Previous servers thought to be secure have been discovered to expose certain vulnerabilities in DDoS mitigation solutions caused by a newly discovered method of carrying out DDoS attacks going by the name of ‘Pulse Wave.’
Discovered by Imperva Incapsula, a DDoS mitigation firm, the discovered new method of DDoS attacks and its name comes from the very nature of its attack which is essentially shaped in the form of abrupt repeating pulses. The abrupt repeating lines consist of a series of short-lived bursts of assault traffic that occur in clockwork-like succession.
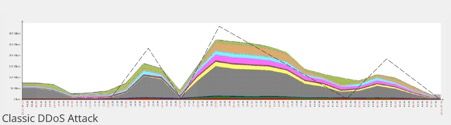
In a classic DDoS attack, the assault itself usually takes the shape of a sloping triangle that goes up and down as the attacker begins to assemble bots and starts to target certain desired objectives:
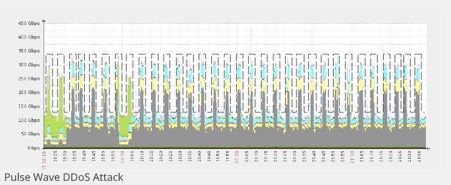
On the other hand, ‘Pulse Wave’ assaults resemble quite a different graph. The graph begins from zero and reaches maximum values in a limited amount of time resulting in a quick recession back towards the zero value, and a return to maximum values in a successive and repetitive cycle at short-lived intervals:
A Single Botnet Facilitating the Whole ‘Pulse Wave’ DDoS Attack
Researchers have observed that in-between the pulses’ gaps the attackers appeared to changing targets continuously and on the go, simultaneously directing similar bursts of traffic at a multitude of victims.
The intriguing thing about this new method of DDoS attacks is that the ‘Pulse Wave’ DDoS utilizes and can jack up DDoS traffic significantly faster than conventional DDoS assaults. Analysts found that during the attack, the botnet does not shut down and it also does not restart itself again sometime later on. Because o the botnet switches to another target, when the down pulse period finishes, the botnet reverts to its initial target followed up by the execution of a short pulse wave cycle and finalizing its move by changing to another target. Thus, the ‘Pulse Wave’ is significantly more effective against targets that are secured from DDoS attacks by a mitigation service that provides failover to the cloud.
Usually, such specific levels of control are typical of botnets that are offered for rent to potential buyers, i.e., attackers, through a DDoS-for-hire service. Botnets that are offered in mutual exchanges between the attacker and individual hosting the botnet, often require to be working at maximum capacity and almost all the time, hence it is essential that they switch between different targets.
“Whoever was on the other end of these assaults, they were able to mobilize a 300Gbps botnet within a matter of seconds,” stated Igal Zeifman, director of marketing at Imperva. The average value of ~1Gbps per normal DDoS attack was shattered by the new ‘Pulse Wave’ attack, with the highest botnet peaking at 350Gbps.
Hybrid Mitigation Solutions Affected by ‘Pulse Wave’ Attacks
Hybrid mitigation approaches consist of a mixture of hardware that is based on the premise, and cloud-based solutions. On-location hardware is designed to be the default and main mitigation solution; however, it is also configured to trigger a cloud-based DDoS protection backup, thus protecting customer information and files whenever the system is about to be inundated with traffic.
In effect, where all this leaves the cloud mitigation service is that it will need to begin sampling traffic anew and from scratch, thus the attacker’s chances of taking down the server are significantly boosted because of the prolonged delay caused by the cloud mitigation service’s resampling. Imperva has also stated that a ‘Pulse Wave’ attack with not jack-up time represents an even worse scenario for networks whom a protected with hybrid DDoS mitigation services.
Such hybrid mitigation solutions are primarily configured to deal with classic and conventional DDoS attacks that build over time. However, because ‘Pulse Wave’ attacks are quick and extremely vicious, the mitigation system in place becomes quickly flooded, left with little to no time, nor the necessary bandwidth to resort to the backup cloud-based solution.
Contrary to Imperva’s statements regarding hybrid mitigation systems, a well-designed and functional DDoS mitigation service would, as a matter of fact, and technicality can handle the ferociousness of a ‘Pulse Wave’ attack. If a DDoS mitigation system utilizes connectionless signaling, protocols, therefore, will be substantially harder to tamper and disrupt, even if the inbound link bandwidth is completely flooded by a DDoS attack.
On another note, there may very well be another explanation for ‘Pulse Wave’ attacks. It could be that the attack itself is against a subnet range, where a piece of the subnet is actively protected by the observer. Hence, the botnet would give off the impression of going flat-out at a high rate and therefore to deceive the mitigation system; it disguises itself by pretending to ‘switch’ targets. Instead, that switch was either attacks owned by the same target that was essentially not protected or was owned by another body that happened to be coincidentally sharing an IP space.
What Do the New ‘Pulse Wave’ DDoS Attacks Mean for Organizations and Companies?
The ‘Pulse Wave’ DDoS technique can enable attackers to shut down companies and organizations for unspecified periods of times, while additionally carrying our DDoS attacks on multiple other targets. This feature is executed in a straightforward but cunning manner. When a pulse hits the company or organization’s equipment, they are effectively shut down, and while the systems may be recovering it will take some time before they fully recover, until then another pulse is sent along the network, effectively jamming and leaving the system stunned.
Zeifman states: “Additionally, the lack of communication prohibits the appliances from providing information required to create an attack signature.”
Most of the victims of the ‘Pulse Wave’ DDoS attacks are organizations within the financial and gaming sectors. The attacks may be novel as well as severe. However, they are not unrecoverable from. Organizations have been steadily recovering from the attacks, albeit slowly and with a prolonged downtime, progress is evident. It is the company’s bottom line that is predominantly affected.
The full ‘Pulse Wave’ DDoS attack is exhaustively detailed in an Imperva Incapsula report that you can find here.