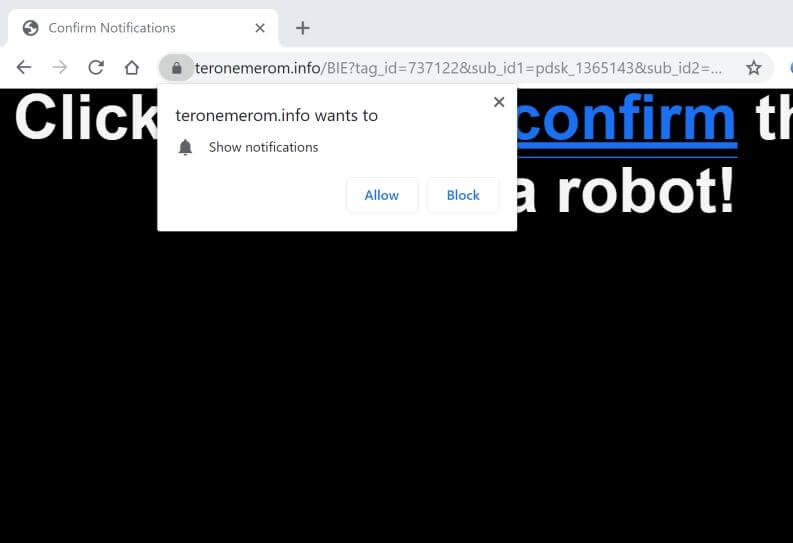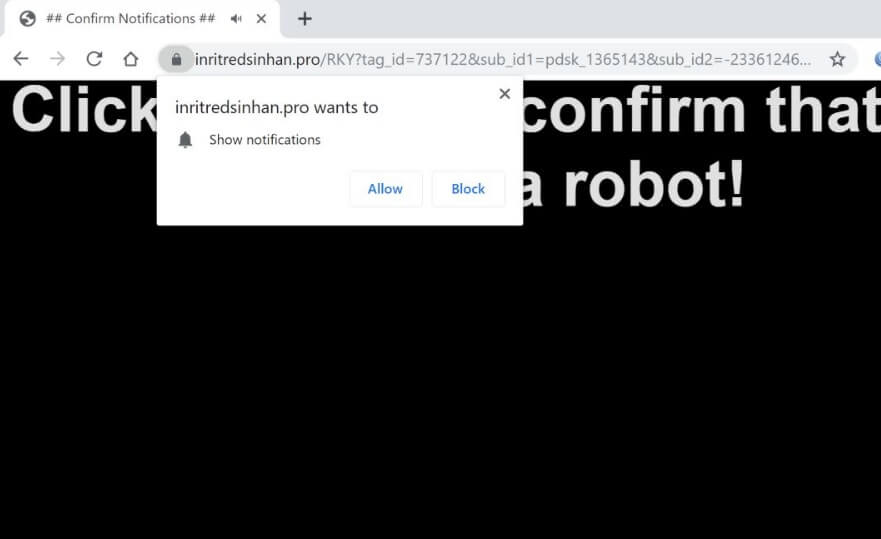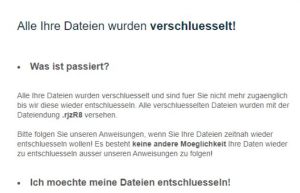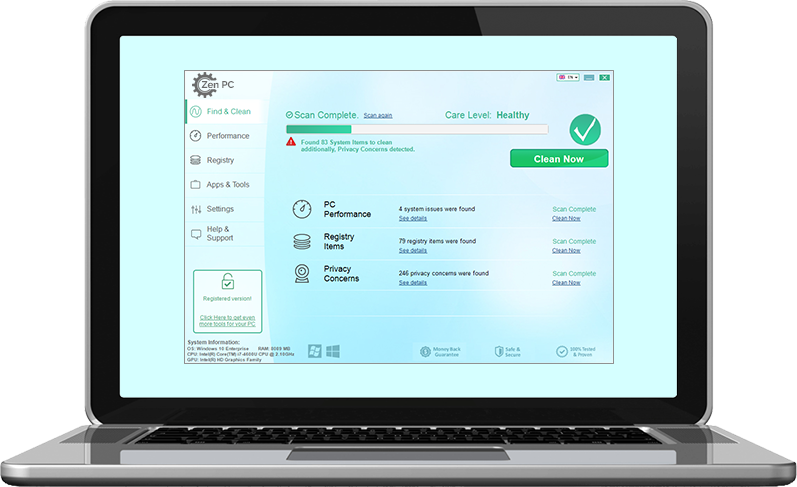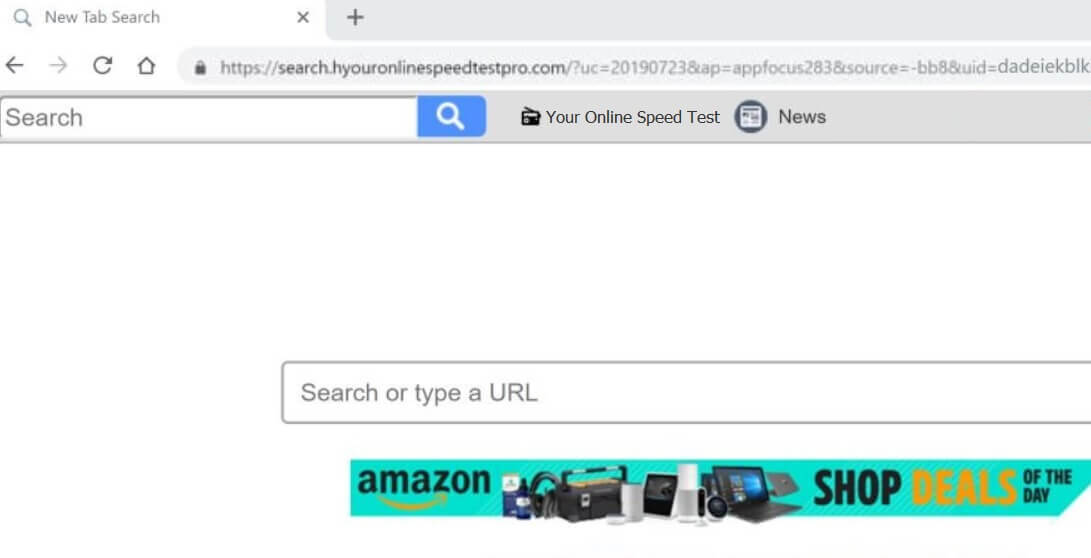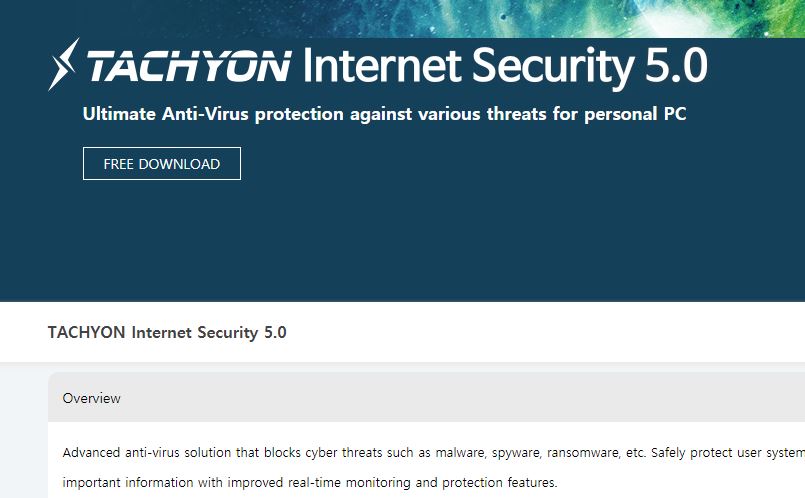