| Name | Hammertoss |
| Type | Backdoor Malware, Malware strain |
| Short Description | Hammertoss employs legit web services, uses stealthy algorithms and is persistent to forensic researchers’ detection. |
A new Russian malware has surfaced the Web. It is called Hammertoss and is a malware strain with backdoor capabilities. Hammertoss is attributed to a Russian group called APT29 and has been discovered by researchers at FireEye Inc. They have been closely monitoring APT29’s activities and even suspect that the hackers’ group has something to do with the Russian government.
Hammertoss Attack Stages Explained
Hammertoss’s attack consists of five stages and affects corporate clients. The malware piece is quite sophisticated, and its creators have reassured to cover their tracks in the stealthiest way. The researchers at FireEye have identified a range of techniques. Here is how the malicious tool operates:
-
1. Employing legit web servers – Twitter, GitHub, to retrieve commands.
2. Algorithms initiating daily and automated Twitter handles.
3. Employing timed starts on a particular date or within a given period, usually the victim’s workweek.
4. Embedding pictures with commands and encrypted data.
5. Using a compromised network to upload files and extract information via cloud services.
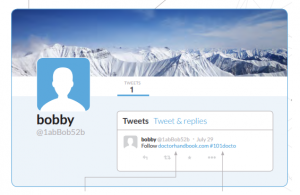
The Hammertoss operation starts off with Twitter. This is where the malware first looks for instructions. The algorithm generates daily Twitter handles. To do that, a basename is employed, for instance, Mike, and three CRC32 values based on the date are created. Here is an example of the basename – labMike.52b. The URL will be something like hxxps://twitter.com/1abMike52b. If a day’s handle is not registered or found, as well as the URL itself, Hammertoss is set to wait until the next day to try yet again to connect with another handle. Shortly said, the Hammertoss malware will blend in the victim’s environment and can remain dormant until activated.
The Twitter Hashtag Explained
If APT29 has registered a particular’s day handle, the group will then tweet a URL and a hashtag. The URL is used to direct Hammertoss to a website that has one or multiple images. The hashtag itself is used to provide a location number and characters for subjoining to an encryption key to decipher the instructions within the image.
The malicious tweet contains a hashtag with instructions to extract encrypted data from the corrupted image file. The characters to be employed for the decryption process are ‘docto’, as visible on the image provided by the FireEye researchers team.
APT29 Hackers Group. Who Is Behind It?
According to the researchers at FireEye, APT29 is most likely sponsored by the Russian government. Having a look at the group’s victims and targets is enough to make such a conclusion. Furthermore, the group’s malicious activities usually take place during official Russian holidays. The time zone for their attacks is usually set at TC +3 – the time zone for cities such as Moscow and St Petersburg. The timetable and overall performance of APT29 speak out tight discipline and coherence, which makes them one of the best – and scariest hacking teams out there.
One of the patterns that differs the group from other hacking teams is the anti-forensic technique used to baffle forensic investigators and their methods. Another stealthy feature found in APT29’s attacks is the monitoring of the victim’s efforts to overthrow them. Their malware pieces are always rapidly developed thanks to the modifying tools they use to sabotage detection.
To summarize, Hammertoss is designed to impair network defenders’ abilities and efforts to recognize Twitter accounts used for Command and Control operations, foresee malevolent network traffic from legitimate activity, and uncover the malicious payloads activated and downloaded by the malware.
To fully understand how the Hammertoss malware works, have a look at the report.