Another phishing campaign has been discovered by Heimdal researchers, taking advantage of Delta Air and downloading Hancitor malware. The potential victim receives an email disguised as a payment confirmation email from the company.
Your Order with Delta Air Lines Has Been Confirmed Phishing Scam
As explained by the researchers, using an airline to masquerade malicious intentions is not random, since many airlines offer discount rates for summer flights at this time of the year. If you have received an email with a subject line “Your order [numbers] with Delta Air Lines has been confirmed!” without having made a reservation, proceed with caution!
Here is what the spam email containing malware looks like:
As with every phishing email, a careful eye would immediately spot several inaccuracies pointing to the unauthentic origin of the message:
- First of all, the email address is not legitimate and does not belong to the said company. If it was the company’s email, it should have ended with “@delta.com” not “@deltaa”.
- No specific information about the flight is given. If this was truly a confirmation email, it should have contained details about the booked flight, and uses the lack of information to lure the user into clicking the provided link.
- The visual format of the email does not correspond to Delta’s usual emails. If you are a customer of the company, you should definitely find this inaccuracy suspicious.
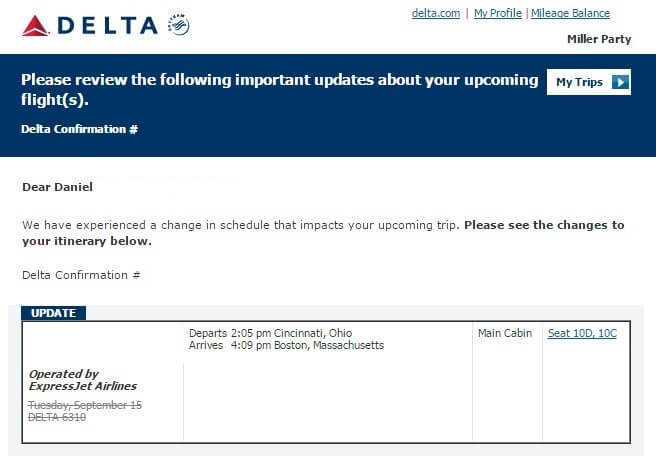
To compare the two emails and see the differences for yourself, here is what a legitimate email sent by the company looks like:
More About the Delta Air Phishing Campaign
Hancitor Malware and Zloader Downloaded onto Compromised Systems
The email s obviously created to scare the user into believing that someone used their credentials and identity to buy an airline ticket. The user would typically panic and would interact with the provided links, which is in fact a very bad idea. The links would redirect the user to infected websites that host Microsoft Word documents containing the Hancitor malware. Hancitor is a versatile piece of malicious code which is often employed in phishing attacks.
The malware is typically used as a bridge to enable future attacks on the compromised system. This means that more malware is about to be downloaded on the computer.
Related: Microsoft and Google’s Cloud Infrastructure Abused by Hackers in Phishing Emails
Once the user downloads Hancitor via the malicious Word document the malware will be activated. As a result, legitimate system processes will be infected via a PowerShell code. Then, the infected system will be connected to one or more Command and Control servers.
Finally, additional malware of the Pony malware family will be downloaded.
As we have previously written, Pony was first introduced in the cyber world years ago. The infamous information stealer has been used to spread Zeus and Necurs Trojans, as well as Cryptolocker and Cribit ransomware.
More specifically, this phishing attack uses Zloader, which is a Pony-based malware. Zloader is a banking malware targeted at victims’ bank accounts.