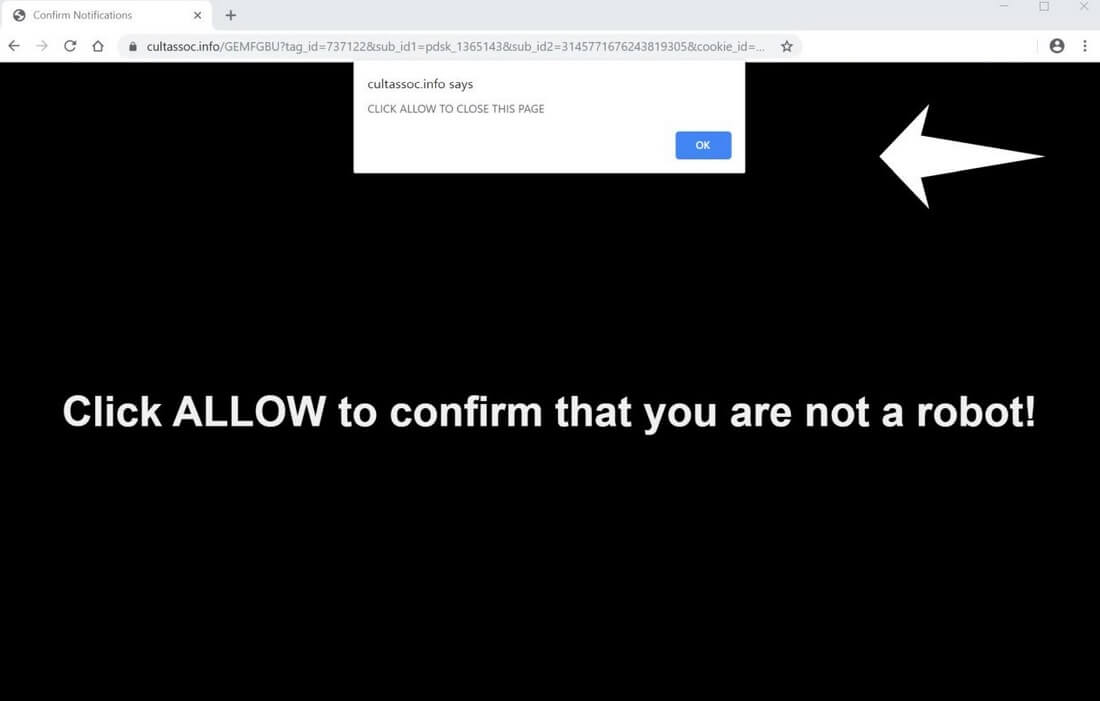
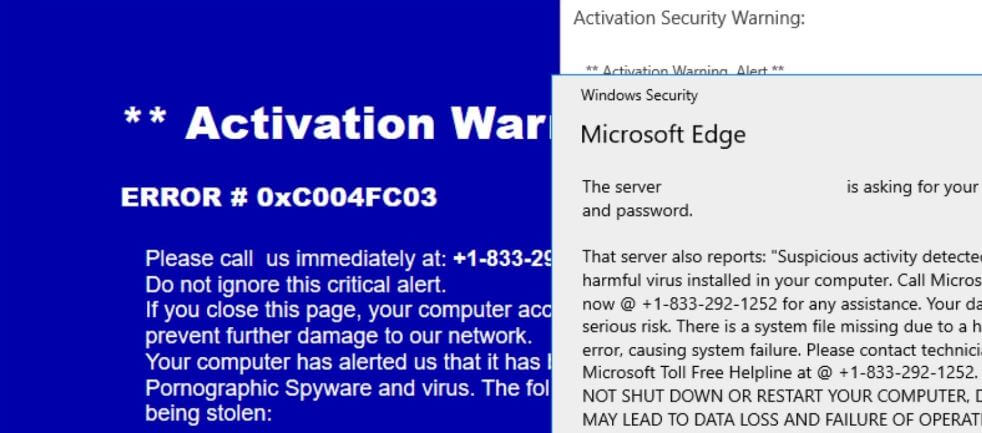
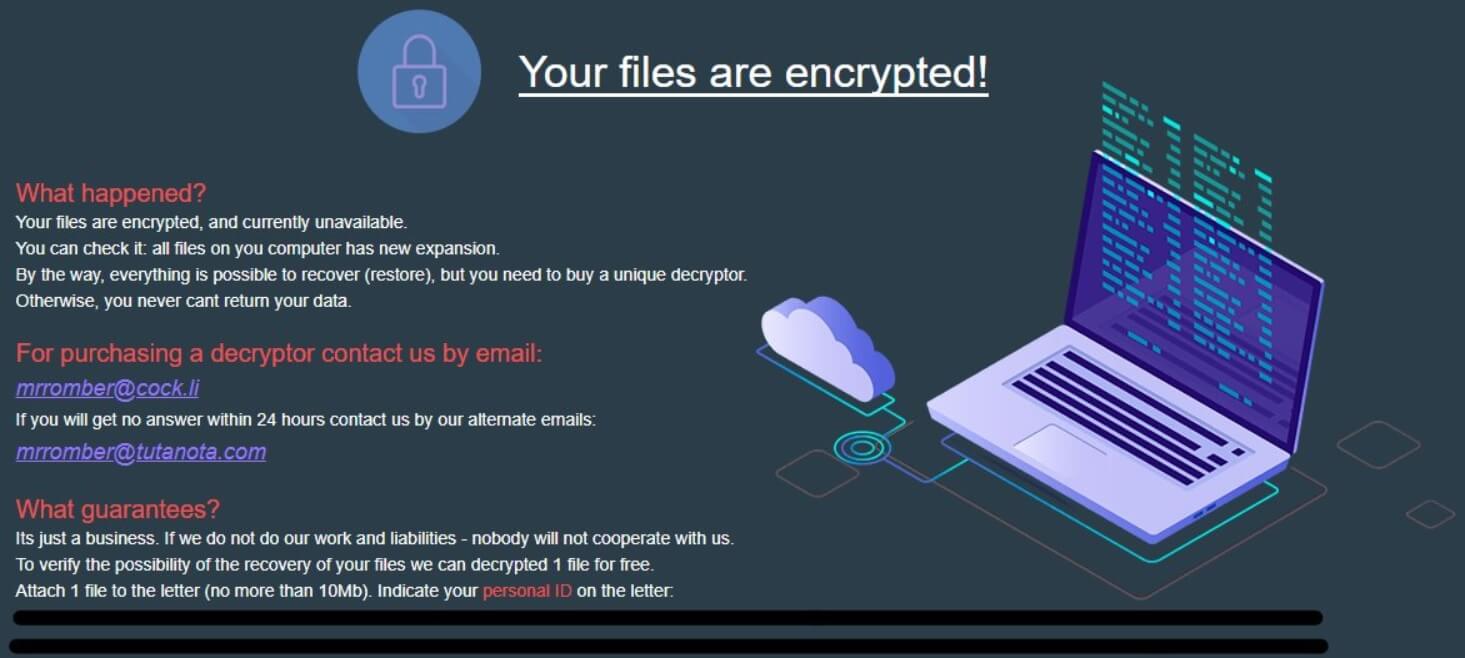
CVE-2019-13720: Severe Chrome Bug Exploited in the Wild
CVE-2019-13720 is a new vulnerability in Chrome. Google is warning users that this use-after-free vulnerability in the browser’s audio component is currently being exploited in the wild. CVE-2019-13720: some details CVE-2019-13720 was discovered by Kaspersky security researchers Anton Ivanov and…