Imagine downloading an app for your Android phone, expecting it to improve your device’s security, only to find out it does precisely the opposite.
Enter BingoMod, a type of malware known as a Remote Access Trojan (RAT) that turns your smartphone into a puppet for cybercriminals, allowing them to steal your financial information and even wipe your device clean, leaving no trace behind.

BingoMod RAT Summary
| Name | BingoMod RAT |
| Type | Android RAT / Malware |
| Short Description | A cunning piece of malware that masquerades as a legitimate app. |
| Symptoms | Data theft and financial loss. |
| Distribution Method | Via fake third-party apps or adverts. |
What Is BingoMod RAT and How Does It Affect Your Android Phone?
Imagine downloading what you think is a helpful app for your Android phone, only for it to turn against you. This is the reality with BingoMod, recently discovered and analyzed by Cleafy researchers.
Unlike regular apps, which provide you with services or entertainment, RATs like BingoMod are designed with a malevolent purpose. They give cybercriminals the ability to control your device remotely without your consent. But BingoMod doesn’t stop at mere control; it goes a step further by engaging in financial theft directly from your phone.
One of the key dangers of BingoMod is how it masquerades as legitimate security software. It tricks users into downloading it, promising to enhance their device’s protection. Yet, once installed, it does the opposite by stealing sensitive information such as login credentials and bank account details.
This can lead to unauthorized money transfers, leaving victims financially hurt and possibly leading to the loss of personal and financial data. To make matters worse, after completing its deceitful activities, BingoMod can wipe the victim’s device, erasing any evidence of its presence and making recovery efforts extremely difficult.
The Mechanics Behind BingoMod: From Infection to Financial Theft
The journey from infection to financial theft with BingoMod is both sophisticated and stealthy. Initially, the malware typically enters through a technique known as smishing – sending text messages with malicious links.
When the user is misled into installing the app, thinking it’s a legitimate security tool, BingoMod first asks for Accessibility Services permissions. This is a devious move, as these permissions are incredibly powerful, giving the malware a variety of capabilities to monitor and control the device.
- After gaining the necessary permissions, BingoMod unpacks and executes its malicious payload. This sets the stage for the malware to begin its true purpose: financial theft.
- Through keylogging and SMS interception, it captures sensitive information such as bank login details and transaction numbers.
- BingoMod then establishes a remote connection, allowing it to receive further malicious commands and perform actions directly on the device – this includes initiating unauthorized money transfers.
- Finally, to cover its tracks, BingoMod can wipe the device clean after the fraudulent activities, making detection and recovery by the victim or authorities much harder.
Why Is BingoMod Particularly Dangerous for Android Users?
BingoMod has emerged as a formidable threat to Android users, distinguishing itself from other Android malware because of its unique capabilities and impact. Unlike many forms of malware that primarily focus on ad fraud or data theft, BingoMod introduces a terrifying twist to the mobile security landscape.
It skillfully combines the ability to steal sensitive financial information with a self-destruct mechanism that wipes devices post-operation, leaving victims with no trace of the culprit or means to recover stolen funds. This multi-pronged approach not only facilitates financial theft but also severely disrupts the lives of its victims by erasing personal data, photos, contacts, and more.
The complexity of BingoMod lies in its exploitation of the On Device Fraud (ODF) technique, which allows it to bypass multifactor authentication and behavioral analysis by banks. By leveraging permissions such as Accessibility Services, BingoMod can perform unauthorized transactions without the user’s knowledge. Its capability to execute overlay attacks and emulate user interactions through VNC-like functions makes it particularly elusive and challenging to detect.
What sets BingoMod further apart is its development strategy. Its creators continuously test and employ obfuscation techniques, making it harder for antivirus solutions to detect and neutralize. This evolving nature indicates a strategic effort to stay ahead of security measures, posing a persistent threat to Android users.
Beyond its technical capabilities, BingoMod’s selective targeting of devices using English, Romanian, and Italian languages suggests a calculated approach to victim selection. This strategic choice of targets amplifies its danger, showing that the actors behind BingoMod are not just randomly deploying their malware; they are targeting specific demographics, potentially based on the perceived ability to profit.
Comparing BingoMod to Other Android Malware: A Disturbing Trend
When compared to other Android malware, BingoMod highlights a disturbing trend in mobile threats: the shift towards more sophisticated and financially damaging operations. Traditional Android malware often aims at stealing data, pushing unwanted advertisements, or enlisting devices in botnets. However, BingoMod signifies a shift towards complex fraud schemes that directly attack financial assets and leverage sophisticated techniques to evade detection.
Previous banking Trojans like Anubis, Bankbot, and Cerberus were known for their capabilities to intercept SMS for two-factor authentication codes and employ overlay attacks. BingoMod, however, takes these threats a step further by incorporating direct device control, enabling real-time fraud without interaction from the victim. This capability, combined with the self-wipe feature to erase evidence, makes BingoMod a more severe threat that not only aims to steal but also to leave its victims with limited means of recourse.
The evolution from simple data theft to direct financial fraud via ODF and the use of self-destructive tactics marks a significant escalation in the threat landscape. BingoMod’s approach of disguising itself as a legitimate security application further demonstrates the cunning strategies employed by its developers to prey on unsuspecting users. This tactic of masquerading as a protective tool while performing malicious actions underlines the sophistication and deceitful methods being adopted in modern malware campaigns.
