Since fake e-mails containing malicious attachments are very popular amongst malware authors because of most users infected via this method, we have decided to provide few useful protection tips. These tips will not make you 100% impenetrable against becoming infected, but it will surely block any threats from entering your computer, in case you cannot decide which file is legitimate and which one is malicious.
Since fake e-mails containing malicious attachments are very popular amongst malware authors because of most users infected via this method, we have decided to provide few useful protection tips. These tips will not make you 100% impenetrable against becoming infected, but it will surely block any threats from entering your computer, in case you cannot decide which file is legitimate and which one is malicious.

Why E-mails?
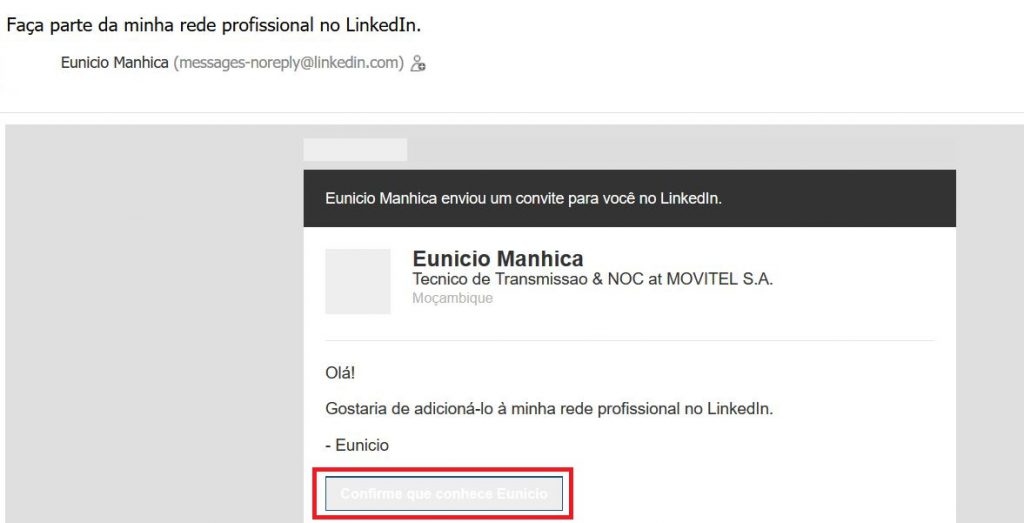
There are many methods to become infected by malware, but the most often met infection cases are caused via e-mail. These types of situations aim to cause infection by sending out false messages accompanied by a malicious attachment. And what is worse is that the cyber-criminals have gotten so good at it, that they even imitate fake buttons, like the below-mentioned fake LinkedIn friend request:
