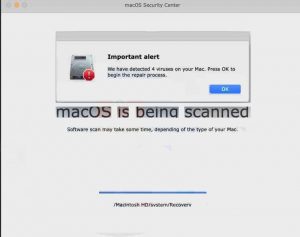
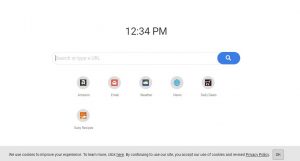
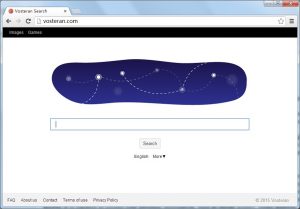
BestBuy Virus – How to Remove It (Illustrated Removal Guide)
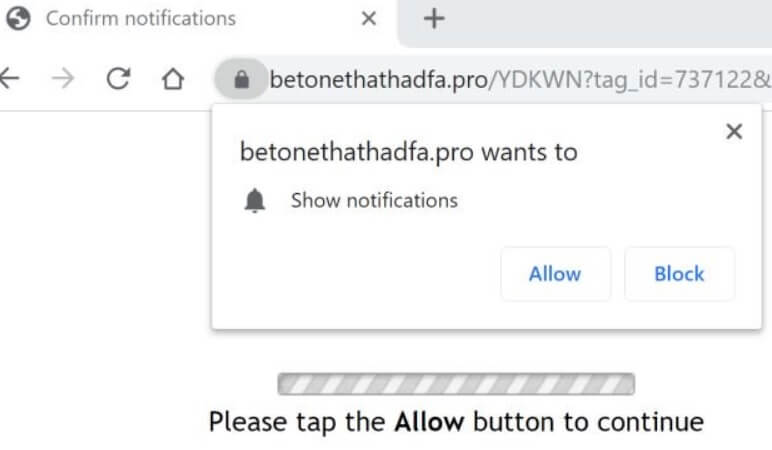
What are BestBuy viruses? Is a BestBuy virus dangerous? How to remove a BestBuy virus from your computer? BestBuy virus infections can happen through multiple ways. They take advantage of the name of the shopping site in order to promote…