In conclusion, BingoMod represents a notable advancement in Android malware with its focus on financial theft, evasion of bank security measures, and self-destruction to avoid detection. Its existence and development underscore the need for Android users to be exceedingly vigilant about the apps they install and to utilize comprehensive security solutions.
Can BingoMod RAT Really Wipe Your Device After Stealing Your Money?
When it comes to the capabilities of modern Android malware, BingoMod Remote Administration Tool (RAT) presents a frighteningly efficient combination of financial theft and device sabotage. This new malware variant doesn’t just stop at pilfering funds from your bank account – it goes a step further by erasing vital data on your device. How does it manage this feat, and what makes it so dangerous? Let’s delve into the functionalities that enable BingoMod to not only act as a financial predator but also as a digital arsonist, leaving no trace of its activities behind.
Understanding the Data Wiping Functionality of BingoMod RAT
BingoMod embodies a sinister dual-threat, not limited to financial theft. After successfully raiding a victim’s bank account, BingoMod activates a data wipe feature. This unique self-destruct sequence is designed to perform a comprehensive clean-up, removing any evidence of its presence and activities, complicating forensic efforts and analysis. This level of sophistication suggests a calculated intention to elude capture and accountability by the creators.
Key aspects of BingoMod’s data-wiping ability include:
- Device Administrator Rights: Initially, for BingoMod to exercise its data-wiping capability, it must obtain device administrator privileges. Once granted, it gains extensive access to device features and settings, enabling it to execute the wipe command effectively.
