.sorry Files Virus (Ransomware) – How to Remove It and Restore Data
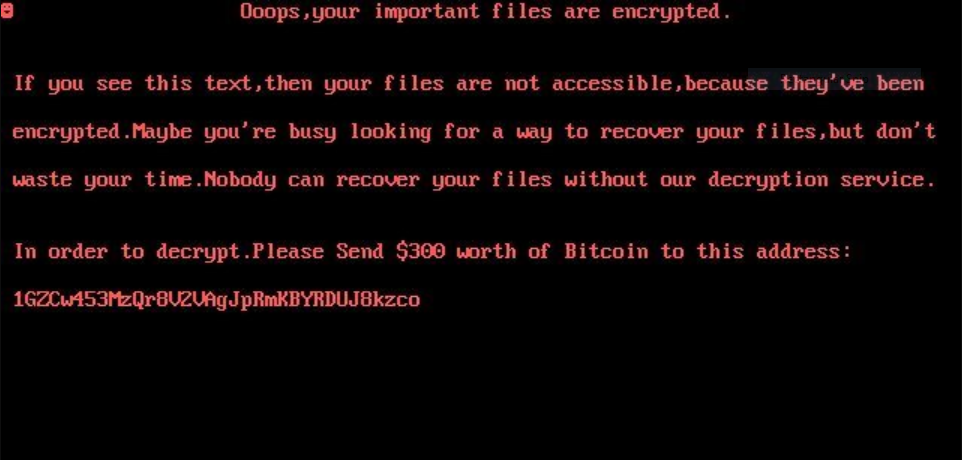
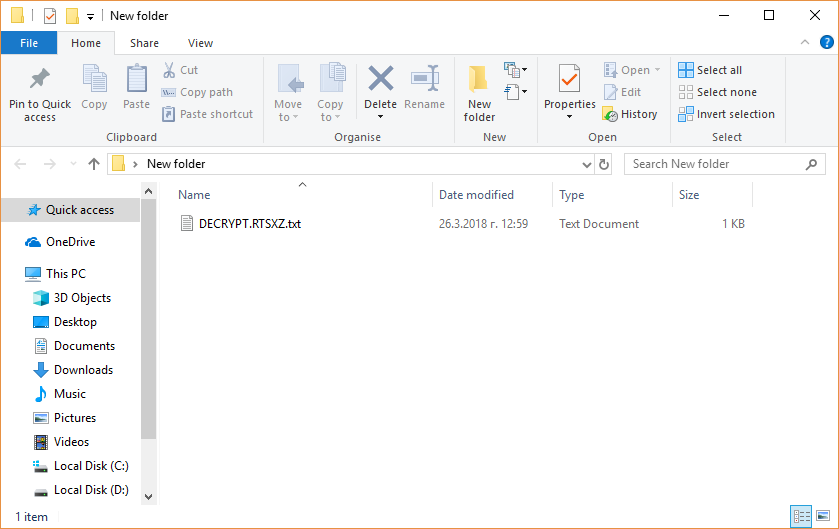
This article has been created in order to help you by explaining what is the .sorry files virus and how to remove this ransomware effectively plus restore data encrypted by it. The .sorry files virus is the type of malware…