Stealing from Ransomware Operators and Ransomware Victims? Mission Possible, Says Onion.to Tor-to-web Proxy Service
Security researchers at Proofpoint have reported that the operators of a Tor proxy service were detected replacing Bitcoin addresses on ransomware payment websites. This means that ransomware payments sent by victims in exchange for decryption keys were diverted towards the address of… other cybercriminals.
What is a Tor proxy service? A website designed to enable users to access .onion domains, which is hosted on Tor network. The service can be used without the Tor browser. These services have been growing in popularity, especially when it comes to ransomware. Many ransomware pieces implement URLs for Tor-to-web proxies in addition to the original payment portal. These proxies come in handy for users that lack technical capabilities.
Tor proxies are simple to use. Users typically add an extension such as .to, .cab to in the onion URL, and it becomes usable in a normal browser. For example, in order to use hxxps://robusttldkxiuqc6[.]onion/, users need a dedicated Tor browser. However, they can use hxxps://robusttldkxiuqc6[.]onion[.]to/ in any browser.
Proofpoint researchers, however, came across something intriguing – Tor proxies designed to steal simultaneously from ransomware authors (or operators) and their victims. The case involves the operators of Onion.top Tor-to-web proxy service who were covertly analyzing Dark Web pages loaded through their portal for strings that resemble Bitcoin wallet addresses typical for ransomware. These addresses were then changed with their own. Three ransomware families seem to be affected by this curious scheme – LockeR, Sigma and GlobeImposter.
How Did Researchers Become Aware of This Practice?
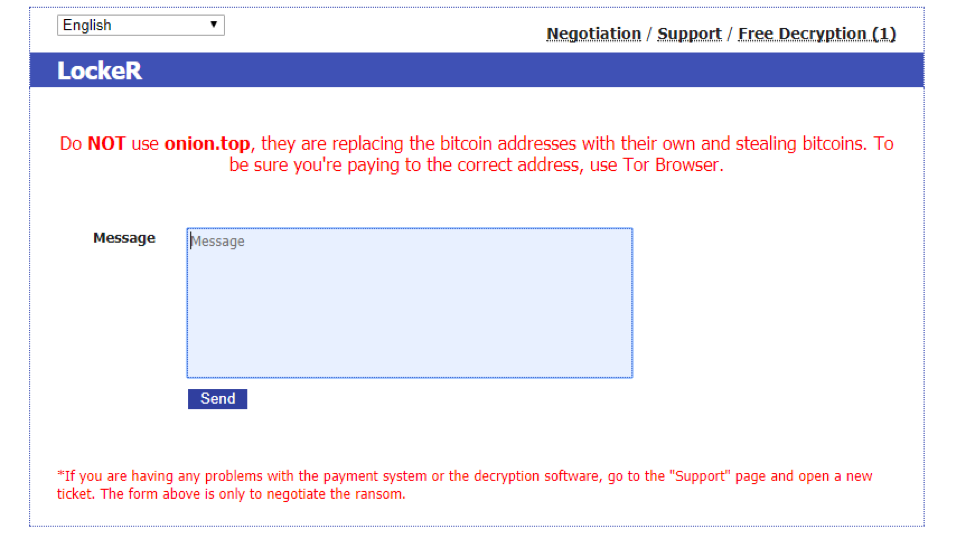
Thanks to a warning visible on the LockeR payment site which was posted by the ransomware’s authors. This is what the message reads:
Do NOT use onion.top, they are replacing the bitcoin address with their own and stealing bitcoins. To be sure you’re paying to the correct address, use Tor Browser.
The Onion.to Tor-to-web proxy service successfully harvested $22,000 both from ransomware authors and their victims.
During their research, the experts noticed various Bitcoin wallet address replacement rules based on the page accessed by the user. This led them to suggest that Onion.to operators were configuring the address changes manually, site by site.
The researchers examined the replacement Bitcoin addresses to determine how much may have been stolen by the proxy operators:
The Bitcoin address 13YFjj7WqWY5Un7Pgw1VdrpceHpn5BTZdp has had a total of 0.15 BTC transferred to it ($1,661 at the time of publication – see Figure 6). The Bitcoin address 1Q64uWnKMUoZ6G7BSrH77xdrewMou2zGpU has had a total of 1.82 BTC transferred to it ($20,154 at the time of publication).
However, it is not clear whether other Bitcoin addresses are being used in this scheme.
In conclusion…
While it appears that operators of onion.top have not stolen a large number of Bitcoins from ransomware victims yet, as many ransomware victims use Tor proxies instead of installing the Tor browser, the potential impact is high for victims attempting to pay the ransom and decrypt their files, researchers say. Nonetheless, the scheme highlights the dubious relationships in the ransomware business, as it raises an interesting business problem for ransomware authors and practical issues for their victims by further increasing the risk to victims who would decide to pay the demanded ransoms. This scheme also sheds a light on another increasingly popular trend – the theft of cryptocurrencies.
Continued volatility in cryptocurrency markets and increasing interest in the Tor network will likely drive further potential abuses of Tor proxies, creating additional risks for new users, Proofpoint researchers concluded.