- Remote Execution: The wiping process can be initiated remotely. This allows the perpetrators behind BingoMod to order a device clean-up from anywhere, ensuring that once the fraudulent activities are completed, they can erase their tracks with a simple command.
- Limited to External Storage: Current observations suggest that the wipe focuses on the device’s external storage, where personal data such as photos, videos, and documents are often stored. This selective wiping safeguards the malware’s stealthiness by not arousing suspicion with a full device reset, which might be more noticeable to the user.
- Overlay Attacks and Advanced Techniques: BingoMod capitalizes on sophisticated methodologies, like overlay attacks, to capture banking credentials without detection. These techniques, combined with the RAT’s data-wiping feature, make it a potent tool for financial fraud and digital obliteration.
How to Detect and Remove BingoMod Malware from Your Android Device
Discovering the presence of BingoMod malware on your Android device and taking swift action to remove it can help protect your precious data and financial assets. This guide brings you a straightforward approach to deal with this malicious software effectively.
Step-by-Step Guide to Safeguard Your Device Against BingoMod RAT
- Check for Unusual Behavior: Begin by observing any unfamiliar activities on your device. This may include sudden drops in performance, unexpected app crashes, or unusual charges to your bank account linked to your mobile device.
- Use Safe Mode: Restart your Android device in ‘Safe Mode’. This allows your device to operate with the minimal necessary processes and can help identify rogue apps since in Safe Mode, most third-party apps won’t run.
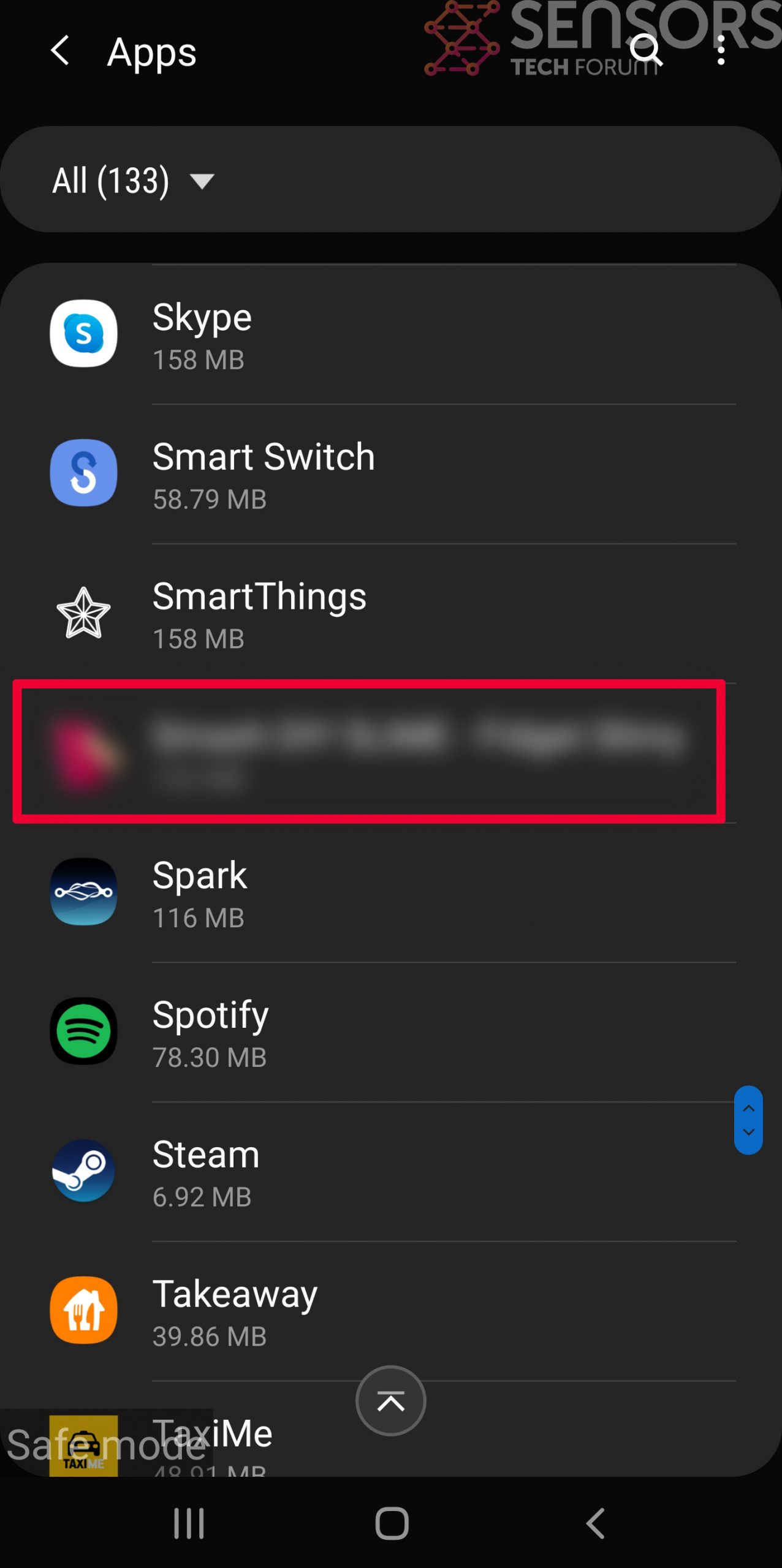
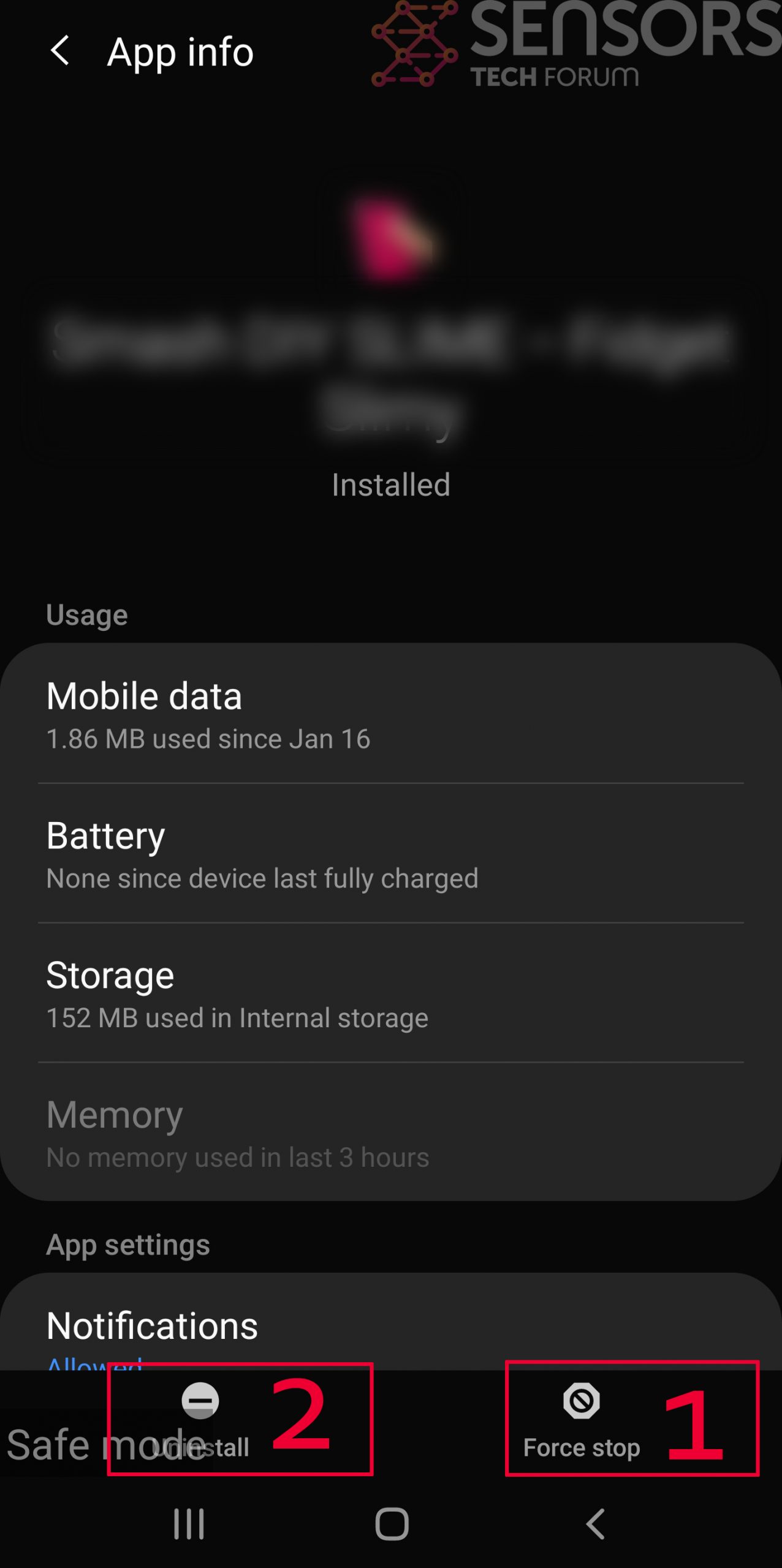
- Locate and Remove Suspicious Apps: In Safe Mode, go to ‘Settings’ > ‘Apps’ and scroll through the list to find and uninstall any suspicious applications that you don’t remember installing or that don’t seem to belong.