And some e-mails are so sophisticated that solely opening them can inject an embedded In images or other content of the e-mail JavaScript code. This code may directly cause the infection.
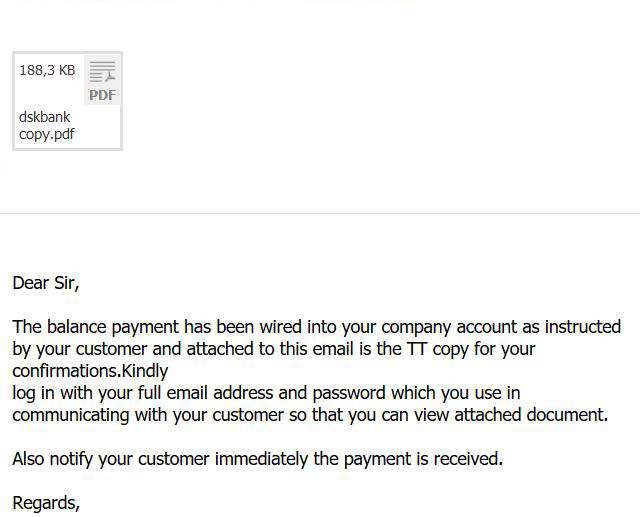
But the most widespread threat remains e-mails with malicious e-mail attachments, asking for users to open them, and pretending to be of an important essence to the user:
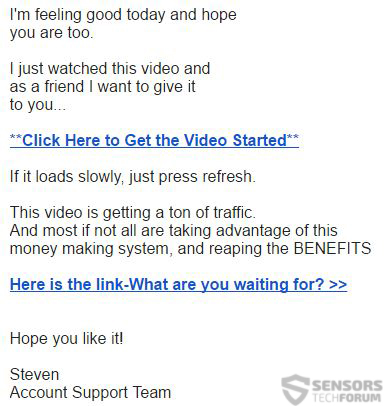
This old-school form of social engineering may trick inexperienced users that they have received an invoice. And it is becoming more and more sophisticated, even by naming users with the name of their e-mail account. We have tested this with a fake e-mail account whose name was called “Good Luck” and the spam which was sent to the g-mail account was the following message:
“Hello Mr. Good Luck
We are hereby notifying you to confirm the following transaction. (see attachment)”
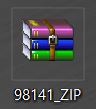
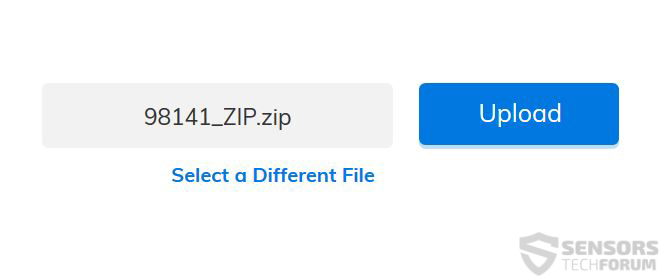
And the attachment was naturally a randomly named .zip file, called 98141_ZIP.zip archive:
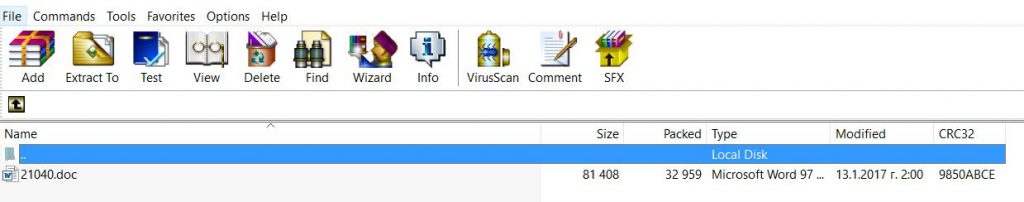
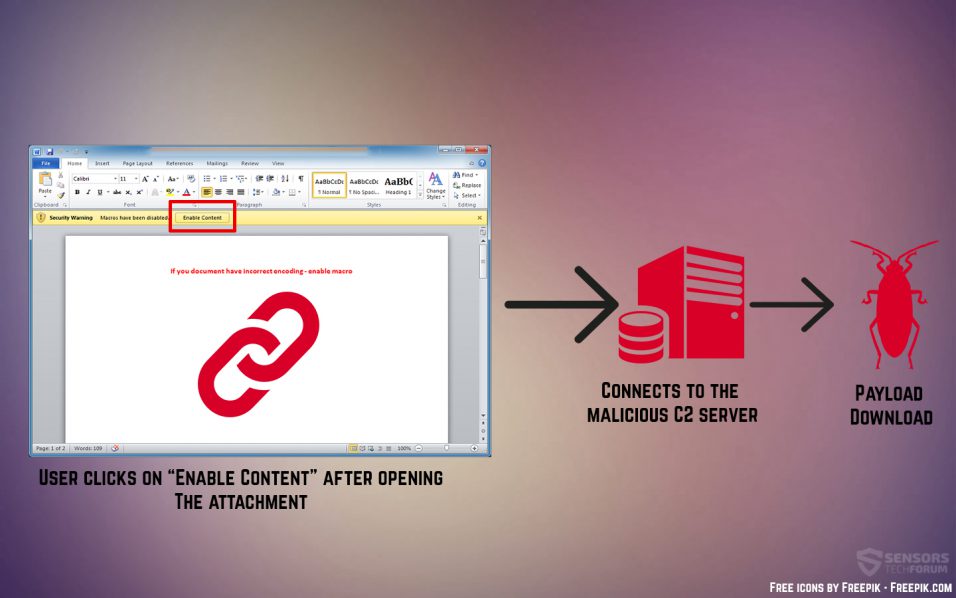
When the malicious .ZIP file is opened, we see the usual .doc Microsoft Word document, which surely has all the first-noticed properties of a completely legitimate word file.
