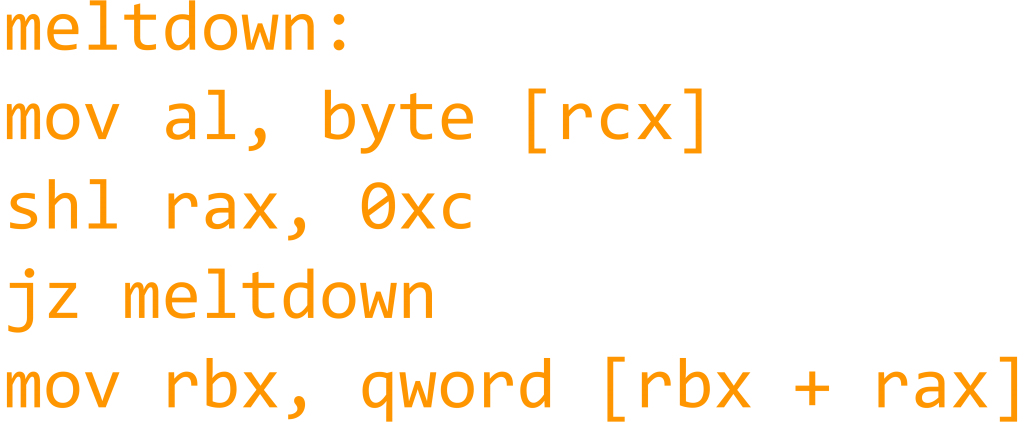
Spoolsv.exe Miner Malware – How to Detect and Remove It
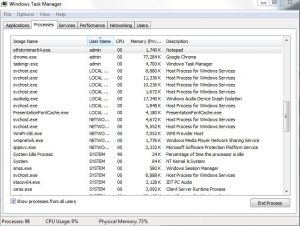
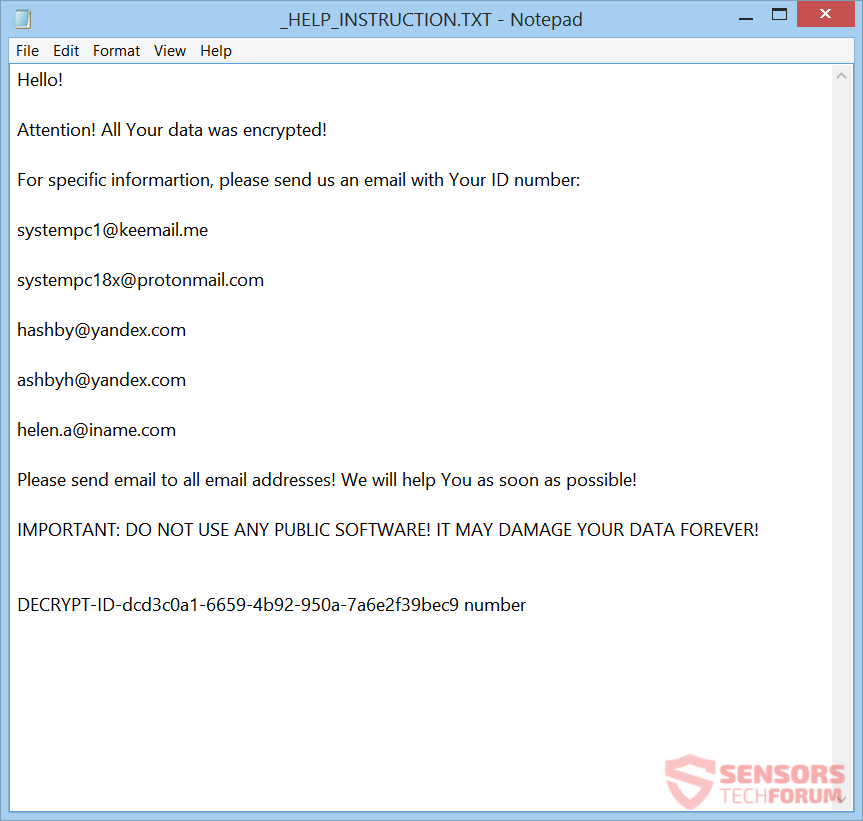
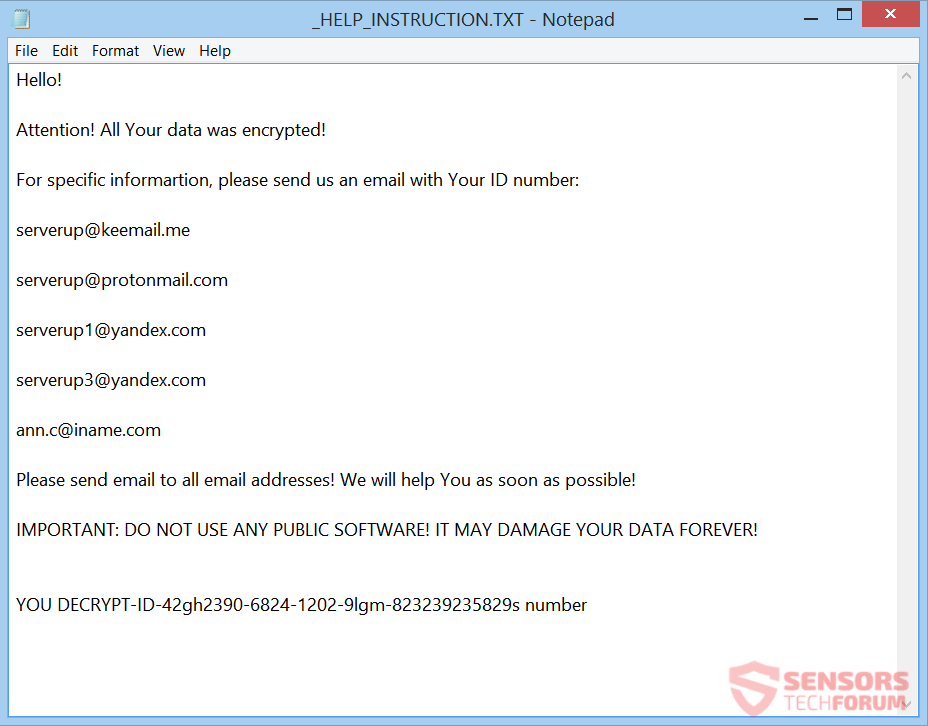