- Run a Security Scan: Use a reputable antivirus app to scan your device for malware. If any threats are detected, follow the provided instructions to address them.
- Factory Reset: If the malware persists, performing a factory reset may be necessary. Back up important data first, as this will erase all data from your device.
- Reinstall Apps from Trusted Sources: After resetting, reinstall applications only from the official Google Play Store to avoid reintroducing malware.
Conclusion
While many antivirus apps offer protection against a variety of threats, BingoMod employs obfuscation and device wiping techniques that can evade standard detection methods. Its ability to mimic legitimate applications and misuse device administrator permissions makes it a tough adversary for regular antivirus solutions.
In conclusion, the battle against mobile malware is ongoing, and staying protected requires both awareness and action. By understanding the risks, exercising caution, and utilizing effective security tools, users can significantly mitigate the threat posed by malicious software. It’s not merely about defending against current threats but also about preparing for future challenges in the ever-evolving cybersecurity landscape.
Preparation before removal of malware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Turn off your phone until you know how bad is the virus infection.
- Open these steps on another, safe device.
- Make sure to take out your SIM card, as the virus could corrupt it in some rare cases.
Step 1: Shut Down your phone to win some time
Shutting down your phone can be done by pressing and holding its power button and choosing shut down.
In case the virus does not let you do this, you can also try to remove the battery.
In case your battery is non-removable, you can try to drain it as fast as possible if you still have control over it.
Notes: This gives you time to see how bad the situation is and to be able to take out your SIM card safely, without the numbers in it to be erased. If the virus is on your computer, it is espeically dangerous to keep the sim card there.
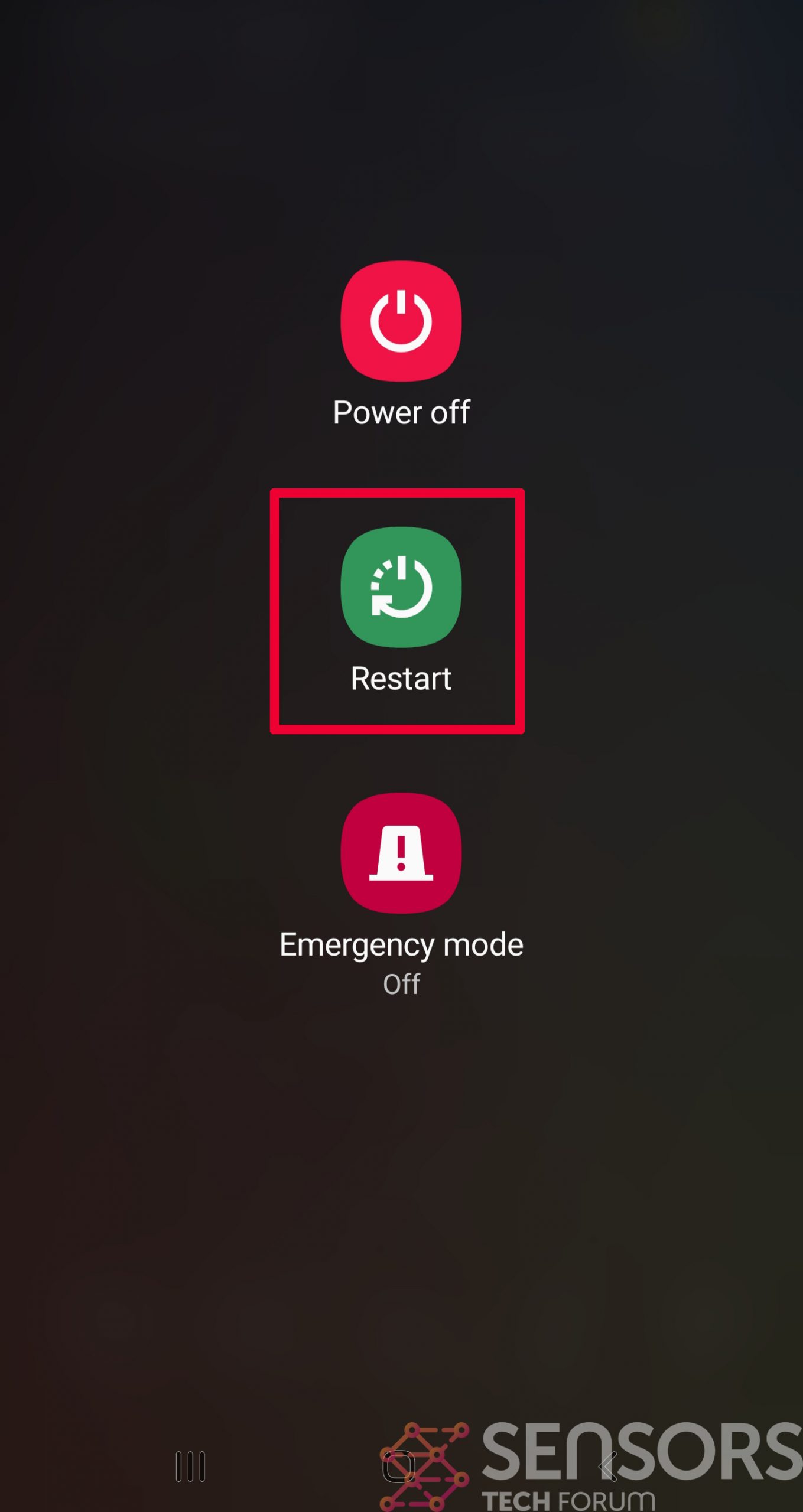
Step 2: Turn on Safe Mode of your Android device.
