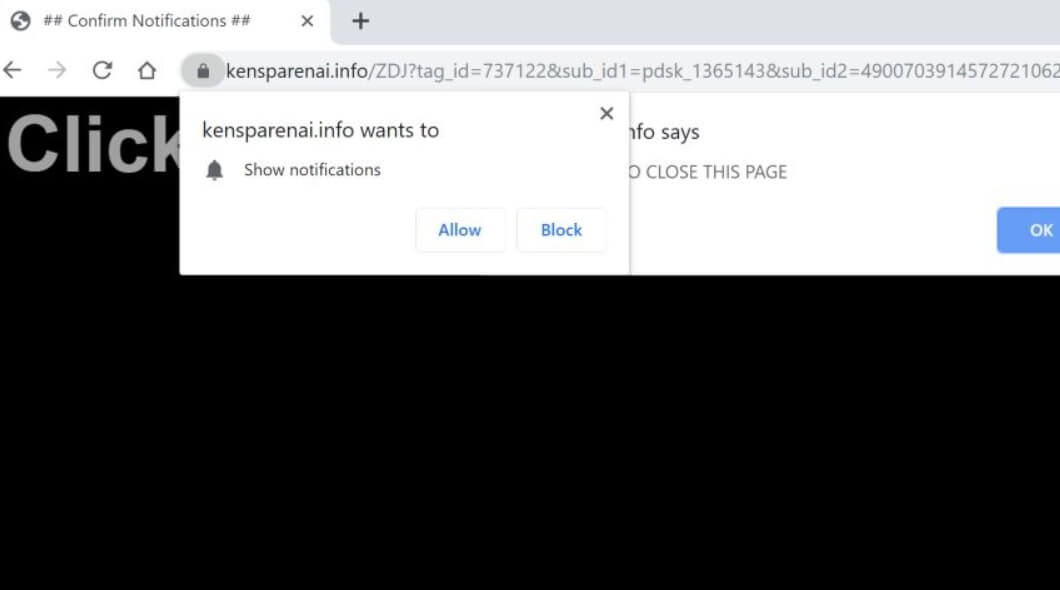
Baldr Malware Set Against CS:GO and Apex Legends Cheaters
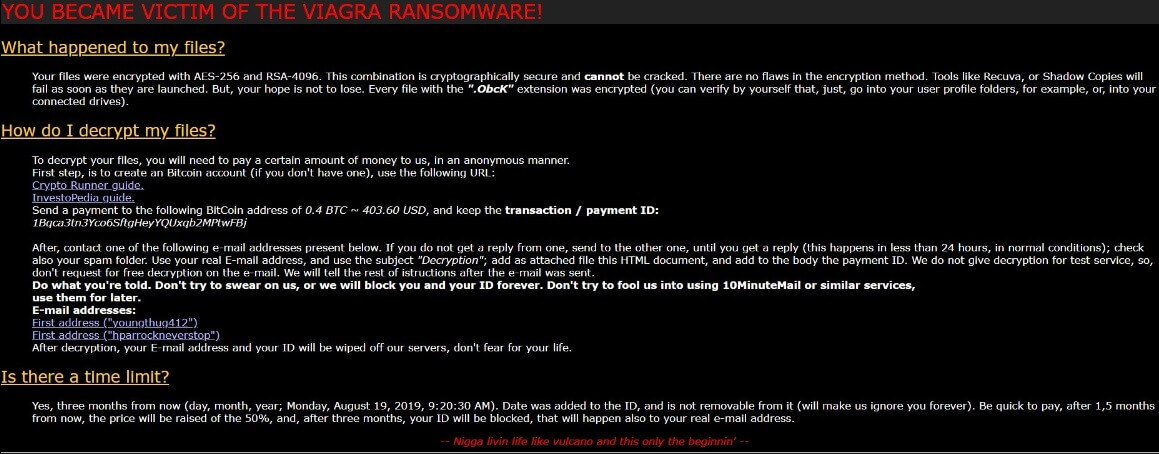
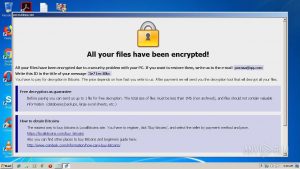
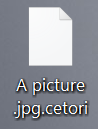
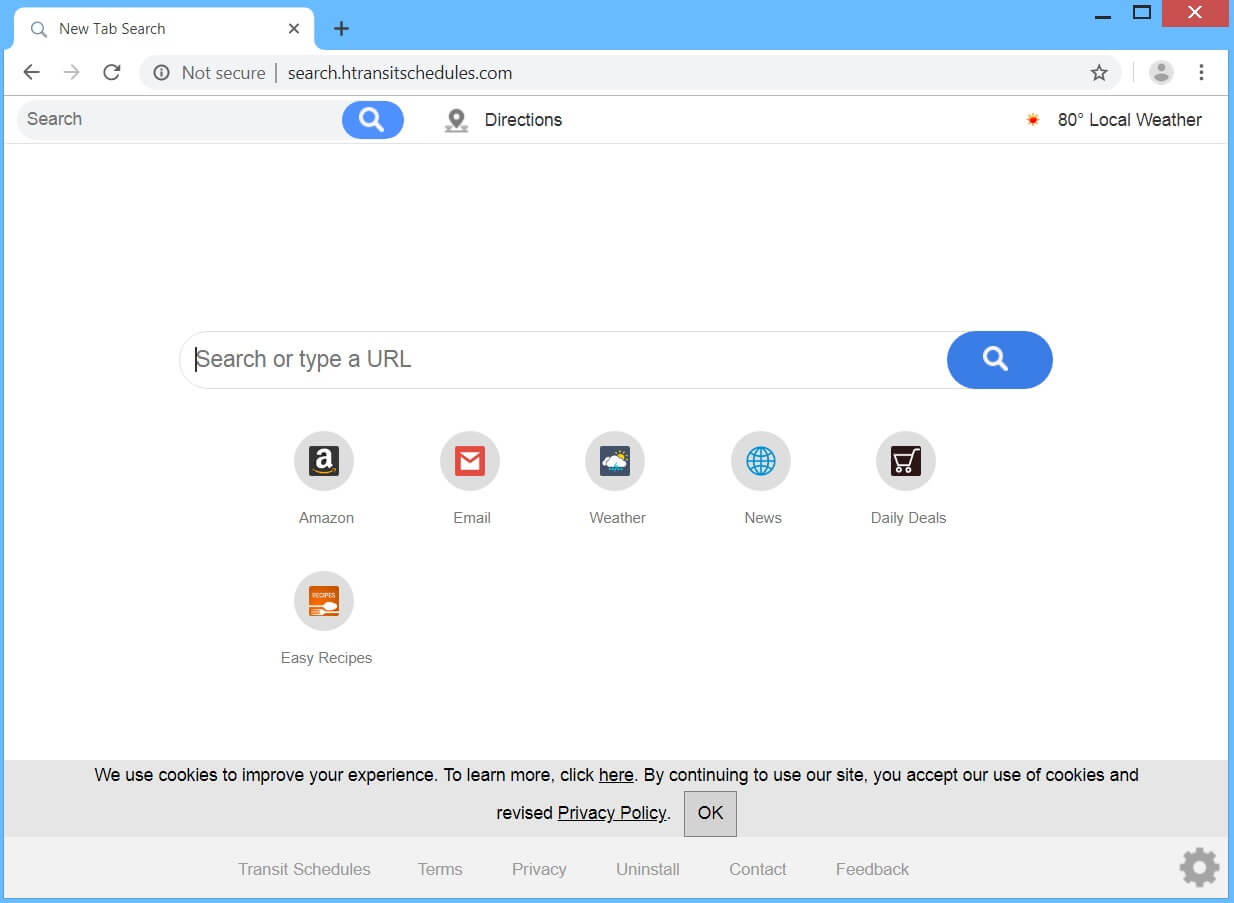
The Baldr Malware is a computer virus which is designed against computer gamers who cheat at two popular games — Counter Strike: Global Offensive and Apex Legends. It is particularly powerful and the hacking group behind it appears to be…