Social media platforms, often seen as arenas for connection and expression, have become breeding grounds for financially motivated threat actors orchestrating large-scale attacks.
Bitdefender Labs has been vigilant in monitoring a growing trend where cybercriminals exploit social media networks for malvertising, a sinister combination of malware and advertising. The objective is clear: hijack accounts and pilfer personal data through the deployment of malicious software. The malware in question is known as NodeStealer.
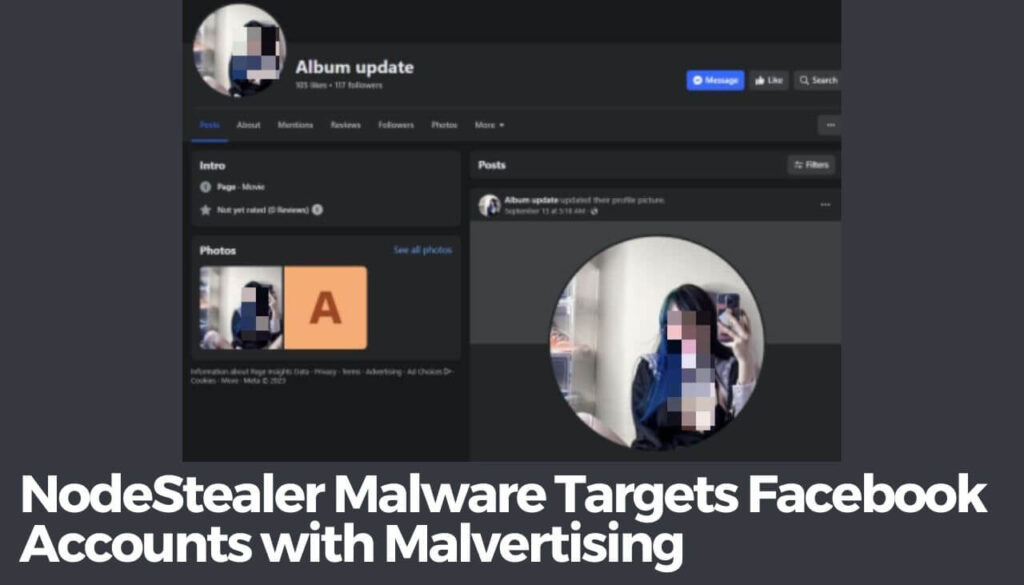
A Look into NodeStealer Attacks
NodeStealer is a relatively new but potent info-stealer, designed to exploit Meta’s ad network on Facebook, posing a direct threat to user privacy and security. The Bitdefender analysis, conducted from October 10 to 20, uncovers a sophisticated campaign that exploits compromised business accounts, delivering malicious ads to the public.
According to the original research, here are the key findings:
- At least 10 compromised business accounts are actively serving malicious ads.
- The ads deploy a newer version of NodeStealer.
- Multiple Facebook profiles, featuring alluring images of women, are created by threat actors.
- Approximately 140 malicious ad campaigns utilize multiple iterations of the same ad.
- Attackers strategically rotate between a maximum of 5 active ads every 24 hours to evade user reports.
- Clicking on these ads initiates the download of a malicious archive, containing a deceptive “.exe Photo Album” file, leading to the deployment of a second executable in .NET. This secondary payload is designed to steal browser cookies and passwords.
- The analysis estimates a potential 100,000 downloads based on the ad reach, with up to 15,000 downloads for a single ad within a 24-hour span.
- The most impacted demographic is males aged 45 and above.
This campaign’s demographic and reach information has been collected through tracking the ads on Meta Ad Library.
NodeStealer, initially discovered by Meta’s security team in January 2023, operates as an info-stealer capable of hijacking browser cookies and executing account takeovers at scale.
NodeStealer 2.1 Adds New Features
The evolving saga of NodeStealer’s malicious endeavors on Facebook unfolds, with threat actors employing innovative methods, including the exploitation of compromised business accounts to target regular users.
This modernized version (NodeStealer 2.1) boasts new features that extend its reach to additional platforms like Gmail and Outlook, aiming to steal crypto wallet balances and unleash further malicious payloads.
The visuals on display within these ads, seemingly innocent at first glance, hide a malicious threat. A closer inspection reveals artfully manipulated or even artificially generated images designed to exploit human curiosity. Exploiting the psychology of anticipation, attackers employ succinct yet alluring descriptions, beckoning users with messages like “New stuff is online today” and “Watch now before it’s deleted.”
Unbeknownst to the user, the seemingly innocuous “Albums” advertised in these campaigns serve as gateways to repositories on platforms like Bitbucket and Gitlab. Concealed within these repositories lies a malicious payload – a Windows executable poised to unleash the insidious NodeStealer onto the unsuspecting user’s device. This stealthy infiltration marks a disturbing evolution in cyber threats, leveraging enticing content as a trojan horse for more insidious intents.
A chilling aspect of these orchestrated attacks is the calculated use of Meta’s Ads Manager tool. The campaigns strategically zero in on male users aged 18 to 65 across Facebook, spanning the continents of Europe, Africa, and the Caribbean. The precision of the targeting amplifies the threat, demonstrating a keen understanding of the social media landscape and the vulnerabilities of a specific demographic.