For most Android devices, switching to Safe Mode is the same. Its done by following these mini-steps:
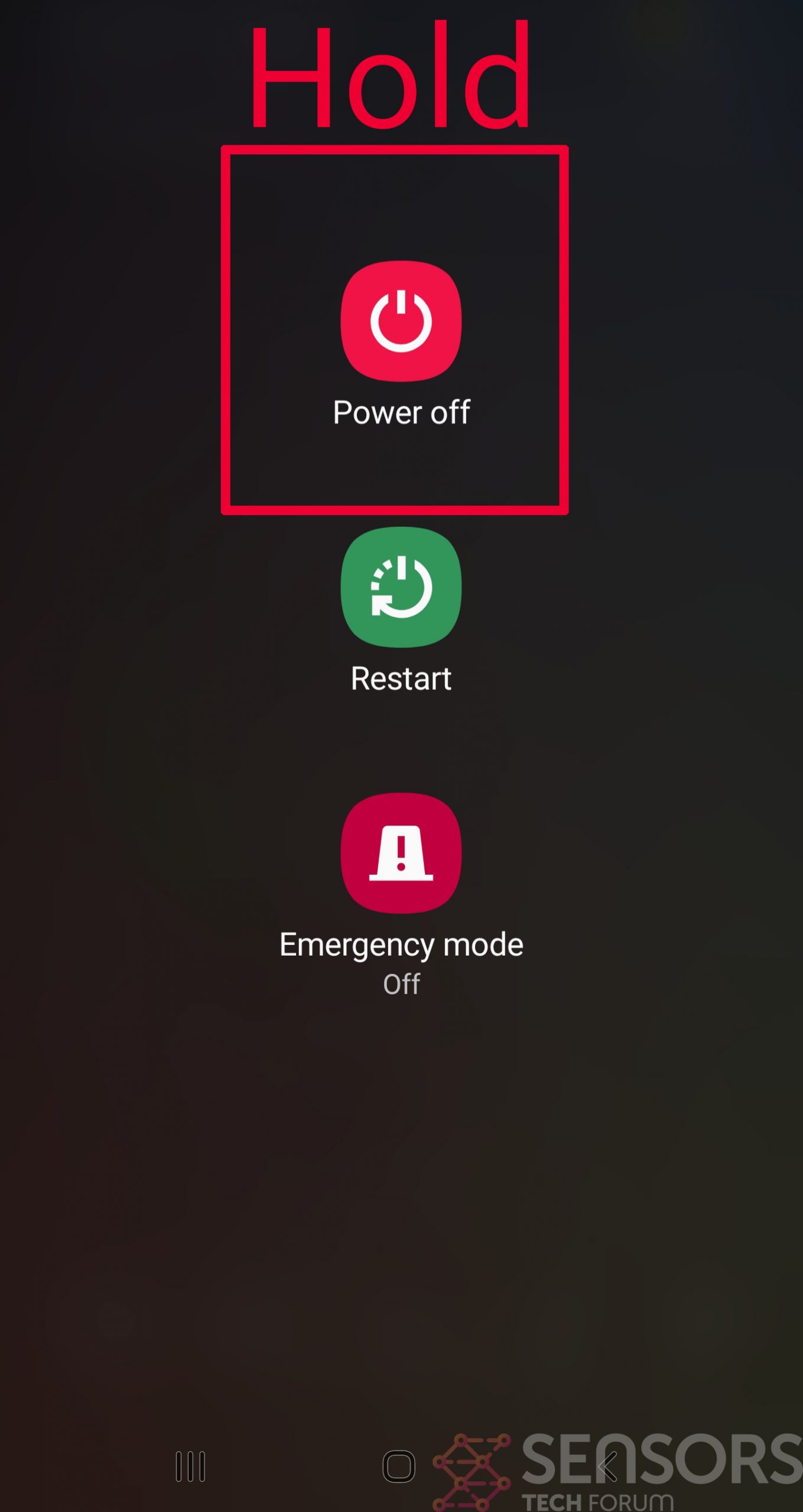
