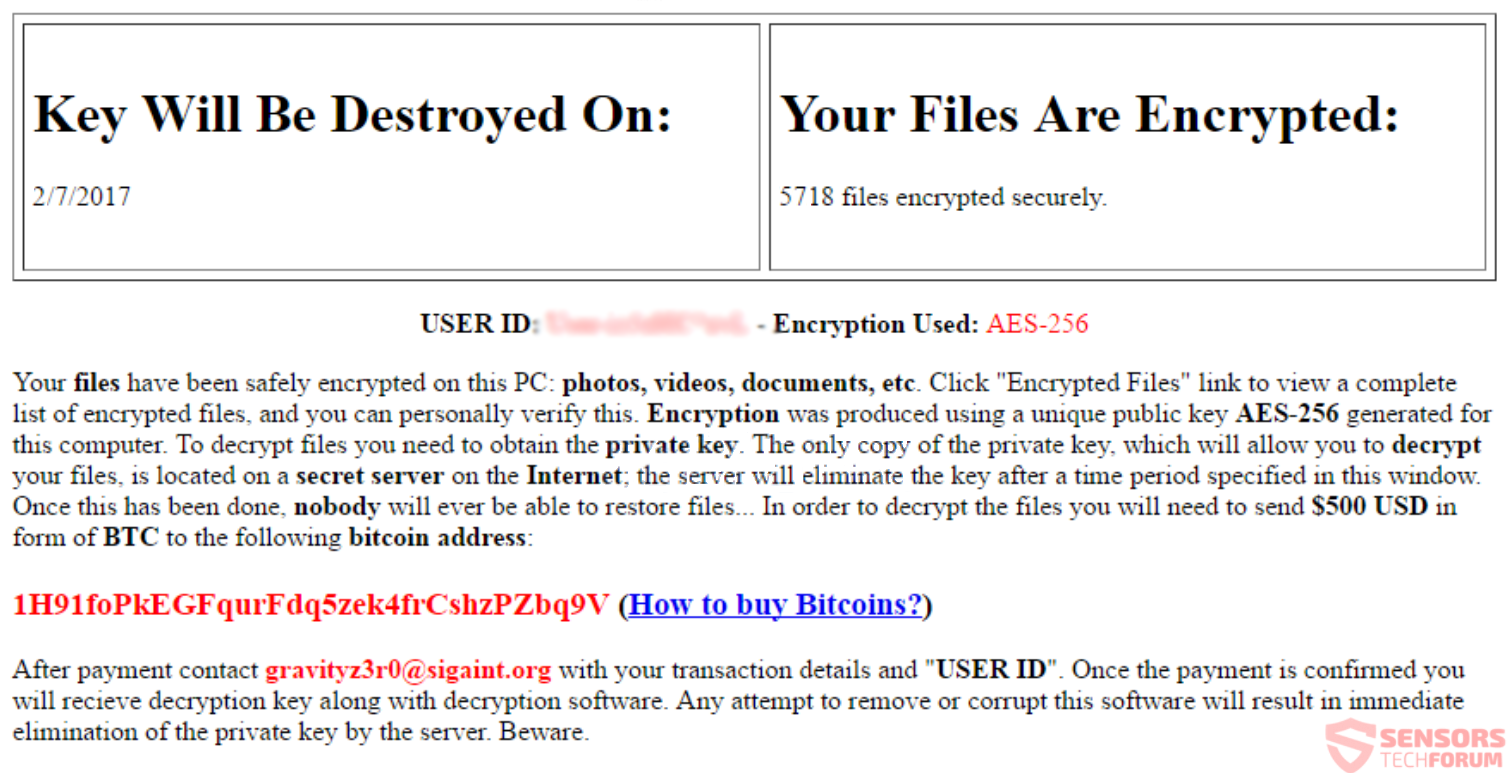
XYZware Ransomware Remove and Restore Files
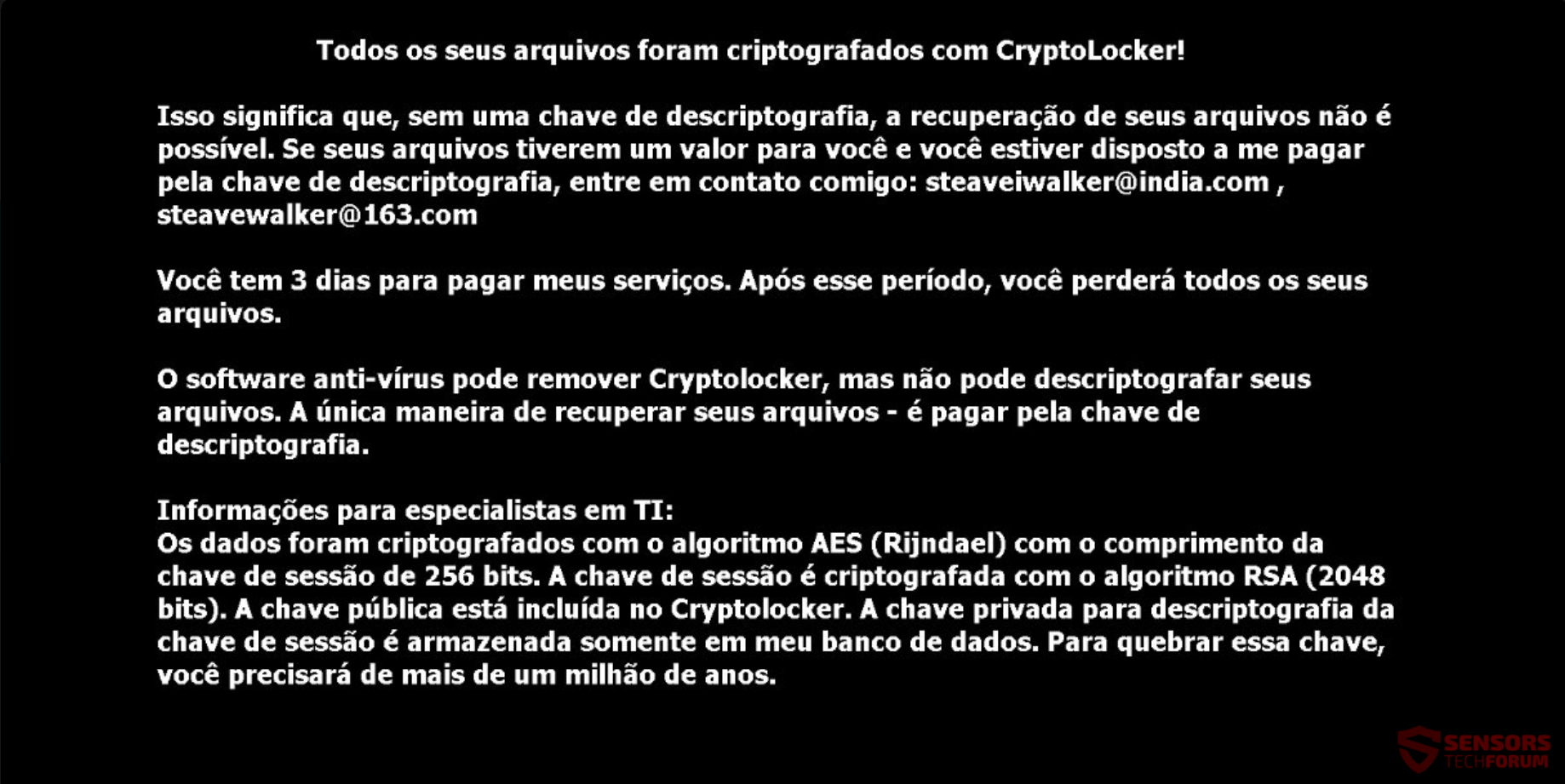
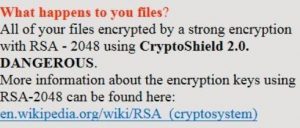
Article created to help you remove XYZware ransomware and restore files that have been encrypted with AES-128 cipher. The ransomware virus, called XYZware has been reported to attack computers all over the world after which encrypt their files using AES-128…



![[KASISKI] File Virus (Restore Files)](https://cdn.sensorstechforum.com/wp-content/uploads/2017/02/ransomware-file-encryption-malware-kasiski-sensorstechforum.jpg)