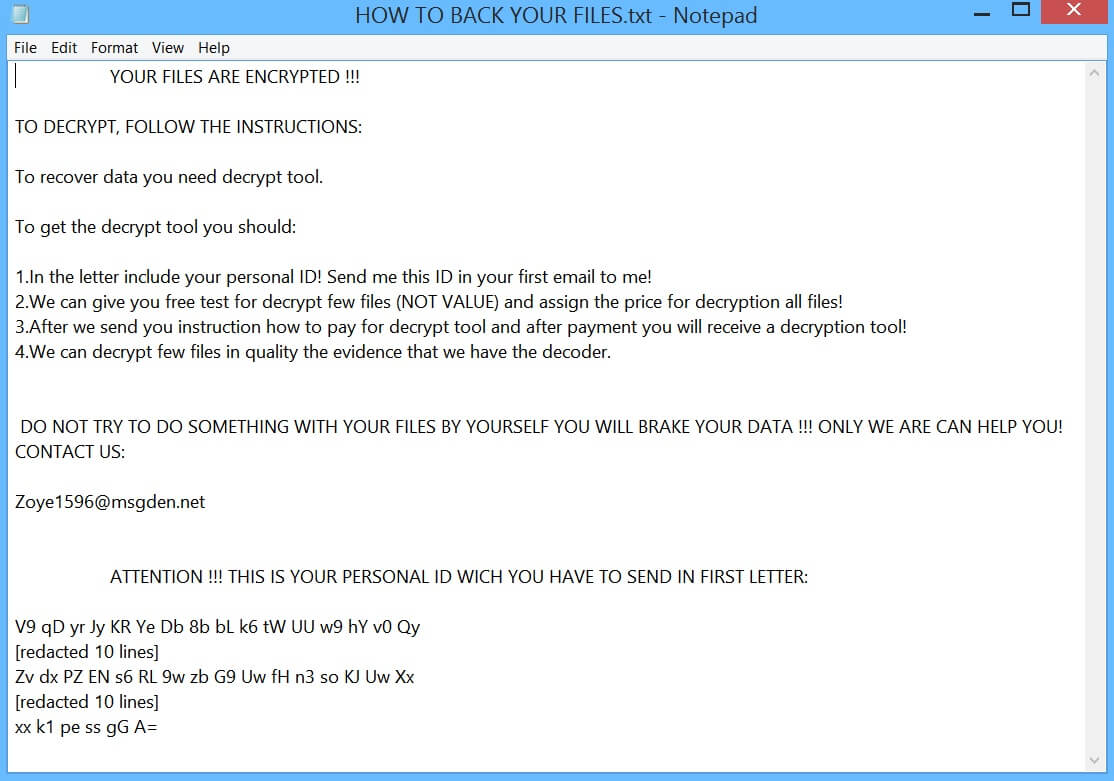
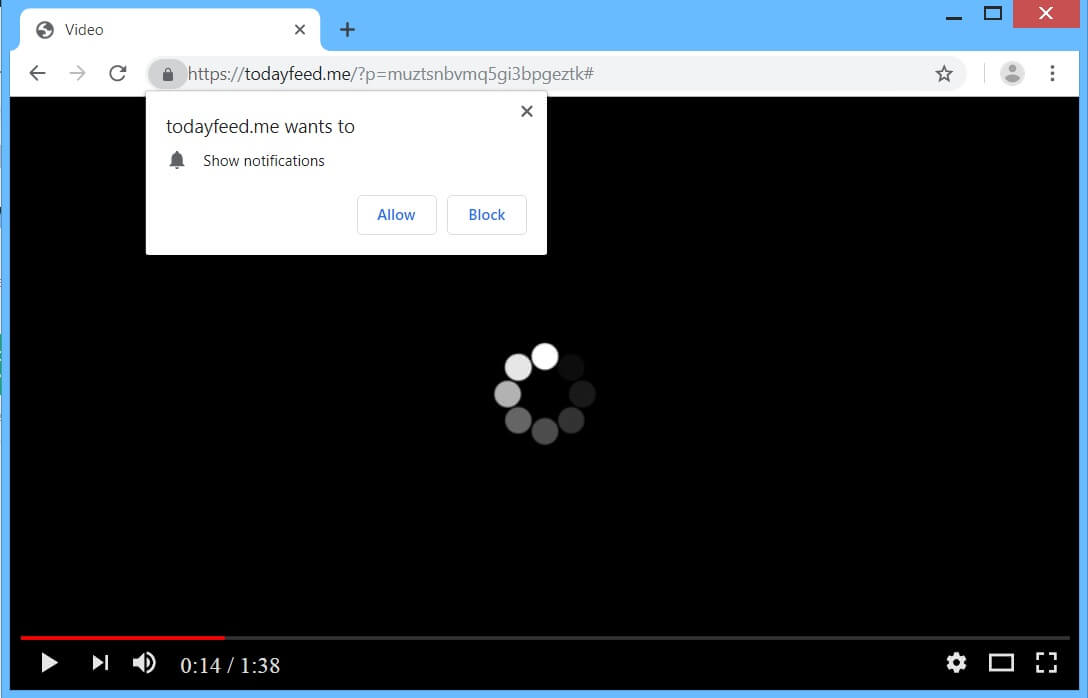
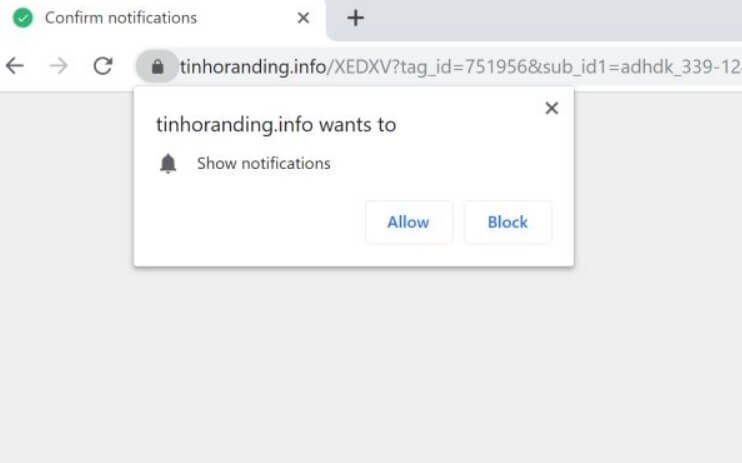
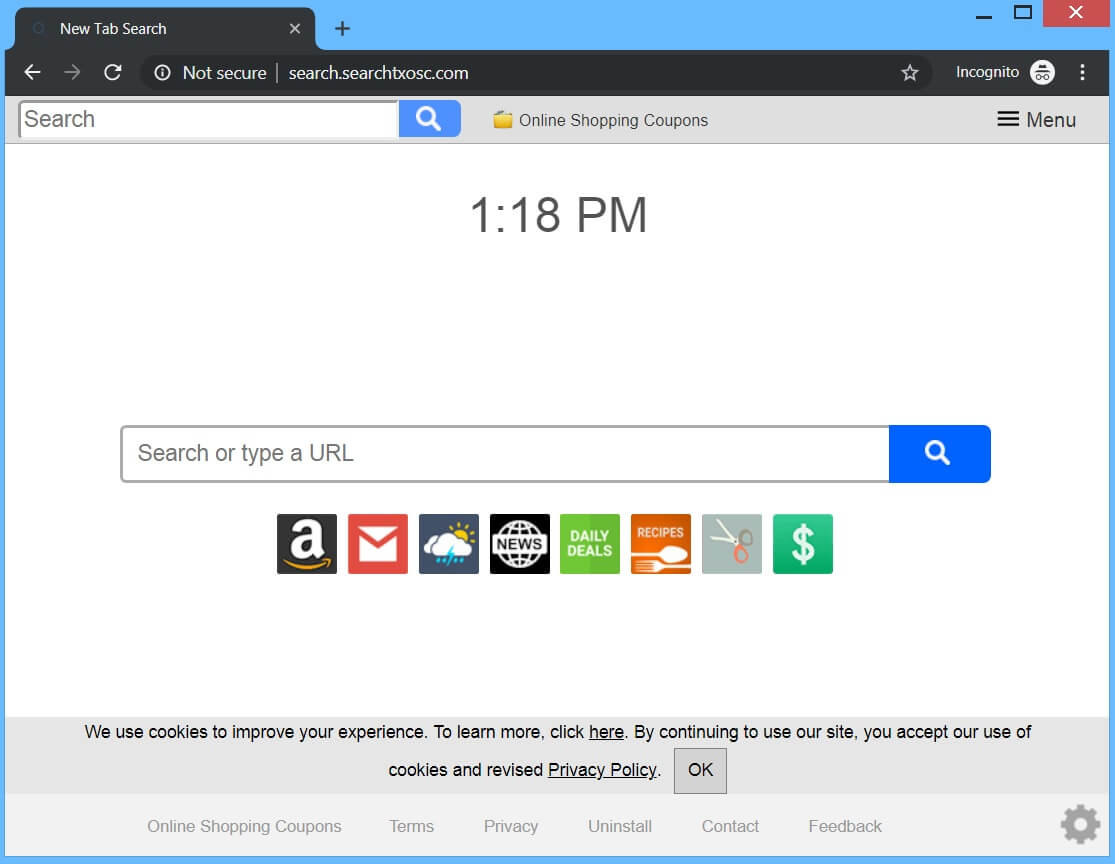
