 Cyber microscope may sound like something from the future but it is indeed reality. It is a tool developed and introduced by Lewis Rhodes Labs. Essentially, LRL Cyber Microscope provides advanced security anomaly detection, and is a quite interesting piece of work. Tools of this sort definitely serve to outline cyber security’s prospects.
Cyber microscope may sound like something from the future but it is indeed reality. It is a tool developed and introduced by Lewis Rhodes Labs. Essentially, LRL Cyber Microscope provides advanced security anomaly detection, and is a quite interesting piece of work. Tools of this sort definitely serve to outline cyber security’s prospects.
The microscope is based upon a Cyber Optimized Neuromorphic Processor, which increases the speed and resolution of detection by more than 100 times (via HelpNet Security). The utility can also be described as a revolutionary processing unit that literally mimics the human brain and the way it processes pieces of information.
As pointed out by the utility’s creator, cyber defense is a three-stage process:
First, intrusion detection systems, (IDS), monitor network and system activity for malicious events. IDSs use hardware and software sensors to execute security policies describing these events to generate alerts. Second, the alerts are consolidated into a security management system. Finally, highly trained security analysts evaluate the alerts using experience and a variety of analytic tools to identify and neutralize treats.
Knowing how cyber defense works and what it lacks, the team at Lewis Rhodes Labs decided to create a device that would run far ahead of regular defense mechanisms.
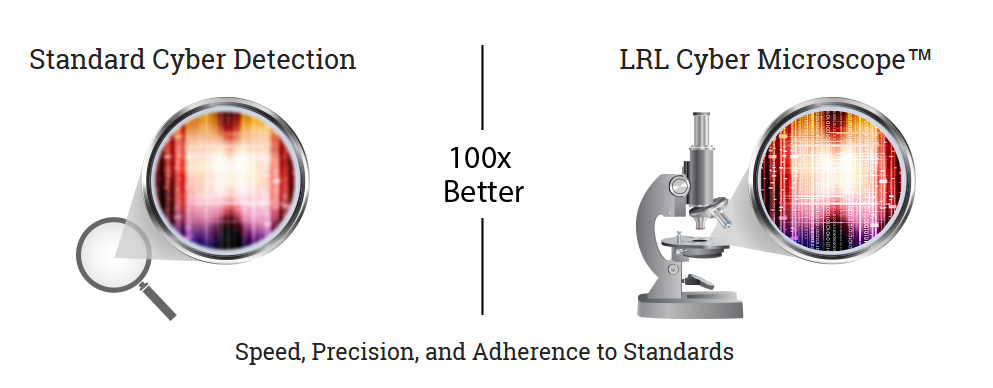
Image Source: Lewis Rhodes Labs
LRL’s Cyber Microscope consists of a PCI-e (Peripheral Component Interconnect Express, a high-speed serial computer expansion bus standard) compatible interface card, driver and PCRE (Perl Compatible Regular Expressions) compiler which is integrated into Suricata and similar intrusion detection systems.
What do security experts say about the microscope?
In addition, the cyber microscope has been applied to the cyber development environment at Sandia National Laboratories. John Zepper, Director of Systems Mission Engineering at the Labs believes that:
The improved speed and accuracy of the LRL Cyber Microscope should allow us to reduce the False Positive rate in our alert database, and we are collaboratively researching methods to use the temporal nature of the Neuromorphic processor to detect novel behavioral variants.
Sean Pike, Program Director, Next-Generation Data Security and eDiscovery & Information Governance at IDC says:
The process of extracting real threats from the typically high number of scanned anomalies is a never-ending challenge for security analysts using any intrusion detection system. Analysts need a cost-effective threat detection solution that provides them with the speed and accuracy to dramatically improve resolution and performance, and ultimately recognize real issues.
Intrigued? More information about the very first cyber microscope is available on Lewis Rhodes Labs official page.