However, when we open this word file, it may be encoded and have a message that will prompt us to enable macros. These very macros may contain the malicious script, which in this case causes an infection with the latest instance of the notorious Cerber Ransomware’s Red 2017 variant. The infection is caused in the following manner:
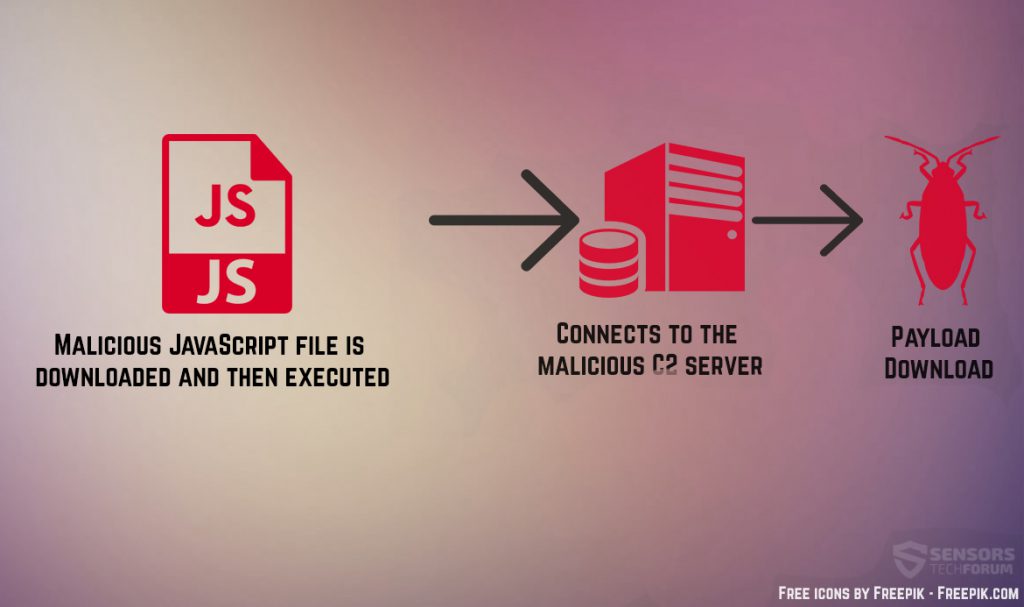
Unfortunately, this is not the only type of case to look for. There is also the situation of using a mallicous JavaScript, VBS or other type of executable file, that may directly cause the infection upon opening, as displayed:
These types of files are also contained in .ZIP or .RAR archives in most cases even double-archived (archive in the archive) to avoid any antivirus detection during the message being sent.

How Do I Protect Myself from Malicious E-mails and Attachments?
Let us assume that you have received a fraudulent e-mail containing the 98141_ZIP.zip archive, which you believe is legitimate, but despite this you feel uncertain on whether this e-mail may contain malware. At this point you may:
- Write back to the one who sent it and ask questions.
- Download and open the file and risk becoming infected with malware.
- Never open the e-mail.
