Remove “Save Yourself Email” Scam Virus (Updated October 2019)
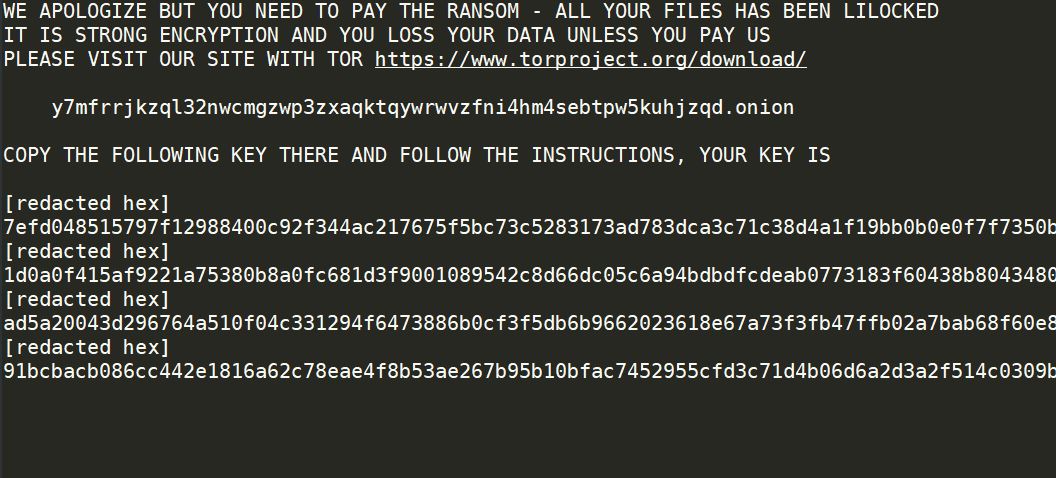
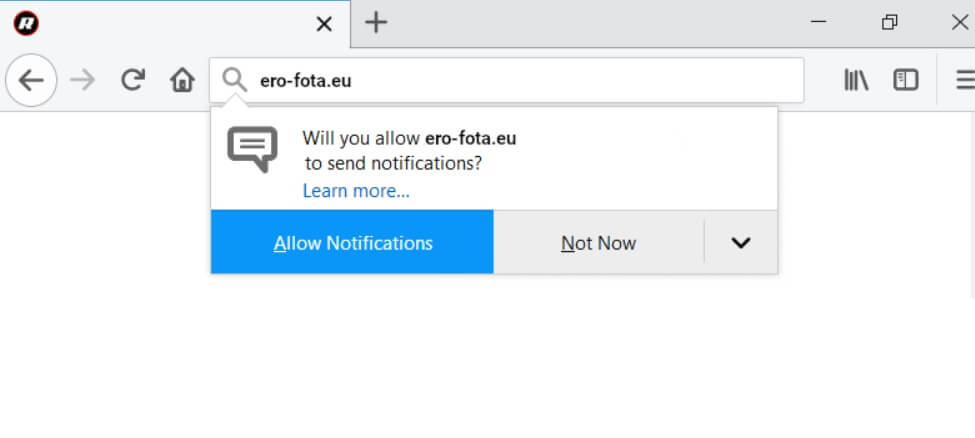
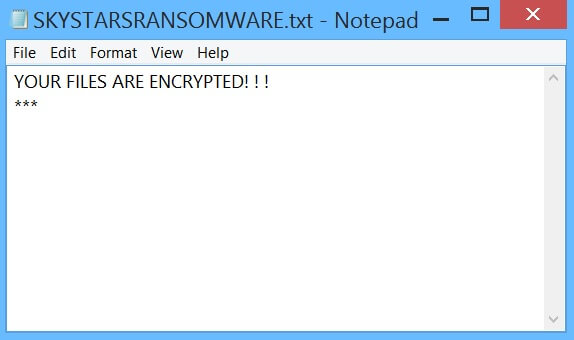
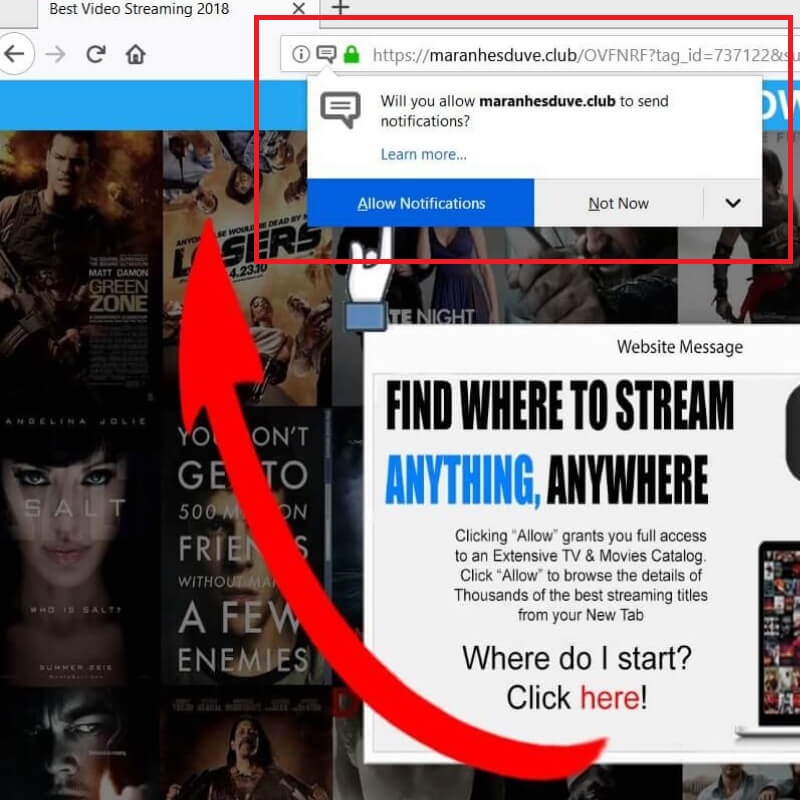
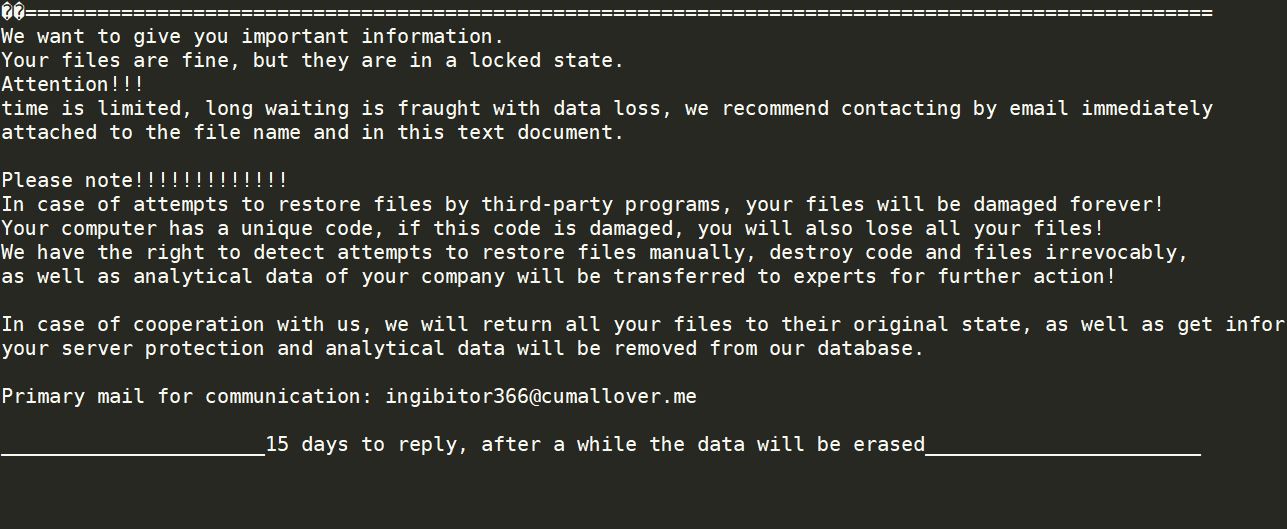
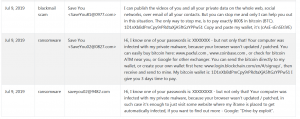
Update October 2019. What is the “Save Yourself” e-mail scam? What are the “Save Yourself” scam messages? How to stop “Save Yourself” e-mail scam? How to remove the “Save Yourself” e-mail scam from your computer thoroughly? The “Save Yourself” e-mail…