A new health-related scam has been detected circling the web, and it’s not related to the coronavirus. Apparently, phishers are now exploiting the fear of HIV.
Scammers have been sending people fake HIV test results containing malicious code, masqueraded to look like as if they were sent by Vanderbilt University’s respected medical center. This phishing scam was disclosed by researchers at Proofpoint.
Fake HIV Results Spam Campaign: Some Details
In this latest healthcare scam, phishers were impersonating Vanderbilt University Medical Center in fake emails luring potential victims to open malicious content embedded into the message.
This low volume campaign had top targeted industries: global insurance, healthcare, and pharmaceutical organizations, but others were targeted as well, Proofpoint said. As for the malware lurking in the emails, scammers chose to use Koadic RAT which allowed attackers to run programs and access victims’ sensitive data, such as personal and financial information.
How do the spam emails look like?
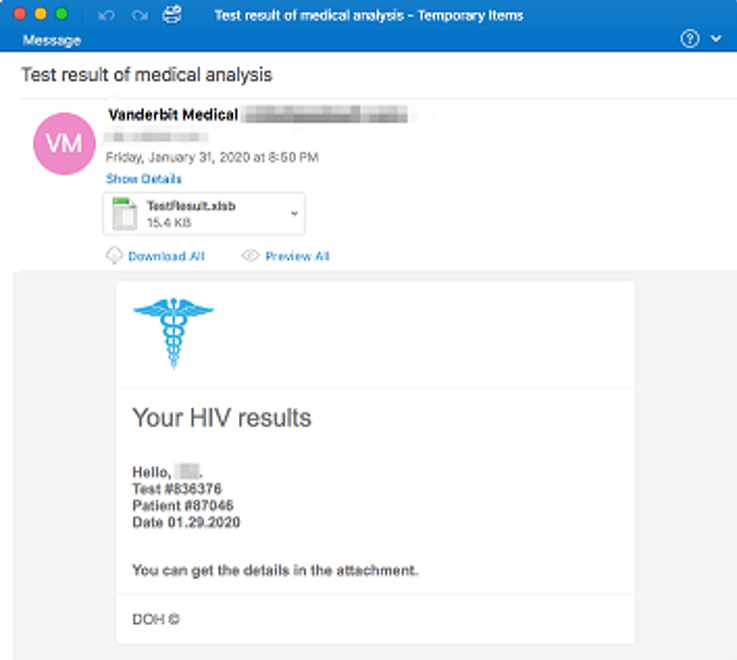
The subject line of the spam campaign was identified to be the following: “Test results of medical analysis”. The email body lures recipients to open a malicious Microsoft Excel attachment called “TestResults.xlsb” which is supposed to contained HIV results. Of course, nothing claimed in these emails is true.
Here’s a sample email of this healthcare spam campaign:
So, what happens after the victim opens the malicious Excel document and enables macros?
If this is done, the document would download the Koadic RAT. It is noteworthy that originally Koadic was created as a tool for network defenders. The original platform was first presented at the Defcon security conference by its developers — Sean Dillon and Zach Harding.
However, Koadic was adopted by threat actors, and has been leveraged by a variety of nation state actors, including Chinese and Russian state-sponsored hackers, Proofpoint researchers say.
This is not the only health-related scam currently active in the wild.
There have been multiple campaigns exploiting the public panic related to the Coronavirus. We recently wrote about one such spam campaign, which was spreading malicious files masqueraded as documents with video instructions on how to protect against the coronavirus. Instead of learning anything useful, the potential victim would get a computer infection ranging from Trojans to worms, revealed telemetry data from IBM X-Force and Kaspersky.