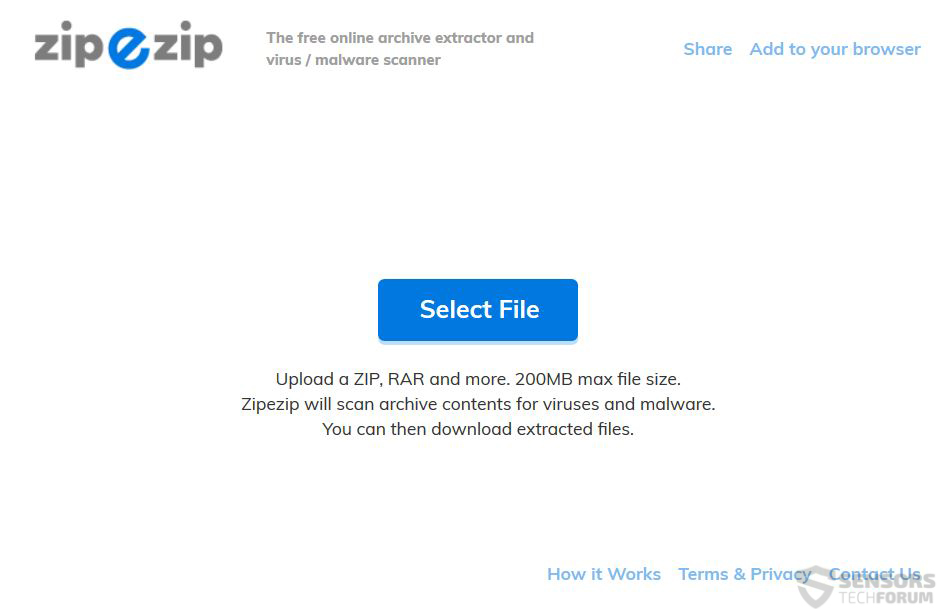
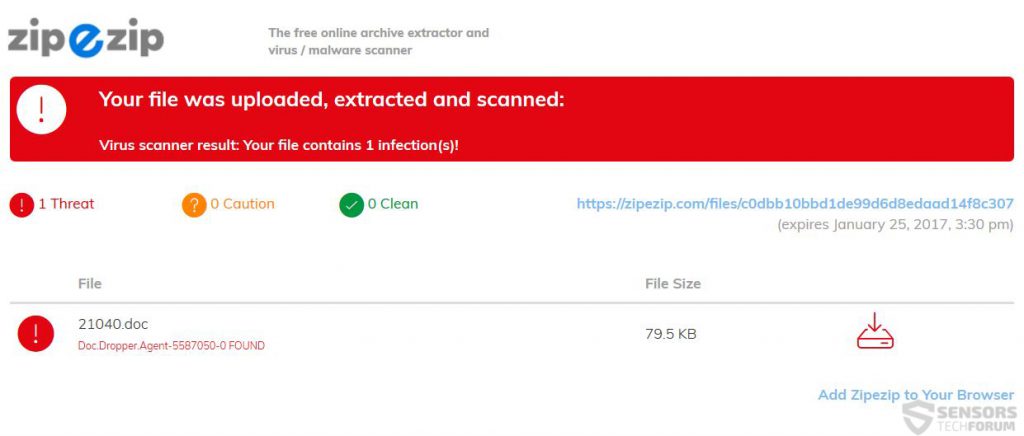
This is not all that you can do, however. There is one more option and that is to download the .zip archive on your computer, without even opening it. Most malicious files contained in archives are harmless if contained within the .zip or .rar archive. This is where you can use the first online scanner for exclusively .ZIP and .RAR archives, called ZipeZip.com. It lets you select a file up to 200 MB and scan it before even having to open the file in question.
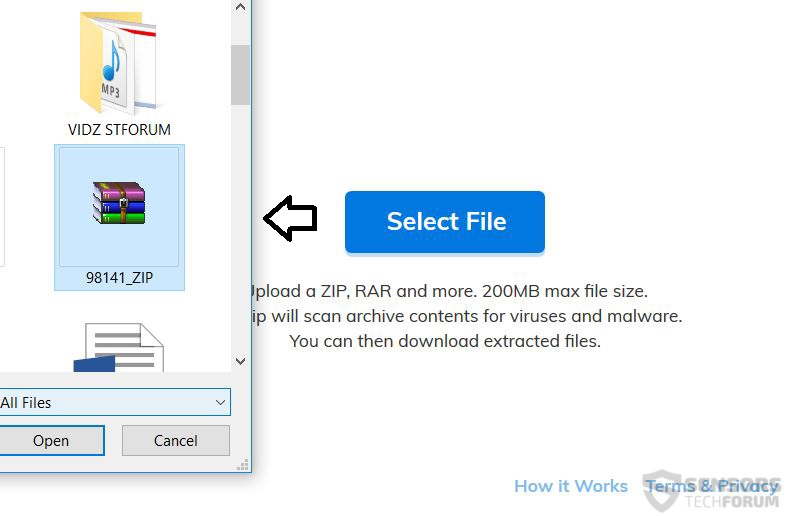
The archive can be scanned by simply clicking on the “Select File” button and then locating it. As soon as the file is selected, it can be quickly uploaded by clicking the “Upload” button.
