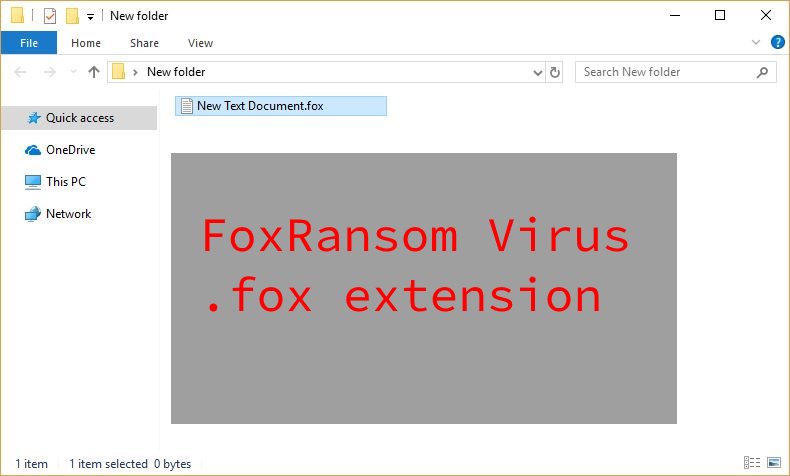
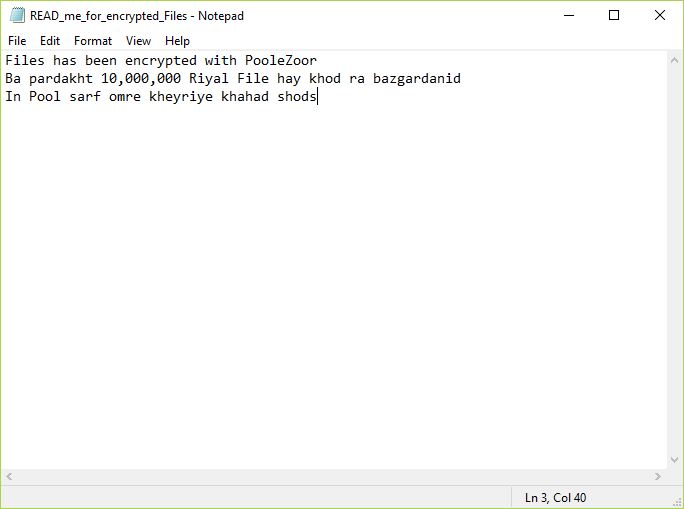
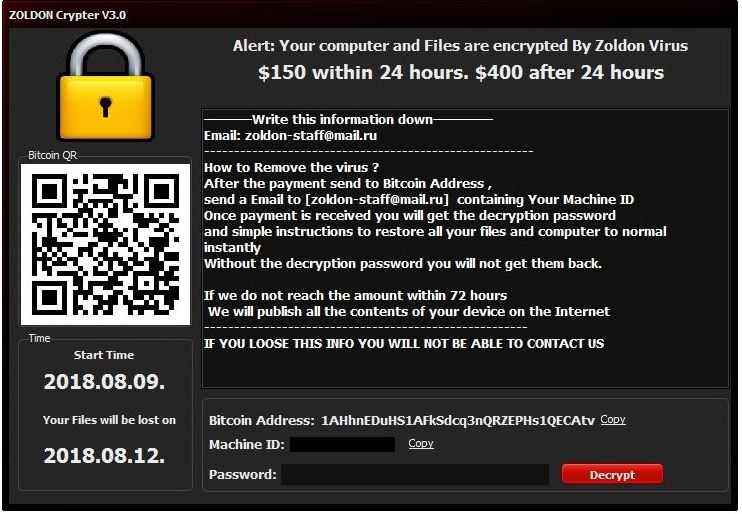
Smartphones Vulnerable to New Form of Attacks Via microSD Cards
Security researchers at CheckPoint have warned about a new danger for our mobile devices, using a vulnerability that goes through the microSD cards. These forms of modified microSD cards can reportedly allow hackers to take over your smartphone by using…