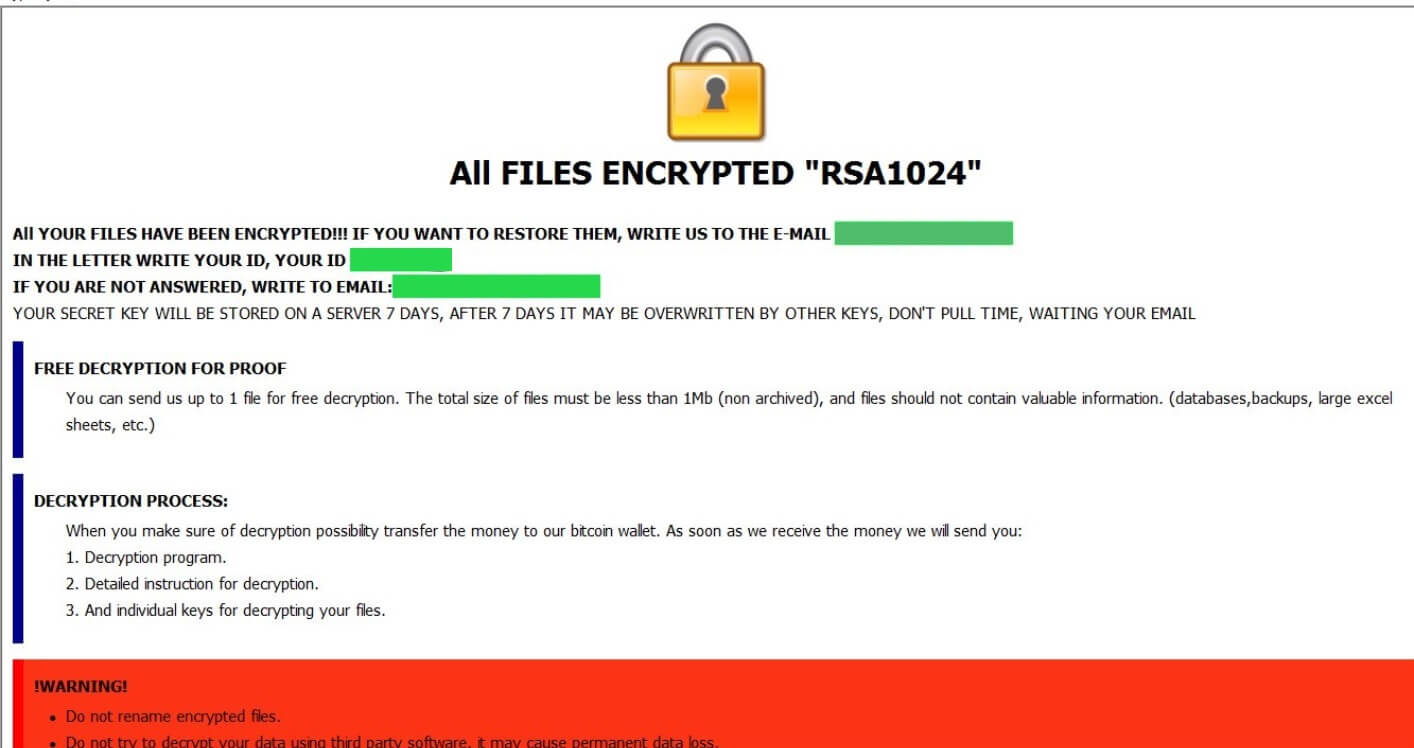
Remove Feethatnot.info Redirect
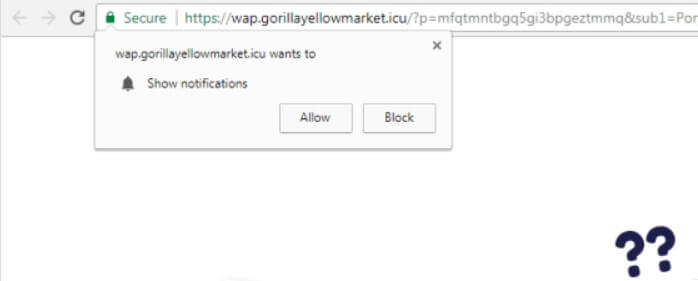
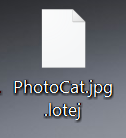
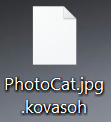
