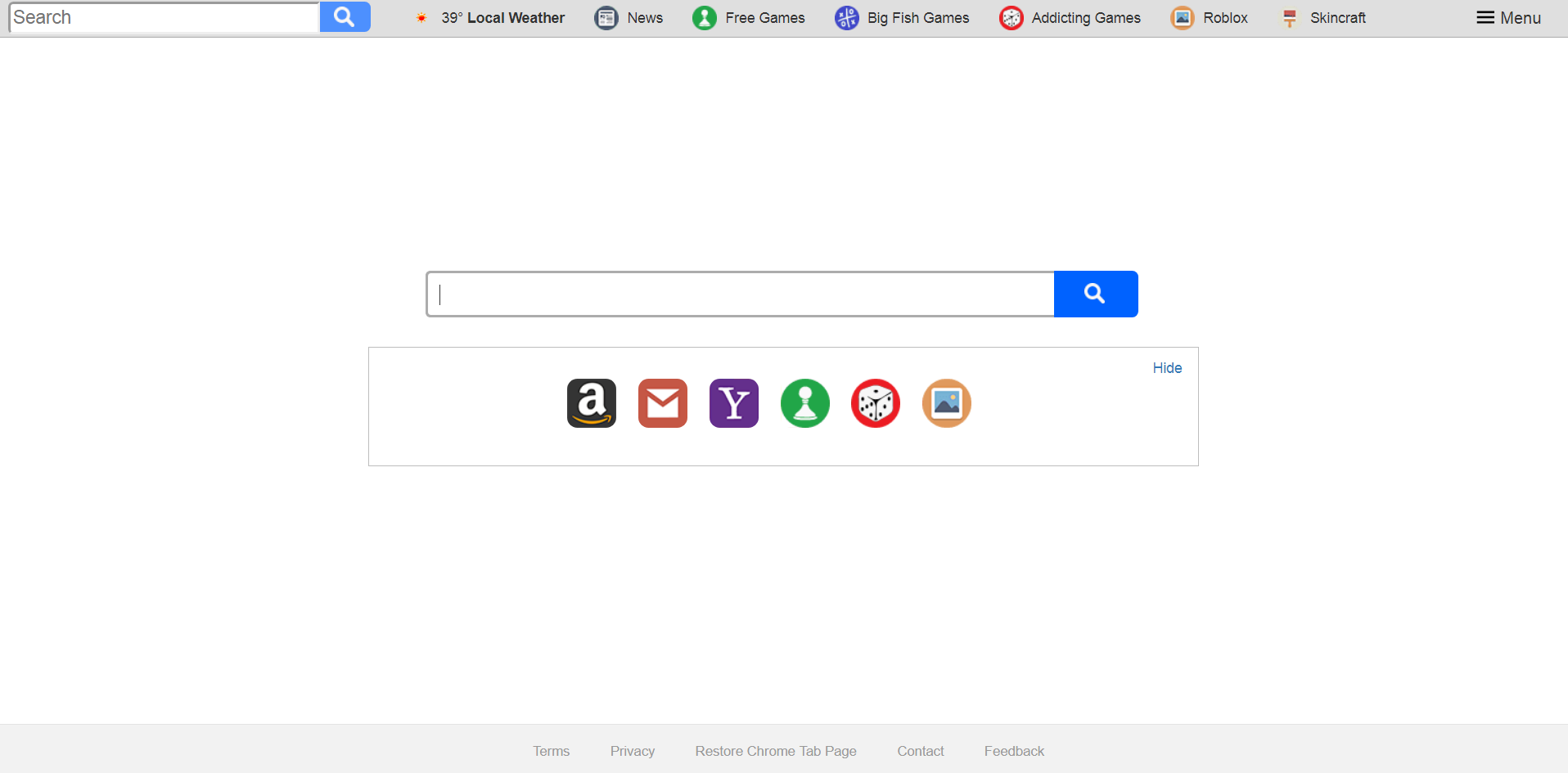
Оkaytab.com Redirect Removal Guide
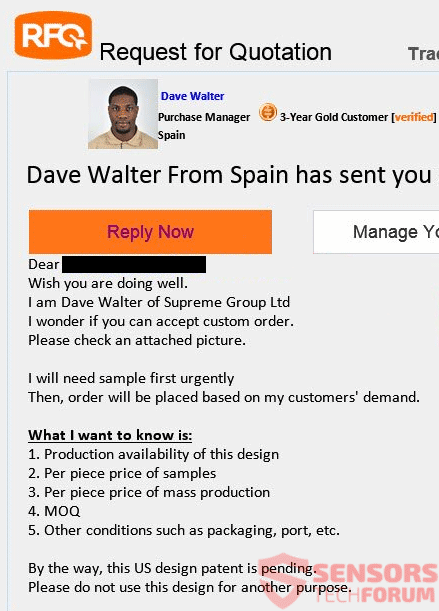
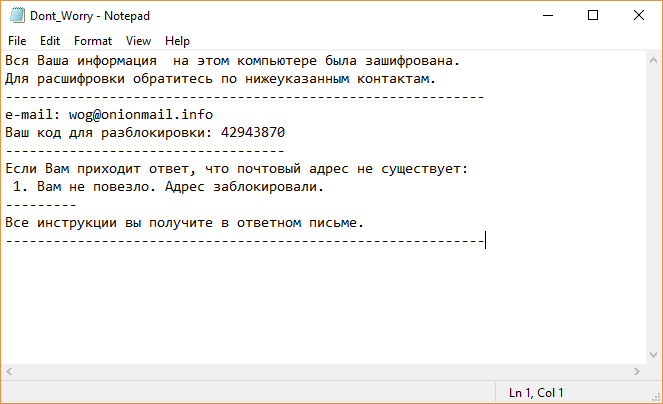
The okaytab.com redirect has been found to infect many users through browser-based addons. It is possible to manipulate them into delivering malware code of different kind. Computer users are also warned of the advanced data gathering which is used to…