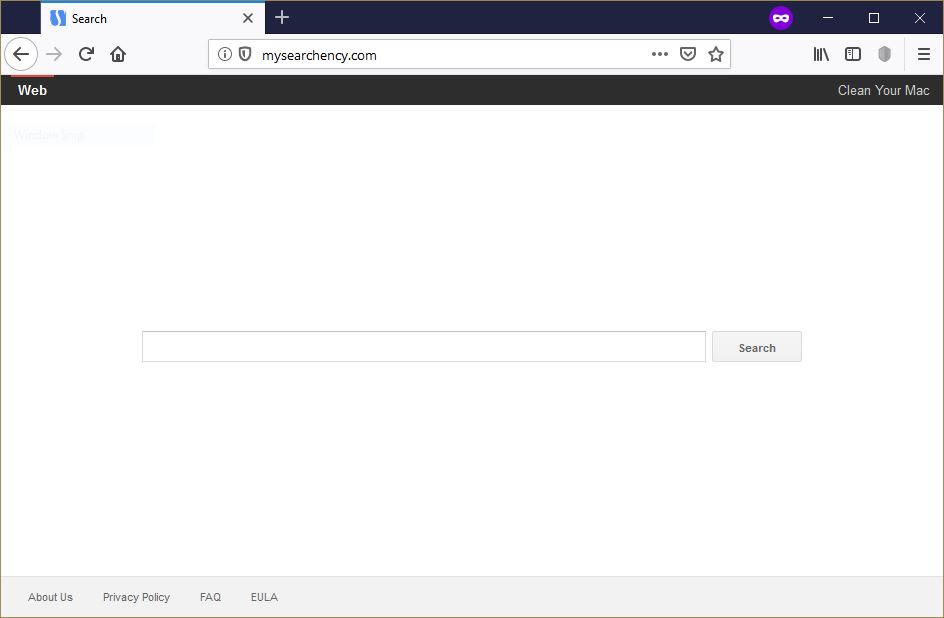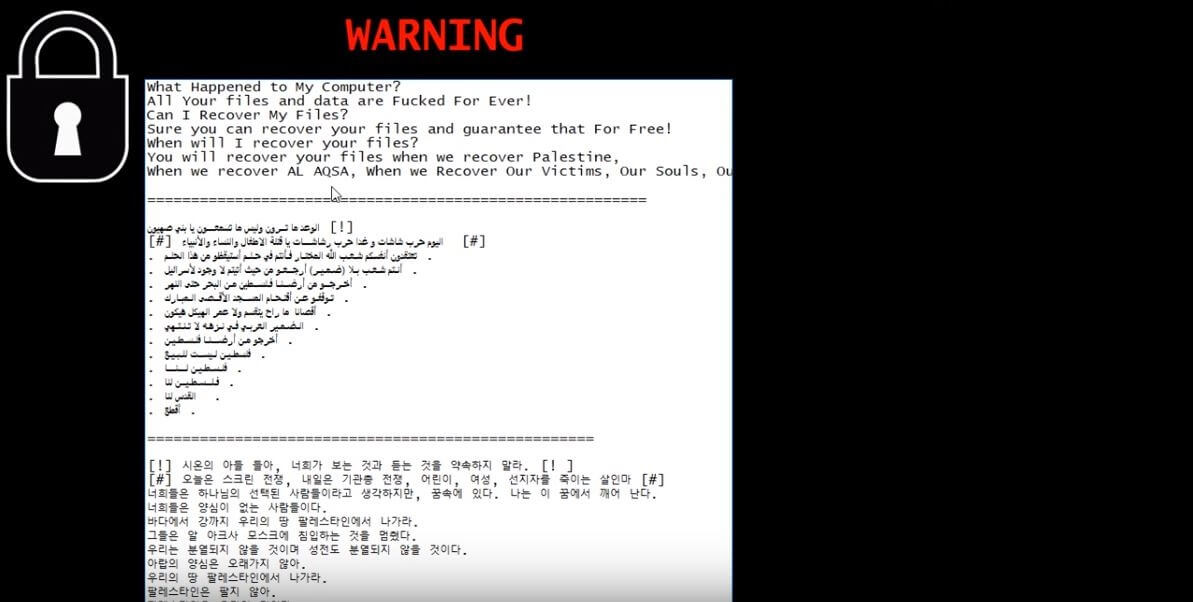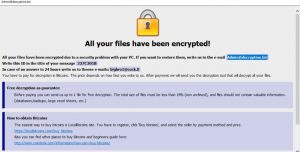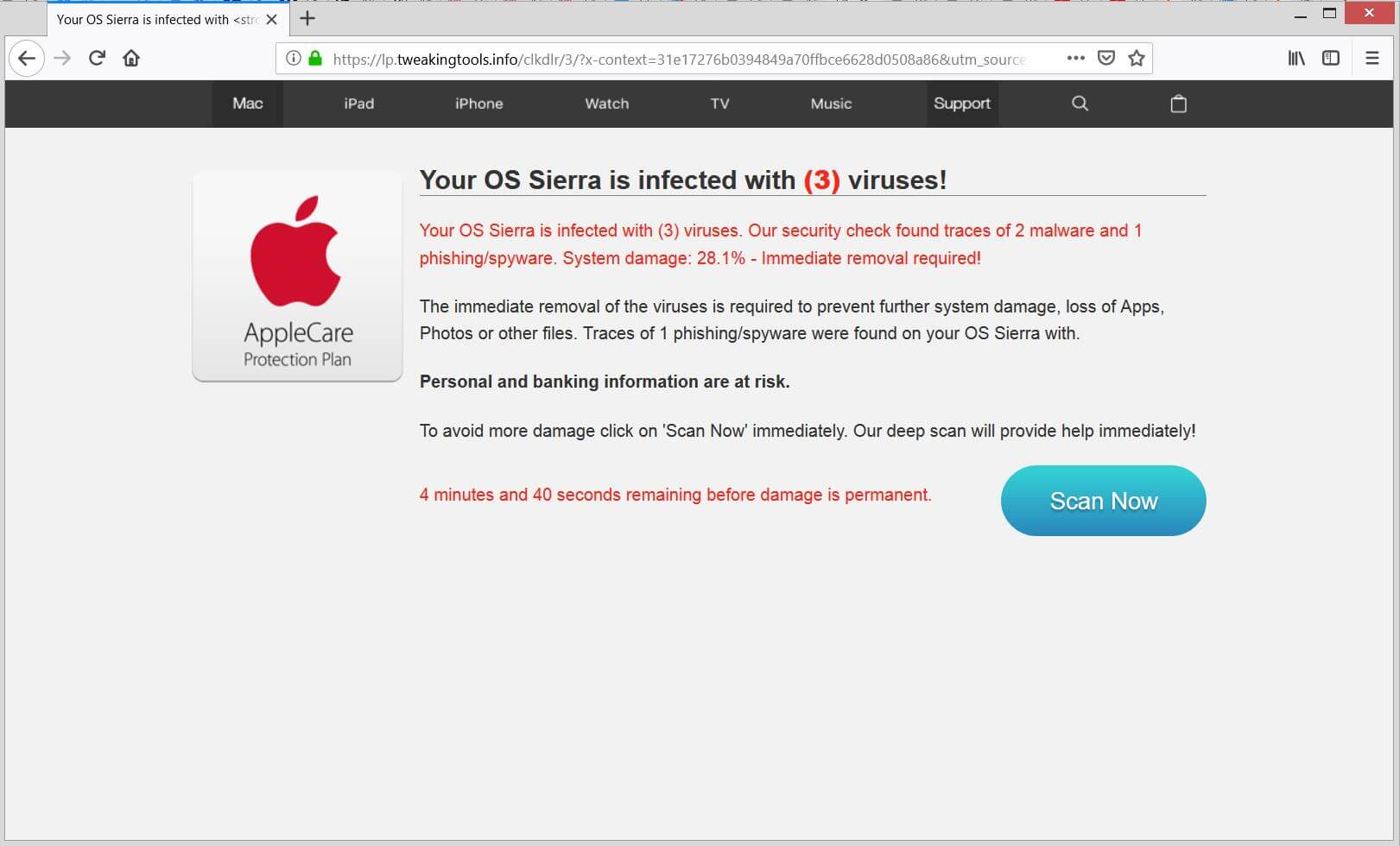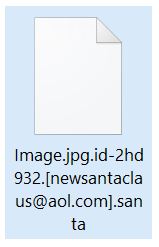