From there, the system of Zip-E-Zip gets to work, It begins to check its advanced database to detect the malicious files within the .ZIP or .RAR archives. Shortly after uploading the file, you will receive an answer to the question “Is this archive malicious?”:
Then, you can safely decide what to do with the malicious e-mail. You can send it to malware researchers for analysis or just delete it.

What If There Is a Malicious Web Link on The E-mail?
Some e-mails, besides sending out malicious files, also contain malicious web links. They are usually blocked by e-mail providers, but some, more sophisticated and highly obfuscated, tend to pass successfully.
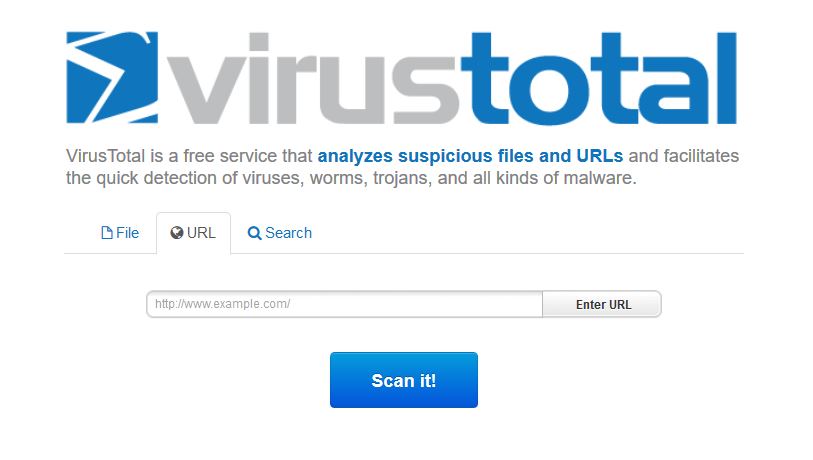
In case you are not sure whether or not the URL is malicious, you can simply open VirusTotal’s website, after which paste the site and click on the “Scan It” button. This will allow you to see if the web link can infect you with malware or if it’s a phishing(fake) one that aims to get you to enter your password and username on a copycat web-page:
VTChromizer Web Link Checker for Chrome
Unfortunately, the extensions are available only for Google Chrome, but soon they may be available for other browsers as well.

Other Important Protection Advises
Besides knowing how to properly check something before actually opening it and becoming infected, we advise you to make sure you combine what you know with the following important techniques, as mentioned by XSolutions:
1. Use spam filtering software to open your e-mails with more protection. Usually, external e-mail programs like Microsoft Outlook and Mozilla Thunderbird have spam filters, but you can find many others as well.
2. Download and install an advanced anti-malware program and make sure it is always updated so that it can stop malware and other unwanted software from causing the inevitable.
3. For public use, when you register on a site to visit it once or just to check something, use a disposable e-mail that is not your personal and important e-mail address.
4. If you receive an e-mail you believe is suspicious, do not even click on the “Unsubscribe” web link before scanning it. Malware writers aim to embed their scripts on every URL and button they hotlink.
5. Regularly clean up your Junk folder and also delete messages permanently so that they can no longer be restored.
6. Setting the e-mail account to create messages to appear in simple text instead of showing any media within it.
7. Learn how to safely store your data, even if you become infected with malware.
The Bottom Line
The instructions and information provided in this article are no full guarantee that any malware will be stopped because these by far aren’t the only method of replicating malware. The cyber-criminals sometimes target networks, using worms and other viruses to cause an infection automatically. But these tools will surely help you avoid the unpleasant after-effect of opening a malicious e-mail attachment.