Android is yet again being targeted by malware, this time by an updated version of a previously known Trojan. The Marcher Android Trojan has been recently upgraded and now it can show fake login screens. The Trojan is doing so to steal the victim’s credentials for several popular Android apps.
Marcher Android Trojan: Timeline of Attacks
Launched in 2013, this Android Trojan has been quite active on Google Play. Its primary purpose has always been harvesting user credentials and credit card data. According to a report by Zscaler, 2013 attacks initiated by Marcher went like that:
The malware waits for victims to open the Google Play store and then displays a fake html overlay page asking for credit card information. The fake page will not go away until the user provides the payment information.
Then, in 2014, the malware was already supplied with newer variants that were specifically targeting organizations in Germany:
Upon infection, Marcher would inspect the victim’s device and send a list of all installed apps to its command and control (C&C) server.
In case of a German financial app, the malware would show a fake page demanding user credentials for the particular institution.
Unaware that the login page is a fake, the victim would provide their credentials where they would then be sent to the malware’s C&C.
Marcher has also targeted financial organizations in other countries – Australia, France, Turkey and the US. Eventually, the malware added the UK to its list of victims.
Marcher Android Trojan 2016 Update. What’s New?
The latest update of the Trojan is all about making it even more dangerous and sneaky. This time, the malware operators have moved their focused to popular Android apps instead of banking apps.
The list of targeted apps should make every Android user more conscious about his device’s security:
- Playstore (com.android.vending)
- Viber app (com.viber.voip)
- Whatsapp (com.whatsapp)
- Skype (com.skype.raider)
- Facebook messenger (com.facebook.orca)
- Facebook (com.facebook.katana)
- Instagram (com.instagram.android)
- Chrome (com.android.chrome)
- Twitter (com.twitter.android)
- Gmail (com.google.android.gm)
- UC Browser (com.UCMobile.intl)
- Line (jp.naver.line.android)
In other words, the latest 2016 variant of the Trojan is solely after credentials of the apps mentioned above. To collect them successfully, Marcher would show a fake login screen whenever the user uses one of the apps listed.
Another change in the newer variants of Marcher is the implementation of simple obfuscation by the malware author via base64 encoding and string replace functions. In older samples, researchers say code obfuscation was not present.
Not surprisingly, the harvested data is sent to an online command & control server that belongs to cyber criminals. Another update in Marcher concerns the way the data is transmitted. Previously this was done in cleartext via HTTP, and now the malware has employed an SSL-protected channel.
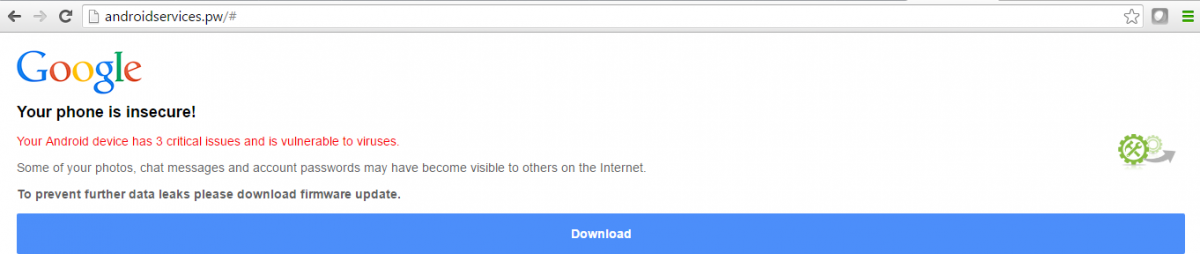
Marcher Infections Initiated by Fake Android Security Updates
In its latest campaign, the malware is being distributed via fake Android firmware update.
The researchers were able to unveil the payload dropped as “Firmware_Update.apk“:
An HTML page serving this malware scares the victim by showing that the device is vulnerable to viruses and to prevent personal data theft, prompting them to install the fake update, researchers say.
How to Stay Protected against Marcher Trojan, Android Malware
All of the updates registered this past month indicate that Marcher is a constantly evolving piece of malware. It is perhaps the most prevalent threat to Android devices.
Since Play Store is often leveraged in attacks, users should be cautious with apps coming from both Play Store and third-party app stores. Nonetheless, the chances of getting malware from an official store are much less than getting malware from unspecified places.
Also, be sure to follow these simple steps for better Android security:
- Research your applications before installing them;
- Carefully read the privacy policy, terms of service and list of permissions in Google Play Store;
- Check if the permissions the app asks are covered by the app’s functionalities;
















I always worried about Trojan whenever i try to download any app from google play, this should be under control in my perception.
I am hacked majorly! I went thru 4 phones and he took over all of them. I knew nothing about hacking but in this nightmare I’ve learned alot. I had a fake google account, pkaystore, fb, Tim tok, all my social media apps were fake. My calls were being redirected as well as my emails. I’ve reset my phones with a hard boot but when I set up my phone after the reset I’m still directed to the fake google sign up., etc… I dont know how to get rid of this hacker.
Hi Denise,
Have you tried contacting the authorities?