
Image Source: Stephencdickson/ Wikipedia
LinkedIn’s data breach is already becoming one of the most controversial and troubling recent data incidents. And it proves that a data breach is definitely a breach in trust – between the vendor and the end user… and between the user and his habits. Anyone’s true colors are shown when there’s a problem, and “thanks” to breaches:
- We learn exactly how safe our personal information is;
- We learn how prepared multi-million companies are in the face of a crisis.
- We learn how shamefully easy hacking multi-million companies really is.
LinkedIn’s overall reaction – from the moment they knew about the problem in 2012 until today – is inadequate, to say the least, even though they started using salted hashes to store passwords after the 2012 breach and added two-step authentication. However, is LinkedIn the only one to blame here? Who is at fault when it comes to data incidents?
LinkedIn’s Portion of Guilt
To make a point or perhaps just to test LinkedIn’s common sense (of security), TrendMicro’s Raimund Genes made an experiment. Being one of the millions affected by the network’s leak of credentials, he received an email prompting him to change his password. This is what happened.
If I would have chosen Raimund_Genes as my password, it would have been marked as green, a Fair Password. When I tried Linkedin_Raimund, it’s also marked as a Strong Password, These are not what I would call strong passwords. You had a breach and it’s getting some attention: use this opportunity to re-educate users on strong password usage.
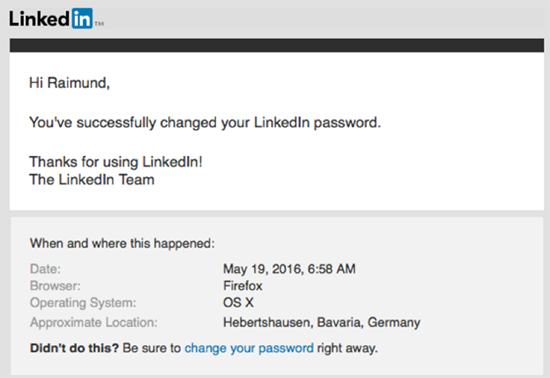
As the author points out, not only the password mechanism ranking is insufficient but LinkedIn also grabbed and displayed his browser, OS information, and his location. Not a safe practice considering the consequences of this breach – 117 million personal credentials being sold on the Dark Web for pennies. Furthermore, where exactly is LinkedIn’s honest explanation? They knew what was going on but didn’t do anything to prevent the leak from completely going rogue.
While breach notification has always been a tricky subject, cursory reassurances aren’t enough, not when companies hold so much valuable data. The trust of users is essential to any business.
Two questions that need to be addressed as soon as possible:
- While it’s been confirmed to be authentic, how exactly did a breach of this scale remain hidden?
- Does this tell us who was responsible for the breach in the first place, and how the information was used?
We Should Also Blame Our Bad Habits
LinkedIn is to blame but so are we. Social networking is always bound with risks, especially when we don’t do anything to protect ourselves. Let’s be honest, how often do we read privacy policy updates, terms of use, etc., of the services we use?
How many users apply whatever is made available to them (2FA, despite its controversial results is better than nothing) to improve the security of their accounts?
Furthermore, as visible by the leaked passwords, the frequency of such incidents doesn’t seem to improve users’ password hygiene. Weak passwords definitely make it easy for attackers to bruteforce accounts.

What Should I Do to Secure My Passwords?
Option 1: Use a Password Manager
The average password manager would install itself as a browser plug-in and take care of password capture.
How will it work? When you log in to a secure website (HTTPS), the password manager would offer to save your logins. When you come back to that page, the manager will automatically fill in your credentials, and sometimes web forms. Most password managers offer a browser-toolbar menu of all saved logins to make it easier to log in to saved sites.
However, password managers are applications, and applications can be hacked as well. Nothing is completely secure nowadays. So we get to option 2.
Option 2: Improve Your Habits
Perhaps the best way to secure your passwords is the most obvious one – change your passwords frequently and use combinations of letters, numbers, symbols, and upper cases. Complex and long passwords make it difficult for attackers to carry out bruteforcing attacks.
- If your credentials have been compromised in a data breach, don’t recycle your old password. Make sure to create brand new passwords, following the tips above. You can check your passwords’ strength via websites such as PasswordMeter.
- If the online service offers 2-factor authentication, use it! Check whatever additional protection is available and apply it.
Overall, what we can hope for is that LikedIn has learned their lesson and that the company has set a standard of what not to do when you have been breached. Companies need to become more straightforward about the privacy of their users. If not, repeating that your users’ privacy is your top priority is nothing but hypocrisy.