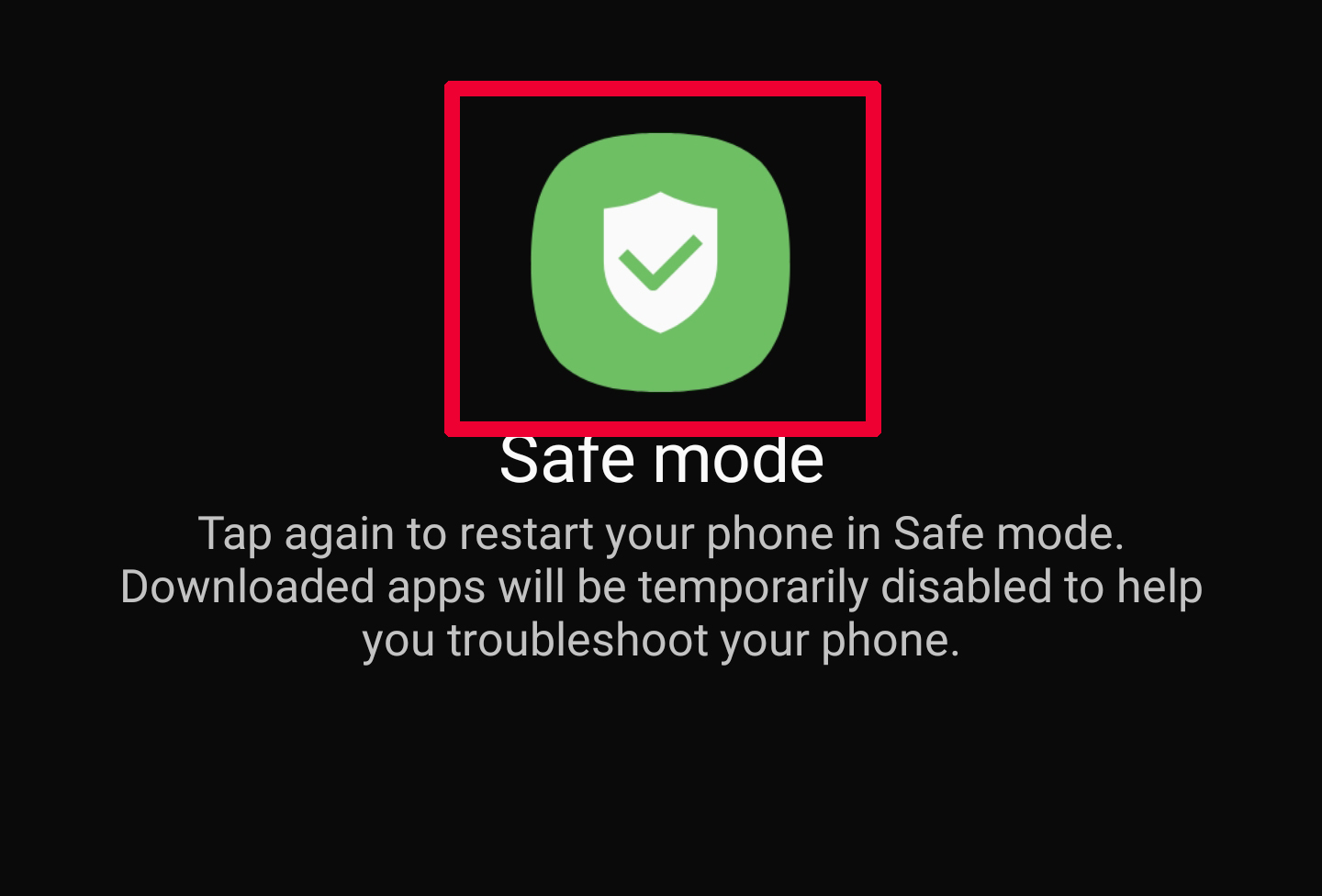

Step 3: Eliminate the App that Your Believe is the Virus
Usually Android viruses get masked in the form of applications. To