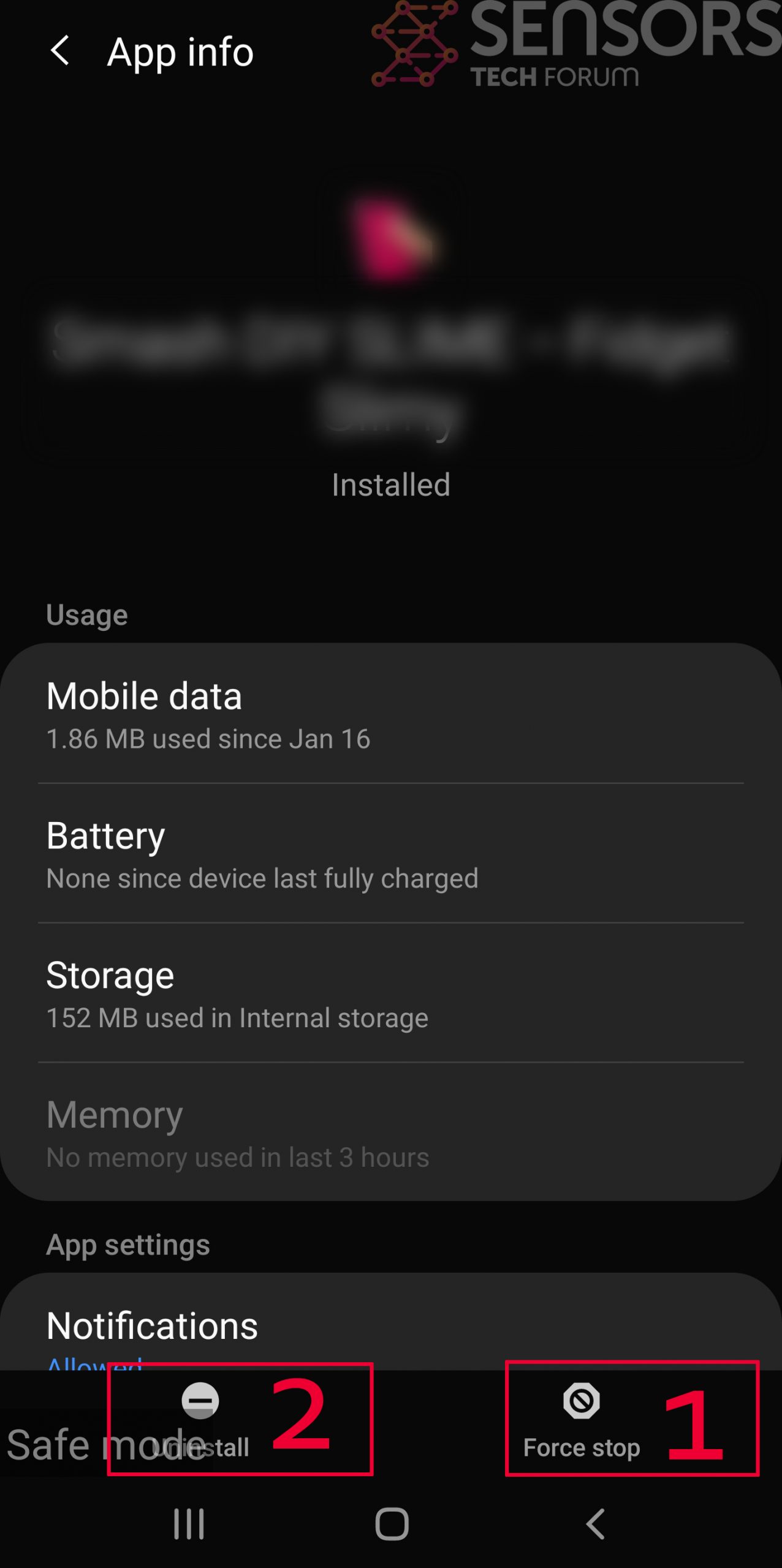
Step 3: Eliminate the App that Your Believe is the Virus
Usually Android viruses get masked in the form of applications. To eliminate apps, follow these mini-steps:
Step 4: Find Hidden Virus Files on Your Android Phone and Remove Them
Simply locate the virus and hold-tap on the virus file to delete it.