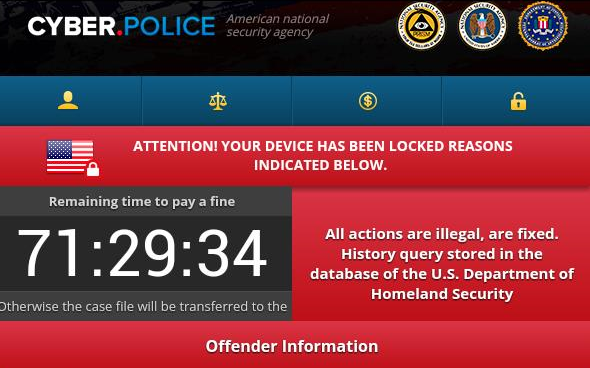
Image Source: Blue Coat
Researchers at Blue Coat have discovered and analyzed a new mobile ransomware campaign that targets older Android devices and doesn’t require user interaction prior to infection. The campaign may be novel but the ransomware has been around since 2014 – Cyber.Police.
Learn More about Cyber.Police’s Previous Attacks
This is perhaps the first time in (mobile) ransomware history when a ransomware is distributed without the “help” of the device’s owner.
If No User Interaction Is Needed, How Is Cyber.Police Spread?
Via malicious ads in the so-called malvertising campaigns. More specifically, the infection takes place when the user visits a compromised website that has bad JavaScript code.
Zimperium’s security researcher Joshua Drake later confirmed that the JavaScript used in the attack contains an exploit leaked in 2015 during the infamous Hacking Team breach. The researcher also confirmed that the exploit’s payload – module.so, a Linux ELF executable – contains the code for an exploit discovered late 2014. The exploit takes advantage of a vulnerability in the libxslt Android library.
Other Stories on Android Malware:
Acecard Trojan Targets Banks
Simple Locker Ransomware
The exploit in question is known as Towelroot or futex. Blue Coat researchers refer to the payload as the ELF payload. No matter of its name, the payload downloads and installs an Android application (.apk) which is, in fact, the ransomware.
It’s also important to note that the lab device which was infected by the ransomware was an older Samsung tablet, running Cyanogenmod 10 version of Android 4.2.2.
A Look into Cyber.Police Ransomware
As already mentioned, Cyber.Police is not new to the malware scene, as it was first detected and analyzed in December 2014. Similarly to other mobile ransomware cases, Cyber.Police doesn’t actually encrypt files, it only locks the device’s screen. Instead of the classical payment in Bitcoins, cyber criminals demand the victim to buy two Apple iTunes gift card codes at the price of $100 each.
Blue Coat researchers also observed unencrypted traffic from their infected device to a command & control server. Such traffic was caught coming from other 224 Android devices. The Android versions were also identified – between version 4.0.3 and 4.4.4.
Another detail about the attack worth mentioning is that some of those 224 devices were not prone to the specific Hacking Team libxlst exploit, which means that other exploits may have been used.
How Can Cyber.Police Be Removed?
The only thing an infected user should do is reset their device to factory settings. As with desktop ransomware, users should also think of backing up the data on their devices. Blue Coat researchers also advice on “using a more up-to-date browser than the built-in Browser app included with Android 4.x devices”.
In case you have lost your files, you can try using a recovery program such as Android Data Recovery Pro by Tenorshare.