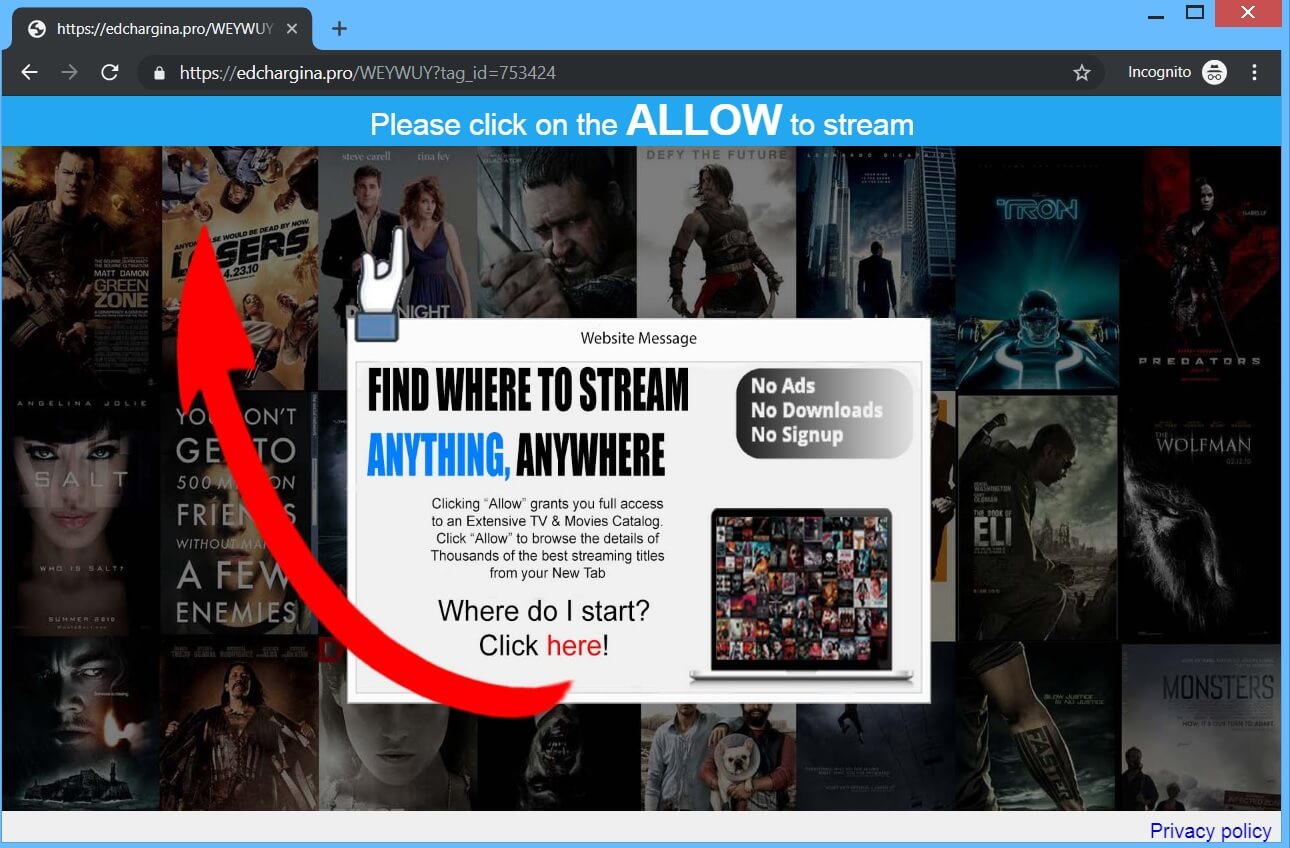
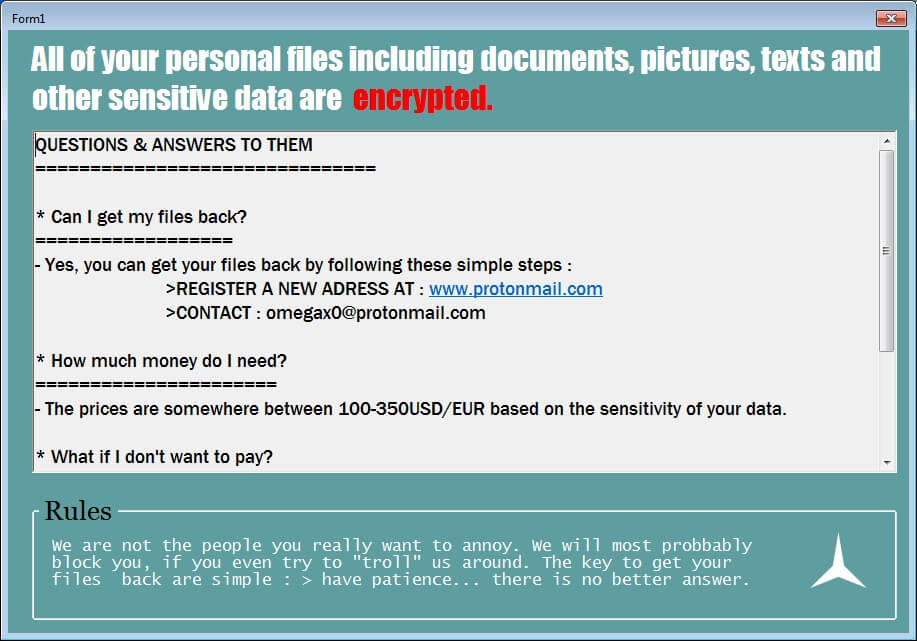
How to Remove Landpage.co YouTube Virus
The so-called Landpage.co is the domain of an online virus that has been detected in active contamination campaigns against online users around the globe. One of the channels used for the spread of the annoying Landpage.co YouTube virus is the…