A new rare technique, used by a cybercriminal group to steal payment card data, has been identified by security researchers. Cyber criminals are using a piece of sophisticated malware that is activated before the Windows operating system boots.
Hence, the technique becomes known as bootkit, which operates on lower-level system components to evade identification and detection. The methods employed by bootkits make them quite persistent. The bootkit may still be there even after the victim reinstalls the operating system.
Researchers at FireEye have been investigating many cases of such malicious operations, targeting personal and financial data. The FireEye team recently detected the bootkit activity described above within a financial enterprise network. The cybercriminal group suspected to be behind the curtains is FIN1 and is most likely of Russian origin. The group has been deploying malicious tools within that unspecified financial enterprise for years now, all of which part of a malicious ecosystem known as Nemesis. Nemesis has been employed to harvest cardholder data that can be monetized by financial services (banks, ATMs, credit unions, etc.).
Other Bootkits:
HDRoot Bootkit
What is specific about Nemesis Bootkit?
The first alarming thing about Nemesis is that it uses extensive backdoors, which support a number of network protocols and command & control communication channels. According to the vast security research by FireEye, Nemesis has the following capabilities:
- File transfer;
- Screen capture;
- Keystroke logging;
- Process manipulation;
- Process injection;
- Task scheduling.
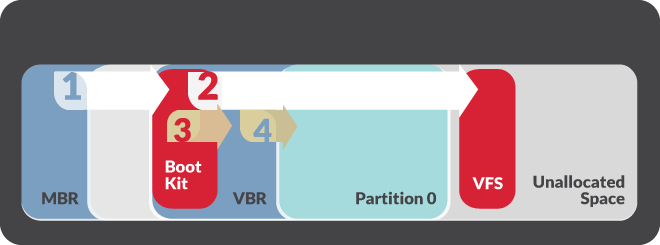
Besides those malicious capabilities, Nemesis has been observed to update its service during ongoing attacks. For example, at the beginning of 2015 FIN1 updated Nemesis to add a tool that alters the legitimate Volume Boot Record or VBR. The update also included the capability to hijack the system boot process so that the Nemesis components are added prior to the booting of Windows OS. FireEye dubbed this utility BOOTRASH.
How does the malware hijack the boot process?
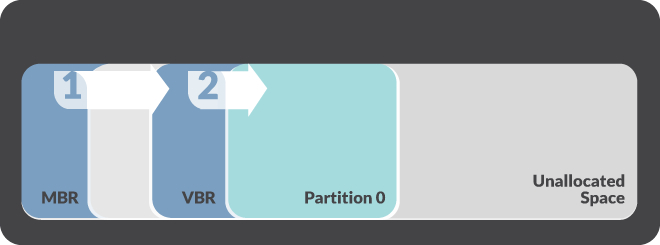
BOOTRASH uses a complex process to create a custom virtual file system which stores the Nemesis components in the unallocated space between partitions. Then, the malware replaces the bootstrap code with its own malicious content and overwrites the original VBR. The bootstrap code calls the Nemesis bootkit. As a result, the latter deflects several boot process functions and implements Nemesis components into the Windows kernel.
Nemesis may not be our regular financial malware, but it is not the first piece that applies bootkits. For example, two years ago RSA warned about a banking Trojan dubbed KINS, which also had VBR bootkit capabilities. Then, in 2013, the Carberp Trojan with bootkit functionalities was spotted in the wild, being sold for $40,000 on underground forums.
Learn More about Banking Trojans:
Carbanak
Bartalex
Researchers warn that persistent threats of this kind should not be perceived only as financial threats. Other Advanced Persistent Threats (such as ROCKBOOT) have been reported to target not only financial but also intellectual property from victim organizations.
Furthermore, the access and utilization of bootkits suggest that cyber groups may have access to more sophisticated malware sets. Such APT methods can be deployed when a targeted organization turns difficult to penetration, or when the targeted data is of great value and continued access is needed.
Is there any protection against bootkits?
As already said, bootkits are quite persistent and are designed to evade detection by being executed outside of the operating system. Classic OS integrity checks will not do the work as well. Furthermore, the components used to load the payload are stored in VFS (Virtual File System) outside Windows, as well as the malware components as well. Shortly said, because of this fact, the malware cannot be typically scanned by AV software. The only place where the malware may be located in live memory.
During their investigation, the FireEye team used Mandiant Intelligent Response – a host-based technology that provides raw disk access and can look for malware outside Windows. Thanks to MIR, the security team was able to identify systems with modified VBR.
More on Incident Response:
CVE and Incident Response
In conclusion, this is the best advice so far given by the security professionals:
The use of malware that persists outside of the operating system requires a different approach to detection and eradication. Malware with bootkit functionality can be installed and executed almost completely independent of the Windows operating system. As a result, incident responders will need tools that can access and search raw disks at scale for evidence of bootkits. Similarly, re-installing the operating system after a compromise is no longer sufficient. System administrators should perform a complete physical wipe of any systems compromised with a bootkit and then reload the operating system.
References
Mandiant Intelligent Response
FireEye