The Chrome CleanUp Tool is a utility application that was originally commissioned by the Google team. In recent versions of the Google Chrome this functionality has been built-in, at the same time the application still remains available online on different sources. We anticipate that computer hackers may create counterfeit copies of it that can be used to infect computers with viruses instead of protecting them.
Reports have appeared online about ‘Get the Chrome Cleanup Tool’ pop-up ads. Needless to say, such pop-ups have nothing to do with actual products and services developed by Google. Pop-ups of this kind stating that you should get the Chrome Cleanup Tool may appear on suspicious pages with unclear origin, and they may try to trick users into believing their browsers are infected. This is a technique typical for tech support scammers and adware operators. If you witness such pop-ups showing up in your browser, you may want to scan your system for potentially unwanted programs and adware.

Chrome Cleanup Tool Description
The origins of the Chrome Cleanup Tool lie in the early details of the Google Chrome browser where it was known as the Software Removal Tool. It was released by the company in an attempt to help users fix certain issues that may arise from browsing: infections with certain browser hijackers and aggressive tracking cookies installation.
The application was heavily dependent on the signatures that were built by the developers. At the time when the Chrome Cleanup tool was being offered by Google the security team was working together with an IT security company to detect the threats.
This means that the tool offers limited protection against certain threats. Being compatible only with a single application — the Google Chrome web browser makes it a utility that may not offer adequate protection against all virus infections. This aspect is probably one of the reasons why the tool has been discounted in favor of a built-in upgraded version.
Recent versions of the application allow the users to launch the application by navigating to the following menu: Settings > Advanced > Reset and clean up > Clean up computer. Google Chrome itself is programmed to automatically launch this function at certain times while at the same time giving users the ability to start a manual scan by themselves.
Chrome Cleanup Tool Issues & Privacy Concerns
When Google announced the feature a few versions ago several users and news media posted their concerns regarding its always-on availability. While the web browser will search for threats based on its built-in list of security risks, there is no option for turning it off. Security and privacy experts point out that all anti-virus tools can be disabled and this behavior might actually cause certain issues in select user cases. The concerns have come up following an analysis of the browser’s performance — the application has been found to scan the user’s folders. The scans take place in the background and use normal user privileges.
Warning! The Chrome Cleanup Tool and the new built-in feature are not considered general-purpose anti-virus or anti-spyware solutions. They can only aid in certain situations when using the default infection options. Every removal attempt also requires the user’s approval and permission.
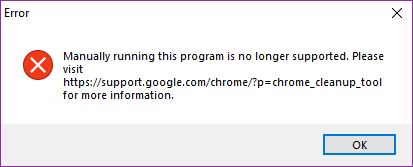
Computer users running newer versions of the Google Chrome web browser will encounter an error message stating that stand-alone installation is not allowed.
Fake Chrome Cleanup Tool Versions to Be Expected
The Chrome Cleanup Tool can be subject to the creation of fake counterfeit copies of it. Computer hackers may take advantage of the fact that it is a widely known application and available free of charge. They can take the legitimate apps and embed virus code in them thus creating infected payload files. This can be done over fake download sites that resemble well-known Internet portals or services. Other distribution methods may utilize file sharing networks such as BitTorrent that are popular with pirate software.
The other popular strategy that can be used by the criminals employs phishing email messages. They are created by the hackers with elements taken from Google official messages and notifications. The targets may be coerced into installing the fake tool via a hyperlink or a direct file attachment.