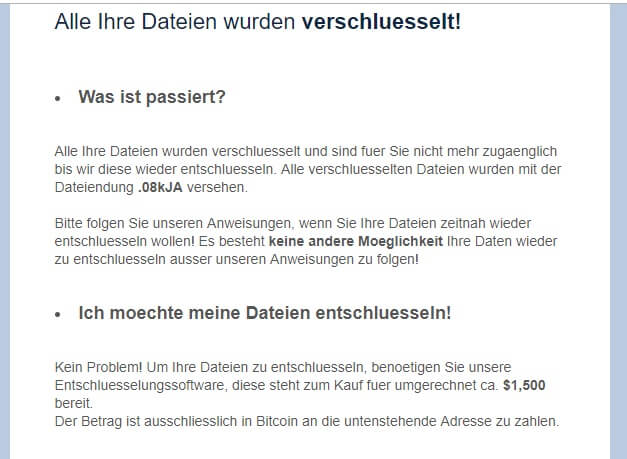
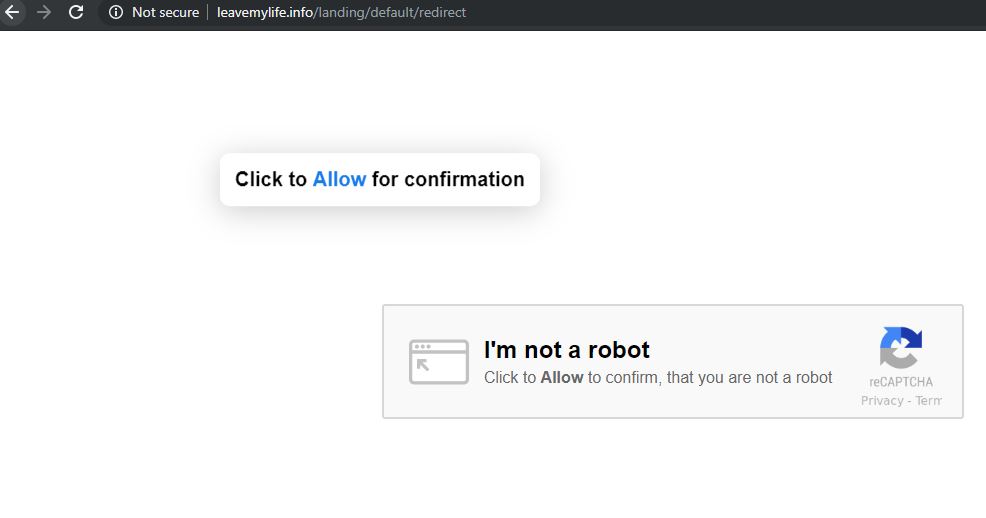
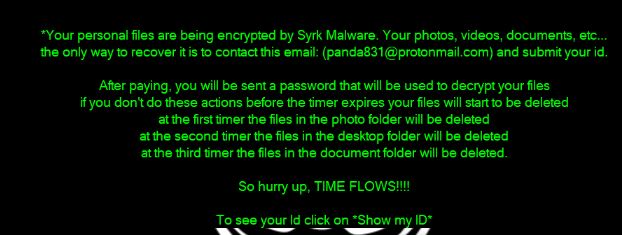
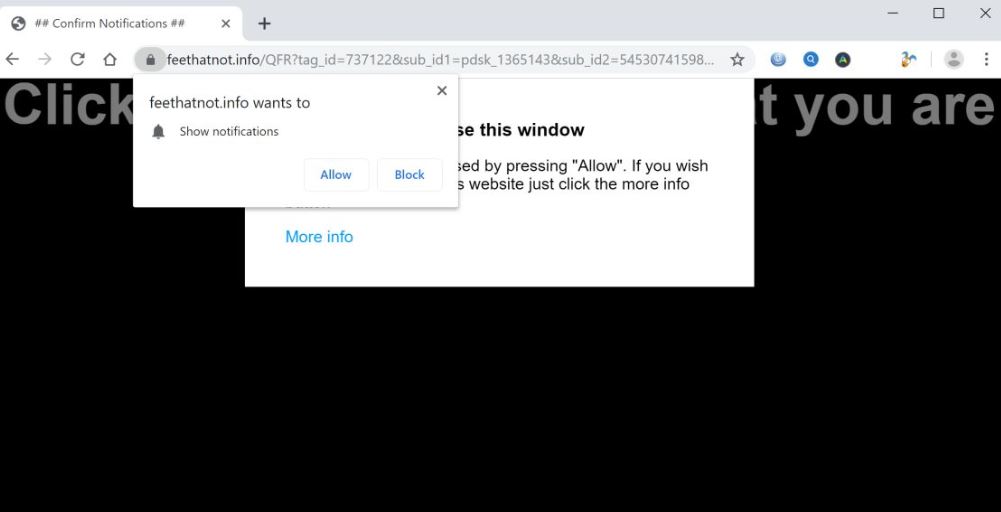
What is Feethatnot.info page? Which program causes Feethatnot.info redirects? How to remove the unwanted program, causing Feethatnot.info redirects from your computer? The Feethatnot.info redirect is a web browser hijacker and dangerous site which are currently distributed in an active attack…