eliminate apps, follow these mini-steps:
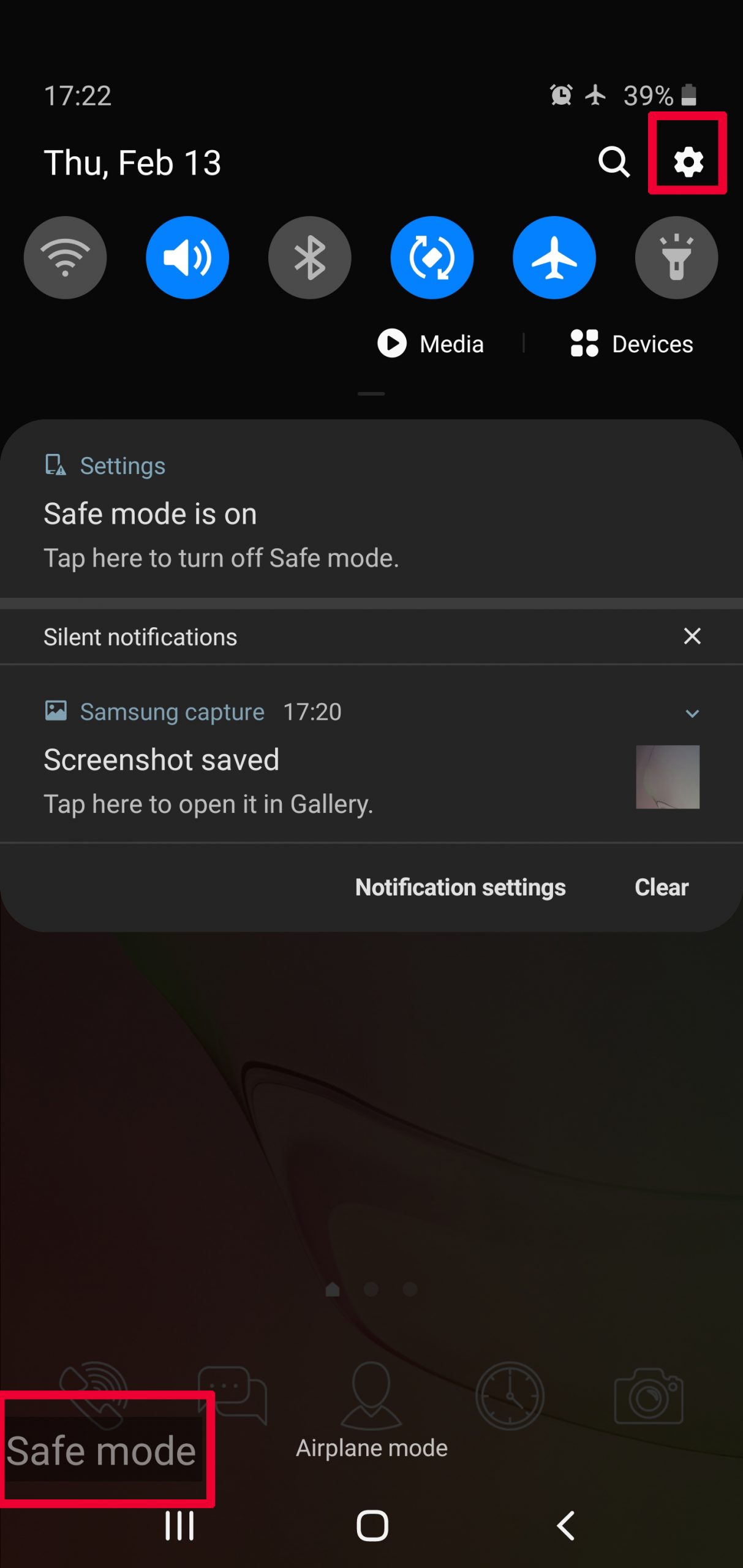
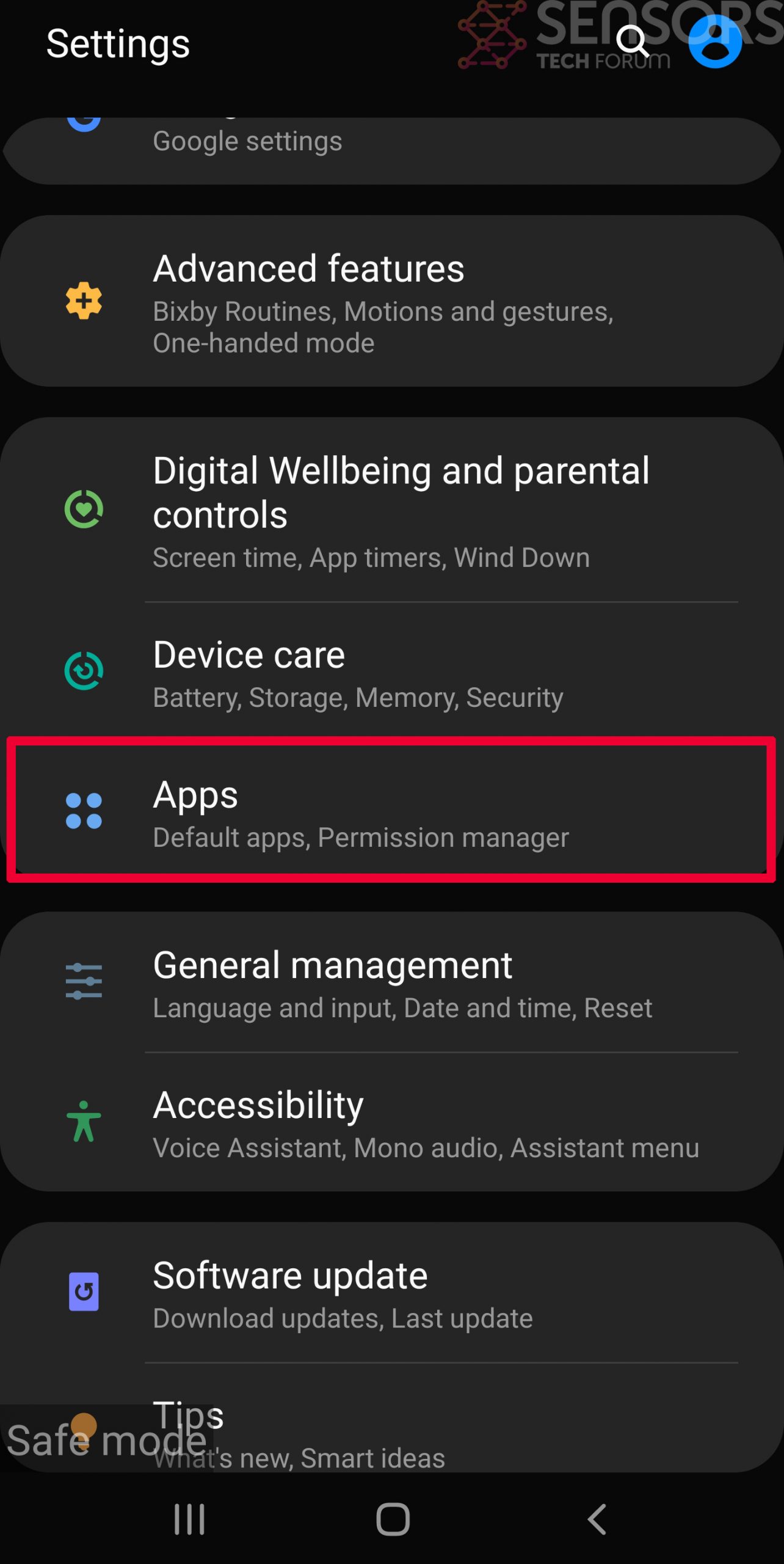
Step 4: Find Hidden Virus