The adoption of cloud collaboration tools in organizations has increased, and so has the interest of hackers.
The adoption of cloud collaboration tools in organizations has increased, and so has the interest of hackers.
According to a new research by Proofpoint, there has been an acceleration in threat actors exploiting Microsoft and Google’s cloud infrastructure to host and send malicious messages. Applications abused in the attacks include Office 365, Azure, OneDrive, SharePoint, G-Suite, and Firebase.
Threat Actors Exploiting Microsoft and Google’s Cloud Infrastructure
“Last year, 59,809,708 malicious messages from Microsoft Office 365 targeted thousands of our customers. And more than 90 million malicious messages were sent or hosted by Google, with 27% sent through Gmail, the world’s most popular email platform,” Proofpoint said. In the first quarter of 2021, the researchers observed seven million malicious messages from Microsoft Office 365 and 45 million malicious messages from Google infrastructure, far exceeding the results from last year.
It is noteworthy that the volume of malicious messages sent from the trusted Microsoft and Google’s services exceeds that of any botnet in 2020. This is mostly due to the trusted reputation of domains such as outlook.com and sharepoint.com, which makes detection more challenging for defenders.
“This authenticity perception is essential, as email recently regained its status as the top vector for ransomware and threat actors increasingly leverage the supply chain and partner ecosystem to compromise accounts, steal credentials, and siphon funds,” the report highlighted.
Last year, hackers targeted 95% of organizations with cloud account compromise attempts.
More than half experienced at least one compromise. 30% of the enterprises that experienced attacks also suffered post-access activities such as file manipulation, email forwarding, and OAuth activity. In case of stolen credentials, malicious actors can also log into systems, move laterally across multiple cloud services and hybrid environments, send emails as real employees, leading to financial and data loss.
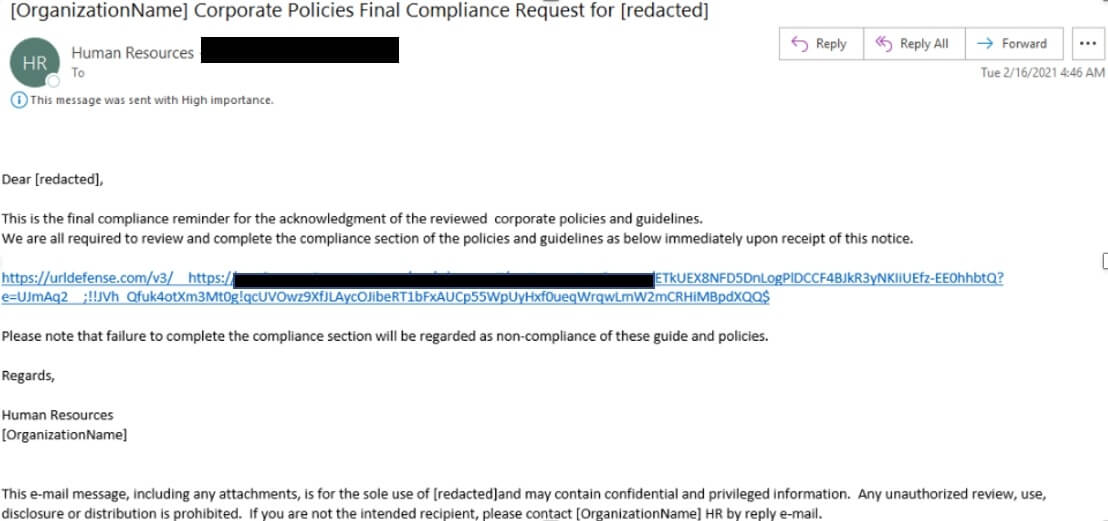
The researchers also shared real samples of recent phishing campaigns abusing Microsoft and Google. Below is a credential phishing attempt featuring a Microsoft SharePoint URL claiming to contain a corporate policy and Covid-19 guidelines:
“The document contains a link leading to a fake Microsoft authentication page designed to harvest user credentials. This low volume campaign involved approximately 5,000 messages targeting users in transportation, manufacturing, and business services,” the report said.
Phishing Becoming More Sophisticated
Last year, Microsoft and Google were abused in attacks against remote workers that work for well-known companies. Threat actors created fake and fraud sites with landing pages and login prompts resembling Google and Microsoft. OneDrive, Office Online and Mailchimp were used in the attacks.
Phishing operators, in general, continue to look for new ways to carry out their attempts and increase their success rate. Earlier this year, we reported about a novel obfuscation technique that uses Morse code to conceal malicious URLs within an email attachment. This was perhaps the first case of threat actors utilizing Morse code in such a way.