.santa Files Virus (Dharma) – How to Remove It
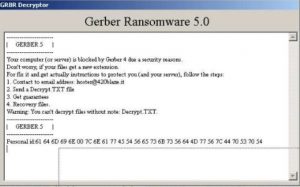
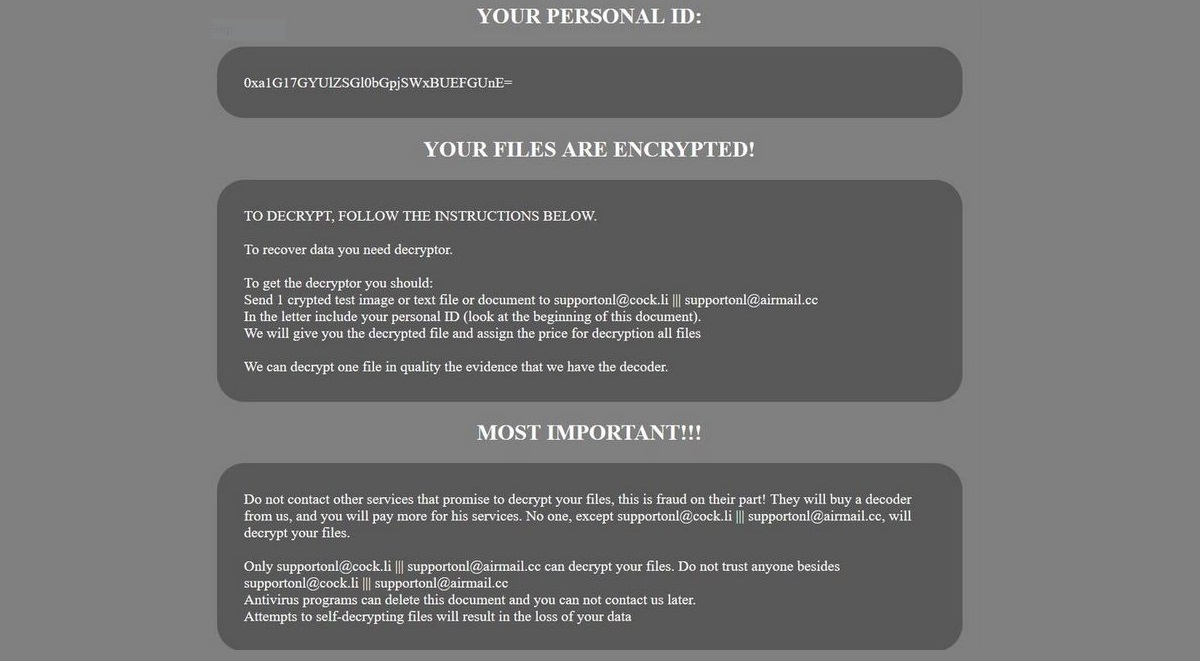
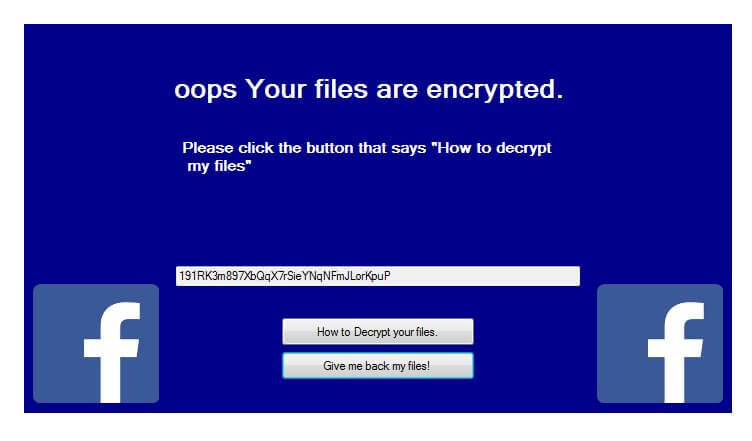
This blog post has been made to explain what is the .santa file version of Dharma ransomware and how you can remove it plus restore files, encrypted by it on your computer. A new variant of Dharma ransomware has surfaced…