Files on Your Android Phone and Remove Them
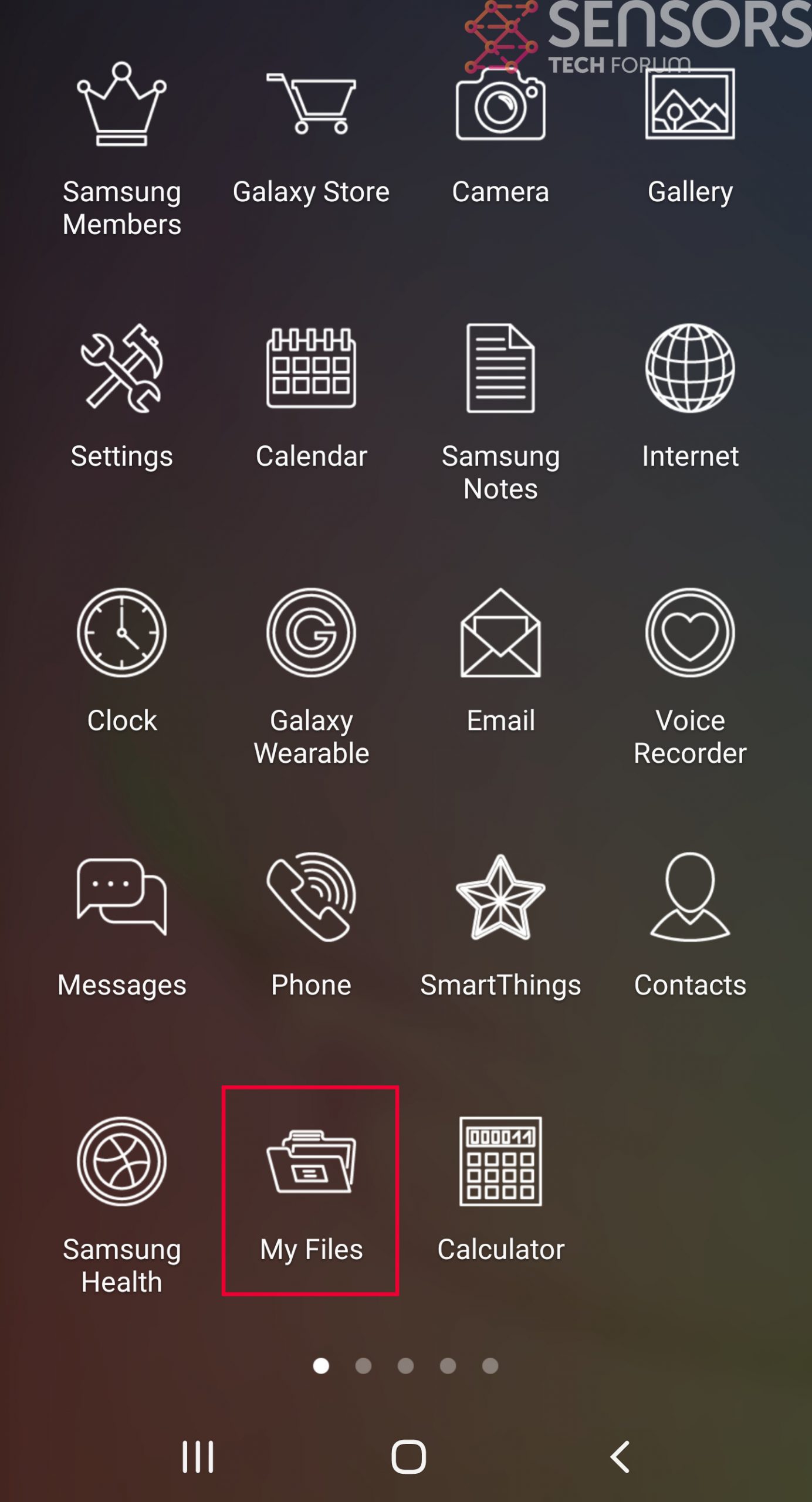
Simply locate the virus and hold-tap on the virus file to delete it.