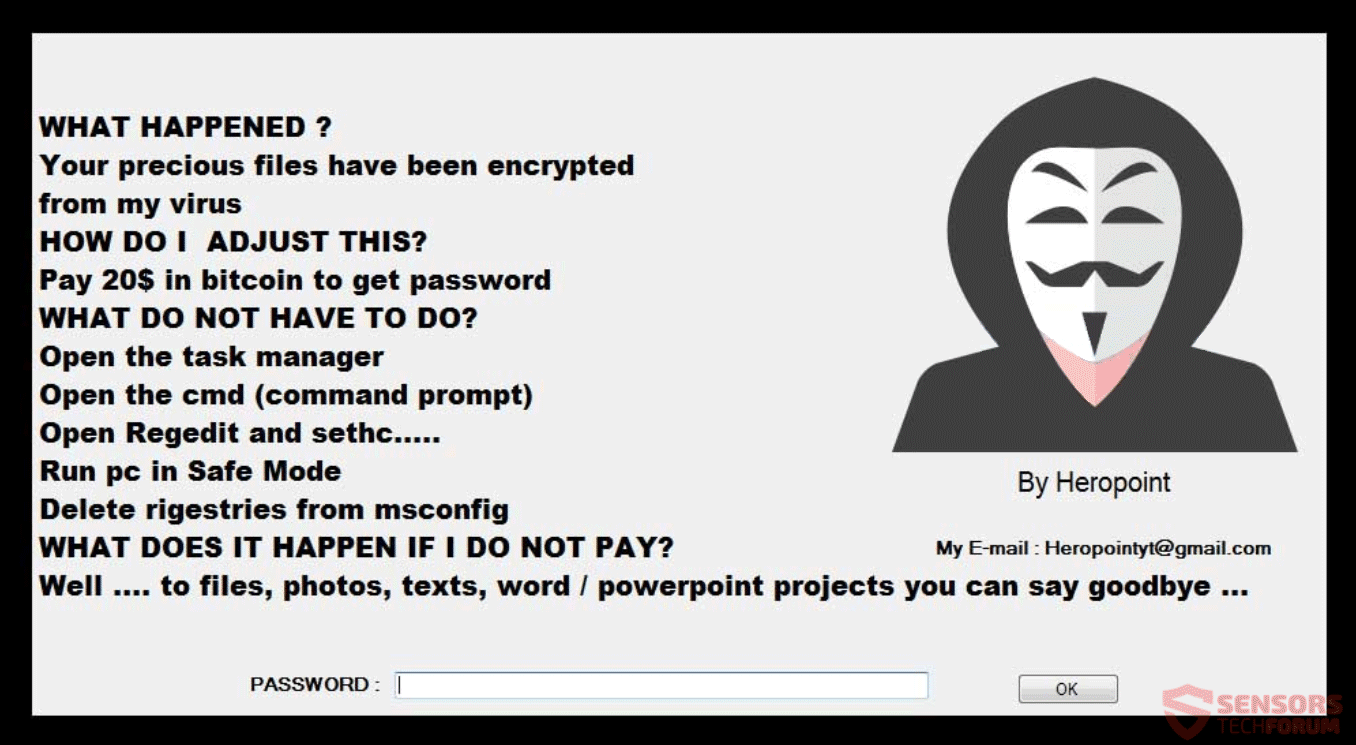
This article has been created in order to help explain what is spoolsv.exe miner malware and how to remove it from your PC. A new miner type of malware has been reported by malware researchers to mask itself behind the…